Technical Debt and it Types Datasets
Collection
24 items
•
Updated
•
1
Unnamed: 0
int64 0
832k
| id
float64 2.49B
32.1B
| type
stringclasses 1
value | created_at
stringlengths 19
19
| repo
stringlengths 4
112
| repo_url
stringlengths 33
141
| action
stringclasses 3
values | title
stringlengths 1
1.02k
| labels
stringlengths 4
1.54k
| body
stringlengths 1
262k
| index
stringclasses 17
values | text_combine
stringlengths 95
262k
| label
stringclasses 2
values | text
stringlengths 96
252k
| binary_label
int64 0
1
|
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
45,861 | 24,248,229,123 | IssuesEvent | 2022-09-27 12:22:55 | TodePond/CellPond | https://api.github.com/repos/TodePond/CellPond | closed | Empty cells not getting drawn often enough | bug performance | When the world is nearly full of a very active cell (such as direction water) the random redraw rate does not reliably draw the remaining empty cells. This makes it look like there are floating phantom cells there. Non-active cells should be drawn more somehow! | True | Empty cells not getting drawn often enough - When the world is nearly full of a very active cell (such as direction water) the random redraw rate does not reliably draw the remaining empty cells. This makes it look like there are floating phantom cells there. Non-active cells should be drawn more somehow! | non_test | empty cells not getting drawn often enough when the world is nearly full of a very active cell such as direction water the random redraw rate does not reliably draw the remaining empty cells this makes it look like there are floating phantom cells there non active cells should be drawn more somehow | 0 |
237,566 | 19,657,581,893 | IssuesEvent | 2022-01-10 14:04:42 | OllisGit/OctoPrint-DeleteAfterPrint | https://api.github.com/repos/OllisGit/OctoPrint-DeleteAfterPrint | closed | Select folder to move to from sidebar dialog | type: enhancement status: waitingForTestFeedback | Often I change the folder to move a file into after print. I then go into settings, find the plugin and change the folder.
It would be quit useful, to be able to select the folder to move to from a "pulldown". In theory, this pulldown could also feature the keyword [delete], so the delete option would not need a checkbox.
Currently the sidebar looks like this:

A dialog for selecting the folder to move/delete (similar when you "move" an item from the "Files" sidebar could look like this:

You could also add these two entries:
[do nothing]
[delete] | 1.0 | Select folder to move to from sidebar dialog - Often I change the folder to move a file into after print. I then go into settings, find the plugin and change the folder.
It would be quit useful, to be able to select the folder to move to from a "pulldown". In theory, this pulldown could also feature the keyword [delete], so the delete option would not need a checkbox.
Currently the sidebar looks like this:

A dialog for selecting the folder to move/delete (similar when you "move" an item from the "Files" sidebar could look like this:

You could also add these two entries:
[do nothing]
[delete] | test | select folder to move to from sidebar dialog often i change the folder to move a file into after print i then go into settings find the plugin and change the folder it would be quit useful to be able to select the folder to move to from a pulldown in theory this pulldown could also feature the keyword so the delete option would not need a checkbox currently the sidebar looks like this a dialog for selecting the folder to move delete similar when you move an item from the files sidebar could look like this you could also add these two entries | 1 |
153,183 | 24,084,494,218 | IssuesEvent | 2022-09-19 09:40:56 | broodroosterdev/windesheimapp | https://api.github.com/repos/broodroosterdev/windesheimapp | closed | Brightspace | design needed ui api | ## API
- [x] Login
- [x] Refresh
- [x] Implementeren Siren
- [x] Ophalen courses
- [x] Course pinnen
- [ ] Ophalen inhoud
- [ ] Ophalen berichten
- [ ] Onderzoeken datatypes
- [ ] Onderzoeken downloaden bestanden
## UI
- [x] Brightspace tab in appbar
- [x] Overzicht van courses
- [x] Course pinnen
- [x] Course card
- [ ] Inhoud van course (lesstof)
- [ ] Berichten van course | 1.0 | Brightspace - ## API
- [x] Login
- [x] Refresh
- [x] Implementeren Siren
- [x] Ophalen courses
- [x] Course pinnen
- [ ] Ophalen inhoud
- [ ] Ophalen berichten
- [ ] Onderzoeken datatypes
- [ ] Onderzoeken downloaden bestanden
## UI
- [x] Brightspace tab in appbar
- [x] Overzicht van courses
- [x] Course pinnen
- [x] Course card
- [ ] Inhoud van course (lesstof)
- [ ] Berichten van course | non_test | brightspace api login refresh implementeren siren ophalen courses course pinnen ophalen inhoud ophalen berichten onderzoeken datatypes onderzoeken downloaden bestanden ui brightspace tab in appbar overzicht van courses course pinnen course card inhoud van course lesstof berichten van course | 0 |
443,396 | 30,887,932,562 | IssuesEvent | 2023-08-04 00:35:24 | facebook/flow | https://api.github.com/repos/facebook/flow | closed | Example from docs for $ObjMap broken | Typing: unions/intersections Typing: destructors documentation | $ObjMap mixes up return values when mapping functions. By "mixes up" i mean that I get errors showing that flow is considering the union of all return types collectively for each function individually.
* [docs im referring to](https://flow.org/en/docs/types/utilities/#toc-objmap)
* [try it in the playground](https://flow.org/try/#0PTAEAEDMBsHsHcBQiSmgUwC4HIDOp4AnAS03VAENRIBXAOwGNNjY7RMBPAB3MwAsKmdhQDW6fFQAGACgCUoALwA+UADVJlOgBNQhLDUJ0JoSetDTS+PZgNtOPWYnvkAogA9MhCkwBK+wwAq3OQKoAA8qkrScooqqvLKasi0jMysuvRhAIIANKAA8gBcoADeANpiHMW4nsR0AOYAusUxiVkAvlGwxfmyxQAk+QBGAFYAshRcYfl57p7emH42gcEqJYiguv5swyPoTAB0lbjSsLIHelo0DOjR3gx5Igkqu-uYBxS4uMT1dNL3eRKoAqzVAsBBMXaskBUIA3Ih2sgGKwamDFKUNpQWs92IQaOgcpihtjYqBsJBYLBsAj4YhpHi-mcPsUhpSMBQ6LJYaBUPkRHSGadzsTQDUSA0uZtefzUP13DwmC5CIRYIQBfQhQcRazYOzOdzUAA5WA8PJDUDEYxiur1FBgOVuBWYJUqtWCpkMbmbb0+qVgY2m0AMAifUB0WBCOrsPjkVU-OoUaBg0ZvIA)
Expected:
only errors on line 18 and 20 showing usage. This is the case with v56
Actual:
Using version 68 the following errors are displayed in addition to 18 and 20.
```
11: a: () => true,
^ Cannot return `true` because string [1] is incompatible with boolean [2].
References:
12: b: () => 'foo' ^ [1]
11: a: () => true,
^ [2]
12: b: () => 'foo' ^ Cannot return `'foo'` because boolean [1] is incompatible with string [2].
References:
11: a: () => true,
^ [1]
12: b: () => 'foo' ^ [2]
```
Impact:
Anyone wanting to map an object type containing functions to a transformed set of functions will be affected. I discovered this while making types to transform from types for our API to backend types for our controllers, which are basically the same as the API types but with additional parameters.
* [example from my use case](https://flow.org/try/#0PQKgBAAgZgNg9gdzCYAoVxhgIJgEZwCuAdgCZhRwBOYA5gKbH1UCWAxmAMrMBu792AA4swAFwCeg+qnoAPQdVFjJ9MAHFGzdtyp82A4WAC8YAN4BqANoBbeqIAWcUgDkAhrYBcYAM6jWxWgBdLwAKQVcqd28vV2JxAEpjAD4wAAUqOGsWb3oAHljxJIBfdEwuTNVCURYYFgllKW8xODFI4m9KKmsxe1VsVIBJChI2arhiMBZiURbvCocp2h7XJWsVtl6mgGs4V1QJKTAAJTtCKmIAFRVcgDEvG5Gx4hSTABIAYVcYGFzcgDUkiEQgA6UERWjRMAFRJGFJ-GFwgA0YBuSX2KhwVFohFs0yuUlu90eLHGLzAHy+P1y2EBIXBXmwCKhcSZ2GRqPRhwAsnZHKR8XkhCwvBomKw2Do9AYWMieQ4nF5fP5aGTXgBRGD0XGiAXU4Sy3lONGc1QXNodajWIUXODvcZ+ODfZjGMC5OV8oWA1xed1OIUI1BgMBhCJRBlYnGMHXXX2kT3Iwg5KheYg4vDMZEzLaMRV+RZMk6iM6XGOGuPCY1lBZNbI9VQHev2FZQnyLTVgWzy8hTFtse0ZJ00TrMnCDHyOQgwbvWQSa7UyeSKBp9YSxu3TAeaqi6oUizTiyX8IUGru55Wqz7fXJm2IWrrW239x1bk98nf6sCxpKVrDVyZNBx6wxBxm1cHxeH4AByJo4B4ZhKTAPsN2fZ1vAnKdJhnOcozEVwtkWSZphaVw2D7EglAQzs+RrCY6iafoBgXBQqCUBscGEdcHUHd9hXUfdtAg-RPRdV4AHk8AAKy5VxBD1GUwBvdpOitYQbU4zdmGNINtLAdBA1ABS1U4C5OGQLBAx03SqzaZSCMA5cmgQXoJkA8QwGIOAlB7WIwDgST6FGMAEGoLYmigKZ6FBYETQU+hfFjABGF06TPfNkjSDIshyXJU2sdMqDRNiLji0RYwAJmS713LTZgmXSTJsjyJVFmNIFXATJNkXCLpvDqzLGuBKg4sdOCQgS+IvApK9FLvFSWDUp9B2RYr4rLBKkniABuMAyjgLYwAAQlQNqOozMBuusXr0vqrLIqGuYYFGyDXEgibyUvH4ZuUh91JQqhlpK8qNu23atiO7SMCwPAqiC5y6zciJVAQSJBCkbsJh8vyJIC1jejc0gWg8pRgqoLYouioqSqFF1TAAHws8xREBstsFCKrmoCPqGuy3L8qSREGaZ1auwAIVCPAUxqqgudu3IOZVVBaZKSGwDkKRRnocg-xmIKQuO0wLKF0qWbZ1KAlO-7ztDS6ZYG+6RvoMb4mRMo7Unch0xbeWAH5fb9-3vcN5nRfFyW8rOxMzu6qJbZyQbhsex3nteoMyjIjDPbA3nmADwOigZDjFq3XUVtET14iAA) | 1.0 | Example from docs for $ObjMap broken - $ObjMap mixes up return values when mapping functions. By "mixes up" i mean that I get errors showing that flow is considering the union of all return types collectively for each function individually.
* [docs im referring to](https://flow.org/en/docs/types/utilities/#toc-objmap)
* [try it in the playground](https://flow.org/try/#0PTAEAEDMBsHsHcBQiSmgUwC4HIDOp4AnAS03VAENRIBXAOwGNNjY7RMBPAB3MwAsKmdhQDW6fFQAGACgCUoALwA+UADVJlOgBNQhLDUJ0JoSetDTS+PZgNtOPWYnvkAogA9MhCkwBK+wwAq3OQKoAA8qkrScooqqvLKasi0jMysuvRhAIIANKAA8gBcoADeANpiHMW4nsR0AOYAusUxiVkAvlGwxfmyxQAk+QBGAFYAshRcYfl57p7emH42gcEqJYiguv5swyPoTAB0lbjSsLIHelo0DOjR3gx5Igkqu-uYBxS4uMT1dNL3eRKoAqzVAsBBMXaskBUIA3Ih2sgGKwamDFKUNpQWs92IQaOgcpihtjYqBsJBYLBsAj4YhpHi-mcPsUhpSMBQ6LJYaBUPkRHSGadzsTQDUSA0uZtefzUP13DwmC5CIRYIQBfQhQcRazYOzOdzUAA5WA8PJDUDEYxiur1FBgOVuBWYJUqtWCpkMbmbb0+qVgY2m0AMAifUB0WBCOrsPjkVU-OoUaBg0ZvIA)
Expected:
only errors on line 18 and 20 showing usage. This is the case with v56
Actual:
Using version 68 the following errors are displayed in addition to 18 and 20.
```
11: a: () => true,
^ Cannot return `true` because string [1] is incompatible with boolean [2].
References:
12: b: () => 'foo' ^ [1]
11: a: () => true,
^ [2]
12: b: () => 'foo' ^ Cannot return `'foo'` because boolean [1] is incompatible with string [2].
References:
11: a: () => true,
^ [1]
12: b: () => 'foo' ^ [2]
```
Impact:
Anyone wanting to map an object type containing functions to a transformed set of functions will be affected. I discovered this while making types to transform from types for our API to backend types for our controllers, which are basically the same as the API types but with additional parameters.
* [example from my use case](https://flow.org/try/#0PQKgBAAgZgNg9gdzCYAoVxhgIJgEZwCuAdgCZhRwBOYA5gKbH1UCWAxmAMrMBu792AA4swAFwCeg+qnoAPQdVFjJ9MAHFGzdtyp82A4WAC8YAN4BqANoBbeqIAWcUgDkAhrYBcYAM6jWxWgBdLwAKQVcqd28vV2JxAEpjAD4wAAUqOGsWb3oAHljxJIBfdEwuTNVCURYYFgllKW8xODFI4m9KKmsxe1VsVIBJChI2arhiMBZiURbvCocp2h7XJWsVtl6mgGs4V1QJKTAAJTtCKmIAFRVcgDEvG5Gx4hSTABIAYVcYGFzcgDUkiEQgA6UERWjRMAFRJGFJ-GFwgA0YBuSX2KhwVFohFs0yuUlu90eLHGLzAHy+P1y2EBIXBXmwCKhcSZ2GRqPRhwAsnZHKR8XkhCwvBomKw2Do9AYWMieQ4nF5fP5aGTXgBRGD0XGiAXU4Sy3lONGc1QXNodajWIUXODvcZ+ODfZjGMC5OV8oWA1xed1OIUI1BgMBhCJRBlYnGMHXXX2kT3Iwg5KheYg4vDMZEzLaMRV+RZMk6iM6XGOGuPCY1lBZNbI9VQHev2FZQnyLTVgWzy8hTFtse0ZJ00TrMnCDHyOQgwbvWQSa7UyeSKBp9YSxu3TAeaqi6oUizTiyX8IUGru55Wqz7fXJm2IWrrW239x1bk98nf6sCxpKVrDVyZNBx6wxBxm1cHxeH4AByJo4B4ZhKTAPsN2fZ1vAnKdJhnOcozEVwtkWSZphaVw2D7EglAQzs+RrCY6iafoBgXBQqCUBscGEdcHUHd9hXUfdtAg-RPRdV4AHk8AAKy5VxBD1GUwBvdpOitYQbU4zdmGNINtLAdBA1ABS1U4C5OGQLBAx03SqzaZSCMA5cmgQXoJkA8QwGIOAlB7WIwDgST6FGMAEGoLYmigKZ6FBYETQU+hfFjABGF06TPfNkjSDIshyXJU2sdMqDRNiLji0RYwAJmS713LTZgmXSTJsjyJVFmNIFXATJNkXCLpvDqzLGuBKg4sdOCQgS+IvApK9FLvFSWDUp9B2RYr4rLBKkniABuMAyjgLYwAAQlQNqOozMBuusXr0vqrLIqGuYYFGyDXEgibyUvH4ZuUh91JQqhlpK8qNu23atiO7SMCwPAqiC5y6zciJVAQSJBCkbsJh8vyJIC1jejc0gWg8pRgqoLYouioqSqFF1TAAHws8xREBstsFCKrmoCPqGuy3L8qSREGaZ1auwAIVCPAUxqqgudu3IOZVVBaZKSGwDkKRRnocg-xmIKQuO0wLKF0qWbZ1KAlO-7ztDS6ZYG+6RvoMb4mRMo7Unch0xbeWAH5fb9-3vcN5nRfFyW8rOxMzu6qJbZyQbhsex3nteoMyjIjDPbA3nmADwOigZDjFq3XUVtET14iAA) | non_test | example from docs for objmap broken objmap mixes up return values when mapping functions by mixes up i mean that i get errors showing that flow is considering the union of all return types collectively for each function individually expected only errors on line and showing usage this is the case with actual using version the following errors are displayed in addition to and a true cannot return true because string is incompatible with boolean references b foo a true b foo cannot return foo because boolean is incompatible with string references a true b foo impact anyone wanting to map an object type containing functions to a transformed set of functions will be affected i discovered this while making types to transform from types for our api to backend types for our controllers which are basically the same as the api types but with additional parameters | 0 |
102,298 | 8,824,191,626 | IssuesEvent | 2019-01-02 16:11:27 | elastic/kibana | https://api.github.com/repos/elastic/kibana | closed | Failing test: UI Functional Tests.test/functional/apps/visualize/_pie_chart·js - visualize app pie chart other bucket should apply correct filter on other bucket by clicking on a legend | :KibanaApp blocker failed-test v6.6.0 | A test failed on a tracked branch
```
{ [POST http://localhost:9515/session/845af3a09d1f44c34132155bc27aa549/execute / {"script":"return arguments[0].getAttribute(arguments[1]);","args":[{"ELEMENT":"0.22915362292940733-37"},"data-label"]}] stale element reference: element is not attached to the page document
(Session info: headless chrome=70.0.3538.110)
(Driver info: chromedriver=2.42.591071 (0b695ff80972cc1a65a5cd643186d2ae582cd4ac),platform=Linux 4.9.0-8-amd64 x86_64)
at Server._post (test/functional/services/remote/verbose_remote_logging.js:34:21)
at runRequest (node_modules/leadfoot/Session.js:92:40)
at getFinalValue (node_modules/dojo/_debug/Promise.ts:462:22)
at node_modules/dojo/_debug/Promise.ts:478:11
at node_modules/dojo/_debug/Promise.ts:393:16
at runCallbacks (node_modules/dojo/_debug/Promise.ts:11:12)
at node_modules/dojo/_debug/Promise.ts:317:5
at run (node_modules/dojo/_debug/Promise.ts:237:8)
at node_modules/dojo/_debug/nextTick.ts:44:4
at _combinedTickCallback (internal/process/next_tick.js:132:7)
at process._tickCallback (internal/process/next_tick.js:181:9)
name: 'StaleElementReference',
message: '[POST http://localhost:9515/session/845af3a09d1f44c34132155bc27aa549/execute / {"script":"return arguments[0].getAttribute(arguments[1]);","args":[{"ELEMENT":"0.22915362292940733-37"},"data-label"]}] stale element reference: element is not attached to the page document\n (Session info: headless chrome=70.0.3538.110)\n (Driver info: chromedriver=2.42.591071 (0b695ff80972cc1a65a5cd643186d2ae582cd4ac),platform=Linux 4.9.0-8-amd64 x86_64)',
status: 10,
detail:
{ message: 'stale element reference: element is not attached to the page document\n (Session info: headless chrome=70.0.3538.110)\n (Driver info: chromedriver=2.42.591071 (0b695ff80972cc1a65a5cd643186d2ae582cd4ac),platform=Linux 4.9.0-8-amd64 x86_64)' },
request:
{ url: 'http://localhost:9515/session/845af3a09d1f44c34132155bc27aa549/execute',
method: 'POST',
data:
{ script: 'return arguments[0].getAttribute(arguments[1]);',
args: [Array] } },
response:
{ data: <Buffer 7b 22 73 65 73 73 69 6f 6e 49 64 22 3a 22 38 34 35 61 66 33 61 30 39 64 31 66 34 34 63 33 34 31 33 32 31 35 35 62 63 32 37 61 61 35 34 39 22 2c 22 73 ... >,
getHeader: [Function: getHeader],
requestOptions:
{ followRedirects: false,
handleAs: 'text',
headers: [Object],
method: 'POST',
data: '{"script":"return arguments[0].getAttribute(arguments[1]);","args":[{"ELEMENT":"0.22915362292940733-37"},"data-label"]}' },
statusCode: 200,
url: 'http://localhost:9515/session/845af3a09d1f44c34132155bc27aa549/execute',
nativeResponse:
IncomingMessage {
_readableState: [Object],
readable: false,
domain: null,
_events: [Object],
_eventsCount: 2,
_maxListeners: undefined,
socket: [Object],
connection: [Object],
httpVersionMajor: 1,
httpVersionMinor: 1,
httpVersion: '1.1',
complete: true,
headers: [Object],
rawHeaders: [Array],
trailers: {},
rawTrailers: [],
aborted: false,
upgrade: false,
url: '',
method: null,
statusCode: 200,
statusMessage: 'OK',
client: [Object],
_consuming: true,
_dumped: false,
req: [Object],
read: [Function] } } }
```
First failure: [Jenkins Build](https://kibana-ci.elastic.co/job/elastic+kibana+master/JOB=kibana-ciGroup11,node=immutable/140/)
<!-- kibanaCiData = {"failed-test":{"test.class":"UI Functional Tests.test/functional/apps/visualize/_pie_chart·js","test.name":"visualize app pie chart other bucket should apply correct filter on other bucket by clicking on a legend","test.failCount":1}} --> | 1.0 | Failing test: UI Functional Tests.test/functional/apps/visualize/_pie_chart·js - visualize app pie chart other bucket should apply correct filter on other bucket by clicking on a legend - A test failed on a tracked branch
```
{ [POST http://localhost:9515/session/845af3a09d1f44c34132155bc27aa549/execute / {"script":"return arguments[0].getAttribute(arguments[1]);","args":[{"ELEMENT":"0.22915362292940733-37"},"data-label"]}] stale element reference: element is not attached to the page document
(Session info: headless chrome=70.0.3538.110)
(Driver info: chromedriver=2.42.591071 (0b695ff80972cc1a65a5cd643186d2ae582cd4ac),platform=Linux 4.9.0-8-amd64 x86_64)
at Server._post (test/functional/services/remote/verbose_remote_logging.js:34:21)
at runRequest (node_modules/leadfoot/Session.js:92:40)
at getFinalValue (node_modules/dojo/_debug/Promise.ts:462:22)
at node_modules/dojo/_debug/Promise.ts:478:11
at node_modules/dojo/_debug/Promise.ts:393:16
at runCallbacks (node_modules/dojo/_debug/Promise.ts:11:12)
at node_modules/dojo/_debug/Promise.ts:317:5
at run (node_modules/dojo/_debug/Promise.ts:237:8)
at node_modules/dojo/_debug/nextTick.ts:44:4
at _combinedTickCallback (internal/process/next_tick.js:132:7)
at process._tickCallback (internal/process/next_tick.js:181:9)
name: 'StaleElementReference',
message: '[POST http://localhost:9515/session/845af3a09d1f44c34132155bc27aa549/execute / {"script":"return arguments[0].getAttribute(arguments[1]);","args":[{"ELEMENT":"0.22915362292940733-37"},"data-label"]}] stale element reference: element is not attached to the page document\n (Session info: headless chrome=70.0.3538.110)\n (Driver info: chromedriver=2.42.591071 (0b695ff80972cc1a65a5cd643186d2ae582cd4ac),platform=Linux 4.9.0-8-amd64 x86_64)',
status: 10,
detail:
{ message: 'stale element reference: element is not attached to the page document\n (Session info: headless chrome=70.0.3538.110)\n (Driver info: chromedriver=2.42.591071 (0b695ff80972cc1a65a5cd643186d2ae582cd4ac),platform=Linux 4.9.0-8-amd64 x86_64)' },
request:
{ url: 'http://localhost:9515/session/845af3a09d1f44c34132155bc27aa549/execute',
method: 'POST',
data:
{ script: 'return arguments[0].getAttribute(arguments[1]);',
args: [Array] } },
response:
{ data: <Buffer 7b 22 73 65 73 73 69 6f 6e 49 64 22 3a 22 38 34 35 61 66 33 61 30 39 64 31 66 34 34 63 33 34 31 33 32 31 35 35 62 63 32 37 61 61 35 34 39 22 2c 22 73 ... >,
getHeader: [Function: getHeader],
requestOptions:
{ followRedirects: false,
handleAs: 'text',
headers: [Object],
method: 'POST',
data: '{"script":"return arguments[0].getAttribute(arguments[1]);","args":[{"ELEMENT":"0.22915362292940733-37"},"data-label"]}' },
statusCode: 200,
url: 'http://localhost:9515/session/845af3a09d1f44c34132155bc27aa549/execute',
nativeResponse:
IncomingMessage {
_readableState: [Object],
readable: false,
domain: null,
_events: [Object],
_eventsCount: 2,
_maxListeners: undefined,
socket: [Object],
connection: [Object],
httpVersionMajor: 1,
httpVersionMinor: 1,
httpVersion: '1.1',
complete: true,
headers: [Object],
rawHeaders: [Array],
trailers: {},
rawTrailers: [],
aborted: false,
upgrade: false,
url: '',
method: null,
statusCode: 200,
statusMessage: 'OK',
client: [Object],
_consuming: true,
_dumped: false,
req: [Object],
read: [Function] } } }
```
First failure: [Jenkins Build](https://kibana-ci.elastic.co/job/elastic+kibana+master/JOB=kibana-ciGroup11,node=immutable/140/)
<!-- kibanaCiData = {"failed-test":{"test.class":"UI Functional Tests.test/functional/apps/visualize/_pie_chart·js","test.name":"visualize app pie chart other bucket should apply correct filter on other bucket by clicking on a legend","test.failCount":1}} --> | test | failing test ui functional tests test functional apps visualize pie chart·js visualize app pie chart other bucket should apply correct filter on other bucket by clicking on a legend a test failed on a tracked branch getattribute arguments args stale element reference element is not attached to the page document session info headless chrome driver info chromedriver platform linux at server post test functional services remote verbose remote logging js at runrequest node modules leadfoot session js at getfinalvalue node modules dojo debug promise ts at node modules dojo debug promise ts at node modules dojo debug promise ts at runcallbacks node modules dojo debug promise ts at node modules dojo debug promise ts at run node modules dojo debug promise ts at node modules dojo debug nexttick ts at combinedtickcallback internal process next tick js at process tickcallback internal process next tick js name staleelementreference message getattribute arguments args stale element reference element is not attached to the page document n session info headless chrome n driver info chromedriver platform linux status detail message stale element reference element is not attached to the page document n session info headless chrome n driver info chromedriver platform linux request url method post data script return arguments getattribute arguments args response data getheader requestoptions followredirects false handleas text headers method post data script return arguments getattribute arguments args statuscode url nativeresponse incomingmessage readablestate readable false domain null events eventscount maxlisteners undefined socket connection httpversionmajor httpversionminor httpversion complete true headers rawheaders trailers rawtrailers aborted false upgrade false url method null statuscode statusmessage ok client consuming true dumped false req read first failure | 1 |
103,550 | 8,921,712,518 | IssuesEvent | 2019-01-21 10:50:05 | jordan528/rbac | https://api.github.com/repos/jordan528/rbac | closed | RBAC testing : ApiV1UsersPersonalSignUpPostRolePmDisallowedRbac | RBAC testing | Project : RBAC testing
Job : Default
Env : Default
Category : null
Tags : null
Severity : null
Region : local
Result : fail
Status Code : 500
Headers : {}
Endpoint : http://localhost:8090/api/v1/users/personal-sign-up
Request :
{
"accountNonExpired" : false,
"accountNonLocked" : false,
"company" : "Aufderhar and Sons",
"createdBy" : "",
"createdDate" : "",
"credentialsNonExpired" : false,
"email" : "[email protected]",
"enabled" : false,
"id" : "",
"inactive" : false,
"jobTitle" : "Senior Hospitality Representative",
"location" : "2nX8UsUz",
"modifiedBy" : "",
"modifiedDate" : "",
"name" : "2nX8UsUz",
"password" : "2nX8UsUz",
"username" : "josefina.dare",
"version" : ""
}
Response :
I/O error on POST request for "http://localhost:8090/api/v1/users/personal-sign-up": Connect to localhost:8090 [localhost/127.0.0.1, localhost/0:0:0:0:0:0:0:1] failed: Connection refused: connect; nested exception is org.apache.http.conn.HttpHostConnectException: Connect to localhost:8090 [localhost/127.0.0.1, localhost/0:0:0:0:0:0:0:1] failed: Connection refused: connect
Logs :
Assertion [@StatusCode == 401 OR @StatusCode == 403] resolved-to [500 == 401 OR 500 == 403] result [Failed]
--- FX Bot --- | 1.0 | RBAC testing : ApiV1UsersPersonalSignUpPostRolePmDisallowedRbac - Project : RBAC testing
Job : Default
Env : Default
Category : null
Tags : null
Severity : null
Region : local
Result : fail
Status Code : 500
Headers : {}
Endpoint : http://localhost:8090/api/v1/users/personal-sign-up
Request :
{
"accountNonExpired" : false,
"accountNonLocked" : false,
"company" : "Aufderhar and Sons",
"createdBy" : "",
"createdDate" : "",
"credentialsNonExpired" : false,
"email" : "[email protected]",
"enabled" : false,
"id" : "",
"inactive" : false,
"jobTitle" : "Senior Hospitality Representative",
"location" : "2nX8UsUz",
"modifiedBy" : "",
"modifiedDate" : "",
"name" : "2nX8UsUz",
"password" : "2nX8UsUz",
"username" : "josefina.dare",
"version" : ""
}
Response :
I/O error on POST request for "http://localhost:8090/api/v1/users/personal-sign-up": Connect to localhost:8090 [localhost/127.0.0.1, localhost/0:0:0:0:0:0:0:1] failed: Connection refused: connect; nested exception is org.apache.http.conn.HttpHostConnectException: Connect to localhost:8090 [localhost/127.0.0.1, localhost/0:0:0:0:0:0:0:1] failed: Connection refused: connect
Logs :
Assertion [@StatusCode == 401 OR @StatusCode == 403] resolved-to [500 == 401 OR 500 == 403] result [Failed]
--- FX Bot --- | test | rbac testing project rbac testing job default env default category null tags null severity null region local result fail status code headers endpoint request accountnonexpired false accountnonlocked false company aufderhar and sons createdby createddate credentialsnonexpired false email wendy berge hotmail com enabled false id inactive false jobtitle senior hospitality representative location modifiedby modifieddate name password username josefina dare version response i o error on post request for connect to localhost failed connection refused connect nested exception is org apache http conn httphostconnectexception connect to localhost failed connection refused connect logs assertion resolved to result fx bot | 1 |
28,928 | 4,446,319,412 | IssuesEvent | 2016-08-20 16:05:38 | PokemonGoF/PokemonGo-Bot | https://api.github.com/repos/PokemonGoF/PokemonGo-Bot | closed | [ERROR] [u"KeyError: 'new_catch_rate'" | Bug Help to Test |
### Expected Behavior
Run smoothly, snipe and return, catch etc
### Actual Behavior
UnicodeDecodeError: 'ascii' codec can't decode byte 0x9c in position 1: ordinal not in range(128)
2016-08-13 12:44:27,947 [sentry.errors.uncaught] [ERROR] [u"KeyError: 'new_catch_rate'", u' File "pokecli.py", line 502, in <module>', u' File "pokecli.py", line 133, in main']
### config.json
"tasks": [
{
"type": "HandleSoftBan"
},
{
"type": "CollectLevelUpReward"
},
{
"type": "IncubateEggs",
"config": {
"longer_eggs_first": true
}
},
{
"type": "TransferPokemon"
},
{
"type": "EvolvePokemon",
"config": {
"evolve_all": "NONE",
"evolve_cp_min": 300,
"evolve_speed": 20,
"use_lucky_egg": false
}
},
{
"type": "RecycleItems",
"config": {
"item_filter": {
"Pokeball": { "keep" : 100 },
"Potion": { "keep" : 10 },
"Super Potion": { "keep" : 20 },
"Hyper Potion": { "keep" : 30 },
"Revive": { "keep" : 30 },
"Razz Berry": { "keep" : 100 }
}
}
},
{
"type": "CatchVisiblePokemon"
},
{
"type": "CatchLuredPokemon"
},
{
"type": "SpinFort"
},
{
"type": "MoveToMapPokemon",
"config": {
"address": "http://localhost:5000",
"max_distance": 150000,
"min_time": 60,
"prioritize_vips": true,
"snipe": true,
"update_map": true,
"mode": "priority",
"catch": {
"==========Legendary==========": 0,
"Dragonite": 1000,
"Dragonair": 1000,
"Aerodactyl": 1000,
"Snorlax": 1000,
"Articuno": 1000,
"Zapdos": 1000,
"Moltres": 1000,
"Dratini": 1000,
"Mewtwo": 1000,
"Mew": 1000,
"==========Region Locked==========": 0,
"Farfetch'd": 1000,
"Kangaskhan": 1000,
"Mr. Mime": 1000,
"Tauros": 1000,
"==========Very Rare==========": 0,
"Lapras": 900,
"Electabuzz": 900,
"Magmar": 900,
"Ditto": 900,
"==========Starters==========": 0,
"Bulbasaur": 400,
"Ivysaur": 600,
"Venusaur": 1300,
"Charmander": 400,
"Charmeleon": 600,
"Charizard": 1300,
"Squirtle": 400,
"Wartortle": 600,
"Blastoise": 1300,
"Pikachu": 600,
"Raichu": 1000,
"==========Semi Rare==========": 0,
"Porygon": 200,
"Scyther": 200,
"Jynx": 200,
"==========Uncommon==========": 0,
"Omanyte": 150,
"Omastar": 500,
"Seel": 300,
"Dewgong": 500,
"Grimer": 200,
"Muk": 500,
"Shellder": 200,
"Cloyster": 500,
"Gastly": 200,
"Haunter": 500,
"Gengar": 1000,
"Onix": 600,
"Drowzee": 1000,
"Hypno": 600,
"Vulpix": 200,
"Ninetales": 600,
"Paras": 100,
"Parasect": 500,
"Growlithe": 200,
"Arcanine": 700,
"Tentacool": 200,
"Tentacruel": 500,
"Mankey": 150,
"Primeape": 500,
"Clefairy": 150,
"Clefable": 500,
"Jigglypuff": 150,
"Wigglytuff": 500,
"Venonat": 100,
"Venomoth": 500,
"Diglett": 200,
"Dugtrio": 500,
"Meowth": 250,
"Persian": 500,
"Psyduck": 150,
"Golduck": 500,
"Geodude": 100,
"Graveler": 500,
"Golem": 800,
"Eevee": 200,
"Vaporeon": 800,
"Jolteon": 800,
"Flareon": 800,
"Kabuto": 150,
"Kabutops": 500,
"Magikarp": 150,
"Gyarados": 800,
"Pinsir": 150,
"Ponyta": 200,
"Rapidash": 500,
"Slowpoke": 200,
"Slowbro": 500,
"Magnemite": 250,
"Magneton": 500,
"Krabby": 100,
"Kingler": 500,
"Voltorb": 200,
"Electrode": 500,
"Exeggcute": 250,
"Exeggcutor": 500,
"Cubone": 300,
"Marowak": 800,
"Hitmonlee": 400,
"Hitmonchan": 400,
"Lickitung": 500,
"Koffing": 200,
"Weezing": 500,
"Rhyhorn": 200,
"Rhydon": 500,
"Chansey": 800,
"Tangela": 300,
"Horsea": 200,
"Seadra": 600,
"Goldeen": 150,
"Seaking": 500,
"Staryu": 200,
"Starmie": 800,
"==========T1 Evolvers==========": 0,
"Caterpie": 10,
"Metapod": 10,
"Butterfree": 500,
"Weedle": 10,
"Kakuna": 10,
"Beedrill": 500,
"Pidgey": 10,
"Pidgeotto": 10,
"Pidgeot": 300,
"==========T2 Evolvers==========": 0,
"Nidoran F": 10,
"Nidorina": 10,
"Nidoqueen": 10,
"Nidoran M": 10,
"Nidorino": 10,
"Nidoking": 10,
"Oddish": 100,
"Gloom": 200,
"Vileplume": 600,
"Poliwag": 200,
"Poliwhirl": 400,
"Poliwrath": 800,
"Abra": 300,
"Kadabra": 600,
"Alakazam": 800,
"Machop": 150,
"Machoke": 400,
"Machamp": 800,
"Bellsprout": 100,
"Weepinbell": 400,
"Victreebel": 800,
"==========Trash==========": 0,
"Rattata": 10,
"Raticate": 10,
"Spearow": 10,
"Fearow": 10,
"Ekans": 10,
"Arbok": 10,
"Sandshrew": 10,
"Sandslash": 10,
"Zubat": 10,
"Golbat": 10,
"Doduo": 10,
"Dodrio": 10
}
}
},
{
"type": "MoveToFort"
},
{
"type": "FollowSpiral"
}
],
"map_object_cache_time": 5,
"forts": {
"avoid_circles": true,
"max_circle_size": 50
},
"websocket_server": false,
"walk": 4.16,
"action_wait_min": 1,
"action_wait_max": 4,
"debug": false,
"test": false,
"health_record": false,
"location_cache": true,
"distance_unit": "km",
"reconnecting_timeout": 15,
"evolve_captured": "NONE",
"catch_randomize_reticle_factor": 1.0,
"catch_randomize_spin_factor": 1.0,
"catch": {
"any": {"catch_above_cp": 0, "catch_above_iv": 0, "logic": "or"},
"// Example of always catching Rattata:": {},
"// Rattata": { "always_catch" : true }
},
"release": {
"any": {"release_below_cp": 750, "release_below_iv": 0.75, "logic": "and"},
"// Example of always releasing Rattata:": {},
"// Rattata": {"always_release": true},
"// Example of keeping 3 stronger (based on CP) Pidgey:": {},
"// Pidgey": {"keep_best_cp": 3},
"// Example of keeping 2 stronger (based on IV) Zubat:": {},
"// Zubat": {"keep_best_iv": 2},
"// Also, it is working with any": {},
"// any": {"keep_best_iv": 3},
"// Example of keeping the 2 strongest (based on CP) and 3 best (based on IV) Zubat:": {},
"// Zubat": {"keep_best_cp": 2, "keep_best_iv": 3}
},
"vips" : {
"Any pokemon put here directly force to use Berry & Best Ball to capture, to secure the capture rate!": {},
"any": {"catch_above_cp": 1200, "catch_above_iv": 0.9, "logic": "or" },
"Lapras": {},
"Moltres": {},
"Zapdos": {},
"Articuno": {},
"Snorlax": {},
"Dragonite": {},
"Dragonair": {},
"Exeggutor": {},
"Blastoise": {},
"Venasaur": {},
"Charizard": {},
"// S-Tier pokemons (if pokemon can be evolved into tier, list the representative)": {},
"Mewtwo": {},
"Dragonite": {},
"Snorlax": {},
"// Mew evolves to Mewtwo": {},
"Mew": {},
"Arcanine": {},
"Vaporeon": {},
"Gyarados": {},
"Exeggutor": {},
"Muk": {},
"Weezing": {},
"Flareon": {}
### Steps to Reproduce
python pokecli.py
**Occurred straight after this**
2016-08-13 12:44:24,265 [PokemonCatchWorker] [INFO] [pokemon_appeared] A wild Snorlax appeared! [CP 1676] [Potential 0.91] [S/A/D 15/13/13]
2016-08-13 12:44:27,312 [PokemonCatchWorker] [INFO] [vip_pokemon] This is a VIP pokemon. Catch!!!
### Other Information
OS: Windows 10
Branch: dev
Git Commit: (ae0ae815089bf1e3b17497b476d524a0468949e2)
Python Version: (python 2.7)
| 1.0 | [ERROR] [u"KeyError: 'new_catch_rate'" -
### Expected Behavior
Run smoothly, snipe and return, catch etc
### Actual Behavior
UnicodeDecodeError: 'ascii' codec can't decode byte 0x9c in position 1: ordinal not in range(128)
2016-08-13 12:44:27,947 [sentry.errors.uncaught] [ERROR] [u"KeyError: 'new_catch_rate'", u' File "pokecli.py", line 502, in <module>', u' File "pokecli.py", line 133, in main']
### config.json
"tasks": [
{
"type": "HandleSoftBan"
},
{
"type": "CollectLevelUpReward"
},
{
"type": "IncubateEggs",
"config": {
"longer_eggs_first": true
}
},
{
"type": "TransferPokemon"
},
{
"type": "EvolvePokemon",
"config": {
"evolve_all": "NONE",
"evolve_cp_min": 300,
"evolve_speed": 20,
"use_lucky_egg": false
}
},
{
"type": "RecycleItems",
"config": {
"item_filter": {
"Pokeball": { "keep" : 100 },
"Potion": { "keep" : 10 },
"Super Potion": { "keep" : 20 },
"Hyper Potion": { "keep" : 30 },
"Revive": { "keep" : 30 },
"Razz Berry": { "keep" : 100 }
}
}
},
{
"type": "CatchVisiblePokemon"
},
{
"type": "CatchLuredPokemon"
},
{
"type": "SpinFort"
},
{
"type": "MoveToMapPokemon",
"config": {
"address": "http://localhost:5000",
"max_distance": 150000,
"min_time": 60,
"prioritize_vips": true,
"snipe": true,
"update_map": true,
"mode": "priority",
"catch": {
"==========Legendary==========": 0,
"Dragonite": 1000,
"Dragonair": 1000,
"Aerodactyl": 1000,
"Snorlax": 1000,
"Articuno": 1000,
"Zapdos": 1000,
"Moltres": 1000,
"Dratini": 1000,
"Mewtwo": 1000,
"Mew": 1000,
"==========Region Locked==========": 0,
"Farfetch'd": 1000,
"Kangaskhan": 1000,
"Mr. Mime": 1000,
"Tauros": 1000,
"==========Very Rare==========": 0,
"Lapras": 900,
"Electabuzz": 900,
"Magmar": 900,
"Ditto": 900,
"==========Starters==========": 0,
"Bulbasaur": 400,
"Ivysaur": 600,
"Venusaur": 1300,
"Charmander": 400,
"Charmeleon": 600,
"Charizard": 1300,
"Squirtle": 400,
"Wartortle": 600,
"Blastoise": 1300,
"Pikachu": 600,
"Raichu": 1000,
"==========Semi Rare==========": 0,
"Porygon": 200,
"Scyther": 200,
"Jynx": 200,
"==========Uncommon==========": 0,
"Omanyte": 150,
"Omastar": 500,
"Seel": 300,
"Dewgong": 500,
"Grimer": 200,
"Muk": 500,
"Shellder": 200,
"Cloyster": 500,
"Gastly": 200,
"Haunter": 500,
"Gengar": 1000,
"Onix": 600,
"Drowzee": 1000,
"Hypno": 600,
"Vulpix": 200,
"Ninetales": 600,
"Paras": 100,
"Parasect": 500,
"Growlithe": 200,
"Arcanine": 700,
"Tentacool": 200,
"Tentacruel": 500,
"Mankey": 150,
"Primeape": 500,
"Clefairy": 150,
"Clefable": 500,
"Jigglypuff": 150,
"Wigglytuff": 500,
"Venonat": 100,
"Venomoth": 500,
"Diglett": 200,
"Dugtrio": 500,
"Meowth": 250,
"Persian": 500,
"Psyduck": 150,
"Golduck": 500,
"Geodude": 100,
"Graveler": 500,
"Golem": 800,
"Eevee": 200,
"Vaporeon": 800,
"Jolteon": 800,
"Flareon": 800,
"Kabuto": 150,
"Kabutops": 500,
"Magikarp": 150,
"Gyarados": 800,
"Pinsir": 150,
"Ponyta": 200,
"Rapidash": 500,
"Slowpoke": 200,
"Slowbro": 500,
"Magnemite": 250,
"Magneton": 500,
"Krabby": 100,
"Kingler": 500,
"Voltorb": 200,
"Electrode": 500,
"Exeggcute": 250,
"Exeggcutor": 500,
"Cubone": 300,
"Marowak": 800,
"Hitmonlee": 400,
"Hitmonchan": 400,
"Lickitung": 500,
"Koffing": 200,
"Weezing": 500,
"Rhyhorn": 200,
"Rhydon": 500,
"Chansey": 800,
"Tangela": 300,
"Horsea": 200,
"Seadra": 600,
"Goldeen": 150,
"Seaking": 500,
"Staryu": 200,
"Starmie": 800,
"==========T1 Evolvers==========": 0,
"Caterpie": 10,
"Metapod": 10,
"Butterfree": 500,
"Weedle": 10,
"Kakuna": 10,
"Beedrill": 500,
"Pidgey": 10,
"Pidgeotto": 10,
"Pidgeot": 300,
"==========T2 Evolvers==========": 0,
"Nidoran F": 10,
"Nidorina": 10,
"Nidoqueen": 10,
"Nidoran M": 10,
"Nidorino": 10,
"Nidoking": 10,
"Oddish": 100,
"Gloom": 200,
"Vileplume": 600,
"Poliwag": 200,
"Poliwhirl": 400,
"Poliwrath": 800,
"Abra": 300,
"Kadabra": 600,
"Alakazam": 800,
"Machop": 150,
"Machoke": 400,
"Machamp": 800,
"Bellsprout": 100,
"Weepinbell": 400,
"Victreebel": 800,
"==========Trash==========": 0,
"Rattata": 10,
"Raticate": 10,
"Spearow": 10,
"Fearow": 10,
"Ekans": 10,
"Arbok": 10,
"Sandshrew": 10,
"Sandslash": 10,
"Zubat": 10,
"Golbat": 10,
"Doduo": 10,
"Dodrio": 10
}
}
},
{
"type": "MoveToFort"
},
{
"type": "FollowSpiral"
}
],
"map_object_cache_time": 5,
"forts": {
"avoid_circles": true,
"max_circle_size": 50
},
"websocket_server": false,
"walk": 4.16,
"action_wait_min": 1,
"action_wait_max": 4,
"debug": false,
"test": false,
"health_record": false,
"location_cache": true,
"distance_unit": "km",
"reconnecting_timeout": 15,
"evolve_captured": "NONE",
"catch_randomize_reticle_factor": 1.0,
"catch_randomize_spin_factor": 1.0,
"catch": {
"any": {"catch_above_cp": 0, "catch_above_iv": 0, "logic": "or"},
"// Example of always catching Rattata:": {},
"// Rattata": { "always_catch" : true }
},
"release": {
"any": {"release_below_cp": 750, "release_below_iv": 0.75, "logic": "and"},
"// Example of always releasing Rattata:": {},
"// Rattata": {"always_release": true},
"// Example of keeping 3 stronger (based on CP) Pidgey:": {},
"// Pidgey": {"keep_best_cp": 3},
"// Example of keeping 2 stronger (based on IV) Zubat:": {},
"// Zubat": {"keep_best_iv": 2},
"// Also, it is working with any": {},
"// any": {"keep_best_iv": 3},
"// Example of keeping the 2 strongest (based on CP) and 3 best (based on IV) Zubat:": {},
"// Zubat": {"keep_best_cp": 2, "keep_best_iv": 3}
},
"vips" : {
"Any pokemon put here directly force to use Berry & Best Ball to capture, to secure the capture rate!": {},
"any": {"catch_above_cp": 1200, "catch_above_iv": 0.9, "logic": "or" },
"Lapras": {},
"Moltres": {},
"Zapdos": {},
"Articuno": {},
"Snorlax": {},
"Dragonite": {},
"Dragonair": {},
"Exeggutor": {},
"Blastoise": {},
"Venasaur": {},
"Charizard": {},
"// S-Tier pokemons (if pokemon can be evolved into tier, list the representative)": {},
"Mewtwo": {},
"Dragonite": {},
"Snorlax": {},
"// Mew evolves to Mewtwo": {},
"Mew": {},
"Arcanine": {},
"Vaporeon": {},
"Gyarados": {},
"Exeggutor": {},
"Muk": {},
"Weezing": {},
"Flareon": {}
### Steps to Reproduce
python pokecli.py
**Occurred straight after this**
2016-08-13 12:44:24,265 [PokemonCatchWorker] [INFO] [pokemon_appeared] A wild Snorlax appeared! [CP 1676] [Potential 0.91] [S/A/D 15/13/13]
2016-08-13 12:44:27,312 [PokemonCatchWorker] [INFO] [vip_pokemon] This is a VIP pokemon. Catch!!!
### Other Information
OS: Windows 10
Branch: dev
Git Commit: (ae0ae815089bf1e3b17497b476d524a0468949e2)
Python Version: (python 2.7)
| test | u keyerror new catch rate expected behavior run smoothly snipe and return catch etc actual behavior unicodedecodeerror ascii codec can t decode byte in position ordinal not in range config json tasks type handlesoftban type collectlevelupreward type incubateeggs config longer eggs first true type transferpokemon type evolvepokemon config evolve all none evolve cp min evolve speed use lucky egg false type recycleitems config item filter pokeball keep potion keep super potion keep hyper potion keep revive keep razz berry keep type catchvisiblepokemon type catchluredpokemon type spinfort type movetomappokemon config address max distance min time prioritize vips true snipe true update map true mode priority catch legendary dragonite dragonair aerodactyl snorlax articuno zapdos moltres dratini mewtwo mew region locked farfetch d kangaskhan mr mime tauros very rare lapras electabuzz magmar ditto starters bulbasaur ivysaur venusaur charmander charmeleon charizard squirtle wartortle blastoise pikachu raichu semi rare porygon scyther jynx uncommon omanyte omastar seel dewgong grimer muk shellder cloyster gastly haunter gengar onix drowzee hypno vulpix ninetales paras parasect growlithe arcanine tentacool tentacruel mankey primeape clefairy clefable jigglypuff wigglytuff venonat venomoth diglett dugtrio meowth persian psyduck golduck geodude graveler golem eevee vaporeon jolteon flareon kabuto kabutops magikarp gyarados pinsir ponyta rapidash slowpoke slowbro magnemite magneton krabby kingler voltorb electrode exeggcute exeggcutor cubone marowak hitmonlee hitmonchan lickitung koffing weezing rhyhorn rhydon chansey tangela horsea seadra goldeen seaking staryu starmie evolvers caterpie metapod butterfree weedle kakuna beedrill pidgey pidgeotto pidgeot evolvers nidoran f nidorina nidoqueen nidoran m nidorino nidoking oddish gloom vileplume poliwag poliwhirl poliwrath abra kadabra alakazam machop machoke machamp bellsprout weepinbell victreebel trash rattata raticate spearow fearow ekans arbok sandshrew sandslash zubat golbat doduo dodrio type movetofort type followspiral map object cache time forts avoid circles true max circle size websocket server false walk action wait min action wait max debug false test false health record false location cache true distance unit km reconnecting timeout evolve captured none catch randomize reticle factor catch randomize spin factor catch any catch above cp catch above iv logic or example of always catching rattata rattata always catch true release any release below cp release below iv logic and example of always releasing rattata rattata always release true example of keeping stronger based on cp pidgey pidgey keep best cp example of keeping stronger based on iv zubat zubat keep best iv also it is working with any any keep best iv example of keeping the strongest based on cp and best based on iv zubat zubat keep best cp keep best iv vips any pokemon put here directly force to use berry best ball to capture to secure the capture rate any catch above cp catch above iv logic or lapras moltres zapdos articuno snorlax dragonite dragonair exeggutor blastoise venasaur charizard s tier pokemons if pokemon can be evolved into tier list the representative mewtwo dragonite snorlax mew evolves to mewtwo mew arcanine vaporeon gyarados exeggutor muk weezing flareon steps to reproduce python pokecli py occurred straight after this a wild snorlax appeared this is a vip pokemon catch other information os windows branch dev git commit python version python | 1 |
31,550 | 4,710,245,172 | IssuesEvent | 2016-10-14 09:28:26 | GeoSmartCity-CIP/gsc-datacatalogue | https://api.github.com/repos/GeoSmartCity-CIP/gsc-datacatalogue | closed | Response of Permissions web service, action: listperm | 2nd priority enhancement ready for testing | **Q**: The function that lists permissions for roles returns an array without wrapping it in a response object. This is handled in the application but is different from all other Web Services.
**A**: Ok
| 1.0 | Response of Permissions web service, action: listperm - **Q**: The function that lists permissions for roles returns an array without wrapping it in a response object. This is handled in the application but is different from all other Web Services.
**A**: Ok
| test | response of permissions web service action listperm q the function that lists permissions for roles returns an array without wrapping it in a response object this is handled in the application but is different from all other web services a ok | 1 |
369,594 | 10,915,213,060 | IssuesEvent | 2019-11-21 10:42:27 | OceanShare/OceanShare-iOS | https://api.github.com/repos/OceanShare/OceanShare-iOS | closed | Send user name in markers table | Priority: Medium Status: Abandoned Type: Optimization Type: Production | Send user name in the markers table instead of retrieving userid for every markers and duplicate requests. | 1.0 | Send user name in markers table - Send user name in the markers table instead of retrieving userid for every markers and duplicate requests. | non_test | send user name in markers table send user name in the markers table instead of retrieving userid for every markers and duplicate requests | 0 |
146,187 | 13,173,374,135 | IssuesEvent | 2020-08-11 20:11:47 | MLH-Fellowship/nodemaker | https://api.github.com/repos/MLH-Fellowship/nodemaker | closed | Single installation command for frontend and backend dependencies | DX backend documentation | Docs would need to be updated as well. | 1.0 | Single installation command for frontend and backend dependencies - Docs would need to be updated as well. | non_test | single installation command for frontend and backend dependencies docs would need to be updated as well | 0 |
176,289 | 13,633,786,480 | IssuesEvent | 2020-09-24 22:10:16 | JuliaEarth/GeoStats.jl | https://api.github.com/repos/JuliaEarth/GeoStats.jl | closed | More tests for local Kriging | tests | @exepulveda I've noticed the current tests for local Kriging use a greedy neighborhood (ball with radius 100 on 100x100 grid). Do you think you could add more tests to stress the recent improvements to the solver? | 1.0 | More tests for local Kriging - @exepulveda I've noticed the current tests for local Kriging use a greedy neighborhood (ball with radius 100 on 100x100 grid). Do you think you could add more tests to stress the recent improvements to the solver? | test | more tests for local kriging exepulveda i ve noticed the current tests for local kriging use a greedy neighborhood ball with radius on grid do you think you could add more tests to stress the recent improvements to the solver | 1 |
327,405 | 28,060,128,105 | IssuesEvent | 2023-03-29 12:06:23 | ethereum/solidity | https://api.github.com/repos/ethereum/solidity | closed | External test benchmarking extensions | testing :hammer: medium effort medium impact should have closed-due-inactivity stale | #12441 adds benchmarking functionality to our external tests. I have a lot of ideas for extra improvements and not all of them may be worth the effort so I'm creating this issue to discuss them.
Current ideas:
- [ ] **Compilation time benchmarking**. Including the compilation duration in the benchmark JSON.
- [ ] **Diff repo**. Currently you have to manually download and diff the results. We could instead have a repository where the `c_ext_benchmarks` job commits the JSON files. It would have branches corresponding to the main repo (including `develop`) and you could go there and easily view the diff with the base branch via Github UI.
- [x] **Script for calculating gas differences**. I chose the current JSON structure to be easily diffable but it might still not be as convenient as just seeing a straight difference between two gas values. We could have a script that takes two benchmarks and produces a JSON file with absolute and/or relative differences. (done in #12804)
- [x] Could also support producing a Markdown table. Might be easier to view and could be posted in a github comment. (done in #12804)
- [x] **Benchmark diff for PRs**. We could have a job that finds artifacts from a CI run on the base branch, calculates the diff with the current PR, creates a markdown table and posts it in the PR. (done in #12818, but without posting a comment in the PR)
- Might be too spammy unless we can do it in such a way that it's a single comment that gets automatically updated (like it works with coverage for example).
- [ ] **Dumping Standard JSON from external tests**. External tests are pretty heavy. To make reproducing problems locally easier, we could have the test extract the combined Standard JSON input that the framework uses for compilation and attach it as an artifact.
- [ ] **Dumping Yul from external tests**. The external tests can relatively easily extract the `--ir-optimized` output that might be useful to inspect the effect of our optimizer changes in more detail. It could be zipped into a single package and attached as an artifact.
- [ ] We could also store it in the diff repo.
- [ ] **Weekly benchmark summary**. A weekly job that runs `c_ext_benchmarks`, creates a short table from the summary JSON and posts it on gitter. For brevity the table would only list the output from one preset (the one with max optimization), not all 6.
- [ ] **Weekly benchmark diff**. The weekly summary job could use the CircleCI API to get a compiler binary from last week, get two benchmark outputs and post just the differences instead of absolute values. | 1.0 | External test benchmarking extensions - #12441 adds benchmarking functionality to our external tests. I have a lot of ideas for extra improvements and not all of them may be worth the effort so I'm creating this issue to discuss them.
Current ideas:
- [ ] **Compilation time benchmarking**. Including the compilation duration in the benchmark JSON.
- [ ] **Diff repo**. Currently you have to manually download and diff the results. We could instead have a repository where the `c_ext_benchmarks` job commits the JSON files. It would have branches corresponding to the main repo (including `develop`) and you could go there and easily view the diff with the base branch via Github UI.
- [x] **Script for calculating gas differences**. I chose the current JSON structure to be easily diffable but it might still not be as convenient as just seeing a straight difference between two gas values. We could have a script that takes two benchmarks and produces a JSON file with absolute and/or relative differences. (done in #12804)
- [x] Could also support producing a Markdown table. Might be easier to view and could be posted in a github comment. (done in #12804)
- [x] **Benchmark diff for PRs**. We could have a job that finds artifacts from a CI run on the base branch, calculates the diff with the current PR, creates a markdown table and posts it in the PR. (done in #12818, but without posting a comment in the PR)
- Might be too spammy unless we can do it in such a way that it's a single comment that gets automatically updated (like it works with coverage for example).
- [ ] **Dumping Standard JSON from external tests**. External tests are pretty heavy. To make reproducing problems locally easier, we could have the test extract the combined Standard JSON input that the framework uses for compilation and attach it as an artifact.
- [ ] **Dumping Yul from external tests**. The external tests can relatively easily extract the `--ir-optimized` output that might be useful to inspect the effect of our optimizer changes in more detail. It could be zipped into a single package and attached as an artifact.
- [ ] We could also store it in the diff repo.
- [ ] **Weekly benchmark summary**. A weekly job that runs `c_ext_benchmarks`, creates a short table from the summary JSON and posts it on gitter. For brevity the table would only list the output from one preset (the one with max optimization), not all 6.
- [ ] **Weekly benchmark diff**. The weekly summary job could use the CircleCI API to get a compiler binary from last week, get two benchmark outputs and post just the differences instead of absolute values. | test | external test benchmarking extensions adds benchmarking functionality to our external tests i have a lot of ideas for extra improvements and not all of them may be worth the effort so i m creating this issue to discuss them current ideas compilation time benchmarking including the compilation duration in the benchmark json diff repo currently you have to manually download and diff the results we could instead have a repository where the c ext benchmarks job commits the json files it would have branches corresponding to the main repo including develop and you could go there and easily view the diff with the base branch via github ui script for calculating gas differences i chose the current json structure to be easily diffable but it might still not be as convenient as just seeing a straight difference between two gas values we could have a script that takes two benchmarks and produces a json file with absolute and or relative differences done in could also support producing a markdown table might be easier to view and could be posted in a github comment done in benchmark diff for prs we could have a job that finds artifacts from a ci run on the base branch calculates the diff with the current pr creates a markdown table and posts it in the pr done in but without posting a comment in the pr might be too spammy unless we can do it in such a way that it s a single comment that gets automatically updated like it works with coverage for example dumping standard json from external tests external tests are pretty heavy to make reproducing problems locally easier we could have the test extract the combined standard json input that the framework uses for compilation and attach it as an artifact dumping yul from external tests the external tests can relatively easily extract the ir optimized output that might be useful to inspect the effect of our optimizer changes in more detail it could be zipped into a single package and attached as an artifact we could also store it in the diff repo weekly benchmark summary a weekly job that runs c ext benchmarks creates a short table from the summary json and posts it on gitter for brevity the table would only list the output from one preset the one with max optimization not all weekly benchmark diff the weekly summary job could use the circleci api to get a compiler binary from last week get two benchmark outputs and post just the differences instead of absolute values | 1 |
227,533 | 7,534,742,633 | IssuesEvent | 2018-04-16 09:02:53 | cs121-team-panda/coconut-interpreter-flask | https://api.github.com/repos/cs121-team-panda/coconut-interpreter-flask | closed | Measure run-time for each components. | High priority | Needed for Phase 2 presentations.
Progress: Green
Plans:
- [x] Measure the run-time for all coconut code from the tutorial website and put it in the table.
- [x] Measure the run-time on Heroku; try with small code and big code from the tutorial.
- [x] Measure the run-time on AWS; same as above. | 1.0 | Measure run-time for each components. - Needed for Phase 2 presentations.
Progress: Green
Plans:
- [x] Measure the run-time for all coconut code from the tutorial website and put it in the table.
- [x] Measure the run-time on Heroku; try with small code and big code from the tutorial.
- [x] Measure the run-time on AWS; same as above. | non_test | measure run time for each components needed for phase presentations progress green plans measure the run time for all coconut code from the tutorial website and put it in the table measure the run time on heroku try with small code and big code from the tutorial measure the run time on aws same as above | 0 |
271,344 | 23,596,515,293 | IssuesEvent | 2022-08-23 19:48:35 | xmos/sln_voice | https://api.github.com/repos/xmos/sln_voice | closed | Setup XVF3610 devkit w/ AVS to test with STLP application | size:S type:testing | It may just work.
See: https://www.xmos.ai/download/XVF3610-Quick-start-guide(1).pdf
- [ ] Documentation
Requires https://github.com/xmos/sln_avona/issues/31 | 1.0 | Setup XVF3610 devkit w/ AVS to test with STLP application - It may just work.
See: https://www.xmos.ai/download/XVF3610-Quick-start-guide(1).pdf
- [ ] Documentation
Requires https://github.com/xmos/sln_avona/issues/31 | test | setup devkit w avs to test with stlp application it may just work see documentation requires | 1 |
802,679 | 29,043,989,481 | IssuesEvent | 2023-05-13 10:08:29 | Rostlab/LambdaPP | https://api.github.com/repos/Rostlab/LambdaPP | closed | Transition to new URL | priority | From embed.predictprotein.org created by [t03i](https://github.com/t03i): sacdallago/embed.predictprotein.org#57
Now that we converged on a name, it might be time to move the URL to be more aligned with the name.
I would suggest to use lambda.predictprotein.org and alias lambdapp.predictprotein.org and embed.predictprotein.org to it.
As far as I understood it, we can just do that in the predictprotein DNS records and in the CNAME record in the GitHub repo?
@sacdallago What do you think? | 1.0 | Transition to new URL - From embed.predictprotein.org created by [t03i](https://github.com/t03i): sacdallago/embed.predictprotein.org#57
Now that we converged on a name, it might be time to move the URL to be more aligned with the name.
I would suggest to use lambda.predictprotein.org and alias lambdapp.predictprotein.org and embed.predictprotein.org to it.
As far as I understood it, we can just do that in the predictprotein DNS records and in the CNAME record in the GitHub repo?
@sacdallago What do you think? | non_test | transition to new url from embed predictprotein org created by sacdallago embed predictprotein org now that we converged on a name it might be time to move the url to be more aligned with the name i would suggest to use lambda predictprotein org and alias lambdapp predictprotein org and embed predictprotein org to it as far as i understood it we can just do that in the predictprotein dns records and in the cname record in the github repo sacdallago what do you think | 0 |
107,108 | 23,348,423,956 | IssuesEvent | 2022-08-09 20:25:56 | WayofTime/BloodMagic | https://api.github.com/repos/WayofTime/BloodMagic | closed | [1.18.2 Bug] Bedrock Recipe | code complete 1.18.2 | #### Issue Description:
Some recipe from the arcane ashes creates bedrock in survival, they are super easy to be done too
#### What happens:
Certain recipe from the arcane ashes creates bedrock even in survival
#### What you expected to happen:
Those should not do that lmao
#### Steps to reproduce:
1. Use an arcane ash
2. Use 2 bone on it
3. Wait and it should spawn a bedrock block on the ground
Recipe in JEI

Recipe ID

Recipe inside the mod's data

____
#### Affected Versions (Do *not* use "latest"):
- BloodMagic: 3.2.3-38
- Minecraft: 1.18.2
- Forge: 40.1.68 | 1.0 | [1.18.2 Bug] Bedrock Recipe - #### Issue Description:
Some recipe from the arcane ashes creates bedrock in survival, they are super easy to be done too
#### What happens:
Certain recipe from the arcane ashes creates bedrock even in survival
#### What you expected to happen:
Those should not do that lmao
#### Steps to reproduce:
1. Use an arcane ash
2. Use 2 bone on it
3. Wait and it should spawn a bedrock block on the ground
Recipe in JEI

Recipe ID

Recipe inside the mod's data

____
#### Affected Versions (Do *not* use "latest"):
- BloodMagic: 3.2.3-38
- Minecraft: 1.18.2
- Forge: 40.1.68 | non_test | bedrock recipe issue description some recipe from the arcane ashes creates bedrock in survival they are super easy to be done too what happens certain recipe from the arcane ashes creates bedrock even in survival what you expected to happen those should not do that lmao steps to reproduce use an arcane ash use bone on it wait and it should spawn a bedrock block on the ground recipe in jei recipe id recipe inside the mod s data affected versions do not use latest bloodmagic minecraft forge | 0 |
78,148 | 9,665,597,601 | IssuesEvent | 2019-05-21 08:53:23 | canonical-web-and-design/snapcraft.io | https://api.github.com/repos/canonical-web-and-design/snapcraft.io | closed | Subscribe newsletter | Review: Design +1 Review: UX +1 | ## Current signup
Reference when designing: https://github.com/canonical-web-and-design/meeting-notes/issues/384
<img width="1439" alt="Screenshot 2019-04-24 at 15 23 42" src="https://user-images.githubusercontent.com/17748020/56667086-0faace80-66a5-11e9-9148-328f050b6798.png"> | 1.0 | Subscribe newsletter - ## Current signup
Reference when designing: https://github.com/canonical-web-and-design/meeting-notes/issues/384
<img width="1439" alt="Screenshot 2019-04-24 at 15 23 42" src="https://user-images.githubusercontent.com/17748020/56667086-0faace80-66a5-11e9-9148-328f050b6798.png"> | non_test | subscribe newsletter current signup reference when designing img width alt screenshot at src | 0 |
573,340 | 17,023,632,782 | IssuesEvent | 2021-07-03 03:01:27 | tomhughes/trac-tickets | https://api.github.com/repos/tomhughes/trac-tickets | closed | [roads] Rendering alternate names instead of normal names | Component: mapnik Priority: minor Resolution: duplicate Type: enhancement | **[Submitted to the original trac issue database at 11.33am, Thursday, 9th September 2010]**
In case of lock=yes (lock=*) or bridge=yes (bridge=*) the alternate name lock_name="..." or bridge_name="..." should be used instead of the normal name="...". The normal name may not be rendered in case no alternate name exist (see http://www.openstreetmap.org/?lat=48.74196&lon=6.94223&zoom=17&layers=M).
If the name doesn't fit within the lock/bridge the alternate name should be rendered next and not above the object.
| 1.0 | [roads] Rendering alternate names instead of normal names - **[Submitted to the original trac issue database at 11.33am, Thursday, 9th September 2010]**
In case of lock=yes (lock=*) or bridge=yes (bridge=*) the alternate name lock_name="..." or bridge_name="..." should be used instead of the normal name="...". The normal name may not be rendered in case no alternate name exist (see http://www.openstreetmap.org/?lat=48.74196&lon=6.94223&zoom=17&layers=M).
If the name doesn't fit within the lock/bridge the alternate name should be rendered next and not above the object.
| non_test | rendering alternate names instead of normal names in case of lock yes lock or bridge yes bridge the alternate name lock name or bridge name should be used instead of the normal name the normal name may not be rendered in case no alternate name exist see if the name doesn t fit within the lock bridge the alternate name should be rendered next and not above the object | 0 |
627,184 | 19,898,740,724 | IssuesEvent | 2022-01-25 04:12:55 | TheMegax/fabric-elytra-autopilot | https://api.github.com/repos/TheMegax/fabric-elytra-autopilot | closed | Gets confused in the End | bug high priority | Reproduce:
1. Create a survival world, go to the End
2. /takeoff
3. /flyto x z
Expected:
/flyto to work as it does in the Overworld
Actual:
Height from ground changes to "???" (presumably due to void); "You're too low to activate auto-flight!" and it doesn't seem to land safely either.
Minecraft 1.18.1, Elytra AutoPilot 1.3.0, Fabric API 0.46.2 | 1.0 | Gets confused in the End - Reproduce:
1. Create a survival world, go to the End
2. /takeoff
3. /flyto x z
Expected:
/flyto to work as it does in the Overworld
Actual:
Height from ground changes to "???" (presumably due to void); "You're too low to activate auto-flight!" and it doesn't seem to land safely either.
Minecraft 1.18.1, Elytra AutoPilot 1.3.0, Fabric API 0.46.2 | non_test | gets confused in the end reproduce create a survival world go to the end takeoff flyto x z expected flyto to work as it does in the overworld actual height from ground changes to presumably due to void you re too low to activate auto flight and it doesn t seem to land safely either minecraft elytra autopilot fabric api | 0 |
171,124 | 27,065,032,992 | IssuesEvent | 2023-02-13 23:19:18 | filrpe/treinamento-OBI-2023 | https://api.github.com/repos/filrpe/treinamento-OBI-2023 | closed | Banner para divulgação no site do IFPA | design | Dar uma olhada no [portal do ifpa](https://ifpa.edu.br/index.php) e em como eles colocam os Banners deles (resolução), e criar um nosso inspirado nesse padrão (exemplo: https://ifpa.edu.br/component/content/article?id=1950), com as seguintes informações;
- Período de inscrições: de 06 a 22 de Fevereiro.
- Texto de chamada para o treinamento.
- Logo abaixo o link do nosso formulário de inscrições (ou QR code, dá pra gerar em ferramentas online)
- Sugestão de paleta de cores: Verde escuro com a logo branca do ifpa, porém não obrigatório. Fica a critério. | 1.0 | Banner para divulgação no site do IFPA - Dar uma olhada no [portal do ifpa](https://ifpa.edu.br/index.php) e em como eles colocam os Banners deles (resolução), e criar um nosso inspirado nesse padrão (exemplo: https://ifpa.edu.br/component/content/article?id=1950), com as seguintes informações;
- Período de inscrições: de 06 a 22 de Fevereiro.
- Texto de chamada para o treinamento.
- Logo abaixo o link do nosso formulário de inscrições (ou QR code, dá pra gerar em ferramentas online)
- Sugestão de paleta de cores: Verde escuro com a logo branca do ifpa, porém não obrigatório. Fica a critério. | non_test | banner para divulgação no site do ifpa dar uma olhada no e em como eles colocam os banners deles resolução e criar um nosso inspirado nesse padrão exemplo com as seguintes informações período de inscrições de a de fevereiro texto de chamada para o treinamento logo abaixo o link do nosso formulário de inscrições ou qr code dá pra gerar em ferramentas online sugestão de paleta de cores verde escuro com a logo branca do ifpa porém não obrigatório fica a critério | 0 |
52,328 | 6,227,400,647 | IssuesEvent | 2017-07-10 20:41:29 | dotnet/corefx | https://api.github.com/repos/dotnet/corefx | closed | Tests under: BasicEventSourceTests.TestsUserErrors failed with "Xunit.Sdk.EqualException" & "Xunit.Sdk.TrueException" | area-System.Diagnostics.Tracing test-run-uwp-ilc | Opened on behalf of @Jiayili1
The test `BasicEventSourceTests.TestsUserErrors/Test_BadEventSource_MismatchedIds` has failed.
Assert.Equal() Failure\r
? (pos 5)\r
Expected: EventSourceMessage\r
Actual: Event1\r
? (pos 5)
Stack Trace:
at BasicEventSourceTests.TestsUserErrors.Test_Bad_EventSource_Startup(Boolean onStartup, Listener listener, Diagnostics.Tracing.EventSourceSettings settings)
at BasicEventSourceTests.TestsUserErrors.Test_BadEventSource_MismatchedIds()
at xunit.console.netcore!<BaseAddress>+0xa9afce
at xunit.console.netcore!<BaseAddress>+0x9716ac
at xunit.console.netcore!<BaseAddress>+0x971504
Build : Master - 20170619.01 (UWP ILC Tests)
Failing configurations:
- Windows.10.Amd64-x86
- Debug
- Release
- Windows.10.Amd64-x64
- Debug
- Release
Detail: https://mc.dot.net/#/product/netcore/master/source/official~2Fcorefx~2Fmaster~2F/type/test~2Ffunctional~2Filc~2F/build/20170619.01/workItem/System.Diagnostics.Tracing.Tests/analysis/xunit/BasicEventSourceTests.TestsUserErrors~2FTest_BadEventSource_MismatchedIds | 1.0 | Tests under: BasicEventSourceTests.TestsUserErrors failed with "Xunit.Sdk.EqualException" & "Xunit.Sdk.TrueException" - Opened on behalf of @Jiayili1
The test `BasicEventSourceTests.TestsUserErrors/Test_BadEventSource_MismatchedIds` has failed.
Assert.Equal() Failure\r
? (pos 5)\r
Expected: EventSourceMessage\r
Actual: Event1\r
? (pos 5)
Stack Trace:
at BasicEventSourceTests.TestsUserErrors.Test_Bad_EventSource_Startup(Boolean onStartup, Listener listener, Diagnostics.Tracing.EventSourceSettings settings)
at BasicEventSourceTests.TestsUserErrors.Test_BadEventSource_MismatchedIds()
at xunit.console.netcore!<BaseAddress>+0xa9afce
at xunit.console.netcore!<BaseAddress>+0x9716ac
at xunit.console.netcore!<BaseAddress>+0x971504
Build : Master - 20170619.01 (UWP ILC Tests)
Failing configurations:
- Windows.10.Amd64-x86
- Debug
- Release
- Windows.10.Amd64-x64
- Debug
- Release
Detail: https://mc.dot.net/#/product/netcore/master/source/official~2Fcorefx~2Fmaster~2F/type/test~2Ffunctional~2Filc~2F/build/20170619.01/workItem/System.Diagnostics.Tracing.Tests/analysis/xunit/BasicEventSourceTests.TestsUserErrors~2FTest_BadEventSource_MismatchedIds | test | tests under basiceventsourcetests testsusererrors failed with xunit sdk equalexception xunit sdk trueexception opened on behalf of the test basiceventsourcetests testsusererrors test badeventsource mismatchedids has failed assert equal failure r pos r expected eventsourcemessage r actual r pos stack trace at basiceventsourcetests testsusererrors test bad eventsource startup boolean onstartup listener listener diagnostics tracing eventsourcesettings settings at basiceventsourcetests testsusererrors test badeventsource mismatchedids at xunit console netcore at xunit console netcore at xunit console netcore build master uwp ilc tests failing configurations windows debug release windows debug release detail | 1 |
322,836 | 27,638,582,330 | IssuesEvent | 2023-03-10 16:14:09 | RibonDAO/interface | https://api.github.com/repos/RibonDAO/interface | closed | Add tests to InputAutoComplete component | good first issue test | ## Details
Add tests to the component InputAutoComplete to increase test coverage and ensure that the component works well
## Some attention points
* Make sure the entire file is covered.
To do so, you can run yarn testCoverage and see if the file you're updating or creating has 100%.
* We have a testUtils with our custom functions.
Don't forget to use them in place of "testing-library/react" functions.
* Feel free to add new tests and new functions that were not used yet.
## Are you getting started?
Check [Ribon Docs](https://ribondao.github.io/docs/) to learn what is Ribon, how to contribute and get a Smart contract overview.
## Get rewarded in USDC
We have USDC bountys for all our issues on Github. If you want to get rewarded for solving this issue just follow these steps:
- Click on [this link](https://app.dework.xyz/ribon/ribon-dao-english/view/board-l60qxf65?taskId=797db1ea-ed49-41b8-98c9-b6df6552f9ca) to access this issue on Ribons Dework.
- Log in using your Github account, and add your metamask wallet.
- Make sure you're in the right issue, then click on "submit work" to apply.
- You'll be added to our discord and a thread will be automaticaly created so you can talk with the reviewer. You can ask questions or simply ask to work on the issue and we will assign it to you.
- When you're done, link your pool request. We will review your work and send the USDC to the wallet you added on dework.
## Questions? Join Discord!
We highly recommend that you join us in [Discord #development channel](https://discord.gg/APAKvaSuMN) to ask questions quickly and hear about upcoming new issues.
| 1.0 | Add tests to InputAutoComplete component - ## Details
Add tests to the component InputAutoComplete to increase test coverage and ensure that the component works well
## Some attention points
* Make sure the entire file is covered.
To do so, you can run yarn testCoverage and see if the file you're updating or creating has 100%.
* We have a testUtils with our custom functions.
Don't forget to use them in place of "testing-library/react" functions.
* Feel free to add new tests and new functions that were not used yet.
## Are you getting started?
Check [Ribon Docs](https://ribondao.github.io/docs/) to learn what is Ribon, how to contribute and get a Smart contract overview.
## Get rewarded in USDC
We have USDC bountys for all our issues on Github. If you want to get rewarded for solving this issue just follow these steps:
- Click on [this link](https://app.dework.xyz/ribon/ribon-dao-english/view/board-l60qxf65?taskId=797db1ea-ed49-41b8-98c9-b6df6552f9ca) to access this issue on Ribons Dework.
- Log in using your Github account, and add your metamask wallet.
- Make sure you're in the right issue, then click on "submit work" to apply.
- You'll be added to our discord and a thread will be automaticaly created so you can talk with the reviewer. You can ask questions or simply ask to work on the issue and we will assign it to you.
- When you're done, link your pool request. We will review your work and send the USDC to the wallet you added on dework.
## Questions? Join Discord!
We highly recommend that you join us in [Discord #development channel](https://discord.gg/APAKvaSuMN) to ask questions quickly and hear about upcoming new issues.
| test | add tests to inputautocomplete component details add tests to the component inputautocomplete to increase test coverage and ensure that the component works well some attention points make sure the entire file is covered to do so you can run yarn testcoverage and see if the file you re updating or creating has we have a testutils with our custom functions don t forget to use them in place of testing library react functions feel free to add new tests and new functions that were not used yet are you getting started check to learn what is ribon how to contribute and get a smart contract overview get rewarded in usdc we have usdc bountys for all our issues on github if you want to get rewarded for solving this issue just follow these steps click on to access this issue on ribons dework log in using your github account and add your metamask wallet make sure you re in the right issue then click on submit work to apply you ll be added to our discord and a thread will be automaticaly created so you can talk with the reviewer you can ask questions or simply ask to work on the issue and we will assign it to you when you re done link your pool request we will review your work and send the usdc to the wallet you added on dework questions join discord we highly recommend that you join us in to ask questions quickly and hear about upcoming new issues | 1 |
40,415 | 5,290,458,209 | IssuesEvent | 2017-02-08 19:56:41 | medic/medic-webapp | https://api.github.com/repos/medic/medic-webapp | closed | Create a script that invokes `_view_cleanup` for all CouchDB databases | 4 - Acceptance Testing | This issue supersedes #2687, and is required for medic/medic-projects#743.
Build a script that connects to the local CouchDB database using gardener's stored administrative credentials, and uses `curl` to request `_view_cleanup` for every design document in any database.
| 1.0 | Create a script that invokes `_view_cleanup` for all CouchDB databases - This issue supersedes #2687, and is required for medic/medic-projects#743.
Build a script that connects to the local CouchDB database using gardener's stored administrative credentials, and uses `curl` to request `_view_cleanup` for every design document in any database.
| test | create a script that invokes view cleanup for all couchdb databases this issue supersedes and is required for medic medic projects build a script that connects to the local couchdb database using gardener s stored administrative credentials and uses curl to request view cleanup for every design document in any database | 1 |
316,332 | 9,645,873,456 | IssuesEvent | 2019-05-17 09:44:44 | StrangeLoopGames/EcoIssues | https://api.github.com/repos/StrangeLoopGames/EcoIssues | closed | Master: Otter provide meat instead of carcas. | Medium Priority | In real life, otter skin used in many valuable products!
https://www.ebay.com/bhp/otter-fur
https://github.com/StrangeLoopGames/EcoIssues/issues/10615 | 1.0 | Master: Otter provide meat instead of carcas. - In real life, otter skin used in many valuable products!
https://www.ebay.com/bhp/otter-fur
https://github.com/StrangeLoopGames/EcoIssues/issues/10615 | non_test | master otter provide meat instead of carcas in real life otter skin used in many valuable products | 0 |
220,190 | 17,155,771,776 | IssuesEvent | 2021-07-14 06:35:26 | elastic/elasticsearch | https://api.github.com/repos/elastic/elasticsearch | closed | [CI] GeoPointShapeQueryTests testFieldAlias failing | :Analytics/Geo >test-failure Team:Analytics | **Build scan:**
https://gradle-enterprise.elastic.co/s/4luaklzcgjbiu/tests/:server:test/org.elasticsearch.search.geo.GeoPointShapeQueryTests/testFieldAlias
**Reproduction line:**
`./gradlew ':server:test' --tests "org.elasticsearch.search.geo.GeoPointShapeQueryTests.testFieldAlias" -Dtests.seed=1363D0D5C6B0CD8 -Dtests.locale=bg-BG -Dtests.timezone=Etc/GMT-8 -Druntime.java=11`
**Applicable branches:**
master, 7.x
**Reproduces locally?:**
Yes
**Failure history:**
https://gradle-enterprise.elastic.co/scans/tests?tests.container=org.elasticsearch.search.geo.GeoPointShapeQueryTests&tests.test=testFieldAlias
**Failure excerpt:**
```
java.lang.AssertionError: expected:<1> but was:<0>
at __randomizedtesting.SeedInfo.seed([1363D0D5C6B0CD8:3B70AC687EDC98EC]:0)
at org.junit.Assert.fail(Assert.java:88)
at org.junit.Assert.failNotEquals(Assert.java:834)
at org.junit.Assert.assertEquals(Assert.java:645)
at org.junit.Assert.assertEquals(Assert.java:631)
at org.elasticsearch.search.geo.GeoPointShapeQueryTests.testFieldAlias(GeoPointShapeQueryTests.java:62)
at jdk.internal.reflect.NativeMethodAccessorImpl.invoke0(NativeMethodAccessorImpl.java:-2)
at jdk.internal.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62)
at jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
at java.lang.reflect.Method.invoke(Method.java:566)
at com.carrotsearch.randomizedtesting.RandomizedRunner.invoke(RandomizedRunner.java:1758)
at com.carrotsearch.randomizedtesting.RandomizedRunner$8.evaluate(RandomizedRunner.java:946)
at com.carrotsearch.randomizedtesting.RandomizedRunner$9.evaluate(RandomizedRunner.java:982)
at com.carrotsearch.randomizedtesting.RandomizedRunner$10.evaluate(RandomizedRunner.java:996)
at com.carrotsearch.randomizedtesting.rules.StatementAdapter.evaluate(StatementAdapter.java:36)
at org.apache.lucene.util.TestRuleSetupTeardownChained$1.evaluate(TestRuleSetupTeardownChained.java:49)
at org.apache.lucene.util.AbstractBeforeAfterRule$1.evaluate(AbstractBeforeAfterRule.java:45)
at org.apache.lucene.util.TestRuleThreadAndTestName$1.evaluate(TestRuleThreadAndTestName.java:48)
at org.apache.lucene.util.TestRuleIgnoreAfterMaxFailures$1.evaluate(TestRuleIgnoreAfterMaxFailures.java:64)
at org.apache.lucene.util.TestRuleMarkFailure$1.evaluate(TestRuleMarkFailure.java:47)
at com.carrotsearch.randomizedtesting.rules.StatementAdapter.evaluate(StatementAdapter.java:36)
at com.carrotsearch.randomizedtesting.ThreadLeakControl$StatementRunner.run(ThreadLeakControl.java:375)
at com.carrotsearch.randomizedtesting.ThreadLeakControl.forkTimeoutingTask(ThreadLeakControl.java:824)
at com.carrotsearch.randomizedtesting.ThreadLeakControl$3.evaluate(ThreadLeakControl.java:475)
at com.carrotsearch.randomizedtesting.RandomizedRunner.runSingleTest(RandomizedRunner.java:955)
at com.carrotsearch.randomizedtesting.RandomizedRunner$5.evaluate(RandomizedRunner.java:840)
at com.carrotsearch.randomizedtesting.RandomizedRunner$6.evaluate(RandomizedRunner.java:891)
at com.carrotsearch.randomizedtesting.RandomizedRunner$7.evaluate(RandomizedRunner.java:902)
at org.apache.lucene.util.AbstractBeforeAfterRule$1.evaluate(AbstractBeforeAfterRule.java:45)
at com.carrotsearch.randomizedtesting.rules.StatementAdapter.evaluate(StatementAdapter.java:36)
at org.apache.lucene.util.TestRuleStoreClassName$1.evaluate(TestRuleStoreClassName.java:41)
at com.carrotsearch.randomizedtesting.rules.NoShadowingOrOverridesOnMethodsRule$1.evaluate(NoShadowingOrOverridesOnMethodsRule.java:40)
at com.carrotsearch.randomizedtesting.rules.NoShadowingOrOverridesOnMethodsRule$1.evaluate(NoShadowingOrOverridesOnMethodsRule.java:40)
at com.carrotsearch.randomizedtesting.rules.StatementAdapter.evaluate(StatementAdapter.java:36)
at com.carrotsearch.randomizedtesting.rules.StatementAdapter.evaluate(StatementAdapter.java:36)
at org.apache.lucene.util.TestRuleAssertionsRequired$1.evaluate(TestRuleAssertionsRequired.java:53)
at org.apache.lucene.util.TestRuleMarkFailure$1.evaluate(TestRuleMarkFailure.java:47)
at org.apache.lucene.util.TestRuleIgnoreAfterMaxFailures$1.evaluate(TestRuleIgnoreAfterMaxFailures.java:64)
at org.apache.lucene.util.TestRuleIgnoreTestSuites$1.evaluate(TestRuleIgnoreTestSuites.java:54)
at com.carrotsearch.randomizedtesting.rules.StatementAdapter.evaluate(StatementAdapter.java:36)
at com.carrotsearch.randomizedtesting.ThreadLeakControl$StatementRunner.run(ThreadLeakControl.java:375)
at com.carrotsearch.randomizedtesting.ThreadLeakControl.lambda$forkTimeoutingTask$0(ThreadLeakControl.java:831)
at java.lang.Thread.run(Thread.java:834)
``` | 1.0 | [CI] GeoPointShapeQueryTests testFieldAlias failing - **Build scan:**
https://gradle-enterprise.elastic.co/s/4luaklzcgjbiu/tests/:server:test/org.elasticsearch.search.geo.GeoPointShapeQueryTests/testFieldAlias
**Reproduction line:**
`./gradlew ':server:test' --tests "org.elasticsearch.search.geo.GeoPointShapeQueryTests.testFieldAlias" -Dtests.seed=1363D0D5C6B0CD8 -Dtests.locale=bg-BG -Dtests.timezone=Etc/GMT-8 -Druntime.java=11`
**Applicable branches:**
master, 7.x
**Reproduces locally?:**
Yes
**Failure history:**
https://gradle-enterprise.elastic.co/scans/tests?tests.container=org.elasticsearch.search.geo.GeoPointShapeQueryTests&tests.test=testFieldAlias
**Failure excerpt:**
```
java.lang.AssertionError: expected:<1> but was:<0>
at __randomizedtesting.SeedInfo.seed([1363D0D5C6B0CD8:3B70AC687EDC98EC]:0)
at org.junit.Assert.fail(Assert.java:88)
at org.junit.Assert.failNotEquals(Assert.java:834)
at org.junit.Assert.assertEquals(Assert.java:645)
at org.junit.Assert.assertEquals(Assert.java:631)
at org.elasticsearch.search.geo.GeoPointShapeQueryTests.testFieldAlias(GeoPointShapeQueryTests.java:62)
at jdk.internal.reflect.NativeMethodAccessorImpl.invoke0(NativeMethodAccessorImpl.java:-2)
at jdk.internal.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62)
at jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
at java.lang.reflect.Method.invoke(Method.java:566)
at com.carrotsearch.randomizedtesting.RandomizedRunner.invoke(RandomizedRunner.java:1758)
at com.carrotsearch.randomizedtesting.RandomizedRunner$8.evaluate(RandomizedRunner.java:946)
at com.carrotsearch.randomizedtesting.RandomizedRunner$9.evaluate(RandomizedRunner.java:982)
at com.carrotsearch.randomizedtesting.RandomizedRunner$10.evaluate(RandomizedRunner.java:996)
at com.carrotsearch.randomizedtesting.rules.StatementAdapter.evaluate(StatementAdapter.java:36)
at org.apache.lucene.util.TestRuleSetupTeardownChained$1.evaluate(TestRuleSetupTeardownChained.java:49)
at org.apache.lucene.util.AbstractBeforeAfterRule$1.evaluate(AbstractBeforeAfterRule.java:45)
at org.apache.lucene.util.TestRuleThreadAndTestName$1.evaluate(TestRuleThreadAndTestName.java:48)
at org.apache.lucene.util.TestRuleIgnoreAfterMaxFailures$1.evaluate(TestRuleIgnoreAfterMaxFailures.java:64)
at org.apache.lucene.util.TestRuleMarkFailure$1.evaluate(TestRuleMarkFailure.java:47)
at com.carrotsearch.randomizedtesting.rules.StatementAdapter.evaluate(StatementAdapter.java:36)
at com.carrotsearch.randomizedtesting.ThreadLeakControl$StatementRunner.run(ThreadLeakControl.java:375)
at com.carrotsearch.randomizedtesting.ThreadLeakControl.forkTimeoutingTask(ThreadLeakControl.java:824)
at com.carrotsearch.randomizedtesting.ThreadLeakControl$3.evaluate(ThreadLeakControl.java:475)
at com.carrotsearch.randomizedtesting.RandomizedRunner.runSingleTest(RandomizedRunner.java:955)
at com.carrotsearch.randomizedtesting.RandomizedRunner$5.evaluate(RandomizedRunner.java:840)
at com.carrotsearch.randomizedtesting.RandomizedRunner$6.evaluate(RandomizedRunner.java:891)
at com.carrotsearch.randomizedtesting.RandomizedRunner$7.evaluate(RandomizedRunner.java:902)
at org.apache.lucene.util.AbstractBeforeAfterRule$1.evaluate(AbstractBeforeAfterRule.java:45)
at com.carrotsearch.randomizedtesting.rules.StatementAdapter.evaluate(StatementAdapter.java:36)
at org.apache.lucene.util.TestRuleStoreClassName$1.evaluate(TestRuleStoreClassName.java:41)
at com.carrotsearch.randomizedtesting.rules.NoShadowingOrOverridesOnMethodsRule$1.evaluate(NoShadowingOrOverridesOnMethodsRule.java:40)
at com.carrotsearch.randomizedtesting.rules.NoShadowingOrOverridesOnMethodsRule$1.evaluate(NoShadowingOrOverridesOnMethodsRule.java:40)
at com.carrotsearch.randomizedtesting.rules.StatementAdapter.evaluate(StatementAdapter.java:36)
at com.carrotsearch.randomizedtesting.rules.StatementAdapter.evaluate(StatementAdapter.java:36)
at org.apache.lucene.util.TestRuleAssertionsRequired$1.evaluate(TestRuleAssertionsRequired.java:53)
at org.apache.lucene.util.TestRuleMarkFailure$1.evaluate(TestRuleMarkFailure.java:47)
at org.apache.lucene.util.TestRuleIgnoreAfterMaxFailures$1.evaluate(TestRuleIgnoreAfterMaxFailures.java:64)
at org.apache.lucene.util.TestRuleIgnoreTestSuites$1.evaluate(TestRuleIgnoreTestSuites.java:54)
at com.carrotsearch.randomizedtesting.rules.StatementAdapter.evaluate(StatementAdapter.java:36)
at com.carrotsearch.randomizedtesting.ThreadLeakControl$StatementRunner.run(ThreadLeakControl.java:375)
at com.carrotsearch.randomizedtesting.ThreadLeakControl.lambda$forkTimeoutingTask$0(ThreadLeakControl.java:831)
at java.lang.Thread.run(Thread.java:834)
``` | test | geopointshapequerytests testfieldalias failing build scan reproduction line gradlew server test tests org elasticsearch search geo geopointshapequerytests testfieldalias dtests seed dtests locale bg bg dtests timezone etc gmt druntime java applicable branches master x reproduces locally yes failure history failure excerpt java lang assertionerror expected but was at randomizedtesting seedinfo seed at org junit assert fail assert java at org junit assert failnotequals assert java at org junit assert assertequals assert java at org junit assert assertequals assert java at org elasticsearch search geo geopointshapequerytests testfieldalias geopointshapequerytests java at jdk internal reflect nativemethodaccessorimpl nativemethodaccessorimpl java at jdk internal reflect nativemethodaccessorimpl invoke nativemethodaccessorimpl java at jdk internal reflect delegatingmethodaccessorimpl invoke delegatingmethodaccessorimpl java at java lang reflect method invoke method java at com carrotsearch randomizedtesting randomizedrunner invoke randomizedrunner java at com carrotsearch randomizedtesting randomizedrunner evaluate randomizedrunner java at com carrotsearch randomizedtesting randomizedrunner evaluate randomizedrunner java at com carrotsearch randomizedtesting randomizedrunner evaluate randomizedrunner java at com carrotsearch randomizedtesting rules statementadapter evaluate statementadapter java at org apache lucene util testrulesetupteardownchained evaluate testrulesetupteardownchained java at org apache lucene util abstractbeforeafterrule evaluate abstractbeforeafterrule java at org apache lucene util testrulethreadandtestname evaluate testrulethreadandtestname java at org apache lucene util testruleignoreaftermaxfailures evaluate testruleignoreaftermaxfailures java at org apache lucene util testrulemarkfailure evaluate testrulemarkfailure java at com carrotsearch randomizedtesting rules statementadapter evaluate statementadapter java at com carrotsearch randomizedtesting threadleakcontrol statementrunner run threadleakcontrol java at com carrotsearch randomizedtesting threadleakcontrol forktimeoutingtask threadleakcontrol java at com carrotsearch randomizedtesting threadleakcontrol evaluate threadleakcontrol java at com carrotsearch randomizedtesting randomizedrunner runsingletest randomizedrunner java at com carrotsearch randomizedtesting randomizedrunner evaluate randomizedrunner java at com carrotsearch randomizedtesting randomizedrunner evaluate randomizedrunner java at com carrotsearch randomizedtesting randomizedrunner evaluate randomizedrunner java at org apache lucene util abstractbeforeafterrule evaluate abstractbeforeafterrule java at com carrotsearch randomizedtesting rules statementadapter evaluate statementadapter java at org apache lucene util testrulestoreclassname evaluate testrulestoreclassname java at com carrotsearch randomizedtesting rules noshadowingoroverridesonmethodsrule evaluate noshadowingoroverridesonmethodsrule java at com carrotsearch randomizedtesting rules noshadowingoroverridesonmethodsrule evaluate noshadowingoroverridesonmethodsrule java at com carrotsearch randomizedtesting rules statementadapter evaluate statementadapter java at com carrotsearch randomizedtesting rules statementadapter evaluate statementadapter java at org apache lucene util testruleassertionsrequired evaluate testruleassertionsrequired java at org apache lucene util testrulemarkfailure evaluate testrulemarkfailure java at org apache lucene util testruleignoreaftermaxfailures evaluate testruleignoreaftermaxfailures java at org apache lucene util testruleignoretestsuites evaluate testruleignoretestsuites java at com carrotsearch randomizedtesting rules statementadapter evaluate statementadapter java at com carrotsearch randomizedtesting threadleakcontrol statementrunner run threadleakcontrol java at com carrotsearch randomizedtesting threadleakcontrol lambda forktimeoutingtask threadleakcontrol java at java lang thread run thread java | 1 |
501,639 | 14,530,531,212 | IssuesEvent | 2020-12-14 19:24:15 | OpenLiberty/ci.maven | https://api.github.com/repos/OpenLiberty/ci.maven | opened | Feature list to install is not correctly updated when modifying server.xml in devc | devModeContainers medium priority | 1. Have this in server.xml:
```
<featureManager>
<feature>aaa</feature>
<feature>bbb</feature>
</featureManager>
```
2. Start mvn liberty:devc
3. Change `bbb` to `ccc`
4. Even though `bbb` is no longer specified, devc still tries to install it.
```
[INFO] Installing features [aaa, ccc, bbb] on container liberty-dev
[ERROR] An error occurred while installing features: CWWKF1402E: The following features were not obtained: aaa ccc bbb. Ensure that the features are valid. RC=21
``` | 1.0 | Feature list to install is not correctly updated when modifying server.xml in devc - 1. Have this in server.xml:
```
<featureManager>
<feature>aaa</feature>
<feature>bbb</feature>
</featureManager>
```
2. Start mvn liberty:devc
3. Change `bbb` to `ccc`
4. Even though `bbb` is no longer specified, devc still tries to install it.
```
[INFO] Installing features [aaa, ccc, bbb] on container liberty-dev
[ERROR] An error occurred while installing features: CWWKF1402E: The following features were not obtained: aaa ccc bbb. Ensure that the features are valid. RC=21
``` | non_test | feature list to install is not correctly updated when modifying server xml in devc have this in server xml aaa bbb start mvn liberty devc change bbb to ccc even though bbb is no longer specified devc still tries to install it installing features on container liberty dev an error occurred while installing features the following features were not obtained aaa ccc bbb ensure that the features are valid rc | 0 |
214,976 | 16,620,941,996 | IssuesEvent | 2021-06-03 00:50:27 | sugarlabs/musicblocks | https://api.github.com/repos/sugarlabs/musicblocks | closed | Pitch Number not Working for temperament when outside of first octave | Issue-Bug WF6-Needs testing | Using Pitch Number to generate pitches for a custom temperament fails when outside the first (i.e. original) octave.
```
Uncaught TypeError: Cannot read property '1' of undefined
at numberToPitch (musicutils.js:2538)
at Function.playPitchNumber (PitchActions.js:435)
at PitchNumberBlock.flow (PitchBlocks.js:1604)
at Logo.runFromBlockNow (logo.js:1472)
at logo.js:1325
```
Test Program:
[Simple-Program-Pitch-Number-Fail-Outside-Octave.html.zip](https://github.com/sugarlabs/musicblocks/files/6565193/Simple-Program-Pitch-Number-Fail-Outside-Octave.html.zip)
Steps to reproduce:
1. Generate a custom temperament (tested with 41EDO and 5EDO)
2. Use pitch number to generate the pitches within a note value block
3. When the value into pitch number is greater than the number of pitches within one octave of the custom temperament, the program will fail to continue.

| 1.0 | Pitch Number not Working for temperament when outside of first octave - Using Pitch Number to generate pitches for a custom temperament fails when outside the first (i.e. original) octave.
```
Uncaught TypeError: Cannot read property '1' of undefined
at numberToPitch (musicutils.js:2538)
at Function.playPitchNumber (PitchActions.js:435)
at PitchNumberBlock.flow (PitchBlocks.js:1604)
at Logo.runFromBlockNow (logo.js:1472)
at logo.js:1325
```
Test Program:
[Simple-Program-Pitch-Number-Fail-Outside-Octave.html.zip](https://github.com/sugarlabs/musicblocks/files/6565193/Simple-Program-Pitch-Number-Fail-Outside-Octave.html.zip)
Steps to reproduce:
1. Generate a custom temperament (tested with 41EDO and 5EDO)
2. Use pitch number to generate the pitches within a note value block
3. When the value into pitch number is greater than the number of pitches within one octave of the custom temperament, the program will fail to continue.

| test | pitch number not working for temperament when outside of first octave using pitch number to generate pitches for a custom temperament fails when outside the first i e original octave uncaught typeerror cannot read property of undefined at numbertopitch musicutils js at function playpitchnumber pitchactions js at pitchnumberblock flow pitchblocks js at logo runfromblocknow logo js at logo js test program steps to reproduce generate a custom temperament tested with and use pitch number to generate the pitches within a note value block when the value into pitch number is greater than the number of pitches within one octave of the custom temperament the program will fail to continue | 1 |
301,667 | 26,084,919,070 | IssuesEvent | 2022-12-26 00:34:52 | devssa/onde-codar-em-salvador | https://api.github.com/repos/devssa/onde-codar-em-salvador | closed | [REMOTO] SRE CONFIDENCIAL | EFETIVO(CLT) PLENO TESTE AUTOMATIZADO TESTE DE INTEGRAÇÃO DOCKER NOSQL AWS TESTE INTEGRAÇÃO HELP WANTED feature_request Stale | [REMOTO] SRE CONFIDENCIAL
Trabalhe na empresa que vem revolucionando o mercado de recrutamento, foi escolhida pela Endeavor como uma das melhores 16 scale up SAAS! Atualmente, a empresa recebeu um investimento de 20 milhões do fundo Astela e é uma das startups que mais vem crescendo no Brasil.
Não estamos em busca de nenhuma stack especifica, buscamos pessoas com propósito, proatividade, mão na massa e dispostas a aprender e crescer exponencialmente. Serão bem vindos conhecimentos em AWS, testes automatizados, integração contínua...
Estamos te esperando. Topa o desafio? 🙂
byintera.in/10h
Vaga 100% remota ##
Não estamos em busca de nenhuma stack especifica, buscamos pessoas com propósito, proatividade, mão na massa e dispostas a aprender e crescer exponencialmente. Serão bem vindos conhecimentos em AWS, testes automatizados, integração contínua...
Contratação CLT ##
Como se candidatar preencher o formulário no final do link byintera.in/10h ##
Labels ###
Regime-CLT ###
Nível- Pleno ###
Stacks- AWS- Docker- Shell Script - Bash- SQL- nosql
| 3.0 | [REMOTO] SRE CONFIDENCIAL - [REMOTO] SRE CONFIDENCIAL
Trabalhe na empresa que vem revolucionando o mercado de recrutamento, foi escolhida pela Endeavor como uma das melhores 16 scale up SAAS! Atualmente, a empresa recebeu um investimento de 20 milhões do fundo Astela e é uma das startups que mais vem crescendo no Brasil.
Não estamos em busca de nenhuma stack especifica, buscamos pessoas com propósito, proatividade, mão na massa e dispostas a aprender e crescer exponencialmente. Serão bem vindos conhecimentos em AWS, testes automatizados, integração contínua...
Estamos te esperando. Topa o desafio? 🙂
byintera.in/10h
Vaga 100% remota ##
Não estamos em busca de nenhuma stack especifica, buscamos pessoas com propósito, proatividade, mão na massa e dispostas a aprender e crescer exponencialmente. Serão bem vindos conhecimentos em AWS, testes automatizados, integração contínua...
Contratação CLT ##
Como se candidatar preencher o formulário no final do link byintera.in/10h ##
Labels ###
Regime-CLT ###
Nível- Pleno ###
Stacks- AWS- Docker- Shell Script - Bash- SQL- nosql
| test | sre confidencial sre confidencial trabalhe na empresa que vem revolucionando o mercado de recrutamento foi escolhida pela endeavor como uma das melhores scale up saas atualmente a empresa recebeu um investimento de milhões do fundo astela e é uma das startups que mais vem crescendo no brasil não estamos em busca de nenhuma stack especifica buscamos pessoas com propósito proatividade mão na massa e dispostas a aprender e crescer exponencialmente serão bem vindos conhecimentos em aws testes automatizados integração contínua estamos te esperando topa o desafio 🙂 byintera in vaga remota não estamos em busca de nenhuma stack especifica buscamos pessoas com propósito proatividade mão na massa e dispostas a aprender e crescer exponencialmente serão bem vindos conhecimentos em aws testes automatizados integração contínua contratação clt como se candidatar preencher o formulário no final do link byintera in labels regime clt nível pleno stacks aws docker shell script bash sql nosql | 1 |
256,467 | 22,054,365,591 | IssuesEvent | 2022-05-30 11:31:39 | IRPTeam/IRP | https://api.github.com/repos/IRPTeam/IRP | closed | StockBalanceDetail in serial lot numbers | bug testing | При создании серии не проставляется галочка учета серии по складу, не смотря на то что в виде номенклатуры есть учет по сериям.
Проставили галочку в виде номенклатуры.
Сканируем ШК товара в документах, открывается форма подбора серийников.
Пикаем серийник, нажимаем Создать, а галочка StockBalanceDetail не проставляется | 1.0 | StockBalanceDetail in serial lot numbers - При создании серии не проставляется галочка учета серии по складу, не смотря на то что в виде номенклатуры есть учет по сериям.
Проставили галочку в виде номенклатуры.
Сканируем ШК товара в документах, открывается форма подбора серийников.
Пикаем серийник, нажимаем Создать, а галочка StockBalanceDetail не проставляется | test | stockbalancedetail in serial lot numbers при создании серии не проставляется галочка учета серии по складу не смотря на то что в виде номенклатуры есть учет по сериям проставили галочку в виде номенклатуры сканируем шк товара в документах открывается форма подбора серийников пикаем серийник нажимаем создать а галочка stockbalancedetail не проставляется | 1 |
72,051 | 7,276,467,360 | IssuesEvent | 2018-02-21 16:27:30 | torbengb/bank2ynab | https://api.github.com/repos/torbengb/bank2ynab | closed | Support for ING [NL] | bank format good first issue help wanted to be tested | Header row: "\"Datum\",\"Naam / Omschrijving\",\"Rekening\",\"Tegenrekening\",\"Code\",\"Af Bij\",\"Bedrag (EUR)\",\"MutatieSoort\",\"Mededelingen\""
- [AndreSomers/ING2YNAB](https://github.com/AndreSomers/ING2YNAB) (empty project)
- [dive/ing-to-ynab-json-converter](https://github.com/dive/ing-to-ynab-json-converter)
- [ernezt/ynab-ing-converter](https://github.com/ernezt/ynab-ing-converter)This doesnt' look like a real program...
- [Remco32/ing-to-ynab-converter](https://github.com/Remco32/ing-to-ynab-converter) I can't really interpret this one! | 1.0 | Support for ING [NL] - Header row: "\"Datum\",\"Naam / Omschrijving\",\"Rekening\",\"Tegenrekening\",\"Code\",\"Af Bij\",\"Bedrag (EUR)\",\"MutatieSoort\",\"Mededelingen\""
- [AndreSomers/ING2YNAB](https://github.com/AndreSomers/ING2YNAB) (empty project)
- [dive/ing-to-ynab-json-converter](https://github.com/dive/ing-to-ynab-json-converter)
- [ernezt/ynab-ing-converter](https://github.com/ernezt/ynab-ing-converter)This doesnt' look like a real program...
- [Remco32/ing-to-ynab-converter](https://github.com/Remco32/ing-to-ynab-converter) I can't really interpret this one! | test | support for ing header row datum naam omschrijving rekening tegenrekening code af bij bedrag eur mutatiesoort mededelingen empty project doesnt look like a real program i can t really interpret this one | 1 |
162,259 | 6,149,601,223 | IssuesEvent | 2017-06-27 20:30:04 | minishift/minishift | https://api.github.com/repos/minishift/minishift | closed | `minishift start` fails on mac/xhyve | kind/bug priority/major status/needs-info | I am unable to start minishift on mac:
```
$ minishift start
Starting local OpenShift cluster using 'xhyve' hypervisor...
E0519 16:48:03.096205 36976 start.go:176] Error starting the VM: Unused explicit driver options: map[xhyve-virtio-9p:true xhyve-uuid:F4BB3F79-AB4E-4708-95CA-E32FBFCDEFD3]. Retrying.
E0519 16:48:03.121593 36976 start.go:176] Error starting the VM: Unused explicit driver options: map[xhyve-uuid:F4BB3F79-AB4E-4708-95CA-E32FBFCDEFD3 xhyve-virtio-9p:true]. Retrying.
E0519 16:48:03.151993 36976 start.go:176] Error starting the VM: Unused explicit driver options: map[xhyve-virtio-9p:true xhyve-uuid:F4BB3F79-AB4E-4708-95CA-E32FBFCDEFD3]. Retrying.
Error starting the VM: Unused explicit driver options: map[xhyve-virtio-9p:true xhyve-uuid:F4BB3F79-AB4E-4708-95CA-E32FBFCDEFD3]
Unused explicit driver options: map[xhyve-uuid:F4BB3F79-AB4E-4708-95CA-E32FBFCDEFD3 xhyve-virtio-9p:true]
Unused explicit driver options: map[xhyve-virtio-9p:true xhyve-uuid:F4BB3F79-AB4E-4708-95CA-E32FBFCDEFD3]
```

| 1.0 | `minishift start` fails on mac/xhyve - I am unable to start minishift on mac:
```
$ minishift start
Starting local OpenShift cluster using 'xhyve' hypervisor...
E0519 16:48:03.096205 36976 start.go:176] Error starting the VM: Unused explicit driver options: map[xhyve-virtio-9p:true xhyve-uuid:F4BB3F79-AB4E-4708-95CA-E32FBFCDEFD3]. Retrying.
E0519 16:48:03.121593 36976 start.go:176] Error starting the VM: Unused explicit driver options: map[xhyve-uuid:F4BB3F79-AB4E-4708-95CA-E32FBFCDEFD3 xhyve-virtio-9p:true]. Retrying.
E0519 16:48:03.151993 36976 start.go:176] Error starting the VM: Unused explicit driver options: map[xhyve-virtio-9p:true xhyve-uuid:F4BB3F79-AB4E-4708-95CA-E32FBFCDEFD3]. Retrying.
Error starting the VM: Unused explicit driver options: map[xhyve-virtio-9p:true xhyve-uuid:F4BB3F79-AB4E-4708-95CA-E32FBFCDEFD3]
Unused explicit driver options: map[xhyve-uuid:F4BB3F79-AB4E-4708-95CA-E32FBFCDEFD3 xhyve-virtio-9p:true]
Unused explicit driver options: map[xhyve-virtio-9p:true xhyve-uuid:F4BB3F79-AB4E-4708-95CA-E32FBFCDEFD3]
```

| non_test | minishift start fails on mac xhyve i am unable to start minishift on mac minishift start starting local openshift cluster using xhyve hypervisor start go error starting the vm unused explicit driver options map retrying start go error starting the vm unused explicit driver options map retrying start go error starting the vm unused explicit driver options map retrying error starting the vm unused explicit driver options map unused explicit driver options map unused explicit driver options map | 0 |
243,183 | 18,677,673,099 | IssuesEvent | 2021-10-31 20:47:52 | AY2122S1-CS2103T-F11-4/tp | https://api.github.com/repos/AY2122S1-CS2103T-F11-4/tp | closed | [PE-D] Help Command User Guide | documentation duplicate | 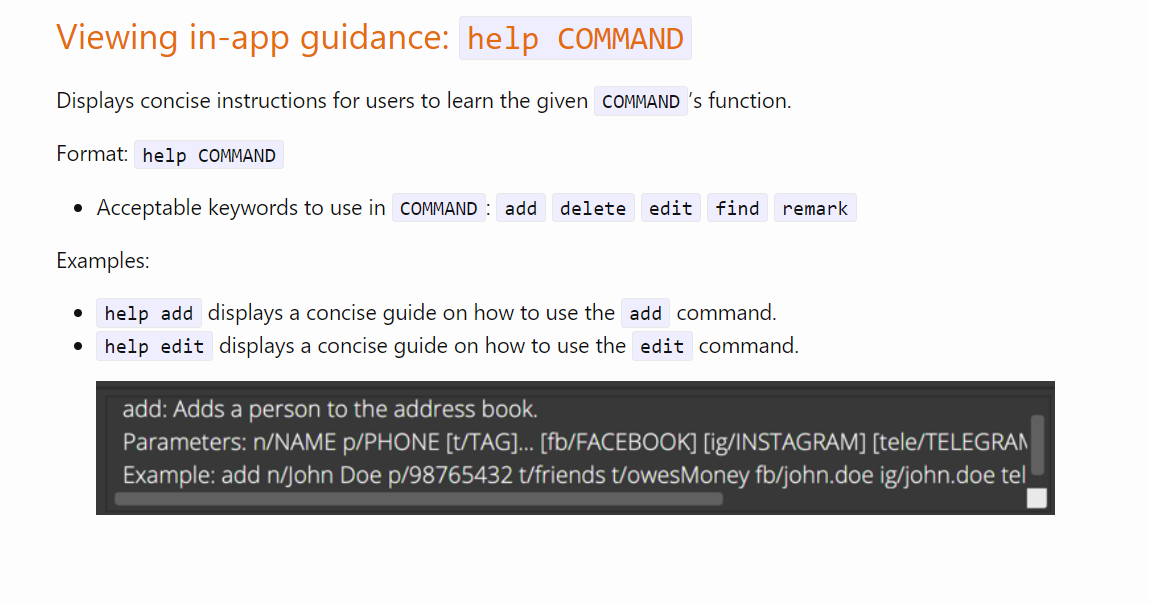
help command inputs not updated to show new commands that can be used from help window in guide
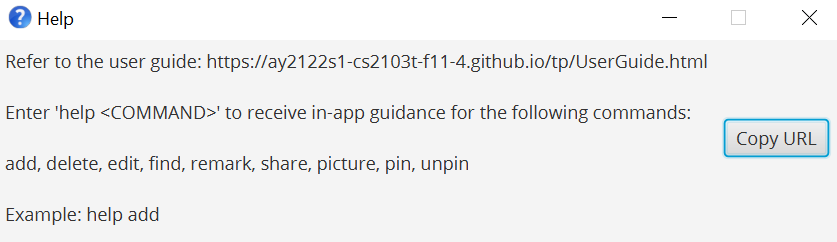
<!--session: 1635494612655-78768029-5c83-42fa-8cd5-edbbb31654ef-->
<!--Version: Web v3.4.1-->
-------------
Labels: `type.DocumentationBug` `severity.VeryLow`
original: RonaldTanSingWei/ped#5 | 1.0 | [PE-D] Help Command User Guide - 
help command inputs not updated to show new commands that can be used from help window in guide

<!--session: 1635494612655-78768029-5c83-42fa-8cd5-edbbb31654ef-->
<!--Version: Web v3.4.1-->
-------------
Labels: `type.DocumentationBug` `severity.VeryLow`
original: RonaldTanSingWei/ped#5 | non_test | help command user guide help command inputs not updated to show new commands that can be used from help window in guide labels type documentationbug severity verylow original ronaldtansingwei ped | 0 |
173,016 | 21,094,384,459 | IssuesEvent | 2022-04-04 08:56:27 | lukebroganws/NodeGoat | https://api.github.com/repos/lukebroganws/NodeGoat | closed | grunt-1.0.3.tgz: 6 vulnerabilities (highest severity is: 9.8) - autoclosed | security vulnerability | <details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>grunt-1.0.3.tgz</b></p></summary>
<p>The JavaScript Task Runner</p>
<p>Library home page: <a href="https://registry.npmjs.org/grunt/-/grunt-1.0.3.tgz">https://registry.npmjs.org/grunt/-/grunt-1.0.3.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/grunt/package.json</p>
<p>
<p>Found in HEAD commit: <a href="https://github.com/lukebroganws/NodeGoat/commit/87ddac411e57ea4967b0d6435a454aa503b72ae5">87ddac411e57ea4967b0d6435a454aa503b72ae5</a></p></details>
## Vulnerabilities
| CVE | Severity | <img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS | Dependency | Type | Fixed in | Remediation Available |
| ------------- | ------------- | ----- | ----- | ----- | --- | --- |
| [CVE-2020-28282](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-28282) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | getobject-0.1.0.tgz | Transitive | 1.3.0 | ✅ |
| [WS-2019-0063](https://github.com/nodeca/js-yaml/pull/480) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | js-yaml-3.5.5.tgz | Transitive | 1.0.4 | ✅ |
| [CVE-2021-33623](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-33623) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | trim-newlines-1.0.0.tgz | Transitive | 1.2.0 | ✅ |
| [WS-2019-0032](https://github.com/nodeca/js-yaml/commit/a567ef3c6e61eb319f0bfc2671d91061afb01235) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | js-yaml-3.5.5.tgz | Transitive | 1.0.4 | ✅ |
| [CVE-2020-7729](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-7729) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.1 | grunt-1.0.3.tgz | Direct | 1.3.0 | ✅ |
| [CVE-2021-23362](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-23362) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 5.3 | hosted-git-info-2.7.1.tgz | Transitive | 1.0.4 | ✅ |
## Details
<details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-28282</summary>
### Vulnerable Library - <b>getobject-0.1.0.tgz</b></p>
<p>get.and.set.deep.objects.easily = true</p>
<p>Library home page: <a href="https://registry.npmjs.org/getobject/-/getobject-0.1.0.tgz">https://registry.npmjs.org/getobject/-/getobject-0.1.0.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/getobject/package.json</p>
<p>
Dependency Hierarchy:
- grunt-1.0.3.tgz (Root Library)
- grunt-legacy-util-1.1.1.tgz
- :x: **getobject-0.1.0.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/lukebroganws/NodeGoat/commit/87ddac411e57ea4967b0d6435a454aa503b72ae5">87ddac411e57ea4967b0d6435a454aa503b72ae5</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
Prototype pollution vulnerability in 'getobject' version 0.1.0 allows an attacker to cause a denial of service and may lead to remote code execution.
<p>Publish Date: 2020-12-29
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-28282>CVE-2020-28282</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.npmjs.com/package/getobject">https://www.npmjs.com/package/getobject</a></p>
<p>Release Date: 2020-12-29</p>
<p>Fix Resolution (getobject): 1.0.0</p>
<p>Direct dependency fix Resolution (grunt): 1.3.0</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> WS-2019-0063</summary>
### Vulnerable Library - <b>js-yaml-3.5.5.tgz</b></p>
<p>YAML 1.2 parser and serializer</p>
<p>Library home page: <a href="https://registry.npmjs.org/js-yaml/-/js-yaml-3.5.5.tgz">https://registry.npmjs.org/js-yaml/-/js-yaml-3.5.5.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/js-yaml/package.json</p>
<p>
Dependency Hierarchy:
- grunt-1.0.3.tgz (Root Library)
- :x: **js-yaml-3.5.5.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/lukebroganws/NodeGoat/commit/87ddac411e57ea4967b0d6435a454aa503b72ae5">87ddac411e57ea4967b0d6435a454aa503b72ae5</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
Js-yaml prior to 3.13.1 are vulnerable to Code Injection. The load() function may execute arbitrary code injected through a malicious YAML file.
<p>Publish Date: 2019-04-05
<p>URL: <a href=https://github.com/nodeca/js-yaml/pull/480>WS-2019-0063</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.1</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.npmjs.com/advisories/813">https://www.npmjs.com/advisories/813</a></p>
<p>Release Date: 2019-04-05</p>
<p>Fix Resolution (js-yaml): 3.13.1</p>
<p>Direct dependency fix Resolution (grunt): 1.0.4</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2021-33623</summary>
### Vulnerable Library - <b>trim-newlines-1.0.0.tgz</b></p>
<p>Trim newlines from the start and/or end of a string</p>
<p>Library home page: <a href="https://registry.npmjs.org/trim-newlines/-/trim-newlines-1.0.0.tgz">https://registry.npmjs.org/trim-newlines/-/trim-newlines-1.0.0.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/trim-newlines/package.json</p>
<p>
Dependency Hierarchy:
- grunt-1.0.3.tgz (Root Library)
- dateformat-1.0.12.tgz
- meow-3.7.0.tgz
- :x: **trim-newlines-1.0.0.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/lukebroganws/NodeGoat/commit/87ddac411e57ea4967b0d6435a454aa503b72ae5">87ddac411e57ea4967b0d6435a454aa503b72ae5</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
The trim-newlines package before 3.0.1 and 4.x before 4.0.1 for Node.js has an issue related to regular expression denial-of-service (ReDoS) for the .end() method.
<p>Publish Date: 2021-05-28
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-33623>CVE-2021-33623</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>7.5</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-33623">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-33623</a></p>
<p>Release Date: 2021-05-28</p>
<p>Fix Resolution (trim-newlines): 3.0.1</p>
<p>Direct dependency fix Resolution (grunt): 1.2.0</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> WS-2019-0032</summary>
### Vulnerable Library - <b>js-yaml-3.5.5.tgz</b></p>
<p>YAML 1.2 parser and serializer</p>
<p>Library home page: <a href="https://registry.npmjs.org/js-yaml/-/js-yaml-3.5.5.tgz">https://registry.npmjs.org/js-yaml/-/js-yaml-3.5.5.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/js-yaml/package.json</p>
<p>
Dependency Hierarchy:
- grunt-1.0.3.tgz (Root Library)
- :x: **js-yaml-3.5.5.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/lukebroganws/NodeGoat/commit/87ddac411e57ea4967b0d6435a454aa503b72ae5">87ddac411e57ea4967b0d6435a454aa503b72ae5</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
Versions js-yaml prior to 3.13.0 are vulnerable to Denial of Service. By parsing a carefully-crafted YAML file, the node process stalls and may exhaust system resources leading to a Denial of Service.
<p>Publish Date: 2019-03-20
<p>URL: <a href=https://github.com/nodeca/js-yaml/commit/a567ef3c6e61eb319f0bfc2671d91061afb01235>WS-2019-0032</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>7.5</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.npmjs.com/advisories/788/versions">https://www.npmjs.com/advisories/788/versions</a></p>
<p>Release Date: 2019-03-20</p>
<p>Fix Resolution (js-yaml): 3.13.0</p>
<p>Direct dependency fix Resolution (grunt): 1.0.4</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-7729</summary>
### Vulnerable Library - <b>grunt-1.0.3.tgz</b></p>
<p>The JavaScript Task Runner</p>
<p>Library home page: <a href="https://registry.npmjs.org/grunt/-/grunt-1.0.3.tgz">https://registry.npmjs.org/grunt/-/grunt-1.0.3.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/grunt/package.json</p>
<p>
Dependency Hierarchy:
- :x: **grunt-1.0.3.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/lukebroganws/NodeGoat/commit/87ddac411e57ea4967b0d6435a454aa503b72ae5">87ddac411e57ea4967b0d6435a454aa503b72ae5</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
The package grunt before 1.3.0 are vulnerable to Arbitrary Code Execution due to the default usage of the function load() instead of its secure replacement safeLoad() of the package js-yaml inside grunt.file.readYAML.
<p>Publish Date: 2020-09-03
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-7729>CVE-2020-7729</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>7.1</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: Low
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.npmjs.com/advisories/1684">https://www.npmjs.com/advisories/1684</a></p>
<p>Release Date: 2020-10-27</p>
<p>Fix Resolution: 1.3.0</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> CVE-2021-23362</summary>
### Vulnerable Library - <b>hosted-git-info-2.7.1.tgz</b></p>
<p>Provides metadata and conversions from repository urls for Github, Bitbucket and Gitlab</p>
<p>Library home page: <a href="https://registry.npmjs.org/hosted-git-info/-/hosted-git-info-2.7.1.tgz">https://registry.npmjs.org/hosted-git-info/-/hosted-git-info-2.7.1.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/hosted-git-info/package.json</p>
<p>
Dependency Hierarchy:
- grunt-1.0.3.tgz (Root Library)
- dateformat-1.0.12.tgz
- meow-3.7.0.tgz
- normalize-package-data-2.4.0.tgz
- :x: **hosted-git-info-2.7.1.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/lukebroganws/NodeGoat/commit/87ddac411e57ea4967b0d6435a454aa503b72ae5">87ddac411e57ea4967b0d6435a454aa503b72ae5</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
The package hosted-git-info before 3.0.8 are vulnerable to Regular Expression Denial of Service (ReDoS) via regular expression shortcutMatch in the fromUrl function in index.js. The affected regular expression exhibits polynomial worst-case time complexity.
<p>Publish Date: 2021-03-23
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-23362>CVE-2021-23362</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>5.3</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/advisories/GHSA-43f8-2h32-f4cj">https://github.com/advisories/GHSA-43f8-2h32-f4cj</a></p>
<p>Release Date: 2021-03-23</p>
<p>Fix Resolution (hosted-git-info): 2.8.9</p>
<p>Direct dependency fix Resolution (grunt): 1.0.4</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details>
***
<p>:rescue_worker_helmet: Automatic Remediation is available for this issue.</p>
<!-- <REMEDIATE>[{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"grunt","packageVersion":"1.0.3","packageFilePaths":["/package.json"],"isTransitiveDependency":false,"dependencyTree":"grunt:1.0.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"1.3.0","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2020-28282","vulnerabilityDetails":"Prototype pollution vulnerability in \u0027getobject\u0027 version 0.1.0 allows an attacker to cause a denial of service and may lead to remote code execution.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-28282","cvss3Severity":"high","cvss3Score":"9.8","cvss3Metrics":{"A":"High","AC":"Low","PR":"None","S":"Unchanged","C":"High","UI":"None","AV":"Network","I":"High"},"extraData":{}},{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"grunt","packageVersion":"1.0.3","packageFilePaths":["/package.json"],"isTransitiveDependency":false,"dependencyTree":"grunt:1.0.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"1.0.4","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"WS-2019-0063","vulnerabilityDetails":"Js-yaml prior to 3.13.1 are vulnerable to Code Injection. The load() function may execute arbitrary code injected through a malicious YAML file.","vulnerabilityUrl":"https://github.com/nodeca/js-yaml/pull/480","cvss3Severity":"high","cvss3Score":"8.1","cvss3Metrics":{"A":"High","AC":"High","PR":"None","S":"Unchanged","C":"High","UI":"None","AV":"Network","I":"High"},"extraData":{}},{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"grunt","packageVersion":"1.0.3","packageFilePaths":["/package.json"],"isTransitiveDependency":false,"dependencyTree":"grunt:1.0.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"1.2.0","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2021-33623","vulnerabilityDetails":"The trim-newlines package before 3.0.1 and 4.x before 4.0.1 for Node.js has an issue related to regular expression denial-of-service (ReDoS) for the .end() method.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-33623","cvss3Severity":"high","cvss3Score":"7.5","cvss3Metrics":{"A":"High","AC":"Low","PR":"None","S":"Unchanged","C":"None","UI":"None","AV":"Network","I":"None"},"extraData":{}},{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"grunt","packageVersion":"1.0.3","packageFilePaths":["/package.json"],"isTransitiveDependency":false,"dependencyTree":"grunt:1.0.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"1.0.4","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"WS-2019-0032","vulnerabilityDetails":"Versions js-yaml prior to 3.13.0 are vulnerable to Denial of Service. By parsing a carefully-crafted YAML file, the node process stalls and may exhaust system resources leading to a Denial of Service.","vulnerabilityUrl":"https://github.com/nodeca/js-yaml/commit/a567ef3c6e61eb319f0bfc2671d91061afb01235","cvss3Severity":"high","cvss3Score":"7.5","cvss3Metrics":{"A":"High","AC":"Low","PR":"None","S":"Unchanged","C":"None","UI":"None","AV":"Network","I":"None"},"extraData":{}},{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"grunt","packageVersion":"1.0.3","packageFilePaths":["/package.json"],"isTransitiveDependency":false,"dependencyTree":"grunt:1.0.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"1.3.0","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2020-7729","vulnerabilityDetails":"The package grunt before 1.3.0 are vulnerable to Arbitrary Code Execution due to the default usage of the function load() instead of its secure replacement safeLoad() of the package js-yaml inside grunt.file.readYAML.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-7729","cvss3Severity":"high","cvss3Score":"7.1","cvss3Metrics":{"A":"High","AC":"High","PR":"Low","S":"Unchanged","C":"High","UI":"Required","AV":"Network","I":"High"},"extraData":{}},{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"grunt","packageVersion":"1.0.3","packageFilePaths":["/package.json"],"isTransitiveDependency":false,"dependencyTree":"grunt:1.0.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"1.0.4","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2021-23362","vulnerabilityDetails":"The package hosted-git-info before 3.0.8 are vulnerable to Regular Expression Denial of Service (ReDoS) via regular expression shortcutMatch in the fromUrl function in index.js. The affected regular expression exhibits polynomial worst-case time complexity.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-23362","cvss3Severity":"medium","cvss3Score":"5.3","cvss3Metrics":{"A":"Low","AC":"Low","PR":"None","S":"Unchanged","C":"None","UI":"None","AV":"Network","I":"None"},"extraData":{}}]</REMEDIATE> --> | True | grunt-1.0.3.tgz: 6 vulnerabilities (highest severity is: 9.8) - autoclosed - <details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>grunt-1.0.3.tgz</b></p></summary>
<p>The JavaScript Task Runner</p>
<p>Library home page: <a href="https://registry.npmjs.org/grunt/-/grunt-1.0.3.tgz">https://registry.npmjs.org/grunt/-/grunt-1.0.3.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/grunt/package.json</p>
<p>
<p>Found in HEAD commit: <a href="https://github.com/lukebroganws/NodeGoat/commit/87ddac411e57ea4967b0d6435a454aa503b72ae5">87ddac411e57ea4967b0d6435a454aa503b72ae5</a></p></details>
## Vulnerabilities
| CVE | Severity | <img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS | Dependency | Type | Fixed in | Remediation Available |
| ------------- | ------------- | ----- | ----- | ----- | --- | --- |
| [CVE-2020-28282](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-28282) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | getobject-0.1.0.tgz | Transitive | 1.3.0 | ✅ |
| [WS-2019-0063](https://github.com/nodeca/js-yaml/pull/480) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | js-yaml-3.5.5.tgz | Transitive | 1.0.4 | ✅ |
| [CVE-2021-33623](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-33623) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | trim-newlines-1.0.0.tgz | Transitive | 1.2.0 | ✅ |
| [WS-2019-0032](https://github.com/nodeca/js-yaml/commit/a567ef3c6e61eb319f0bfc2671d91061afb01235) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | js-yaml-3.5.5.tgz | Transitive | 1.0.4 | ✅ |
| [CVE-2020-7729](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-7729) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.1 | grunt-1.0.3.tgz | Direct | 1.3.0 | ✅ |
| [CVE-2021-23362](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-23362) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 5.3 | hosted-git-info-2.7.1.tgz | Transitive | 1.0.4 | ✅ |
## Details
<details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-28282</summary>
### Vulnerable Library - <b>getobject-0.1.0.tgz</b></p>
<p>get.and.set.deep.objects.easily = true</p>
<p>Library home page: <a href="https://registry.npmjs.org/getobject/-/getobject-0.1.0.tgz">https://registry.npmjs.org/getobject/-/getobject-0.1.0.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/getobject/package.json</p>
<p>
Dependency Hierarchy:
- grunt-1.0.3.tgz (Root Library)
- grunt-legacy-util-1.1.1.tgz
- :x: **getobject-0.1.0.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/lukebroganws/NodeGoat/commit/87ddac411e57ea4967b0d6435a454aa503b72ae5">87ddac411e57ea4967b0d6435a454aa503b72ae5</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
Prototype pollution vulnerability in 'getobject' version 0.1.0 allows an attacker to cause a denial of service and may lead to remote code execution.
<p>Publish Date: 2020-12-29
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-28282>CVE-2020-28282</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.npmjs.com/package/getobject">https://www.npmjs.com/package/getobject</a></p>
<p>Release Date: 2020-12-29</p>
<p>Fix Resolution (getobject): 1.0.0</p>
<p>Direct dependency fix Resolution (grunt): 1.3.0</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> WS-2019-0063</summary>
### Vulnerable Library - <b>js-yaml-3.5.5.tgz</b></p>
<p>YAML 1.2 parser and serializer</p>
<p>Library home page: <a href="https://registry.npmjs.org/js-yaml/-/js-yaml-3.5.5.tgz">https://registry.npmjs.org/js-yaml/-/js-yaml-3.5.5.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/js-yaml/package.json</p>
<p>
Dependency Hierarchy:
- grunt-1.0.3.tgz (Root Library)
- :x: **js-yaml-3.5.5.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/lukebroganws/NodeGoat/commit/87ddac411e57ea4967b0d6435a454aa503b72ae5">87ddac411e57ea4967b0d6435a454aa503b72ae5</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
Js-yaml prior to 3.13.1 are vulnerable to Code Injection. The load() function may execute arbitrary code injected through a malicious YAML file.
<p>Publish Date: 2019-04-05
<p>URL: <a href=https://github.com/nodeca/js-yaml/pull/480>WS-2019-0063</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.1</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.npmjs.com/advisories/813">https://www.npmjs.com/advisories/813</a></p>
<p>Release Date: 2019-04-05</p>
<p>Fix Resolution (js-yaml): 3.13.1</p>
<p>Direct dependency fix Resolution (grunt): 1.0.4</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2021-33623</summary>
### Vulnerable Library - <b>trim-newlines-1.0.0.tgz</b></p>
<p>Trim newlines from the start and/or end of a string</p>
<p>Library home page: <a href="https://registry.npmjs.org/trim-newlines/-/trim-newlines-1.0.0.tgz">https://registry.npmjs.org/trim-newlines/-/trim-newlines-1.0.0.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/trim-newlines/package.json</p>
<p>
Dependency Hierarchy:
- grunt-1.0.3.tgz (Root Library)
- dateformat-1.0.12.tgz
- meow-3.7.0.tgz
- :x: **trim-newlines-1.0.0.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/lukebroganws/NodeGoat/commit/87ddac411e57ea4967b0d6435a454aa503b72ae5">87ddac411e57ea4967b0d6435a454aa503b72ae5</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
The trim-newlines package before 3.0.1 and 4.x before 4.0.1 for Node.js has an issue related to regular expression denial-of-service (ReDoS) for the .end() method.
<p>Publish Date: 2021-05-28
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-33623>CVE-2021-33623</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>7.5</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-33623">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-33623</a></p>
<p>Release Date: 2021-05-28</p>
<p>Fix Resolution (trim-newlines): 3.0.1</p>
<p>Direct dependency fix Resolution (grunt): 1.2.0</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> WS-2019-0032</summary>
### Vulnerable Library - <b>js-yaml-3.5.5.tgz</b></p>
<p>YAML 1.2 parser and serializer</p>
<p>Library home page: <a href="https://registry.npmjs.org/js-yaml/-/js-yaml-3.5.5.tgz">https://registry.npmjs.org/js-yaml/-/js-yaml-3.5.5.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/js-yaml/package.json</p>
<p>
Dependency Hierarchy:
- grunt-1.0.3.tgz (Root Library)
- :x: **js-yaml-3.5.5.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/lukebroganws/NodeGoat/commit/87ddac411e57ea4967b0d6435a454aa503b72ae5">87ddac411e57ea4967b0d6435a454aa503b72ae5</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
Versions js-yaml prior to 3.13.0 are vulnerable to Denial of Service. By parsing a carefully-crafted YAML file, the node process stalls and may exhaust system resources leading to a Denial of Service.
<p>Publish Date: 2019-03-20
<p>URL: <a href=https://github.com/nodeca/js-yaml/commit/a567ef3c6e61eb319f0bfc2671d91061afb01235>WS-2019-0032</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>7.5</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.npmjs.com/advisories/788/versions">https://www.npmjs.com/advisories/788/versions</a></p>
<p>Release Date: 2019-03-20</p>
<p>Fix Resolution (js-yaml): 3.13.0</p>
<p>Direct dependency fix Resolution (grunt): 1.0.4</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-7729</summary>
### Vulnerable Library - <b>grunt-1.0.3.tgz</b></p>
<p>The JavaScript Task Runner</p>
<p>Library home page: <a href="https://registry.npmjs.org/grunt/-/grunt-1.0.3.tgz">https://registry.npmjs.org/grunt/-/grunt-1.0.3.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/grunt/package.json</p>
<p>
Dependency Hierarchy:
- :x: **grunt-1.0.3.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/lukebroganws/NodeGoat/commit/87ddac411e57ea4967b0d6435a454aa503b72ae5">87ddac411e57ea4967b0d6435a454aa503b72ae5</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
The package grunt before 1.3.0 are vulnerable to Arbitrary Code Execution due to the default usage of the function load() instead of its secure replacement safeLoad() of the package js-yaml inside grunt.file.readYAML.
<p>Publish Date: 2020-09-03
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-7729>CVE-2020-7729</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>7.1</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: Low
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.npmjs.com/advisories/1684">https://www.npmjs.com/advisories/1684</a></p>
<p>Release Date: 2020-10-27</p>
<p>Fix Resolution: 1.3.0</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> CVE-2021-23362</summary>
### Vulnerable Library - <b>hosted-git-info-2.7.1.tgz</b></p>
<p>Provides metadata and conversions from repository urls for Github, Bitbucket and Gitlab</p>
<p>Library home page: <a href="https://registry.npmjs.org/hosted-git-info/-/hosted-git-info-2.7.1.tgz">https://registry.npmjs.org/hosted-git-info/-/hosted-git-info-2.7.1.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/hosted-git-info/package.json</p>
<p>
Dependency Hierarchy:
- grunt-1.0.3.tgz (Root Library)
- dateformat-1.0.12.tgz
- meow-3.7.0.tgz
- normalize-package-data-2.4.0.tgz
- :x: **hosted-git-info-2.7.1.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/lukebroganws/NodeGoat/commit/87ddac411e57ea4967b0d6435a454aa503b72ae5">87ddac411e57ea4967b0d6435a454aa503b72ae5</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
The package hosted-git-info before 3.0.8 are vulnerable to Regular Expression Denial of Service (ReDoS) via regular expression shortcutMatch in the fromUrl function in index.js. The affected regular expression exhibits polynomial worst-case time complexity.
<p>Publish Date: 2021-03-23
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-23362>CVE-2021-23362</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>5.3</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/advisories/GHSA-43f8-2h32-f4cj">https://github.com/advisories/GHSA-43f8-2h32-f4cj</a></p>
<p>Release Date: 2021-03-23</p>
<p>Fix Resolution (hosted-git-info): 2.8.9</p>
<p>Direct dependency fix Resolution (grunt): 1.0.4</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details>
***
<p>:rescue_worker_helmet: Automatic Remediation is available for this issue.</p>
<!-- <REMEDIATE>[{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"grunt","packageVersion":"1.0.3","packageFilePaths":["/package.json"],"isTransitiveDependency":false,"dependencyTree":"grunt:1.0.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"1.3.0","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2020-28282","vulnerabilityDetails":"Prototype pollution vulnerability in \u0027getobject\u0027 version 0.1.0 allows an attacker to cause a denial of service and may lead to remote code execution.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-28282","cvss3Severity":"high","cvss3Score":"9.8","cvss3Metrics":{"A":"High","AC":"Low","PR":"None","S":"Unchanged","C":"High","UI":"None","AV":"Network","I":"High"},"extraData":{}},{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"grunt","packageVersion":"1.0.3","packageFilePaths":["/package.json"],"isTransitiveDependency":false,"dependencyTree":"grunt:1.0.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"1.0.4","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"WS-2019-0063","vulnerabilityDetails":"Js-yaml prior to 3.13.1 are vulnerable to Code Injection. The load() function may execute arbitrary code injected through a malicious YAML file.","vulnerabilityUrl":"https://github.com/nodeca/js-yaml/pull/480","cvss3Severity":"high","cvss3Score":"8.1","cvss3Metrics":{"A":"High","AC":"High","PR":"None","S":"Unchanged","C":"High","UI":"None","AV":"Network","I":"High"},"extraData":{}},{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"grunt","packageVersion":"1.0.3","packageFilePaths":["/package.json"],"isTransitiveDependency":false,"dependencyTree":"grunt:1.0.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"1.2.0","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2021-33623","vulnerabilityDetails":"The trim-newlines package before 3.0.1 and 4.x before 4.0.1 for Node.js has an issue related to regular expression denial-of-service (ReDoS) for the .end() method.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-33623","cvss3Severity":"high","cvss3Score":"7.5","cvss3Metrics":{"A":"High","AC":"Low","PR":"None","S":"Unchanged","C":"None","UI":"None","AV":"Network","I":"None"},"extraData":{}},{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"grunt","packageVersion":"1.0.3","packageFilePaths":["/package.json"],"isTransitiveDependency":false,"dependencyTree":"grunt:1.0.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"1.0.4","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"WS-2019-0032","vulnerabilityDetails":"Versions js-yaml prior to 3.13.0 are vulnerable to Denial of Service. By parsing a carefully-crafted YAML file, the node process stalls and may exhaust system resources leading to a Denial of Service.","vulnerabilityUrl":"https://github.com/nodeca/js-yaml/commit/a567ef3c6e61eb319f0bfc2671d91061afb01235","cvss3Severity":"high","cvss3Score":"7.5","cvss3Metrics":{"A":"High","AC":"Low","PR":"None","S":"Unchanged","C":"None","UI":"None","AV":"Network","I":"None"},"extraData":{}},{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"grunt","packageVersion":"1.0.3","packageFilePaths":["/package.json"],"isTransitiveDependency":false,"dependencyTree":"grunt:1.0.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"1.3.0","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2020-7729","vulnerabilityDetails":"The package grunt before 1.3.0 are vulnerable to Arbitrary Code Execution due to the default usage of the function load() instead of its secure replacement safeLoad() of the package js-yaml inside grunt.file.readYAML.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-7729","cvss3Severity":"high","cvss3Score":"7.1","cvss3Metrics":{"A":"High","AC":"High","PR":"Low","S":"Unchanged","C":"High","UI":"Required","AV":"Network","I":"High"},"extraData":{}},{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"grunt","packageVersion":"1.0.3","packageFilePaths":["/package.json"],"isTransitiveDependency":false,"dependencyTree":"grunt:1.0.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"1.0.4","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2021-23362","vulnerabilityDetails":"The package hosted-git-info before 3.0.8 are vulnerable to Regular Expression Denial of Service (ReDoS) via regular expression shortcutMatch in the fromUrl function in index.js. The affected regular expression exhibits polynomial worst-case time complexity.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-23362","cvss3Severity":"medium","cvss3Score":"5.3","cvss3Metrics":{"A":"Low","AC":"Low","PR":"None","S":"Unchanged","C":"None","UI":"None","AV":"Network","I":"None"},"extraData":{}}]</REMEDIATE> --> | non_test | grunt tgz vulnerabilities highest severity is autoclosed vulnerable library grunt tgz the javascript task runner library home page a href path to dependency file package json path to vulnerable library node modules grunt package json found in head commit a href vulnerabilities cve severity cvss dependency type fixed in remediation available high getobject tgz transitive high js yaml tgz transitive high trim newlines tgz transitive high js yaml tgz transitive high grunt tgz direct medium hosted git info tgz transitive details cve vulnerable library getobject tgz get and set deep objects easily true library home page a href path to dependency file package json path to vulnerable library node modules getobject package json dependency hierarchy grunt tgz root library grunt legacy util tgz x getobject tgz vulnerable library found in head commit a href found in base branch master vulnerability details prototype pollution vulnerability in getobject version allows an attacker to cause a denial of service and may lead to remote code execution publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution getobject direct dependency fix resolution grunt rescue worker helmet automatic remediation is available for this issue ws vulnerable library js yaml tgz yaml parser and serializer library home page a href path to dependency file package json path to vulnerable library node modules js yaml package json dependency hierarchy grunt tgz root library x js yaml tgz vulnerable library found in head commit a href found in base branch master vulnerability details js yaml prior to are vulnerable to code injection the load function may execute arbitrary code injected through a malicious yaml file publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity high privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution js yaml direct dependency fix resolution grunt rescue worker helmet automatic remediation is available for this issue cve vulnerable library trim newlines tgz trim newlines from the start and or end of a string library home page a href path to dependency file package json path to vulnerable library node modules trim newlines package json dependency hierarchy grunt tgz root library dateformat tgz meow tgz x trim newlines tgz vulnerable library found in head commit a href found in base branch master vulnerability details the trim newlines package before and x before for node js has an issue related to regular expression denial of service redos for the end method publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution trim newlines direct dependency fix resolution grunt rescue worker helmet automatic remediation is available for this issue ws vulnerable library js yaml tgz yaml parser and serializer library home page a href path to dependency file package json path to vulnerable library node modules js yaml package json dependency hierarchy grunt tgz root library x js yaml tgz vulnerable library found in head commit a href found in base branch master vulnerability details versions js yaml prior to are vulnerable to denial of service by parsing a carefully crafted yaml file the node process stalls and may exhaust system resources leading to a denial of service publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution js yaml direct dependency fix resolution grunt rescue worker helmet automatic remediation is available for this issue cve vulnerable library grunt tgz the javascript task runner library home page a href path to dependency file package json path to vulnerable library node modules grunt package json dependency hierarchy x grunt tgz vulnerable library found in head commit a href found in base branch master vulnerability details the package grunt before are vulnerable to arbitrary code execution due to the default usage of the function load instead of its secure replacement safeload of the package js yaml inside grunt file readyaml publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity high privileges required low user interaction required scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution rescue worker helmet automatic remediation is available for this issue cve vulnerable library hosted git info tgz provides metadata and conversions from repository urls for github bitbucket and gitlab library home page a href path to dependency file package json path to vulnerable library node modules hosted git info package json dependency hierarchy grunt tgz root library dateformat tgz meow tgz normalize package data tgz x hosted git info tgz vulnerable library found in head commit a href found in base branch master vulnerability details the package hosted git info before are vulnerable to regular expression denial of service redos via regular expression shortcutmatch in the fromurl function in index js the affected regular expression exhibits polynomial worst case time complexity publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact low for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution hosted git info direct dependency fix resolution grunt rescue worker helmet automatic remediation is available for this issue rescue worker helmet automatic remediation is available for this issue istransitivedependency false dependencytree grunt isminimumfixversionavailable true minimumfixversion isbinary false basebranches vulnerabilityidentifier cve vulnerabilitydetails prototype pollution vulnerability in version allows an attacker to cause a denial of service and may lead to remote code execution vulnerabilityurl istransitivedependency false dependencytree grunt isminimumfixversionavailable true minimumfixversion isbinary false basebranches vulnerabilityidentifier ws vulnerabilitydetails js yaml prior to are vulnerable to code injection the load function may execute arbitrary code injected through a malicious yaml file vulnerabilityurl istransitivedependency false dependencytree grunt isminimumfixversionavailable true minimumfixversion isbinary false basebranches vulnerabilityidentifier cve vulnerabilitydetails the trim newlines package before and x before for node js has an issue related to regular expression denial of service redos for the end method vulnerabilityurl istransitivedependency false dependencytree grunt isminimumfixversionavailable true minimumfixversion isbinary false basebranches vulnerabilityidentifier ws vulnerabilitydetails versions js yaml prior to are vulnerable to denial of service by parsing a carefully crafted yaml file the node process stalls and may exhaust system resources leading to a denial of service vulnerabilityurl istransitivedependency false dependencytree grunt isminimumfixversionavailable true minimumfixversion isbinary false basebranches vulnerabilityidentifier cve vulnerabilitydetails the package grunt before are vulnerable to arbitrary code execution due to the default usage of the function load instead of its secure replacement safeload of the package js yaml inside grunt file readyaml vulnerabilityurl istransitivedependency false dependencytree grunt isminimumfixversionavailable true minimumfixversion isbinary false basebranches vulnerabilityidentifier cve vulnerabilitydetails the package hosted git info before are vulnerable to regular expression denial of service redos via regular expression shortcutmatch in the fromurl function in index js the affected regular expression exhibits polynomial worst case time complexity vulnerabilityurl | 0 |
44,795 | 5,888,744,428 | IssuesEvent | 2017-05-17 10:59:48 | nextcloud/server | https://api.github.com/repos/nextcloud/server | opened | Make app order configurable | 1. to develop design enhancement | Admins should be able to
- set an default order for apps
- set, whether users should be allowed to change the order of the apps
If users are allowed to change the order by themself, this configuration should be handles via drag-and-drop in the app menu.
We could use https://github.com/juliushaertl/apporder/ as base ...
Follow up: https://github.com/juliushaertl/apporder/issues/29
@juliushaertl @nextcloud/designers | 1.0 | Make app order configurable - Admins should be able to
- set an default order for apps
- set, whether users should be allowed to change the order of the apps
If users are allowed to change the order by themself, this configuration should be handles via drag-and-drop in the app menu.
We could use https://github.com/juliushaertl/apporder/ as base ...
Follow up: https://github.com/juliushaertl/apporder/issues/29
@juliushaertl @nextcloud/designers | non_test | make app order configurable admins should be able to set an default order for apps set whether users should be allowed to change the order of the apps if users are allowed to change the order by themself this configuration should be handles via drag and drop in the app menu we could use as base follow up juliushaertl nextcloud designers | 0 |
269,192 | 23,428,150,229 | IssuesEvent | 2022-08-14 18:01:16 | opentibiabr/otservbr-global | https://api.github.com/repos/opentibiabr/otservbr-global | closed | Error Npc's | Type: Bug Priority: High Status: Pending Test source map | ### Priority
High
### Area
- [X] Datapack
- [ ] Source
- [ ] Map
- [ ] Other
### What happened?
Hi, I'm using otservbr in ubuntu 20.04, I just updated version 1290 and it's showing me an error in the console when using certain npcs such as (Hanna, flint, yasior and all the djin) they are for the moment the ones I've tried, I add print of the error displayed.
the exact line of the error is the following:
npcType.onSellItem = function(npc, player, clientId, subtype, amount, name, totalCost)
### What OS are you seeing the problem on?
Ubuntu 20.04
### Code of Conduct
- [X] I agree to follow this project's Code of Conduct | 1.0 | Error Npc's - ### Priority
High
### Area
- [X] Datapack
- [ ] Source
- [ ] Map
- [ ] Other
### What happened?
Hi, I'm using otservbr in ubuntu 20.04, I just updated version 1290 and it's showing me an error in the console when using certain npcs such as (Hanna, flint, yasior and all the djin) they are for the moment the ones I've tried, I add print of the error displayed.
the exact line of the error is the following:
npcType.onSellItem = function(npc, player, clientId, subtype, amount, name, totalCost)

### What OS are you seeing the problem on?
Ubuntu 20.04
### Code of Conduct
- [X] I agree to follow this project's Code of Conduct | test | error npc s priority high area datapack source map other what happened hi i m using otservbr in ubuntu i just updated version and it s showing me an error in the console when using certain npcs such as hanna flint yasior and all the djin they are for the moment the ones i ve tried i add print of the error displayed the exact line of the error is the following npctype onsellitem function npc player clientid subtype amount name totalcost what os are you seeing the problem on ubuntu code of conduct i agree to follow this project s code of conduct | 1 |
308,501 | 26,610,698,112 | IssuesEvent | 2023-01-23 23:48:36 | PalisadoesFoundation/talawa-api | https://api.github.com/repos/PalisadoesFoundation/talawa-api | closed | Resolvers: Create tests for createTask.js | good first issue unapproved points 02 test |
The Talawa-API code base needs to be 100% reliable. This means we need to have 100% test code coverage.
Tests need to be written for file `lib/resolvers/project_task_mutations/createTask.js`
- We will need the API to be refactored for all methods, classes and/or functions found in this file for testing to be correctly executed.
- When complete, all all methods, classes and/or functions in the refactored file will need to be tested. These tests must be placed in a
single file with the name `tests/resolvers/project_task_mutations/createTask.spec.js`. You may need to create the appropriate directory structure to do this.
### IMPORTANT:
Please refer to the parent issue on how to implement these tests correctly:
- https://github.com/PalisadoesFoundation/talawa-api/issues/490
### PR Acceptance Criteria
- When complete this file must show **100%** coverage when merged into the code base. This will be clearly visible when you submit your PR.
- [The current code coverage for the file can be found here](https://codecov.io/gh/PalisadoesFoundation/talawa-api/tree/develop/lib/resolvers/project_task_mutations/). If the file isn't found in this directory, or there is a 404 error, then tests have not been created.
- The PR will show a report for the code coverage for the file you have added. You can use that as a guide. | 1.0 | Resolvers: Create tests for createTask.js -
The Talawa-API code base needs to be 100% reliable. This means we need to have 100% test code coverage.
Tests need to be written for file `lib/resolvers/project_task_mutations/createTask.js`
- We will need the API to be refactored for all methods, classes and/or functions found in this file for testing to be correctly executed.
- When complete, all all methods, classes and/or functions in the refactored file will need to be tested. These tests must be placed in a
single file with the name `tests/resolvers/project_task_mutations/createTask.spec.js`. You may need to create the appropriate directory structure to do this.
### IMPORTANT:
Please refer to the parent issue on how to implement these tests correctly:
- https://github.com/PalisadoesFoundation/talawa-api/issues/490
### PR Acceptance Criteria
- When complete this file must show **100%** coverage when merged into the code base. This will be clearly visible when you submit your PR.
- [The current code coverage for the file can be found here](https://codecov.io/gh/PalisadoesFoundation/talawa-api/tree/develop/lib/resolvers/project_task_mutations/). If the file isn't found in this directory, or there is a 404 error, then tests have not been created.
- The PR will show a report for the code coverage for the file you have added. You can use that as a guide. | test | resolvers create tests for createtask js the talawa api code base needs to be reliable this means we need to have test code coverage tests need to be written for file lib resolvers project task mutations createtask js we will need the api to be refactored for all methods classes and or functions found in this file for testing to be correctly executed when complete all all methods classes and or functions in the refactored file will need to be tested these tests must be placed in a single file with the name tests resolvers project task mutations createtask spec js you may need to create the appropriate directory structure to do this important please refer to the parent issue on how to implement these tests correctly pr acceptance criteria when complete this file must show coverage when merged into the code base this will be clearly visible when you submit your pr if the file isn t found in this directory or there is a error then tests have not been created the pr will show a report for the code coverage for the file you have added you can use that as a guide | 1 |
228,565 | 18,243,066,010 | IssuesEvent | 2021-10-01 14:59:54 | massbitprotocol/massbitprotocol | https://api.github.com/repos/massbitprotocol/massbitprotocol | closed | Compare data with the graph | testing | - run quickswap with the graph to compare when running with Massbit (data + performance)
ETC: 24/9 | 1.0 | Compare data with the graph - - run quickswap with the graph to compare when running with Massbit (data + performance)
ETC: 24/9 | test | compare data with the graph run quickswap with the graph to compare when running with massbit data performance etc | 1 |